当前位置:网站首页>[an Xun cup 2019]attack
[an Xun cup 2019]attack
2022-06-27 14:02:00 【[mzq]】
[ An Xun Cup 2019]Attack
Title address : https://buuoj.cn/challenges#[%E5%AE%89%E6%B4%B5%E6%9D%AF%202019]Attack
foremost Separate in zip File found to contain flag.txt The package ,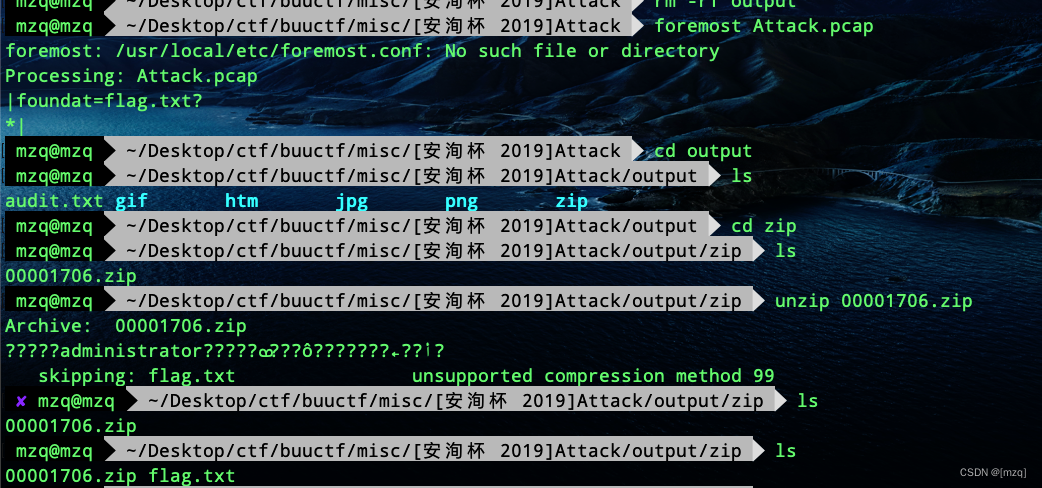
According to the hint, it may be administer Password , Let's go to the wireshark Looking for dmp file
Export with mimikatz Decrypt , obtain administer password
W3lc0meToD0g3

Decompression is obtained. flag

D0g3{3466b11de8894198af3636c5bd1efce2}
边栏推荐
- 跨境电商多商户系统怎么选
- [day 27] given an integer n, print out the full permutation from 1 to n | Full Permutation template
- Kyndryl与Oracle和Veritas达成合作
- Dynamic Networks and Conditional Computation论文简读和代码合集
- Can flush open an account for stock trading? Is it safe?
- Bidding announcement: Oracle database maintenance service procurement of the First Affiliated Hospital of Jinan University
- 关于接口测试自动化的总结与思考
- [business security-04] universal user name and universal password experiment
- PCL库——报错解决:安装时遇到的cmake与anaconda的冲突问题
- 高效率取幂运算
猜你喜欢

Semaphore of thread synchronization

Implementing springboard agent through SSH port forwarding configuration

NAACL 2022 | TAMT:通过下游任务无关掩码训练搜索可迁移的BERT子网络

Kyndryl partnered with Oracle and Veritas

Naacl 2022 | TAMT: search the transportable Bert subnet through downstream task independent mask training
【业务安全-04】万能用户名及万能密码实验

【业务安全-02】业务数据安全测试及商品订购数量篡改实例
Redis 主从复制、哨兵模式、Cluster集群

Redis持久化
![[OS command injection] common OS command execution functions and OS command injection utilization examples and range experiments - based on DVWA range](/img/f2/458770fc74971bef23f96f87733ee5.png)
[OS command injection] common OS command execution functions and OS command injection utilization examples and range experiments - based on DVWA range
随机推荐
What if the win system cannot complete the update and is revoking the status change
Shell 简明教程
[day 27] given an integer n, print out the full permutation from 1 to n | Full Permutation template
Openssf security plan: SBOM will drive software supply chain security
【OS命令注入】常见OS命令执行函数以及OS命令注入利用实例以及靶场实验—基于DVWA靶场
Rereading the classic: the craft of research (1)
每日3题(2):检查二进制字符串字段
buuctf misc 百里挑一
命令行编辑器 sed 基础用法总结
Practice of constructing ten billion relationship knowledge map based on Nebula graph
Gaode map IP positioning 2.0 backup
【mysql进阶】MTS主从同步原理及实操指南(七)
[business security-02] business data security test and example of commodity order quantity tampering
初识云原生安全:云时代的最佳保障
Naacl 2022 | TAMT: search the transportable Bert subnet through downstream task independent mask training
[OS command injection] common OS command execution functions and OS command injection utilization examples and range experiments - based on DVWA range
Is there any discount for opening an account now? Is it safe to open an account online?
AcWing 第57 场周赛
Redis持久化
my.ini文件配置
