当前位置:网站首页>MPLS configuration
MPLS configuration
2022-07-03 19:49:00 【Zhang Xiaoyuan's small network】
establish VRF Space
[r2]ip vpn-instance a
[r2-vpn-instance-a]
To configure VRF Space
[r2-vpn-instance-a]route-distinguisher 100:100 --- To configure RD value
[r2-vpn-instance-a-af-ipv4]vpn-target 100:1 exportextcommunity --- Configure outbound RT
[r2-vpn-instance-a-af-ipv4]vpn-target 100:2 importextcommunity --- Configure inbound RT
[r2-GigabitEthernet0/0/0]ip binding vpn-instance a ---- Speak interface binding
Set to the corresponding VRF In the space
[r2]display ip routing-table vpn-instance a ---- see VRF Spatial routing
surface
[r2]ping -vpn-instance a 192.168.2.1
[r2]ip route-static vpn-instance a 192.168.1.0 24
192.168.2.1 ---- Configure static routing in the spatial routing table
MP-BGP Jianlin
[r2]bgp 1
[r2-bgp]router-id 2.2.2.2
[r2-bgp]peer 4.4.4.4 as 1
[r2-bgp]peer 4.4.4.4 connect-interface LoopBack 0
[r2-bgp]ipv4-family vpnv4
[r2-bgp-af-vpnv4]peer 4.4.4.4 enable
MP-BGP Route Publishing
[r2-bgp]ipv4-family vpn-instance a
[r2-bgp-a]import-route direct
[r2-bgp-a]import-route static
[r2]display bgp vpnv4 vpn-instance a routing-table ---- Look inside the space BGP surface
[r2]display fib vpn-instance a --- Look inside the space FIB surface
[r2]rip 1 vpn-instance a ---- stay VRF Start in space RIP process
[r2-rip-1]v 2
[r2-rip-1]network 192.168.2.0
[r4]ospf 2 vpn-instance b router-id 4.4.4.4 ---- stay VRF Start in space ospf process
The three-tier architecture of the enterprise --- Suggestions for building an enterprise network

Park ---- factory , The government authority , Office buildings , campus , Park, etc , The networks built in these public places to realize data exchange can be called campus networks . Different campus networks may have different emphases .
Wireless is always the last kilometer of wired. Wireless connection depends on wireless devices that can transmit and receive wireless signals , These devices also need to be connected to the network through wired access .
AP --- Wireless access point
WLAN --- WLAN ---- In a broad sense, it refers to radio waves , laser , Infrared ray, etc. to replace part or all of the transmission media of the wired LAN, all the networks constructed .
Wireless networks are inherently flawed :
1, The penetration of wireless signal is poor, and the wireless adopts Ethernet technology --- Frequency division ---- The civil wireless network uses the low-frequency band for data transmission , The congenital defect of low frequency band is poor penetration . 2, The transmission rate of wireless network is related to the signal strength , and , His transmission rate refers to the bidirectional rate
1000 / 8 * 0.85 = 106.25
200 / 8 / 2 * 0.85 = 10.625
3, Wireless network transmission efficiency is low , Slower
Conflict domain : The scope of the conflict --- A hub is in a conflict domain
CSMA/CD --- Carrier sense multiple access / Conflict detection technology
WLAN is equivalent to in the same conflict domain , The wireless technology is used to solve the conflict CSMA/CA
CSMA/CA --- Carrier sense multiple access / Conflict avoidance techniques --- Its transmission efficiency is higher than CD Lower technology
The wireless device cannot detect the conflict. The reason --- The dynamic range of wireless signal strength is very large , Often the received signal strength may be much less than the sent signal strength , This makes it difficult to detect conflicts ( It can increase hardware performance and improve strength )
CA Technology to avoid conflict :
1, When no message is sent in the listening range , Don't send signals directly , It is , Set yourself a random timer first .
2,CSMA/CA The technology adopts stop flow control .
Access layer ---- The main purpose is to connect the terminal equipment to the network , Provide access port --- Generally, layer-2 switches are used ( rely on MAC Address table realizes two layer forwarding )
Convergence layer ---- The main purpose is to gather the traffic collected by the access layer , Generally, three-tier switches are used ---- It has a layer-2 interface similar to that used by ordinary layer-2 switches , It also has a three-tier interface similar to that used by routers or computers . The biggest difference between the second floor opening and the third floor opening is whether there is IP Address .
The layer-3 switch can pass through MAC Address table realizes two layer forwarding , Three layer forwarding can also be realized through routing table .
The core of the three-tier architecture of enterprise network --- redundancy ---- Backup
1, Line redundancy
2, Equipment redundancy
3, Gateway redundancy
4,UPS redundancy ---- UPS --- Uninterruptible power supply ---- Ensure that the power supply of enterprise equipment reaches 6 individual 9 The usability of .99.9999%
A real three-tier architecture , There must be redundancy .
Core layer --- The main function is to complete the rapid forwarding of data between public and private networks . ---- Generally, the router is selected as the core layer device .
VLAN
V --- fictitious
LAN --- LAN ---- Networks with small geographical coverage
MAN --- Metropolitan area network
WAN --- Wide area network
LAN --- Broadcast area
VLAN --- Virtual LAN --- After the switch and router work together , The original broadcast domain is logically divided into multiple ;
First step : establish VLAN
[Huawei]display vlan --- see VLAN Information
VID --- VLAN ID ---- Distinguish and calibrate different VLAN ---- IEEE Organize and issue
802.1Q The standard requires --- VID Must be by 12 Bit binary structure . Value range 0 4095,0 and 4095 Is the reserved number , therefore , The available value range is 1 - 4094
[Huawei]vlan 2 --- establish VLAN
[Huawei]vlan batch 4 to 100 --- Batch creation VLAN
[Huawei]undo vlan batch 4 to 10 --- Batch deletion VLAN
The second step : Put the interface into VLAN
VID Configure the interface mapped to the switch , Realization VLAN Division --- First floor VLAN/ Physics
VLAN
VID Configure the mapping to data MAC Address , Realization VLAN Division --- On the second floor VLAN
VID Configure the type fields mapped to the data , Realization VLAN Division --- Three layers VLAN

VLAN Can also be based on IP Address division , It can even be done according to the strategy VLAN Divide .
802.1Q Standard design VLAN The label of , By 4 Bytes make up , It includes 12 Bit VID, Used to distinguish between different VLAN Of traffic . And add this label to Ethernet Ⅱ Type frame source MAC Between address and type fields .
802.1Q The standard stipulates , Frames with labels are called tagged The frame or 802.1Q frame , Frames without labels are called untagged frame
According to this feature , We call the link between the switch and the computer ACCESS link , also ,ACCESS The interface on the switch side of the link is called ACCESS Interface .ACCESS The link can only pass through untagged frame , also , These frames can only belong to the same VLAN.
We call the link between switches trunk link ,trunk The interfaces at both ends of the link are called trunk Interface .trunk The link is allowed to pass through tagged frame , And these frames can belong to multiple VLAN.
The third step : To configure trunk main rd
The second step is configuration
[sw1-GigabitEthernet0/0/1]port link-type access [sw1-GigabitEthernet0/0/1]port default vlan 2
[sw1]port-group group-member GigabitEthernet 0/0/3
GigabitEthernet 0/0/4
[sw1-port-group] --- Create an interface group
Step 3 configuration
[sw1-GigabitEthernet0/0/5]port link-type trunk
[sw1-GigabitEthernet0/0/5]port trunk allow-pass vlan all
hybrid --- Hybrid interface
[sw1]display port vlan active
Link Type ---- Huawei equipment , The default interface type of all interfaces is hybrid PVID --- Huawei gives every interface , You need to configure a PVID, That is, the interface belongs to VID. All interfaces have not been changed PVID Default PVID The value is 1.
Huawei system regulations : All data entering the switch through the interface , All interfaces must be marked PVID The label of , in other words , All data inside the switch is labeled .
ACCESS Interface
1, When ACCESS The interface received a message from the link untagged After the frame , Swap opportunities add... To this frame VID Interface for PVID yes tag, Then look at this VID Whether it is in the Allow list , If in , Then for what you get tagged Forward frames .
2, When tagged The frame goes from other ports of the switch to one ACCESS After a mouth , Then the exchange opportunity checks the data in this frame tag Of VID Whether you are in your allow list , If in , Will tag After stripping, it will be forwarded from the link , If not , Then discard .
3, If ACCESS The interface received a message from the link tagged After the frame , Then you can directly see the label of the data belongs to VID Whether you are in your allow list , Forward in , No longer discard .
trunk Interface
1, When trunk The interface received a message from the link untagged frame , The switch first adds a... To the data frame VID by PVID Of tag, Then according to VID View the Allow List , If there is , Then forward , without , Then discard ;
2, When one tagged The frame goes from other ports of the switch to one trunk After the port , If tag Of VID stay trunk In the allowed list of , Then forward ( If VID and trunk Interface PVID Phase at the same time , The label needs to be peeled off when transferring out , If not PVID The same label , Then directly transfer out ), If not , Throw away ;
3, If trunk The port receives a message from the link tagged After the frame , View tag Medium VID, If in the Allow List , Then forward , be not in , Then discard ;
Different interfaces have different modification permissions when customizing the forwarding table .
ACCESS Modify permission of interface
You can modify PVID, You can also modify the Allow List ( however , The Allow list can only have one
VID, And it has to be with PVID identical ), The export packaging method is only non packaging .
trunk The modification permission of the interface can be modified PVID, You can also modify the Allow List , The Allow list can be set to more than one VID, Export packaging is only packaging ( and PVID same VID If it is in the Allow list, it is fixed as no label )
[sw1-GigabitEthernet0/0/5]port trunk pvid vlan 2 ---- You can modify trunk Of PVID
hybrid --- The modification permission of hybrid interface can be modified PVID, You can also modify the Allow List , There can also be more than one allowed list
VID, The packaging method can also be modified .
[sw1-GigabitEthernet0/0/1]port link-type hybrid
[sw1-GigabitEthernet0/0/1]port hybrid pvid vlan 2 --- modify hybrid Interface PVID
[sw1-GigabitEthernet0/0/1]port hybrid untagged vlan 2 3 4 --- Define allow list
expand :
MPLS baotou : Usually there are 32bit
20bit Use as label
3 individual bit Of exp, The agreement does not specify , Usually used as COS
1 individual bit Of S, Used to identify whether the stack is low , indicate MPLS Tags can be nested
8 individual bit Of TTL
3bit Of exp Usually corresponds to ip Agreed tos
S Position one : The logo is followed by IP Head .
label label:
It's a shorter one , Fixed length has only local significance .
Forwarding equivalence class FEC:
It is a group of data packets processed in an equivalent way in the forwarding process . If the processing action is the same, it can be understood as the same FEC( One route corresponds to one FEC)
Label switching channel LSP:
One FEC The flow of data , Different nodes are assigned certain labels , Data forwarding follows these tags . The path of data flow is LSP
MPLS The core switch of the network LSR:
Provide label exchange and label distribution functions
MPLS The border switch of the network LER:
stay MPLS The edge of the network , Enter into MPLS The network traffic is controlled by LER Divided into different FEC, And for these FEC Request the appropriate label . It provides traffic classification and label mapping 、 Tag removal function
tagging PUSH、 Pop up the tag POP
MPLS Tag forwarding for , By pre assigned tags , A label forwarding channel is established for the message LSP, At every device that the passage passes through , You only need to search once
FEC The subtlety of :
Different destination addresses ( Belong to the same network segment ) Of IP message , stay ingress Places are divided into the same FEC, With the same label , In this way LSR It's about , Just make a quick exchange according to the label .cache If the function is enabled , The label corresponds to FEC, It may be a network segment , A few entries can match a large number of messages
FEC The fatal flaw of :
For one FEC Come on , All devices along the way must have the same route ( Prefix and mask must be identical ) To build a LSP. Use MPLS On all devices along the way , For routes to use label forwarding , Cannot do aggregation
Near the second floor label For the top of the stack label, near ip The message label Is stack low label,lsr perform label The exchange is always based on the top of the stack label.
Ethernet :0X8847( unicast ) and 0X8848( Multicast ) To identify the bearer is MPLS message .
PPP in :0X8281 To identify the bearer is MPLSCP
Label Builder LDP(label distribution protocol). Follow RIP Very similar .BGP and RSVP You can also distribute labels
Several elements :
1, message ( news )
2, Automatic neighbor discovery and maintenance mechanism
3, A set of algorithms , It is used to calculate the final result according to the collected information
LDP news :
Find out the news DISCOVERY: Used to announce and maintain LSR The existence of
Conversation message SESSION: For building 、 Maintenance and end LDP Session connections between peers
notification message ADVERTISEMENT: Used to create 、 Change and delete specific FEC- Tag binding
Notification message NOTIFICATION news : Used to provide message notification and error notification
The neighbors found out : Mutual development hello message (UDP:PORT646/IP:224.0.0.2)
establish TCP Connect : Initiated by the party with the largest address (TCP:PORT646)(transport address Big )
Session initialization : from MASTER Send initialization message , And carry negotiation parameters
from SLAVE Check whether the parameters are acceptable , Send initialization message if possible , And carry negotiation parameters . And then send keepalive news
master Check whether the parameters are acceptable , Send if you can keepalive news
Receive each other keepalive news , Session creation
Any error messages received during , Close the session , To break off TCP Connect
LDP State transition diagram of session establishment :
NON EXISTENT: The session has not been established . Send each other hello news , At this stage, negotiate the active and passive parties . received tcp After the connection establishment success event is triggered, it becomes initialized state
INITIALIZED: Session connection established successfully . The active party sends initialization message , to turn to opensent state , Waiting for the passive side initialization news
OPENSENT: The active party sends init news , Get into opensent state
OPENREC : Received acceptable init Enter after the message openrec state
OPERATIONAL: All received keepalive Enter after the message operational state
Mark the distribution method :
DOD: Downstream on-demand marking distribution
DU: Downstream autonomous tag distribution
Mark control mode :
Mark control in an orderly way
Independent mode mark control
Label retention :
Conservative way
Free way
Upstream and downstream : In one LSP On , Along the direction of packet transmission , The adjacent LSR They are called upstream LSR And downstream LSR. Downstream is the originator of the route ( Announcer )
DU The way :
The downstream actively sends a tag mapping message to the upstream . There is also horizontal segmentation in label allocation .
Labels are automatically generated by the device at random ,16 The following are reserved by the system
DOD Less use of methods :
The upstream sends a label mapping request message to the downstream , After the downstream receives the message , On request FEC, Allocate tag resources from the tag resource pool
Free way :
Keep all tags sent from neighbors
advantage : When IP Route convergence 、 The next jump changes less lsp Convergence time
shortcoming : Need more memory and label space
Conservative way :
Keep only tags from next hop neighbors , Discard all tags from non next hop neighbors
advantage : Save memory and label space
shortcoming : When IP Route convergence 、 When the next jump changes lsp Slow convergence
Free ways are used more
In an orderly way : Unless LSR It is the originating node of the route , otherwise LSR You must wait until you receive the tag map of the next hop before sending the tag map to the upstream
Independent way :LSR Tag maps can be issued upstream , And don't have to wait to come from LSR Tag map message for next hop
The more popular is the orderly way
DU+ free + In an orderly way :
1, When you find that you have a direct connection route, you will send a label
2, Receive the label from the downstream to a route and the route takes effect ( in other words , This route already exists locally , And the next hop of the route is the same as the next hop of the label ) Tags will be sent when
3, There will be a large number of unselected labels in the label table
Only run MPLS The direct route of the device generates labels , For other devices (IP Domain ) The originating route will not generate labels .
Frame mode : Independent control + Self distribution DOD+ Free to keep
Cell mode : Orderly control + On demand distribution DU+ Conservative reservation
边栏推荐
- Typora charges, WTF? Still need support
- Geek Daily: the system of monitoring employees' turnover intention has been deeply convinced off the shelves; The meta universe app of wechat and QQ was actively removed from the shelves; IntelliJ pla
- Leetcode 1189. Maximum number of balloons (special character count)
- 2022 Xinjiang latest road transportation safety officer simulation examination questions and answers
- Difference between surface go1 and surface GO2 (non professional comparison)
- BOC protected phenylalanine zinc porphyrin (Zn · TAPP Phe BOC) / iron porphyrin (Fe · TAPP Phe BOC) / nickel porphyrin (Ni · TAPP Phe BOC) / manganese porphyrin (Mn · TAPP Phe BOC) Qiyue Keke
- Find a line in a file and remove it
- 第一章: 舍罕王失算
- Chapter 1: extend the same code decimal sum s (D, n)
- 第一章:拓广同码小数和s(d, n)
猜你喜欢
2022 Xinjiang latest road transportation safety officer simulation examination questions and answers

What is the content of game modeling
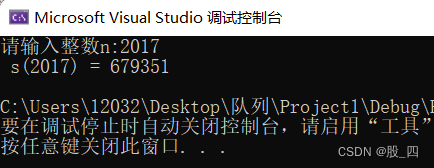
第一章:求n的阶乘n!
BOC protected alanine zinc porphyrin Zn · TAPP ala BOC / alanine zinc porphyrin Zn · TAPP ala BOC / alanine zinc porphyrin Zn · TAPP ala BOC / alanine zinc porphyrin Zn · TAPP ala BOC supplied by Qiyu
第一章:求所有阶乘和数,大奖赛现场统分程序设计,三位阶乘和数,图形点扫描,递归求n的阶乘n!,求n的阶乘n!,舍罕王失算
Chapter 1: find the algebraic sum of odd factors, find the same decimal sum s (D, n), simplify the same code decimal sum s (D, n), expand the same code decimal sum s (D, n)

2022-06-30 网工进阶(十四)路由策略-匹配工具【ACL、IP-Prefix List】、策略工具【Filter-Policy】
Chapitre 1: le roi de shehan a mal calculé
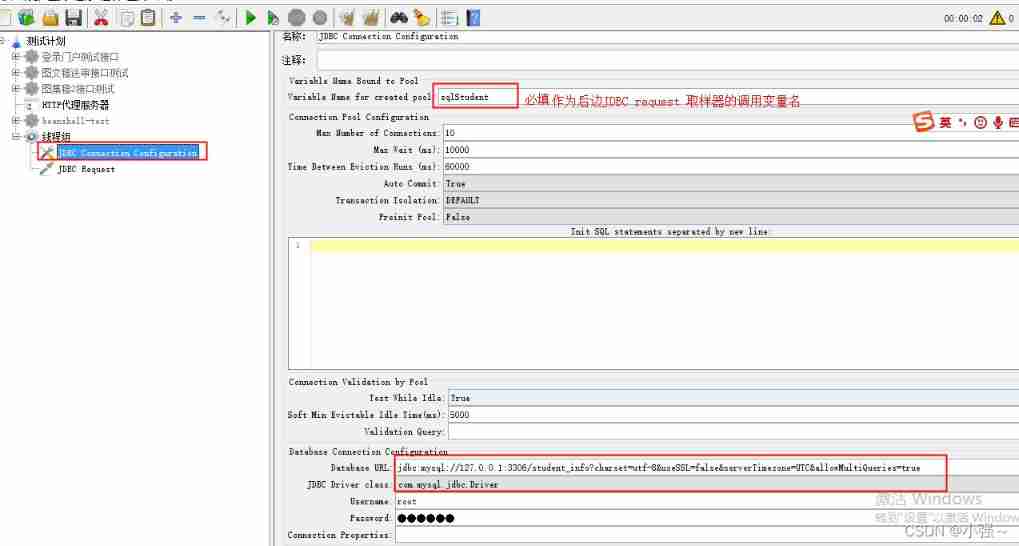
JMeter connection database

2022-07-02 advanced network engineering (XV) routing policy - route policy feature, policy based routing, MQC (modular QoS command line)
随机推荐
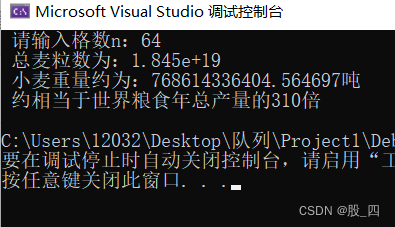
Chapter 1: King Shehan miscalculated
BUUCTF
CesiumJS 2022^ 源码解读[7] - 3DTiles 的请求、加载处理流程解析
Cross compile opencv with contrib
Read the paper glodyne global topology preserving dynamic network embedding
Web Security (VIII) what is CSRF attack? Why can token prevent csdf attacks?
IPv6 experiment
How to check the permission to write to a directory or file- How do you check for permissions to write to a directory or file?
Use of aggregate functions
unittest框架基本使用
Pecan — Overview
4. Data binding
2022-06-28 advanced network engineering (XIII) IS-IS route filtering, route summary, authentication, factors affecting the establishment of Isis neighbor relations, other commands and characteristics
Native table - scroll - merge function
04 -- QT OpenGL two sets of shaders draw two triangles
Compared with 4G, what are the advantages of 5g to meet the technical requirements of industry 4.0
Win10 share you don't have permission
Nacos usage of micro services
第二章:求a,b的最大公约与最小公倍数经典求解,求a,b的最大公约与最小公倍数常规求解,求n个正整数的的最大公约与最小公倍数
Blue Bridge Cup: the fourth preliminary - "simulated intelligent irrigation system"