当前位置:网站首页>切入点表达式
切入点表达式
2022-07-03 16:01:00 【不入开发不工作】
边栏推荐
- 找映射关系
- MB10M-ASEMI整流桥MB10M
- How to use AAB to APK and APK to AAB of Google play apps on the shelves
- [combinatorics] combinatorial identity (sum of variable upper terms 1 combinatorial identity | summary of three combinatorial identity proof methods | proof of sum of variable upper terms 1 combinator
- A Fei's expectation
- “用Android复刻Apple产品UI”(2)——丝滑的AppStore卡片转场动画
- 软件逆向破解入门系列(1)—xdbg32/64的常见配置及功能窗口
- Intelij idea efficient skills (III)
- 软件安装信息、系统服务在注册表中的位置
- Semi supervised learning
猜你喜欢
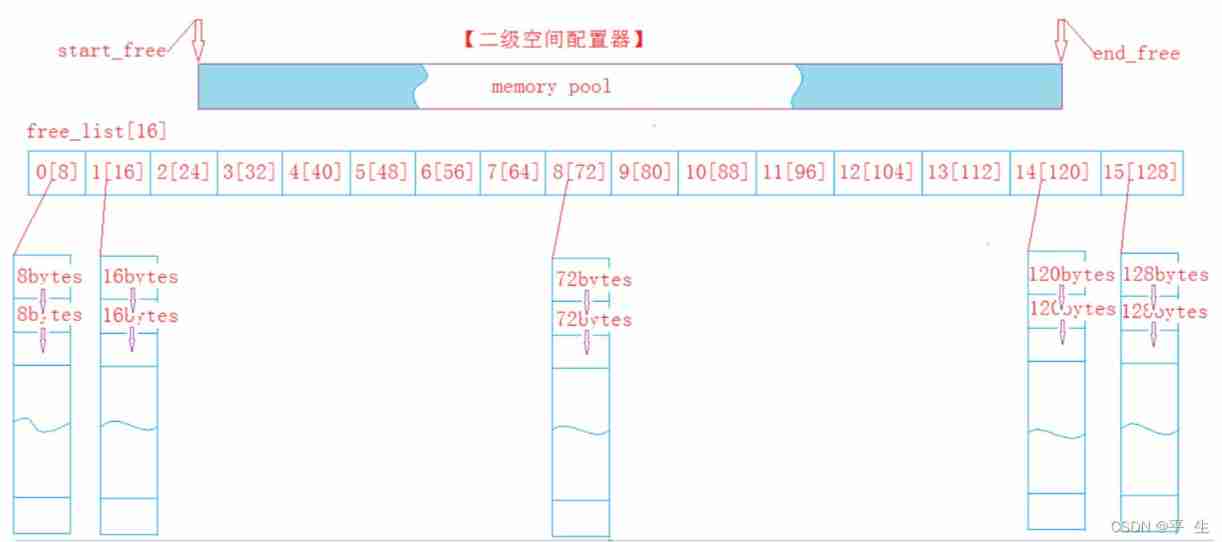
Project -- high concurrency memory pool

找映射关系
Colab works with Google cloud disk
![App mobile terminal test [4] APK operation](/img/f1/4bff6e66b77d0f867bf7237019e982.png)
App mobile terminal test [4] APK operation
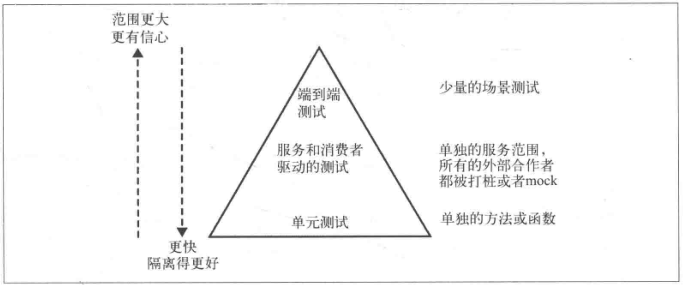
《微服务设计》读书笔记(下)

Brush questions -- sword finger offer

From the 18th line to the first line, the new story of the network security industry

关于网页中的文本选择以及统计选中文本长度

Nifi from introduction to practice (nanny level tutorial) - flow
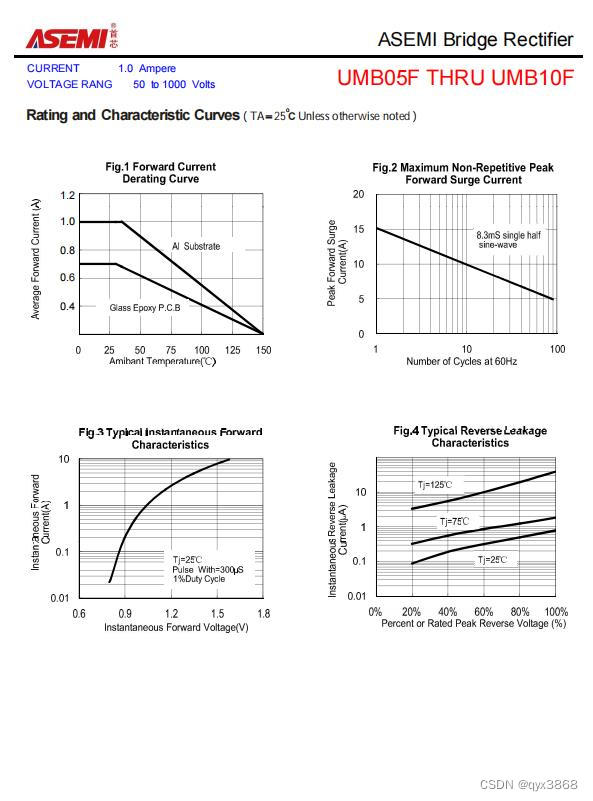
Asemi rectifier bridge umb10f parameters, umb10f specifications, umb10f package
随机推荐
Go语言自学系列 | golang中的if else语句
CString中使用百分号
A Fei's expectation
Microservice API gateway
Detailed explanation of string function and string function with unlimited length
Nine ways to define methods in scala- Nine ways to define a method in Scala?
阿飞的期望
Nifi from introduction to practice (nanny level tutorial) - flow
Detailed explanation of four modes of distributed transaction (Seata)
[redis foundation] understand redis persistence mechanism together (rdb+aof graphic explanation)
Jmeter线程组功能介绍
Unity功能——Unity离线文档下载及使用
初试scikit-learn库
Popular understanding of random forest
【OpenCV 例程200篇】217. 鼠标交互获取多边形区域(ROI)
Break through 1million, sword finger 2million!
How to thicken the brush in the graphical interface
Calibre LVL
Pyinstaller is not an internal or external command, nor is it a runnable program or batch file
Mongodb installation and basic operation