当前位置:网站首页>[ManageEngine] what is Siem
[ManageEngine] what is Siem
2022-07-27 14:48:00 【ManageEngine Zhuohao】
SIEM On behalf of the security 、 Information and event management ( Security,Information, andEventManagement).SIEM Technology will log data 、 Security alerts and events are aggregated into a centralized platform , For safety monitoring For real-time analysis .
SIEM Include :
- Security information management (SIM): SIM A collection involving all network activities . This includes slave servers 、 A firewall 、 domain controller 、 Router 、 The log data collected by the database and network stream , And unstructured data in the network , E-mail . Two techniques can be used to collect log data , That is, agent-free collection and agent-based collection .
- Agent based log collection : This approach requires an agent to be deployed on each device . Agent collects logs , Then return the log to SIEM The server analyzes and filters it before . This technology is mainly used in closed and secure networks , For example, the demilitarized zone with limited communication (DMZ).
- Agentless log collection : This is a more common method ,SIEM The server uses a secure communication channel ( For example, a specific port using a security protocol ) Automatically collect logs generated by the device .
- Security incident management (SIEM): SIEM It refers to the analysis of collected data . Use a variety of techniques to analyze data , Send alarm , and / Or start the workflow for any abnormal behavior .
The analysis process includes :
- Log Association : Analyze all collected data , And correlate the logs , To detect any attack patterns . Log data can also be associated with threat sources , To test compromise indicators (IOC).
- Threat Intelligence : Context threat information is used to detect any intrusion in the network 、 Lateral movement or data leakage .
- User behavior analysis based on machine learning : Machine learning algorithms and analysis tools can form a baseline for user behavior patterns . If the behavior deviates ,SIEM The solution will detect an exception , sound the alarm , Timely take precautions against security threats .
The data obtained by the above technology will be presented in the form of bar chart or pie chart , This makes IT Security administrators can be faster 、 Making decisions easier .
SIEM Classic application scenarios for brute force cracking :
Enter the incorrect network access password five times in one minute . This is considered a low priority attack , Because the user may have entered the wrong password many times .
Now think about what happens if you type 240 Wrong password for times . Then this is most likely a violent attack , Hackers are trying to crack your account .
SIEM How to trigger the alarm :
- Enter the wrong password within one minute n Times will show : Login failed , event ID 4625
- stay n Entering the correct password after failed attempts will display : Login successful , event ID 4624
- Give an alarm : There may be violent attacks on the network .
SIEM Software can detect such violent attacks , notice IT Security administrator , And automatically start the workflow to lock the account and isolate the computer where the event occurs .

EventLog Analyzer Is a log management and analysis tool , Can achieve fast 、 Easily detect cyber threats . This kind of SIEM The solution can identify any IT Log generated by resources and visual analysis . It can be easily extended to any IT The network environment , Resist any internal or external threats .
边栏推荐
- 基于GEC6818开发板的相册
- 线程知识总结
- Win11壁纸变黑怎么办?Win11壁纸变黑了的解决方法
- poj3461 Oulipo【KMP】
- Hdu1422 revisits the world cup [DP]
- 解气!哈工大被禁用MATLAB后,国产工业软件霸气回击
- FPGA timing constraint sharing 04_ Output delay constraint
- Slam overview Reading Note 6: slam research based on image semantics: application-oriented solutions for autonomous navigation of mobile robots 2020
- 数据库使用psql及jdbc进行远程连接,不定时自动断开的解决办法
- SkyWalking分布式系统应用程序性能监控工具-中
猜你喜欢

@What happens when bean and @component are used on the same class?

c语言分层理解(c语言数组)

一文搞懂 Redis 架构演化之路

telnet远程登录aaa模式详解【华为eNSP】
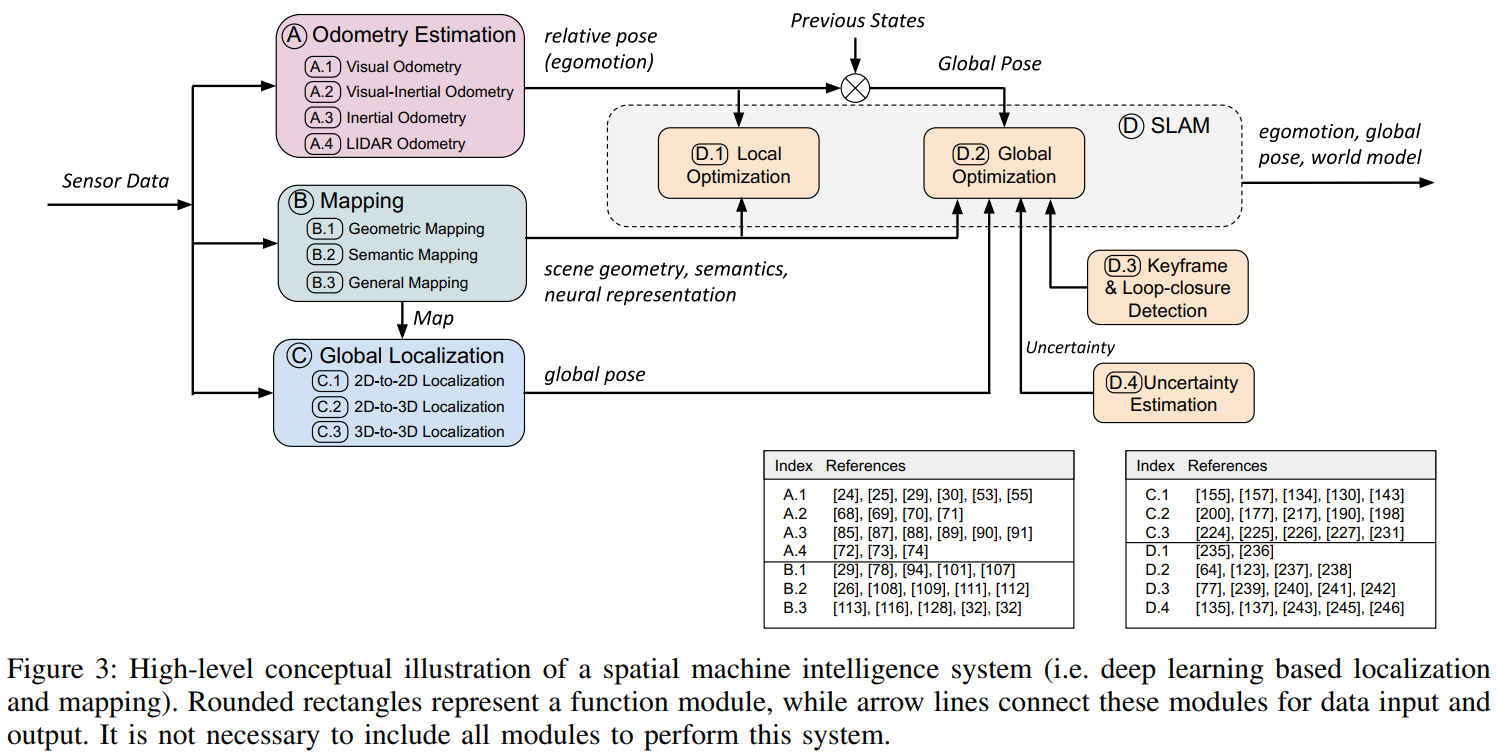
SLAM综述阅读笔记四:A Survey on Deep Learning for Localization and Mapping: Towards the Age of Spatial 2020

Toward fast, flexible, and robust low light image enhancement cvpr2022

Unity3d learning note 10 - texture array

如何做好企业系统漏洞评估
RTL8762DK 环境搭建(一)

大家最想要的,最全的C语言知识点总结,还不赶紧学习
随机推荐
What is the execution method of the stand-alone parallel query of PostgreSQL?
Ten thousand words detailed Google play online application standard package format AAB
Lesson 3: reverse word order
Lesson 3: SPFA seeking the shortest path
TXT把换行 替换为空格或者取消换行
poj3461 Oulipo【KMP】
Lecture 4: Longest ascending substring
Document translation__ Salt and pepper image denoising based on adaptive total variation L1 regularization
一篇文章看懂JS执行上下文
watch VS watchEffect
Why is there no unified quotation for third-party testing fees of software products?
面试官问:如何判断一个元素是否在可视区域?
Kubernetes 节点磁盘故障排查
Photo album based on gec6818 development board
Get the data of the first frame of unity's open camera
Navicate reports an error access violation at address 00000000
Chinese character style transfer --- antagonistic discriminative domain adaptation (L1)
Is there a regular and safe account opening platform for gold speculation
Document translation__ Tvreg V2: variational imaging method for denoising, deconvolution, repair and segmentation (part)
获取Unity打开摄像头第一帧有画面的数据