当前位置:网站首页>Network security Kali penetration learning how to get started with web penetration how to scan based on nmap
Network security Kali penetration learning how to get started with web penetration how to scan based on nmap
2022-07-03 19:44:00 【Learning God is coming】
Nmap It's an open source and free network discovery (Network Discovery) And security audit (Security Auditing) Tools . Software name Nmap yes Network Mapper For short .
nmap Scanning mainly includes four scanning functions: host discovery (Host Discovery)、 Port scanning (Port Scanning)、 Application and version detection (Version Detection)、 Operating system detection (Operating System Detection). Between these four functions , There is also a general dependency .
This article teaches you how to proceed based on Nmap Scan
There are video version and text version below
I don't know how to operate. Please see the text version , Detailed steps inside .
Attention to official account rogue Baron reply 【kali System 】
Video version ↓:
Text version ↓:
Nmap The basic scanning method
Nmap, That is to say Network Mapper, The first is Linux Under the network scanning and sniffing Kit .
notes :Nmap The function of is very powerful, which will be explained in a separate class later
example : scanning 192.168.1.0 This segment
┌──(rootxuegod53)-[~]
└─# nmap -sn 192.168.1.0/24
or
┌──(rootxuegod53)-[~]
└─# nmap -sn 192.168.1.1-254
-sn Parameter description : Means only ping scanning , No port scan
4.3.2 Use nmap Perform a half connection scan
nmap The main scanning types are TCP Full connection scan for ( Will leave a record on the scanned machine ), Half connected scan ( There will be no record )
┌──(rootxuegod53)-[~]
└─# nmap -sS 101.200.128.35 -p 80,81,21,25,110,443
-sS Said the use of SYN Perform a half connection scan
4.3.3 Use nc Scan port
nc yes netcat Abbreviation , With the reputation of Swiss Army knife in the Internet world . Because it's short and sharp 、 Functional and practical , Designed as a simple 、 Reliable Internet tools
nc The role of :
To achieve arbitrary TCP/UDP Port listening ,nc It can be used as server With TCP or UDP Mode to listen on the specified port
Port scan ,nc It can be used as client launch TCP or UDP Connect
Transfer files between machines
Network speed measurement between machines
nc Parameters :
-nv It means the target of our scan is IP Address does not do domain name resolution
-w Time out
-z Indicates port scanning
┌──(rootxuegod53)-[~]
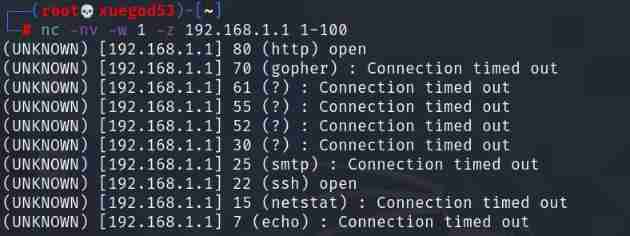
└─# nc -nv -w 1 -z 192.168.1.1 1-100
(UNKNOWN) [192.168.1.1] 80 (http) open
(UNKNOWN) [192.168.1.1] 23 (telnet) : Connection timed out
(UNKNOWN) [192.168.1.1] 21 (ftp) open
边栏推荐
- WPF format datetime in TextBlock- WPF format DateTime in TextBlock?
- NFT without IPFs and completely on the chain?
- 第一章:三位阶乘和数,图形点扫描
- 02 -- QT OpenGL drawing triangle
- unittest框架基本使用
- Day11 - my page, user information acquisition, modification and channel interface
- PR 2021 quick start tutorial, how to create a new sequence and set parameters?
- Day10 ---- 强制登录, token刷新与jwt禁用
- kubernetes集群搭建efk日志收集平台
- Sentinel source code analysis part I sentinel overview
猜你喜欢
![Chapter 2: find the number of daffodils based on decomposition, find the number of daffodils based on combination, find the conformal number in [x, y], explore the n-bit conformal number, recursively](/img/c5/0081689817700770f6210d50ec4e1f.png)
Chapter 2: find the number of daffodils based on decomposition, find the number of daffodils based on combination, find the conformal number in [x, y], explore the n-bit conformal number, recursively

QT -- qfileinfo file information reading

Xctf attack and defense world crypto advanced area best_ rsa

Detailed explanation of shuttle unity interworking principle

Sentinel source code analysis part I sentinel overview
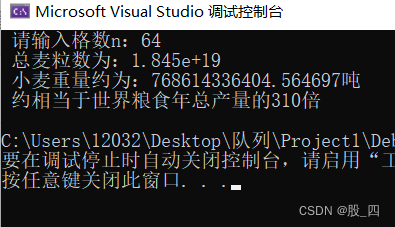
第一章: 舍罕王失算

Chapter 2: 4-digit Kaplan number, search even digit Kaplan number, search n-digit 2-segment sum square number, m-digit ingenious square number without 0, specify the number to form a 7-digit square nu

PR 2021 quick start tutorial, how to create a new sequence and set parameters?
Free year-end report summary template Welfare Collection
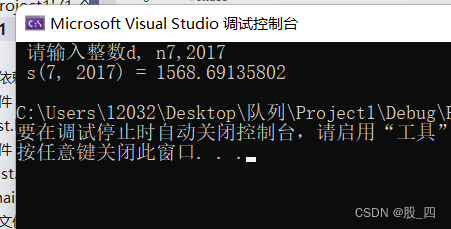
Chapter 1: simplify the same code decimal sum s (D, n)
随机推荐
P1891 crazy LCM (Euler function)
第一章:简化同码小数和s(d, n)
Ae/pr/fcpx super visual effects plug-in package fxfactory
第二章:基于分解的求水仙花数,基于组合的求水仙花数, 兰德尔数,求[x,y]内的守形数,探求n位守形数,递推探索n位逐位整除数
The earliest record
Pecan — @expose()
02 -- QT OpenGL drawing triangle
Chapter 1: seek common? Decimal and S (D, n)
IPv6 experiment
Part 28 supplement (XXVIII) busyindicator (waiting for elements)
Summary of learning materials and notes of Zhang Fei's actual combat electronics 1-31
Rd file name conflict when extending a S4 method of some other package
第一章:拓广同码小数和s(d, n)
Phpstudy set LAN access
Free sharing | linefriends hand account inner page | horizontal grid | not for sale
Chapter 1: find the algebraic sum of odd factors, find the same decimal sum s (D, n), simplify the same code decimal sum s (D, n), expand the same code decimal sum s (D, n)
交叉编译Opencv带Contrib
01 - QT OpenGL display OpenGL window
Basic principle of LSM tree
04 -- QT OpenGL two sets of shaders draw two triangles