当前位置:网站首页>[ManageEngine] the role of IP address scanning
[ManageEngine] the role of IP address scanning
2022-07-03 12:27:00 【ManageEngine Zhuohao】
IP Address scanning is an indispensable technology in today's intelligent era , It improves the security of the Internet , It has also led to the improvement of the quality of life in today's society , Simplify the process , Improve life efficiency , Shaped a convenient lifestyle .
IP The purpose of address scanning
- adopt IP Address scanning can ensure IP Consistency and accuracy of address . In this way, managers can master IP Real time status of resources .
- adopt IP Address scanning can get comprehensive information about device network , Use IP Address scanning software can know who is using address space , You can track in this way IP Address learned IP Address availability and related operations .
- Optimize IP The segmentation of space improves the performance of the network . Use IP Address scanner It can simplify the scanning process and scan multiple subnetworks at the same time . And can view the utilization efficiency of the sub network to obtain a comprehensive summary . It can better provide you with the basis for planning the network structure, so as to prevent the overall network resource depletion caused by the excessive utilization of the network from the side .
- Change dynamic network , Thus to IP Use dynamic allocation . But this has high requirements and must be right IP The status is strictly scanned and monitored , And reasonably plan the network to avoid IP Address resource exhaustion .
IP Advantages of address scanning
High safety
On the market IP Address scanning software has been developed IP Address hopping technology , This is a typical network layer MTD , Can randomly change the host IP Address , Interfere with the attacker's judgment , The attacker cannot scan and invade the target . IP Address is one of the necessary factors for attackers to implement remote network attacks , If you can't get the attack target IP Address , Port scanning cannot be implemented 、 Vulnerability scanning and exploit vulnerabilities . Although it can't completely isolate the attacker's attack , But to a certain extent, it can improve the security of the host , Interfere with attackers .
Flexibility
IP Address scanning can periodically send a random virtual IP The address is assigned to the host , But the actual address of the host does not change . It can be randomly generated synchronously with the password of the host , And USES the DNS Get the currently assigned address , At the same time, the random fingerprint mechanism is also used , Intercept the host response and modify it transparently .
Good compatibility
Various types IP Address scanning mechanisms need to ensure normal network communication , Therefore, a synchronization mechanism is needed to enable the normal legitimate communicators on the network to obtain the dynamics of the hopping party in time IP Address . Some mechanisms employ DNS Mechanism , Some make full use of SDN technology 、 Hypervisor Layer components, etc ; Some require the participation and synchronization of relevant components at the host level , Some only need a gateway 、 Network equipment and other components participate in synchronization , Transparent to upper application software .
IP Address scanning method
IP Address scanning provides the function of device remote control , It is an indispensable means in today's intelligent era . that ,IP What are the address scanning methods ?
Inquire through computer commands
IP Address scanning , It should be input on the computer cmd command , Query the devices in the LAN IP. The specific operation is : In the start menu of the computer , Click on [ function ], Input cmd enter , Enter... In the pop-up command prompt window ipconfig / all enter , You can see the IP 、 gateway 、mac Address and other information . Then enter arp - a , Enter , Just wait for the result to return .
Use IP Address scanning tool
Conduct IP Address scanning , Users can download LAN on the Internet IP Scan tool , After the computer is installed, you can query and scan , Realize the search on the central line of the LAN , You can get the detailed information of the corresponding host directly , Such as : Computer name 、 IP domain name , MAC 、 Network card properties, etc , stay IP Address scanning tool , You can also export information . If you use cmd Commands and scanning tools scan the LAN IP, It is the way of active query and access , The terminal needs to reply to the command .
Log in to the switch
To carry out IP Address scanning , You can log in to the switch to check arp Information , This is that each terminal must set a gateway address to access the Internet , Is a data forwarding , The phase of the terminal is recorded arp Information , Take Huawei switches as an example : telnent Landing switch , Enter the command " display arp ", You can view the relevant network segments of the LAN IP Address .
IP The role of address scanning
Check the usage of network resources
IP Address scanning and updating can be found through relevant investigations IP Allocation can be achieved with overall consistency , At the same time, we can have a deep understanding of the application details of the Internet with the help of scanning technology , In this way, the optimized allocation of network data resources and management resources can be realized faster , A series of methods such as reservation allocation can be adopted IP Scanning technology to know in advance how the business network is , In this way, specific goals can be achieved , Achieve the allocation of data resources in real time , It can also make the utilization rate of the network higher .
Optimize space segmentation
Scanning tools can quickly monitor network usage and scan network usage , And use tracking and recording methods to achieve a new understanding of the application of this technology , The use space of the network can be greatly improved , Both efficiency and speed can reach a new level , Connect complex network systems , It can improve the distribution capacity , And other network data can also achieve deep improvement in utilization , Through the processing of scanning technology , Reduce the consumption of resources to a very low level .
IP Address scanner
Zhuohao OpUtils It is a comprehensive network management tool set , It provides the commonly used by network and system administrators 30 A variety of tools , Include IP Address management 、 Switch port management 、 External equipment monitoring 、 Configuration file backup 、 Bandwidth monitoring 、 Equipment monitoring, etc .
边栏推荐
- 20. Valid brackets
- 1-1 token
- 111. Minimum depth of binary tree
- Is it safe to open an account for online stock speculation? Who can answer
- 01_ Using the concurrent tool class library, is thread safety safe
- [combinatorics] permutation and combination (example of permutation and combination)
- Official website of Unicode query
- 手机号码变成空号导致亚马逊账号登陆两步验证失败的恢复网址及方法
- Fundamentals of concurrent programming (III)
- TOGAF认证自学宝典V2.0
猜你喜欢
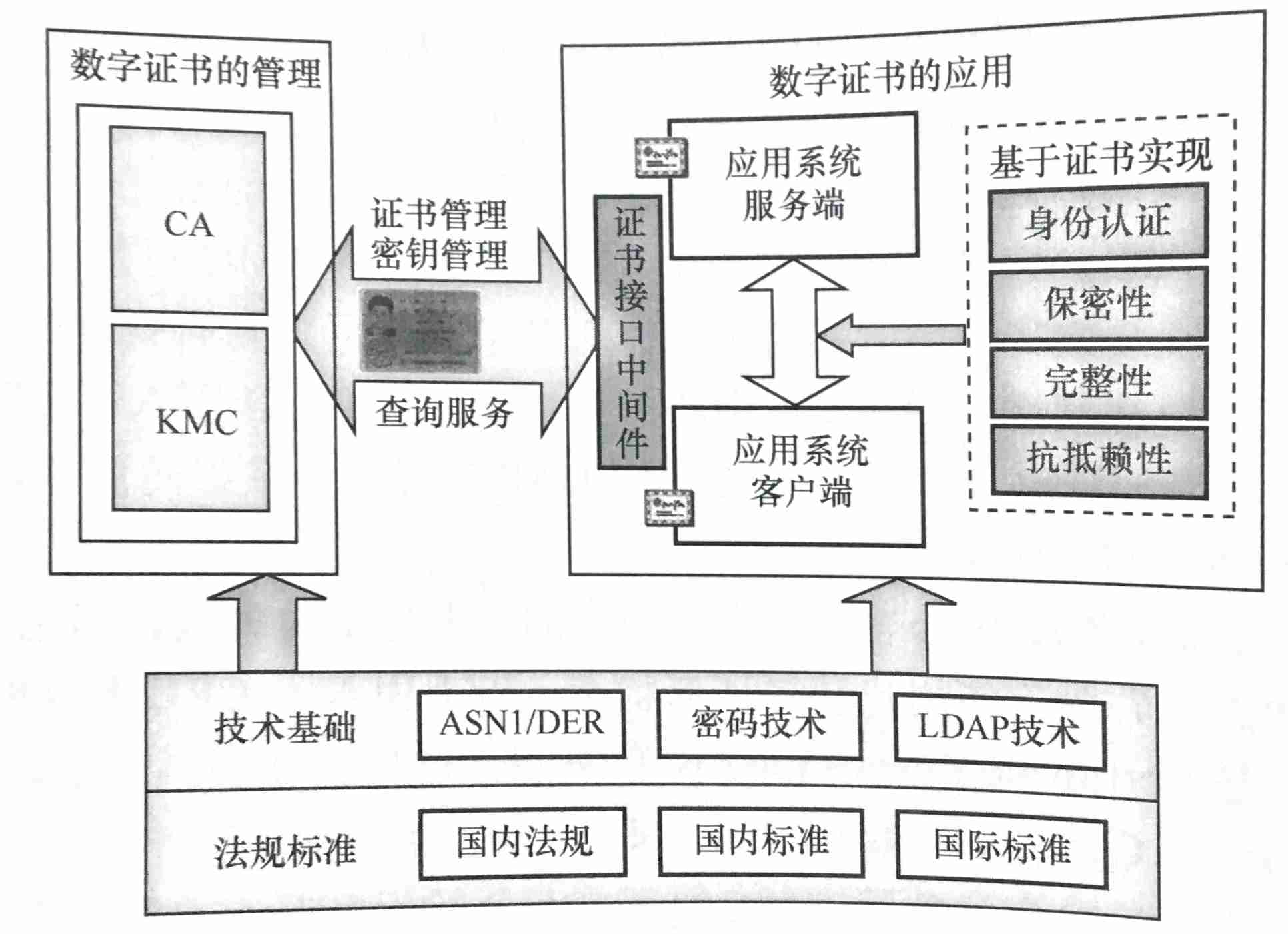
Pki/ca and digital certificate

laravel 时区问题timezone
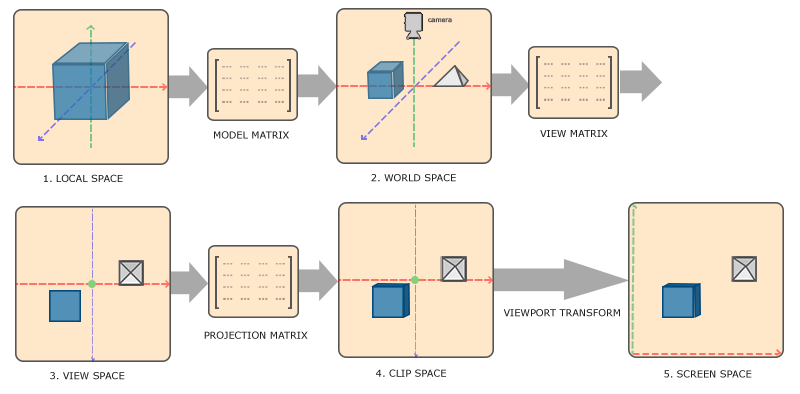
Basic knowledge of OpenGL (sort it out according to your own understanding)
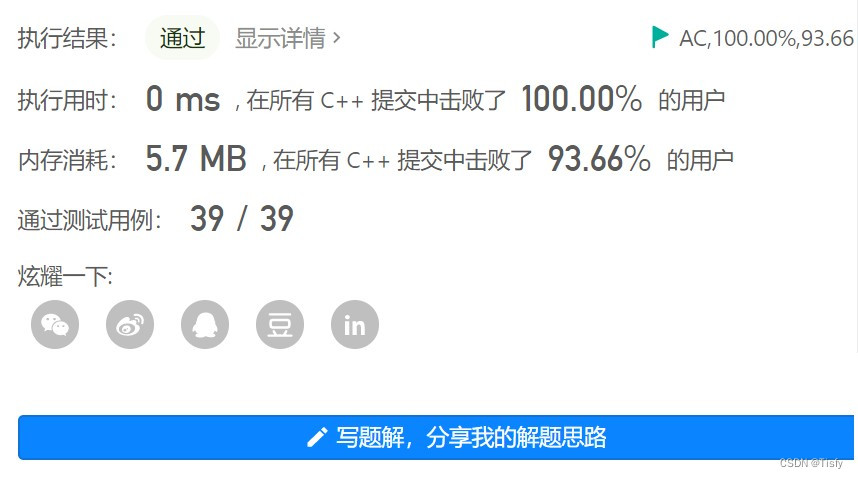
LeetCode 0556.下一个更大元素 III - 4步讲完

(构造笔记)ADT与OOP

Qt+vtk+occt reading iges/step model
ES6新特性

雲計算未來 — 雲原生
win10 上PHP artisan storage:link 出现 symlink (): Protocol error的解决办法

网络通讯之Socket-Tcp(一)
随机推荐
02_ Lock the code, and don't let the "lock" become a worry
[combinatorics] permutation and combination (example of permutation and combination)
Dart: self study system
MySQL time zone solution
Self made pop-up input box, input text, and click to complete the event.
Lambda expression
(构造笔记)ADT与OOP
Adult adult adult
Jsup crawls Baidu Encyclopedia
Official website of Unicode query
elastic_ L04_ introduction. md
2020-10_ Development experience set
[embedded] - Introduction to four memory areas
Use of atomicinteger
Dart: about Libraries
Recovery of website address and method of Amazon account login two-step verification failure caused by mobile phone number becoming empty
[learning notes] DP status and transfer
Php Export word method (One MHT)
SLF4J 日志门面
C language improvement article (wchar_t) character type