当前位置:网站首页>Formal analysis of Woo Lam protocol with scyther tool
Formal analysis of Woo Lam protocol with scyther tool
2022-06-12 13:38:00 【Qinglan drinking boat】
Scyther Tools for formal analysis Woo-Lam agreement
Scyther
Scyther Formal analysis tools can formally describe the protocol , Verify whether there is a security threat to the confidentiality and authentication of the protocol . During the attack, it supports unlimited number of sessions , It supports both strong security model and Delov-Yao Model . In terms of protocol algorithms to be formally analyzed, it does not support the inclusion of “”XOR“” Properties of operational algebra and “”DH“” The properties of algebraic operations and the protocols of algebraic properties containing bilinear pairs . Similar formal protocol analysis tools include SPIN,CPN Tools,Tamarin etc. .
One . Scyther
Scyther-Compromise The state space display used is similar to the search algorithm ,Scyther-Compromise stay Scyther Add the option of strong security module on the basis of , This increases the search time , and Tamarin Is in Scyther Based on , Use Scyther Inverse algorithm of . The other thing is Scyther-Compromise and Tamarin Tools not only support Dolev-Yao Model , And support eCK Equal strength security model .
Two . Woo-Lam agreement

The figure above shows Woo-Lam Protocol message flow diagram .
3、 ... and . Formal modeling analysis
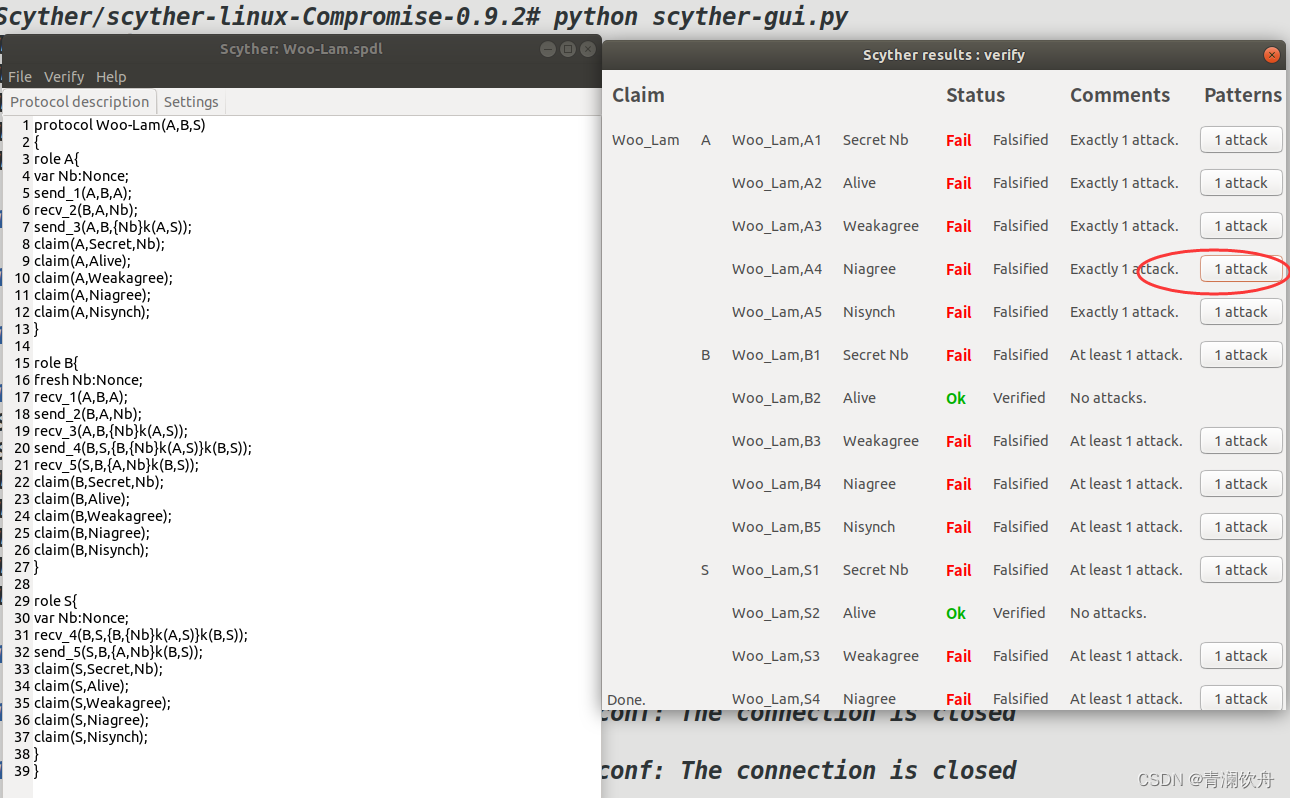
protocol Woo-Lam(A,B,S)
{
role A{
var Nb:Nonce;
send_1(A,B,A);
recv_2(B,A,Nb);
send_3(A,B,{Nb}k(A,S));
claim(A,Secret,Nb);
claim(A,Alive);
claim(A,Weakagree);
claim(A,Niagree);
claim(A,Nisynch);
}
role B{
fresh Nb:Nonce;
recv_1(A,B,A);
send_2(B,A,Nb);
recv_3(A,B,{Nb}k(A,S));
send_4(B,S,{B,{Nb}k(A,S)}k(B,S));
recv_5(S,B,{A,Nb}k(B,S));
claim(B,Secret,Nb);
claim(B,Alive);
claim(B,Weakagree);
claim(B,Niagree);
claim(B,Nisynch);
}
role S{
var Nb:Nonce;
recv_4(B,S,{B,{Nb}k(A,S)}k(B,S));
send_5(S,B,{A,Nb}k(B,S));
claim(S,Secret,Nb);
claim(S,Alive);
claim(S,Weakagree);
claim(S,Niagree);
claim(S,Nisynch);
}
}

You can try it if you like
This is the official account of Xiaobian. , Please move your lovely little hand , Pay attention to it. 
边栏推荐
- [cloud native | kubernetes] in depth understanding of deployment (VIII)
- Computational hierarchy -- the problem of large numbers multiplying decimals
- Possible solutions to problems after CodeBlocks installation
- Wechat web developer tools tutorial, web development issues
- "Non" reliability of TCP
- 高通平台开发系列讲解(协议篇)QMI简单介绍及使用方法
- 开发中使用的语言技巧
- 单向环形链表实现约瑟夫环
- Tinyxml Usage Summary
- C language [23] classic interview questions [2]
猜你喜欢
![2061: [example 1.2] trapezoidal area](/img/83/79b73ca10615c852768aba8d2a5049.jpg)
2061: [example 1.2] trapezoidal area

Title: Yanghui triangle

Octopus network progress monthly report | may 1-May 31, 2022

There was an error installing mysql. Follow the link below to CMD

C#DBHelper_ FactoryDB_ GetConn

How to solve the problem of data table query error when SQLite writes the registration function?
VGA display color bar and picture (FPGA)

Application of binary search -- finding the square root sqrt of a number
![[wechat applet development] Part 1: development tool installation and program configuration](/img/a8/f4dcbde295ba7cf738d878464b3af0.png)
[wechat applet development] Part 1: development tool installation and program configuration

Script import CDN link prompt net:: err_ FILE_ NOT_ Found problem
随机推荐
Codeforces 1637 A. sorting parts - simple thinking
view的子视图的递归
Implementing pytorch style deep learning framework similartorch with numpy
1001:Hello,World
【刷题篇】抽牌获胜的概率
TCP的“非”可靠性
创新实训(十)高级界面美化
Implementing tensorflow deep learning framework similarflow with numpy
It is enough to read this article. Web Chinese development
软件构造 03 正则表达式
"New continent" of mobile application going to sea
2063: [example 1.4] cattle eat grass
AWLive 结构体的使用
达梦数据库DM8 windows环境安装
Pytorch framework
创新实训(十一)开发过程中的一些bug汇总
Multi source BFS problem template (with questions)
Possible solutions to problems after CodeBlocks installation
static 和 extern 关键字详解
2061: [example 1.2] trapezoidal area
