当前位置:网站首页>Mysql database related operations
Mysql database related operations
2022-07-27 03:26:00 【Caribbean waves】
Related operations for database
Hello everyone , This time I bring you my new column : database , The database is relatively not that difficult , As long as you practice hard 、 Memorize grammar , I believe that learning database well is not a problem , Bloggers will start from 0 analyse , Explain the knowledge points of database step by step , And will give many examples . most important of all , Bloggers will not use software , Use the most primitive way -> Command line to explain , The advantage of this explanation is to write sentence by sentence , It won't cause the problem that readers can't keep up with their ideas !
QQ:162196770
WeChat :PRIDE_Xu_
Gitee:https://gitee.com/jialebihaitao
Previous blog portal :
The next blog portal :
Article column :
B standing : Under construction , I will consider in the future B Explain some knowledge points on the station and so on
1、 Operation of database
1.1 Displays the current database
Displays which databases exist on the current server ( Or what data sets )
grammar :
show databases;

Be careful :
databasesIt's the pluralshowanddatabasesSpace between ( A few don't matter , But not without !)SQLStatements are basically based on;At the end of theSQLStatement is case insensitive- The default built-in database , Don't move about ! It's not fun to break the database ~
1.2 Create database
grammar :
create database [if not exists] Database name [ Create rules ];

Be careful :
All the rest
[]There is no need to input , This[]Represents optional ( Write but not write );As long as the name of the database is not the name of the keyword ( In fact, you can also create databases with keywords as their names , Use inverted quotation marks , namely
Just wrap this symbol ( Position inTab upper ,1 To the left of ,Esc Below )), But be careful : Not on a server Create multiple databases with the same name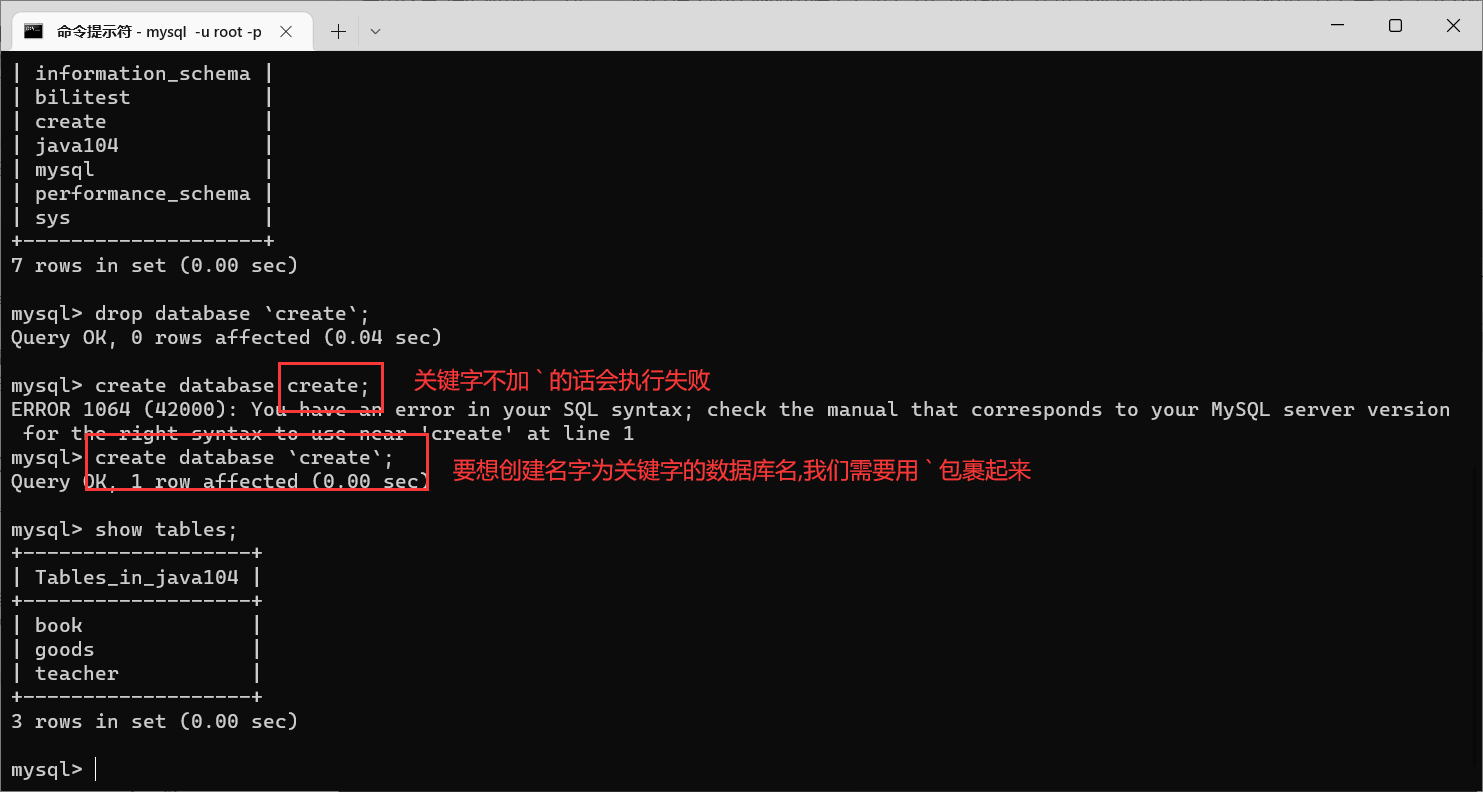
if not existsThe function of is to create as long as it doesn't exist , In fact, it can beUse scenarios : You send someone a paragraph
SQL, But you don't know whether there is a corresponding database on his computer , So choose if not to create this way . Others have already created , Let's not fool aroundInside
databaseIt's singularCreate rules : When creating a database, you can specify character sets and verification rules
Validation rules : Describes the comparison method between current characters
Compare the equality of strings / Size relationship ( For example, we sometimes want to ignore case )
There are not many scenarios , We seldom intervene manually , Generally, you can use the default verification rules .
Character set :
create database test character set utf8mb4;
Inside
utf8mb4What's going on ?First , Let's think about it first , How does a computer save letters ?
ASCII code : By numbers , To represent letters . The one-to-one correspondence between numbers and letters , become ASCII clock
however ASCII It does not contain Chinese , So now two versions are commonly used
GBK2 Bytes to represent a Chinese character
yes
WindowsThe default character encoding of simplified Chinese versionUTF-8: Be regarded as " Universal character encoding "UTF8Variable length coding : A Chinese character , In a few bytes , It's uncertain .It's usually 3 A byte means a Chinese character
Essentially , Is to use numbers to represent symbols in various languages , Corresponding large table , This mapping relationship is called " Character set "
So the one above
utf8mb4What's going on ?utf8mb4Actually, it's better thanutf8There are some special symbols , such asemojiexpression . Set toutf8NothingSo we learned such a thing before
char* s = " hi "; printf("%d\n",strlen(s)); // So, please. , How many bytes does a Chinese character occupy // Through the right GBK as well as UTF8 Explanation , We can see : // You need to confirm which character code it is // GBK -> 2 Bytes // UTF8 -> 3 Bytes 1
Implement this
SQLTime spent in operation : We can see the picture just now , The running time is0.03sec, This is relative to computers , It's actually a very slow speedLet me introduce you the following time of common computer operations :
Access the network :s~ms
Access disk :ms~us
Access memory :us~ns
operation CPU:ps
Be careful : This conversion is 1000, No 1024. Don't get mixed up
Databases are often slow links , Large projects are prone to problems .
1.3 Using a database
Before performing a series of operations on the database , We must select the database first
grammar :
use Database name ;

Use the database statement , No addition ; Can also carry out . But it's not recommended , stay SQL in , Some sentences can be omitted ;, But some statements must be added ;, So we add ;, Let you see which SQL The statement did not add ; Don't be surprised

1.4 Delete database
This operation is dangerous !!! Never delete the database on the company's server .
grammar :
drop database Database name ;
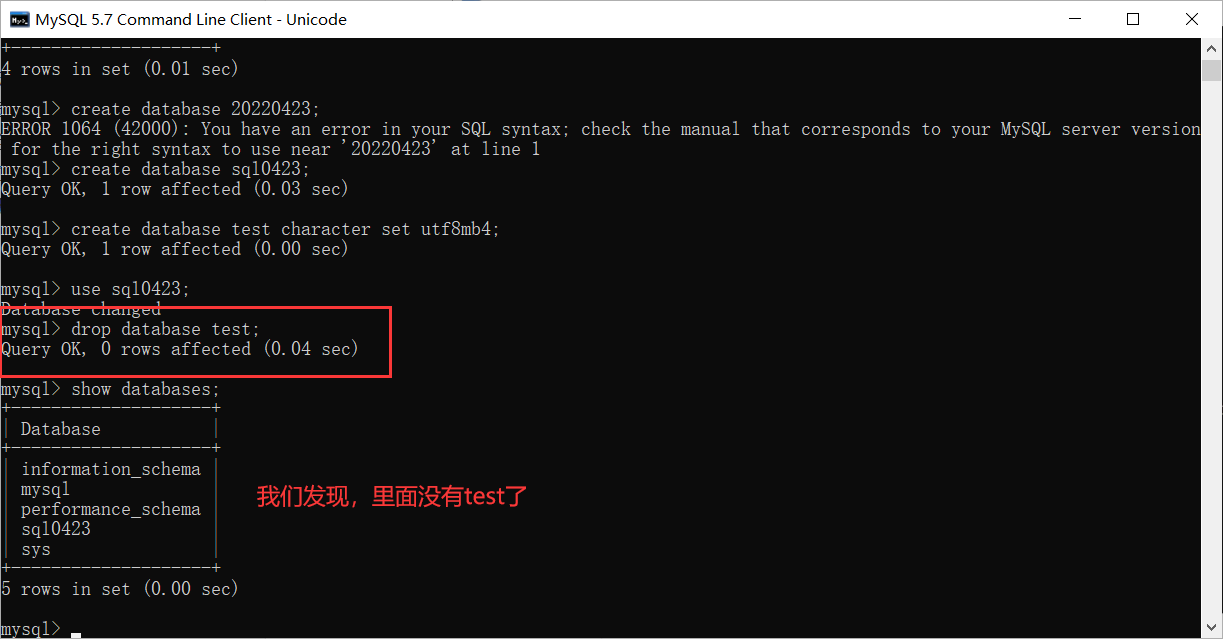
In fact, it can be retrieved , But it's troublesome .
Can be opened
MySQLOfbinlogfunction , Every operation on the database , Will be recorded asbinlogin . ten thousand ⼀ Data destroyed , You can rebinlogImport all operations in ⼀ All over , But the content is not complete

So is there a way , Avoid deleting data in the production environment ?
Access control : Provide administrator privileges , Only administrators can delete
Produced a profession :
DBADatabase administratorBack up a copy : Once deleted , There is still a way to go
Is it possible that permission control has also failed , The backups have also been deleted ? It's certainly possible , That is not “ False deletion ” 了 , It was intentional , Will be sent to a good place to eat and live .
Recover hard disk data :
1.5 Expand :cmd Minor operations
- Press and hold the up and down keys on the keyboard to find historical commands ( Save your energy )
- Copy and paste : Select content , Press enter to copy , Right click Paste
1.6 The environment involved in the company ( Digression )
Office environment : On entry , The computer sent to you by the company ( Of course, there are also a few companies , I will let you bring your computer -> Basically run fast , Far away ), Will use this computer for daily office . The basic configuration is
8 nucleus CPU 16G Memory 512G Hard diskdevelopment environment : It is generally provided in the form of server , The office computer is connected to the server through the network . The corresponding device of this server is generally about
16 nucleus CPU 64G Memory 4T Hard diskSome projects are very resource consuming , A bad start-up memory will eat dozens G, Or even hundreds G. Of course, you can't use your own office computer .
If the developed program is relatively small , At this time, there may be no development environment , You can directly use the office computer to develop .
Generally, the company brings the equipment that has passed the warranty period to the programmer as " development environment "
Test environment : The environment used by the testing staff for the program to be tested , The machines used are basically those that have passed the warranty period
The online environment / Production environment : It is also provided in the form of server , You also need to connect remotely through the network of your office computer . Good configuration , about
56 nucleus CPU 256G/512G Memory A number of T Hard diskProduction environment , In fact, it is an environment that provides services to external users , Never hang up !
Hanging up will cause major resource losses
that MySQL The server will basically appear on the top 2 3 4 Environment , If it is deleted by mistake 2 3 Database in the environment , In fact, the situation is relatively good , The colleagues worked overtime and were rescued , Basically, it will be scolded by many people . But once you accidentally delete 4 That is, the database in the online environment , Then it's over . Users outside will feel the direct impact , The probability will lead to the loss of users , Take legal action and so on . Serious will cause major safety accidents !
边栏推荐
- pip3 设置阿里云
- 常见弱口令大全
- PIP3 setting alicloud
- [从零开始学习FPGA编程-54]:高阶篇 - 基于IP核的FPGA开发-PLL锁相环IP核的原理与配置(Altera)
- Database usage security policy
- 【树链剖分】模板题
- Byte side: can TCP and UDP use the same port?
- What are "full five unique" and "full two unique"? Any difference?
- [机缘参悟-52]:交浅言深要因人而异
- Deep learning vocabulary embedded, beam search
猜你喜欢
随机推荐
[learning notes, dog learning C] string + memory function
Database usage security policy
[flask] the server obtains the file requested by the client
Customer cases | pay attention to the elderly user experience, and the transformation of bank app to adapt to aging should avoid falsehood and be practical
Detailed explanation of const usage in C language
A new paradigm of distributed deep learning programming: Global tensor
如何进行 360 评估
[regular] judgment, mobile number, ID number
Explain tool actual operation
Docker creates MySQL 8.x container and supports Mac and arm architecture chips
字节一面:TCP 和 UDP 可以使用同一个端口吗?
opiodr aborting process unknown ospid (21745) as a result of ORA-609
shell awk
Worthington果胶酶的特性及测定方案
微信小程序生成Excel
Redis源码学习(33),命令执行过程
若依框架代码生成详解
DNS记录类型及相关名词解释
自己梳理的LocalDateTime的工具类
Add support for @data add-on in idea