当前位置:网站首页>The 29th day of force deduction (DP topic)
The 29th day of force deduction (DP topic)
2022-07-03 20:01:00 【NP_ hard】
List of articles
problem Ⅰ
509. Fibonacci Number
The Fibonacci numbers, commonly denoted F(n) form a sequence, called the Fibonacci sequence, such that each number is the sum of the two preceding ones, starting from 0 and 1. That is,
F(0) = 0, F(1) = 1
F(n) = F(n - 1) + F(n - 2), for n > 1.
Given n, calculate F(n).
Example 1:
Input: n = 2
Output: 1
Explanation: F(2) = F(1) + F(0) = 1 + 0 = 1.
Example 2:
Input: n = 3
Output: 2
Explanation: F(3) = F(2) + F(1) = 1 + 1 = 2.
Example 3:
Input: n = 4
Output: 3
Explanation: F(4) = F(3) + F(2) = 2 + 1 = 3.
solution DP
class Solution {
public:
int fib(int n) {
if(!n)return 0;
if(n==1)return 1;
int st = 0, nd = 1;
n--;
while(n--){
int tmp = nd;
nd = st + nd;
st = tmp;
}
return nd;
}
};

NOTE:
this probem’s difficulty is easy, my solution use two temporary variables to store the status of DP
problem Ⅱ
1137. N-th Tribonacci Number
The Tribonacci sequence Tn is defined as follows:
T0 = 0, T1 = 1, T2 = 1, and Tn+3 = Tn + Tn+1 + Tn+2 for n >= 0.
Given n, return the value of Tn.
Example 1:
Input: n = 4
Output: 4
Explanation:
T_3 = 0 + 1 + 1 = 2
T_4 = 1 + 1 + 2 = 4
Example 2:
Input: n = 25
Output: 1389537
solution 1 DP
class Solution {
public:
int tribonacci(int n) {
if(!n)return 0;
if(n==1 || n==2)return 1;
int st=0, nd=1, rd=1;
n -= 2;
while(n--){
int sum = st+nd+rd;
st = nd;
nd = rd;
rd = sum;
}
return rd;
}
};
solution 2 short code
class Solution {
public:
int tribonacci(int n) {
int dp[3] = {
0, 1, 1};
for(int i=3; i<=n; ++i)
dp[i%3] += dp[(i+1)%3] + dp[(i+2)%3];
return dp[n%3];
}
};

problem Ⅲ
746. Min Cost Climbing Stairs
You are given an integer array cost where cost[i] is the cost of ith step on a staircase. Once you pay the cost, you can either climb one or two steps.
You can either start from the step with index 0, or the step with index 1.
Return the minimum cost to reach the top of the floor.
Example 1:
Input: cost = [10,15,20]
Output: 15
Explanation: You will start at index 1.
- Pay 15 and climb two steps to reach the top.
The total cost is 15.
Example 2:
Input: cost = [1,100,1,1,1,100,1,1,100,1]
Output: 6
Explanation: You will start at index 0.
- Pay 1 and climb two steps to reach index 2.
- Pay 1 and climb two steps to reach index 4.
- Pay 1 and climb two steps to reach index 6.
- Pay 1 and climb one step to reach index 7.
- Pay 1 and climb two steps to reach index 9.
- Pay 1 and climb one step to reach the top.
The total cost is 6.
solution
class Solution {
public:
int minCostClimbingStairs(vector<int>& cost) {
int n = cost.size();
for(int i=2; i<n; i++)
cost[i] += min(cost[i-1], cost[i-2]);
return min(cost[n-1], cost[n-2]);
}
};

边栏推荐
- What is the difference between a kill process and a close process- What are the differences between kill process and close process?
- February 14-20, 2022 (osgear source code debugging +ue4 video +ogremain source code transcription)
- Rd file name conflict when extending a S4 method of some other package
- 10 smart contract developer tools that miss and lose
- QT tutorial: signal and slot mechanism
- Global and Chinese market of micro positioning technology 2022-2028: Research Report on technology, participants, trends, market size and share
- Global and Chinese market of electrolyte analyzers 2022-2028: Research Report on technology, participants, trends, market size and share
- Don't be afraid of no foundation. Zero foundation doesn't need any technology to reinstall the computer system
- Class loading process
- Rad+xray vulnerability scanning tool
猜你喜欢
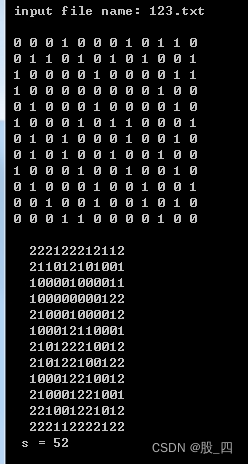
Chapter 1: sum of three factorials, graph point scanning

How to improve data security by renting servers in Hong Kong

Chapter 1: seek common? Decimal and S (D, n)
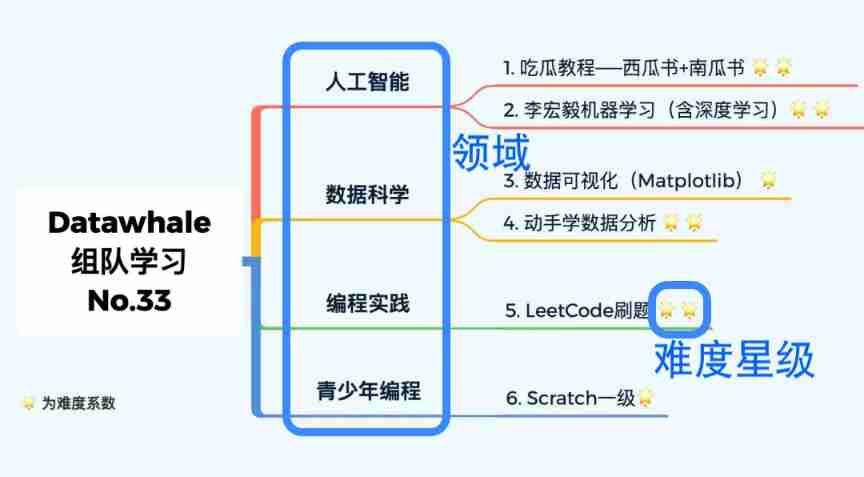
FAQs for datawhale learning!
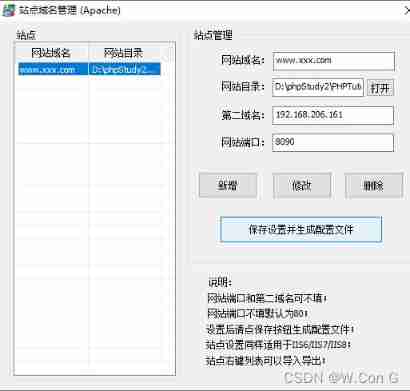
Phpstudy set LAN access
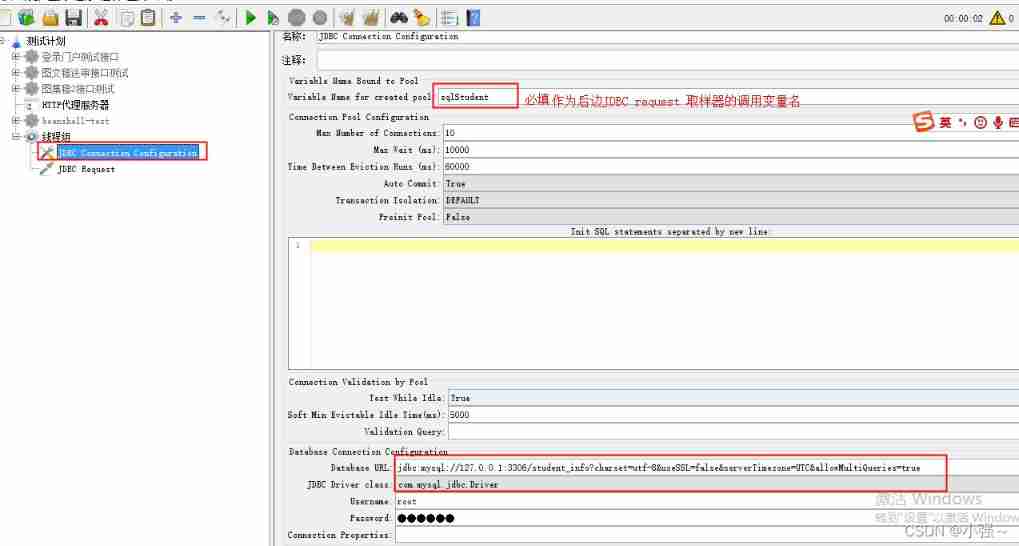
JMeter connection database

第一章:求同吗小数和s(d, n)

第二章:4位卡普雷卡数,搜索偶数位卡普雷卡数,搜索n位2段和平方数,m位不含0的巧妙平方数,指定数字组成没有重复数字的7位平方数,求指定区间内的勾股数组,求指定区间内的倒立勾股数组
原生表格-滚动-合并功能

kubernetes集群搭建efk日志收集平台
随机推荐
第一章:求n的阶乘n!
Ruby replaces gem Alibaba image
Native table - scroll - merge function
2. Template syntax
Rad+xray vulnerability scanning tool
Nacos usage of micro services
Don't be afraid of no foundation. Zero foundation doesn't need any technology to reinstall the computer system
Realize user registration and login
2022-06-28 advanced network engineering (XIII) IS-IS route filtering, route summary, authentication, factors affecting the establishment of Isis neighbor relations, other commands and characteristics
Gym welcomes the first complete environmental document, which makes it easier to get started with intensive learning!
2022 Xinjiang latest road transportation safety officer simulation examination questions and answers
P5.js development - setting
Kubernetes cluster builds efk log collection platform
Meso tetra [P - (p-n-carbazole benzylidene imino)] phenylporphyrin (tcipp) /eu (tcipp) [pc( α- 2-oc8h17) 4] and euh (tcipp) [pc (a-2-oc8h17) 4] supplied by Qiyue
CMD implements the language conversion of locale non Unicode programs
Nerfplusplus parameter format sorting
Global and Chinese market of full authority digital engine control (FADEC) 2022-2028: Research Report on technology, participants, trends, market size and share
Chapter 2: find the classical solution of the maximum Convention and the least common multiple of a and B, find the conventional solution of the maximum Convention and the least common multiple of a a
44. Concurrent programming theory
Virtual machine installation deepin system