当前位置:网站首页>Process of manually encrypting and burning the mass production firmware of ESP equipment
Process of manually encrypting and burning the mass production firmware of ESP equipment
2022-06-13 11:33:00 【25March】
Requirements are as follows :
Want to encrypt the mass production firmware , After encryption, tools can be used to erase the old firmware , Supports repeated firmware burning .
The tools needed :
- esptool , May refer to “esptool.py Introduction and use ”
- Flash Download tool
Reference documents :
Solution :
Appoint Flash Encryption key (
key.bin), That is, each module uses the same Flash Encryption key (key.bin). First compile the project into a separate binary plaintext firmware Use Flash Encryption key (key.bin) To encrypt ; Then you can use Flash Download tool Burning encrypted ciphertext firmware . After the ciphertext firmware is burned , Need to use esptool hold Flash Encryption key (key.bin) Burn to Efuse And open Efuse Medium Flash The encrypted control bit enables the encrypted firmware to run normally . Steps are as follows :*
1 Use esptool Tools , Generate... For mass production firmware Flash Encryption key (key.bin) , For example, the generated encryption key is key.bin :
espsecure.py generate_flash_encryption_key key.bin
2 For each firmware to be mass produced and burned ( bin file ) To encrypt , With hello-world Routine as an example
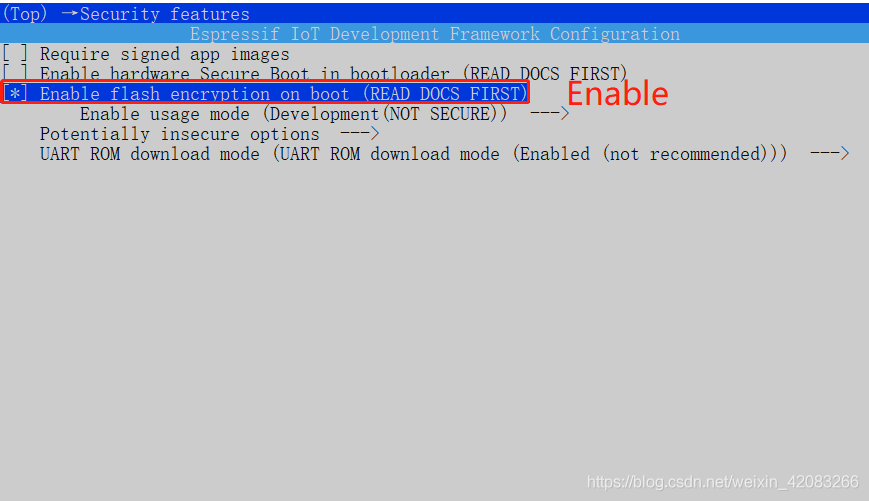
- Need to be in menuconfig In the open Flash Encryption options , as follows :
menuconfig -> Security features -> Enable flash encryption on boot
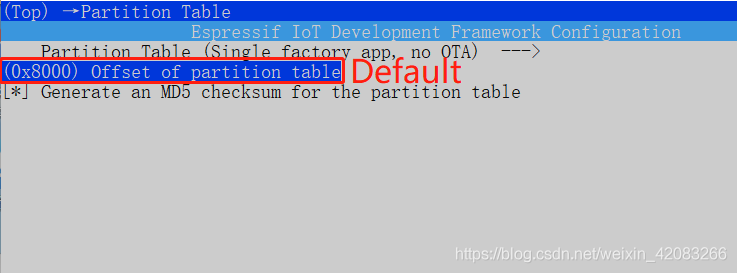
- because Flash Encryption will increase bootloader.bin Size of firmware , So you need to adjust the offset of the default partition table , The default is 0x8000 , Adjustable to 0xa000 . Can be found in menuconfig Revision in China partition_table Set up . as follows :
menuconfig -> Partition Table -> Offset of partition table
- Then compile the project , View the firmware download address corresponding to the compiled firmware . You can see hello-world.bin The download address of became 0x20000
Project build complete. To flash, run this command:
E:\.espressif\python_env\idf4.3_py3.8_env\Scripts\python.exe ..\..\..\components\esptool_py\esptool\esptool.py -p (PORT) -b 460800 --before default_reset --after no_reset --chip esp32c3 write_flash --flash_mode dio --flash_size detect --flash_freq 80m 0x0 build\bootloader\bootloader.bin 0xa000 build\partition_table\partition-table.bin 0x20000 build\hello-world.bin
or run 'idf.py -p (PORT) flash'
3 then , Use generated Flash Encryption key ( key.bin file ) For each independent firmware after project compilation ( bin file ) To encrypt . as follows :
- Use generated Flash Encryption key (
key.bin) Yes bootloader.bin To encrypt , Encrypted bootloader.bin by key_bootloader.bin
espsecure.py encrypt_flash_data --keyfile key.bin --address 0x1000 -o key_bootloader.bin build/bootloader/bootloader.bin
- Use generated Flash Encryption key (
key.bin) Yes partition-table.bin To encrypt , Encrypted partition-table.bin by key_partition-table.bin
espsecure.py encrypt_flash_data --keyfile key.bin --address 0xa000 -o key_partition-table.bin build/partition_table/partition-table.bin
- Use generated Flash Encryption key (
key.bin) Yes hello_world.bin To encrypt , Encrypted hello-world.bin by key_hello-world.bin
espsecure.py encrypt_flash_data --keyfile key.bin --address 0x20000 -o key_hello-world.bin build/hello_world.bin
4 The corresponding download address of the firmware generated according to the project compilation , Burning encrypted firmware ( Encrypted bin file ), Use the following esptool Tools to download encrypted firmware :
esptool.py -b 460800 --before default_reset --after no_reset --chip esp32 write_flash --flash_mode dio --flash_size detect --flash_freq 40m 0x1000 key_bootloader.bin 0xa000 key_partition-table.bin 0x20000 key_hello-world.bin
Be careful :
This step of downloading encrypted firmware can also be used directly Flash Download tool To download , as follows :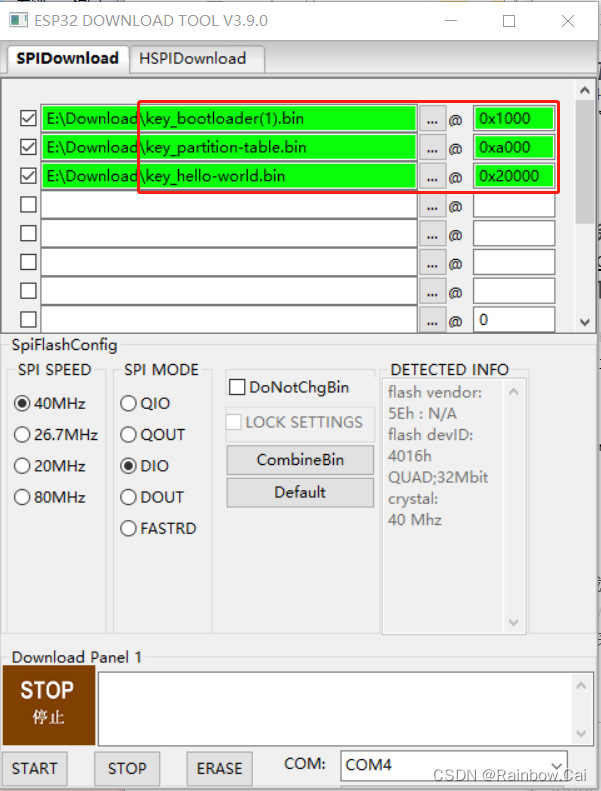
5 take Flash Encryption key (key.bin) Burn to Efuse in :
espefuse.py burn_key flash_encryption key.bin
6 Use esptool Tool on Efuse Medium Flash Encrypted control bit :
espefuse.py burn_efuse FLASH_CRYPT_CONFIG 0xF FLASH_CRYPT_CNT 1
explain :
- if Efuse No write in Flash Encryption key (
key.bin) And on Efuse Medium Flash Encrypted control bit , The encrypted... Cannot be run normally “ The firmware ”( bin file ). - Module on Flash After encryption , Can't use Flash Download tool To re burn firmware and erase firmware , But it supports the use of esptool Tools to re burn firmware and erase firmware .
- Yes Flash The encrypted module rebuilds the firmware , The re fired firmware is required to be in menuconfig In the open
”Flash encryption “And use the same encryption key as the old firmware (key.bin) To encrypt and then burn , In this way, the firmware after reburning can operate normally . - Efuse The encryption key cannot be erased , Therefore, the new key cannot be re burned .
- This solution can be used after the module mass production firmware is encrypted esptool Tools to modify the module
Reburning firmware 、 erase 、 read FlashThe operation of , But the firmware read out is encrypted firmware . If the new module does not burn the key corresponding to the encrypted firmware (key.bin) Words , Just burning the read encrypted firmware to a new module will not work properly .
边栏推荐
- VSCode 如何将已编辑好的文件中的 tab 键转换成空格键
- ARM64 上的性能怪兽:API 网关 Apache APISIX 在 AWS Graviton3 上的安装和性能测试
- [tcapulusdb knowledge base] tcapulusdb doc acceptance - table creation approval introduction
- The leader said he would go online tomorrow, but he didn't know the development process at all
- 【TcaplusDB知识库】TcaplusDB单据受理-建表审批介绍
- ARM64 上的性能怪兽:API 网关 Apache APISIX 在 AWS Graviton3 上的安装和性能测试
- [tcapulusdb knowledge base] Introduction to tcapulusdb general documents
- Web 3.0?高成本版的P2P而已
- We spent a weekend migrating 3.7 million lines of code to typescript
- Ue5 random point in bounding boxf from stream
猜你喜欢
![[tcapulusdb knowledge base] tcapulusdb doc acceptance - Introduction to creating game area](/img/b7/2358e8cf1cdaeaba77e52d04cc74d4.png)
[tcapulusdb knowledge base] tcapulusdb doc acceptance - Introduction to creating game area

我是如何解决码云图床失效问题?

【TcaplusDB知识库】TcaplusDB单据受理-创建业务介绍

Nim game ladder Nim game and SG function application (set game)
Performance monster on arm64: installation and performance test of API gateway Apache APIs IX on AWS graviton3

【TcaplusDB知识库】Tmonitor单机安装指引介绍(一)

2021CCPC网络赛题解加总结
![[ROS] moveit rviz seven DOF Manipulator Simulation](/img/e6/4000ffa06a5c538b30faed33b6c0a2.png)
[ROS] moveit rviz seven DOF Manipulator Simulation

Discord机器人开发

About SAP Spartacus cmsservice Possible optimization ideas for getcomponentdata
随机推荐
【TcaplusDB知识库】Tmonitor单机安装指引介绍(一)
MFC自定义button实现颜色控制
Ue5 small knowledge points geometry script modeling
Nim游戏阶梯 Nim游戏和SG函数应用(集合游戏)
Multiplicative inverse action
Vivo large scale kubernetes cluster automation operation and maintenance practice
fastapi 如何响应文件下载
(幼升小信息-03)批量模板制作 幼儿基本信息收集文件夹(包含PDF、Word、证件文件夹)
[tcapulusdb knowledge base] Introduction to tmonitor background one click installation (I)
状态压缩DP例题(旅行商问题和填矩形问题)
【TcaplusDB知识库】TcaplusDB常规单据介绍
抖音如此重视直播销售外卖套餐,会不会是创业者巨大机会?
Navicat connection MySQL in Pagoda
银行业务系统数据库设计与实现
Anonymity in Web3 and NFT
Analysis and summary of 2021ccpc online games
Go needs to add an arrow syntax, which is more like PHP!
Pagoda add a website: PHP project
Model building process 1==miidock
[tcapulusdb knowledge base] Introduction to new models of tcapulusdb