当前位置:网站首页>Network Security Threat Intelligence System
Network Security Threat Intelligence System
2022-06-11 18:01:00 【The shark is starving】
Course is an introduction to
Threat Intelligence , It is facing new threat forms , Defense thinking from the past based on vulnerability centered approach ,
The inevitable result of evolving into a threat centric approach , It's related to big data security analysis 、 The idea of defense in depth based on attack chain is forming the cornerstone of a new generation of defense system .
at present , As network security threats become more and more complex and common , It is impossible for traditional security methods to identify and resist all possible attacks .
And use threat intelligence to do protection practice , It can help enterprises and countries to establish a data-driven system , Let enterprises and countries “ See ” threat , So as to establish in-depth protection system .
This course is taught by Jinxiangyu (NUKE), yes Sec-UN Founder of the website , Initiator of Security Threat Intelligence promotion alliance , Now he is the vice president of an investment company .
Have undertaken safety assessment 、 Penetration test 、 Emergency response 、 System reinforcement and other technical work ,
later stage , Mainly based on technical management 、 The enterprise architecture 、IT planning 、 Project group management 、 Management and control of large-scale information projects and other fields ,
Through Mr. Jin's explanation , It can give you an in-depth understanding of the new generation of threat centric threat intelligence system .
Course objectives
Through the study of this course , Scholars can understand the new generation of threat centric threat intelligence system .
1. Concept

Offensive and defensive imbalance 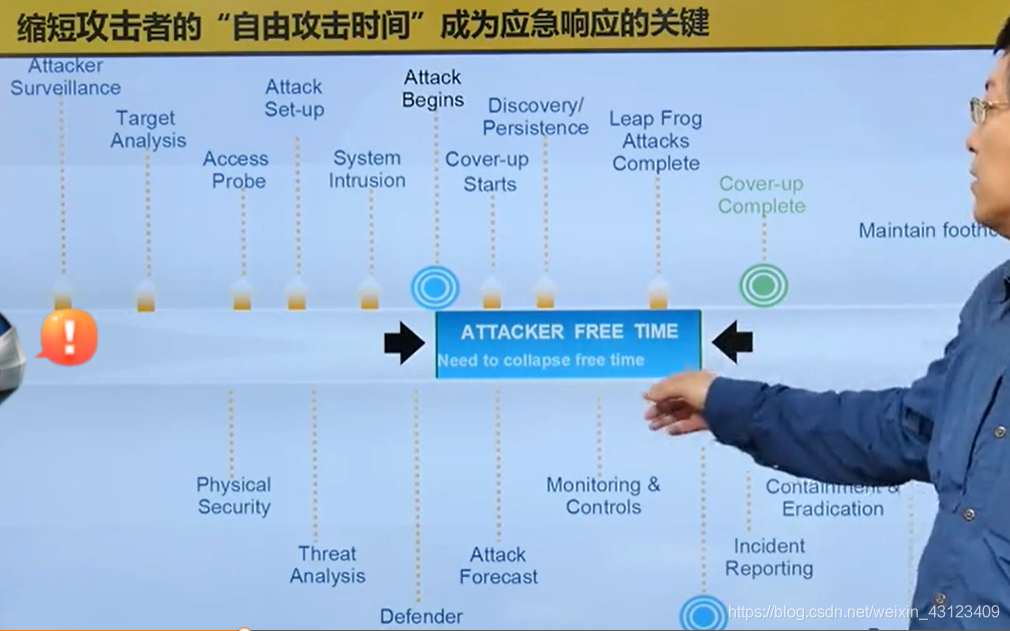
Free attack time : The time from the beginning of the attack to being discovered by the defender 
What is cyber security threat intelligence ?
Threat is a possibility , The event has happened 
Threat Intelligence is processed data 





2. Construction of threat intelligence system








in summary : I haven't finished reading
边栏推荐
- Service学习笔记01-启动方式与生命周期
- tidb-cdc同步mysql没有的特性到mysql时的处理
- ForEach遍历集合、 集合容器
- 开源项目那么多,这次带你了解个版本的区别,明白alpha版、beta版、rc版是什么意思
- Spring 2021 daily question [week7 not finished]
- The top ten trends of 2022 industrial Internet security was officially released
- 6-3 reading articles (*)
- 夜神安装apk,以及bp代理
- [solution] codeforces round 798 (Div. 2)
- Merge K ascending linked lists ---2022/02/26
猜你喜欢

mysql8安装,navicat安装,sqli-labs搭建

threejs利用indexeddb缓存加载glb模型

【C】 ATOI function implementation +offsetof implementation + exchange binary odd and even digits

【先收藏,早晚用得到】100个Flink高频面试题系列(二)
Ffmpeg parity field frame interlace progressive command and code processing

Ffmpeg hardware codec NVIDIA GPU

密码学概述

Summary of clustering methods

【C】 Compilation preprocessing and environment

安装mariadb 10.5.7(tar包安装)
随机推荐
vulhub
7-2 h0107. Pig-Latin
Comparison of mongoose in express, KOA and egg
6-6 batch sum (*)
Can 400 fans earn 20W a month? How did you do it?
which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_ mod
System learning typescript (V) - joint type
[collect first and use it sooner or later] 100 Flink high-frequency interview questions series (III)
[collect first and use it sooner or later] 100 Flink high-frequency interview questions series (II)
Ffmpeg hardware codec NVIDIA GPU
Service学习笔记01-启动方式与生命周期
Hwang
Tidb GC related problems
Hello go (XIII). Go language common standard library III
关于元素位置和尺寸
任意用户密码重置的10种方式
[collect first and use it sooner or later] 100 Flink high-frequency interview questions series (I)
Global and Chinese markets of solid polymer aluminum capacitors 2022-2028: Research Report on technology, participants, trends, market size and share
Rtsp/onvif protocol easynvr video platform arm version cross compilation process and common error handling
Mathematical basis of information security Chapter 2 - congruence