当前位置:网站首页>The real situation of programmers
The real situation of programmers
2022-07-05 21:52:00 【Blue bridge cloud class】
lately , I saw such a question in brush :
Why do programmers write all the time bug , Can't you write it all at once ?
I have question marks all over my face , Why is there such a problem ? See this problem , I just want to ask these questions ( I'm sorry , etc Automatically raise the bar ):
- Why should I always write with the wrong eraser / Transparent adhesive , Can't it be one-time ?
- Why should people often eat , Can't you eat enough at one time ?
- Why do lovers break up , Can't you fall in love and get married directly ?
- ……
In fact, people write bug It is inevitable , After all, no one is perfect , There will always be times when you don't pay attention , Even high-level programmers can't avoid , For example, the loophole that has been highly discussed before ——Apache Log4j 2 Remote code execution vulnerability .
It's just that there are bug deadly , yes , we have bug The harm is small !
here , I can't help but want to share this programmer part “ Ruin the future ” The story of ( As a Entertainment , Do not imitate ! The content comes from : Brush bearded guest ).
Accident one
After graduation, I went directly to work for an operator , One day I took a task , Ask to write a code for sending group notification messages . The brain short circuit didn't change the code that day , Connected to the production environment, directly roll , Code cycle all mobile phone numbers within the operator to send the latest promotional activities .
code → test → Be finished , It's written in a dead cycle . Stop the program in time after finding the problem , Sent a thousand text messages to the first number in the database .
The next day I lost my job .
Accident two
Entered a smart card business company to develop canteen smart card , Code tests are normal
That is, the concurrent bearing capacity is general , But it's OK to brush four or five strokes at the same time .
In the spirit of pragmatism 、 Performance doesn't matter. Just use it , And consulted the canteen , Full of confidence, it was distributed to a university canteen for direct use .
The next day I lost my job , Because the students found that after eating in the canteen and brushing a certain number of pens , Eating suddenly cost nothing .
After watching these two accidents , Are you eating melons ? therefore ,bug Although danger requires caution , But not necessarily 100% Avoided , Let alone just out of society 、 Fresh graduates without practical project experience .
We see bug Will be angry , Some people will complain “ Who wrote this ”, What a coincidence , Write this bug People are themselves , A clown is himself .

These pictures , It also perfectly demonstrates the programmer's discovery bug The state of mind ( Scalp tingling ):







Now , I have to mention it again Apache Log4j 2 Remote code execution vulnerability .
The hole in 2021 year 12 month 10 It was made public , Let many safety engineers 、 Safety manufacturer 、 The security personnel of all enterprises can't sleep , Enter at once “ Combat Defense status ”.
Blue bridge cloud class has reproduced this vulnerability for free , Introduce the principle of this vulnerability 、 Utilization mode 、 Excavation method and repair method . This experiment provides a hands-on online experimental environment , Understand the loopholes more deeply .
If you want to understand Apache Log4j 2 Remote code execution vulnerability , Study for free ~
Apache Log4j 2 Detailed explanation of Remote Code Execution Vulnerability
边栏推荐
- 张丽俊:穿透不确定性要靠四个“不变”
- Robot operation mechanism
- Feng Tang's "spring breeze is not as good as you" digital collection, logged into xirang on July 8!
- Interviewer: will concurrent programming practice meet? (detailed explanation of thread control operation)
- Three components of openpyxl
- K210学习笔记(四) K210同时运行多个模型
- KingbaseES V8R3集群维护案例之---在线添加备库管理节点
- Reptile practice
- 思特奇加入openGauss开源社区,共同推动数据库产业生态发展
- Li Kou ----- the maximum profit of operating Ferris wheel
猜你喜欢

Experienced inductance manufacturers tell you what makes the inductance noisy. Inductance noise is a common inductance fault. If the used inductance makes noise, you don't have to worry. You just need
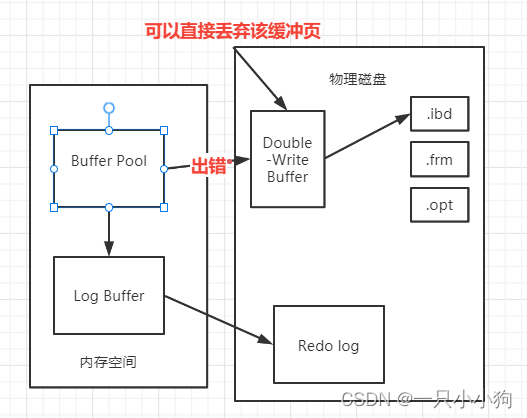
MySQL InnoDB Architecture Principle
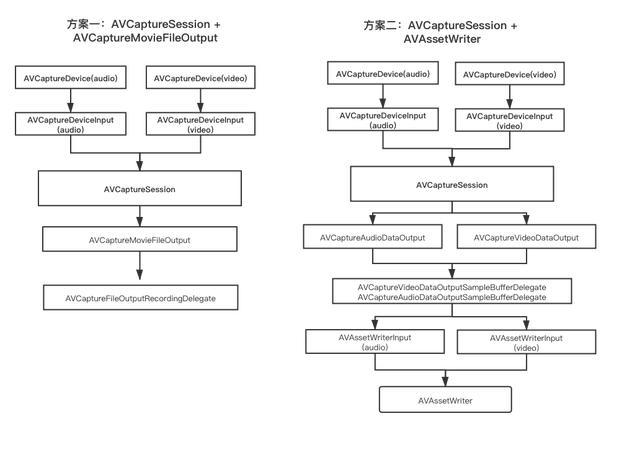
Two ways to realize video recording based on avfoundation
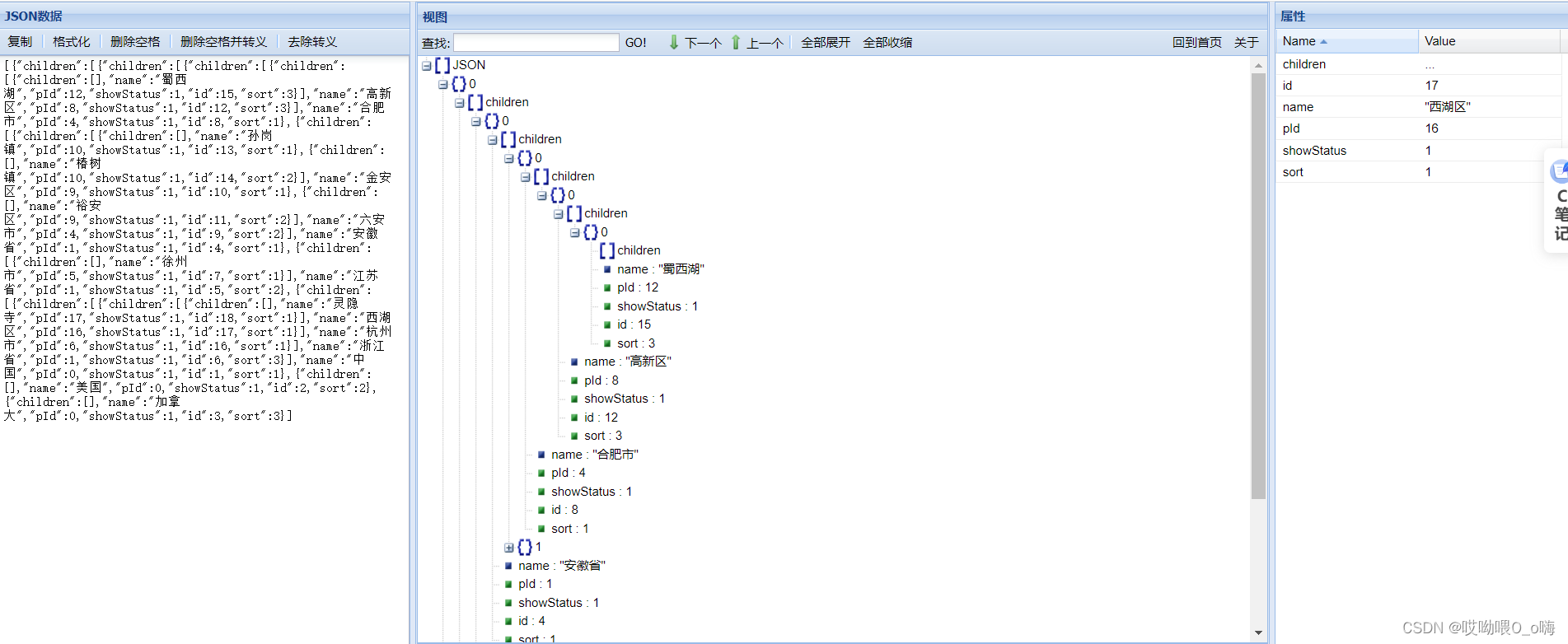
Recursive query of multi-level menu data
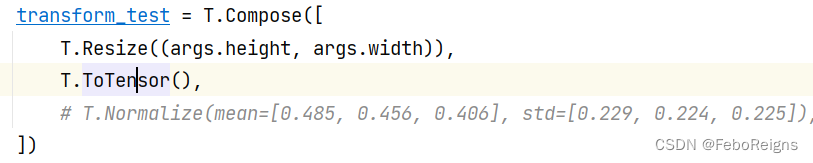
Teach yourself to train pytorch model to Caffe (III)
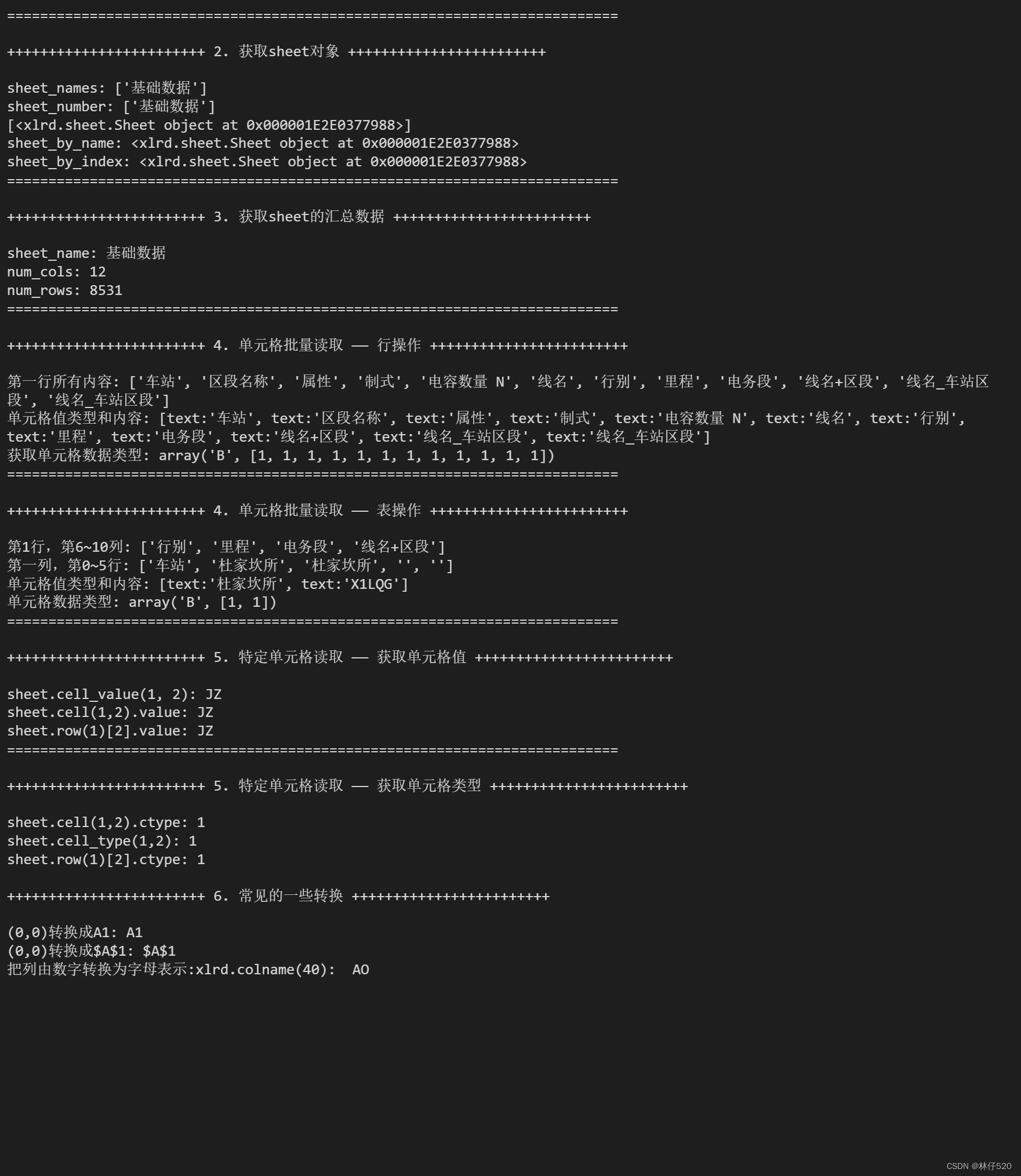
Xlrd common operations
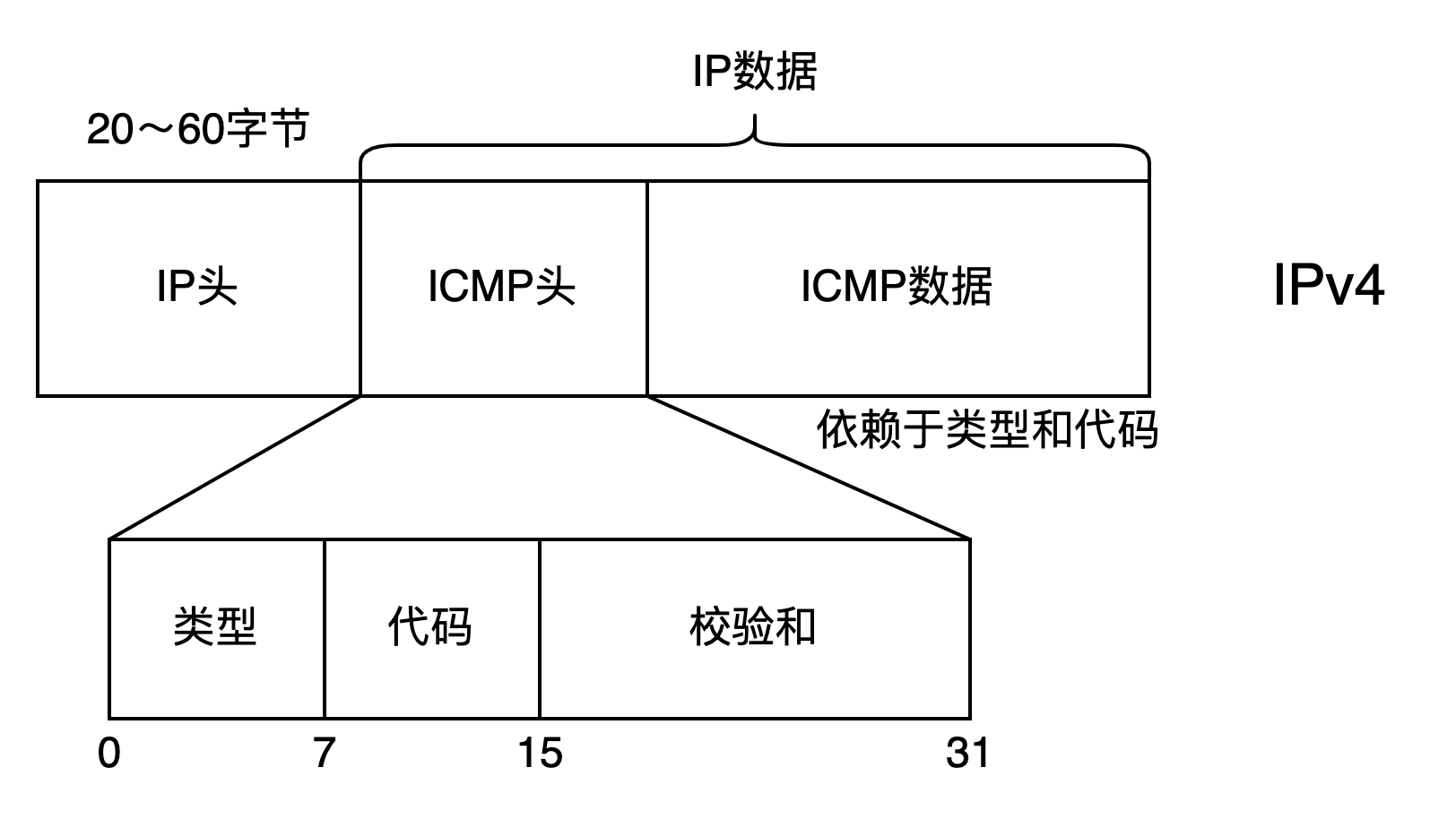
ICMP 介绍

张丽俊:穿透不确定性要靠四个“不变”

How to use tensorflow2 for cat and dog classification and recognition
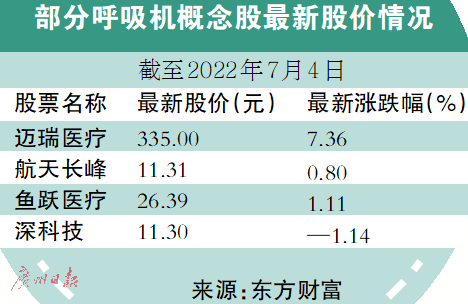
多家呼吸机巨头产品近期被一级召回 呼吸机市场仍在增量竞争
随机推荐
The primary key is set after the table is created, but auto increment is not set
Emotional analysis of wechat chat records on Valentine's day based on Text Mining
Poj3414广泛搜索
Parker驱动器维修COMPAX控制器维修CPX0200H
怎么利用Tensorflow2进行猫狗分类识别
大约SQL现场“这包括”与“包括在”字符串的写法
854. 相似度为 K 的字符串 BFS
SQL common syntax records
Ethereum ETH的奖励机制
Chap2 steps into the palace of R language
Summary of El and JSTL precautions
Teach yourself to train pytorch model to Caffe (I)
SQL knowledge leak detection
ICMP 介绍
Teach yourself to train pytorch model to Caffe (2)
Matlab | app designer · I used Matlab to make a real-time editor of latex formula
MySQL InnoDB Architecture Principle
Summarize the reasons for 2XX, 3xx, 4xx, 5xx status codes
Two ways to realize video recording based on avfoundation
Hysbz 2243 staining (tree chain splitting)