当前位置:网站首页>Memoirs of actual combat: breaking the border from webshell
Memoirs of actual combat: breaking the border from webshell
2022-06-29 08:32:00 【Hetian network security laboratory】
Text
A penetration of an authorized unit , Because of the php frame , some cms Upload , From realization webshell Start .
details
Add listening , Generate Trojan file and change the application name to hide online .


Change the sleep time to 10 second

View host name whoami

Grab the plaintext password

Sure enough, the authority is not enough , Raise the right

Try all kinds of potatoes , According to the patch, I didn't find ,winserver2012 Right to mention here ms16-075 Yes. , But the strange thing is CS Not online , Upload script to go online CS

However, it did not go online , The cost of trial and error is high
【---- Help network security learn , All the following learning materials are free ! Add weix:yj009991, remarks “ csdn ” obtain !】
① Thinking map of the growth path of Network Security Learning
② 60+ Network security classic common toolkit
③ 100+SRC Vulnerability analysis report
④ 150+ Network security attack and defense technology ebook
⑤ The most authoritative CISSP Certification test guide + Question bank
⑥ super 1800 page CTF Practical skills manual
Check it out. winserver 2012 Right to the version of , Uploading multiple scripts does not work ,CS Your plug-in just hit , In fact, I don't know why I failed the first time I tried , It's strange
Restart a monitor

Continue to raise rights ,ms-058 It is possible to raise the right

It was only the second time that the right was successfully raised

Modify sleep time , Neither too long nor too short is recommended , Grab the plaintext password

The plaintext password was successfully retrieved , Try to login remotely , Because in the early stage of information collection 3389 It's open .
Successfully logged in

Try to write scheduled task input permission maintenance , Here, you can choose to plan a task or dll Hijacking is OK , Here I choose to plan the task , After all, authorization projects don't worry about other problems , According to the preceding systeminfo Information at this time, we have obtained the permission of domain control , You can continue to perform intranet horizontal and domain penetration

Of this network segment pc less , Intranet usually has other ip, Direct scan B paragraph

Get a lot of Intranet terminal information , however win10 Mostly ,win10 Of 445 Port utilization is generally blocked , Directly scan whether there are service classes , Such as ftp
The virtual terminal can execute , But no echo , You can only go up remotely


There are a large number of terminals in the intranet , But there's no server , This is the only server , Small domain , At this time, the network topology of the intranet is roughly ,445 There are a large number of hosts open in the intranet

But I tried to use it for several times without success , Basically winserver If you use the server, you can get shell The probability is probably high ,win10 Your host has never been successful before , This time, I didn't get it shell

According to the obtained plaintext password , Password spraying for blasting

Get passwords for some accounts .
Query the currently logged in domain user
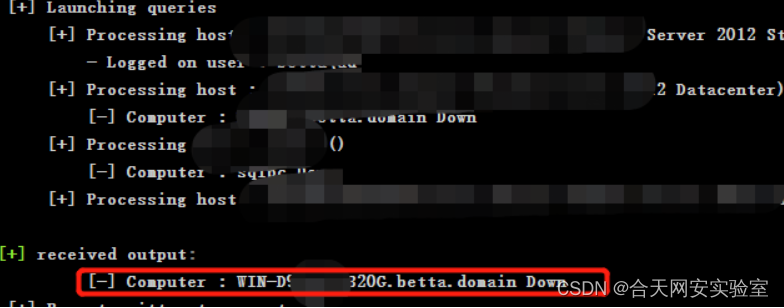
Determine the host according to the host name queried above ip The address is 192.168.0.119,pth After the launch .
Summary
I don't know if it's a honeypot , But there are basically no servers in the intranet , The number of domain users is also small , Anyway, writing the report and handing it in will be over .
边栏推荐
- AWS Iam inline policy example
- Should product managers learn from ink knife or Axure?
- Indextree and Application
- [quantitative investment system] problem records and Solutions
- Soliciting articles and contributions - building a blog environment with a lightweight application server
- STM32基于HAL库的USART+DMA使用
- Binary search tree
- À propos de Hook
- Development trend of garment industry | supply chain | intelligent manufacturing
- Automatic operation and maintenance management platform - construction and daily use of SPuG
猜你喜欢
![Target tracking [single target tracking (vot/sot), target detection, pedestrian re identification (re ID)]](/img/f2/d42032f05214a4ad9339ea18966cc2.jpg)
Target tracking [single target tracking (vot/sot), target detection, pedestrian re identification (re ID)]

Introduction to taro

重磅发布 | 《FISCO BCOS应用落地指南》
![[eye of depth wuenda machine learning homework class phase IV] regularization regularization summary](/img/24/3d0b892c0eaa330f0c69764de5da13.png)
[eye of depth wuenda machine learning homework class phase IV] regularization regularization summary
SQL Server enable CDC

图文详解JVM中的垃圾回收机制(GC)

征文投稿丨使用轻量应用服务器搭建博客环境

Swift中@dynamicMemberLookup和callAsFunction特性实现对象透明代理功能

Seven common sorts

【微服务|OpenFeign】openfeign的超时时间
随机推荐
What are the organizational structure and job responsibilities of product managers in Internet companies?
Oracle-子查询
[redis] redis6 learning framework ideas and details
自动化运维管理平台——spug的搭建和日常使用
Speech signal processing - Fundamentals (I): basic acoustic knowledge
MySQL statistics by day / week / month / quarter / half year / year
[Kerberos] analysis of Kerberos authentication
Audio and video development cases 99 lectures - Contents
【LoRaWAN节点应用】安信可Ra-08/Ra-08H模组入网LoRaWAN网络的应用及功耗情况
Np5 formatted output (III)
[domain penetration authorization] cve-2020-1472 Netlogon privilege escalation vulnerability
Want to open a stock account, is it safe to open a stock account online-
语音合成:概述【不等长序列关系建模的生成任务】
关于#sql#的问题:创建一个名为View_XB视图,功能是①如果有重名的视图先删除后创建②显示XSB表中本班级的男女生各有多少人,并添加检查约束
Stm32 usart+dma usage based on Hal Library
Flutter shared_ Preferences use
Flutter file read / write -path_ provider
Verilog初体验
Seven common sorts
笔记本电脑快速连接手机热点的方法
