当前位置:网站首页>The practice of software R & D should start from the design
The practice of software R & D should start from the design
2022-07-26 14:55:00 【Huawei cloud developer Alliance】
Abstract : Design security is to achieve DevSecOps A very important link , A lot of historical experience also shows that , The earlier the security design of the system is considered in the architecture design stage , Than those systems that consider safety design at a later stage of development and design , It's much safer .
This article is shared from Huawei cloud community 《DevSecOps R & D safety practices —— Design 》, author : Hua Wei Yun PaaS Little helper .
Preface
With DevOps The development of ,DevOps Greatly improve the speed of enterprise application iteration . But at the same time , If safety can't keep pace , Not only offset DevOps Improvements brought about by change , Digitalization slows down the process of enterprise transformation , It will also lead to loopholes and risks . Therefore, security capability has been paid more and more attention all over the world , The endogenous security of software development has become the evaluation of enterprises DevOps An important indicator of maturity level .
The importance of safety design
stay 《DevSecOps Leader's Guide 》 In a Book , author Glenn Wilson Put forward DevSecOps Three tier methodology , Safety education (Security Education)、 Ensure safety through design (Secure By Design)、 Security Automation (Security Automation). Design security is to achieve DevSecOps A very important link , A lot of historical experience also shows that , The earlier the security design of the system is considered in the architecture design stage , Than those systems that consider safety design at a later stage of development and design , It's much safer . According to the National Institute of standards and Technology (NIST) Statistics , Perform code repair after release , The cost of repair is equivalent to the repair performed at the design stage 30 times . The specific data are shown in the figure .

DevSecOps The goal is to be at all stages of the software life cycle , It can be earlier 、 Discover and deal with security issues faster . Move left from the beginning of safety to the present everywhere , To achieve this goal . Therefore, design safety is essential as a leader in the whole life R & D cycle .
How to do a good job in safety design
How to design safely , We mainly focus on the design of security architecture to ensure the safe landing of laws , Conduct threat modeling so that the safe landing can be followed 、 Do a good job in privacy and sensitive data protection, and let the safe landing be described in every detail and implementation .
Security architecture design
stay DevSecOps in , Security design extends from applications to containers and infrastructure , Application code and infrastructure code are important lines of defense against multiple threats from malicious actors . Integrating good design principles into product architecture and development is the basic requirement of writing security code . When architecture is directly related to security control , It is very important to ensure that engineers follow good design principles . Security controls exist throughout the value stream of end-to-end delivery , From the control built into the application during the development phase to the control of saving the application at run time . These measures include protecting the source code or protecting the application runtime , It also extends to the interaction between customers and Applications , Such as authentication and authorization process .
In security architecture design , It can be based on security triples and security design principles . Confidentiality (Confidentiality)、 integrity (Integrity)、 Usability (Availability), Referred to as CIA A triple , Is the basic principle of safety . Confidentiality means that only authorized users can access information , It cannot be obtained by any unauthorized user . Integrity refers to the process of information input and transmission , Not be modified or destroyed by illegal authorization , Ensure data consistency . Availability refers to ensuring that legitimate users' use of information and resources will not be improperly rejected .
General safety design principles in the industry , Mainly reflected in restrictive 、 Simplicity and design :
• Restrictive principle
1. Failure - Default security policy (Fail-Safe Defaults), There should be an emergency safety mechanism when the function fails , In addition, the default product configuration should be in the safe state , There are no security holes .
2. The principle of full Arbitration (Complete Mediation), The security check should cover any access operation . The security mechanism has the ability to identify all sources of each access operation request .
3. The principle of separation of privileges (Separation of Privilege), Break down privileges , Assign to multiple principals , Avoid that a subject has a lot of privileges . For example, set up a system administrator , Configuration administrator , Different roles such as security administrator , Corresponding to different privileges .
4. The principle of minimum authority (Least Privilege), Each object has only the smallest set of privileges required to complete the work , Limit damage caused by accident or error .
• The principle of simplicity
1. The principle of economic application (Economy of Mechanism), The safety design should be as short and concise as possible , Easier to handle when using .
2. The principle of least public mechanism (Least Common Mechanism), The number of shared objects of public resources should be set to a minimum , Avoid scenes where multiple objects share the same resource .
• Design principle
1. Open design principles (Open Design), Don't design your own security mechanism , Don't develop your own algorithm , Development design is more important . You can use the key 、 Password, etc. to enhance the security of the system , In this way, the security mechanism will be subject to extensive review .
2. The principle of psychological affordability (Psychological Acceptability), On the premise of psychological affordability , Set up good interaction for security mechanism , Security mechanisms may add an additional burden to users , But the burden must be reasonable , What users can afford . For example, you need to enter the verification code after multiple login failures .
After years of development and summary in the industry , Some other security principles have been developed and extended , For example, defense in depth 、 Don't take it lightly 、 Protect the weakest link 、 Improve privacy principles, etc .
Threat modeling
Threat modeling is a structured approach to analyzing application security , Used to identify , Quantify and address application related security risks , Optimize system security by identifying targets and vulnerabilities , Then define the process of countermeasures to prevent or mitigate system threats . When designing new products or functions in existing products , Engineers need to be familiar with the types of security vulnerabilities that attackers search , So that they can mitigate the risk of being used ; Need to understand the risks inherent in the design , In order to eliminate or mitigate these risks early in the delivery life cycle . in summary , Threat modeling is the process by which engineers evaluate the design of products or functions to identify threats and determine how to build protection against them .
The process of threat modeling can refer to the methods provided by Microsoft : Preset scene -> Graphical scenarios / The process -> Identify threats -> Provide measures for each threat link -> Verify all threats and mitigation measures .

some IT Internet company , Based on a lot of practical experience , Build its own security threat library and security requirements Library , The lightweight threat modeling process is realized , Through the safety assessment questionnaire , Identify the type of application to be built from the system structure and use scenario , Then match the corresponding threat library and demand Library , Determine the baseline of safety requirements , Finally, the safety design scheme is obtained .
Many threat modeling methods have been developed in the industry , Microsoft STRIDE、 Attack simulation and threat analysis process PASTA、LINDDUN、 Common vulnerability scoring system CVSS、 Attack tree 、Persona non Grata、 Security card 、VAST Modeling and other methods , They can be combined to create more powerful 、 A more comprehensive view of potential threats . Not all methods are comprehensive , Some are abstract , Some are people-centered , There are also methods that specifically address risk or privacy issues , Which method should the organization choose according to the specific needs of the project .
Security, privacy and data protection
Security and privacy requirements analysis and design is the source of the whole life cycle of service application R & D and operation , Security and privacy issues should be carefully considered during the design phase , Determine the safety requirements at the beginning of the project , Try to avoid requirements changes caused by safety .
DevSecOps Research and develop operation security solutions, and focus on the safety problems of pain points , Such as safety requirements 、 Compliance requirements and current hot issues such as personal data and privacy protection , Using security solutions can better avoid such security problems , Improve the security of software application services .
Security and privacy requirements mainly come from customer security requirements , Industry best practices such as OWASP TOP10、OWASP ASVS, Company security policy 《xxx Information technology management specification 》《xxx Data management specifications 》, Industry regulatory requirements , And laws and regulations 《 Network security law 》、《 Personal information protection norms 》、《 Data security law 》 etc. . Establish a clear safety requirements management process , Be able to analyze security requirements 、 review 、 Effective management of decision-making and other links , Make requirements decomposition and allocation traceable .
Huawei cloud security design practice
Huawei has 20 Years of R & D safety accumulation , Huawei's R & D security capability is gradually formed with the continuous problems in the business . Huawei will open its operation and maintenance security capabilities , And the upcoming R & D security capabilities and Huawei cloud DevCloud Deep integration , Bring... To the enterprise DevSecOps platform , Let the enterprise convenient landing DevSecOps idea , In the process of software development, built-in security protection , Let software “ Natural safety , Grow up healthy ”, Become the competitiveness of enterprises .
Security architecture design
Huawei in terms of security design principles , Based on industry norms , Built its own basic safety technology and engineering ability , Formed safety standards and specifications , This includes security / Privacy requirements baseline , Code for design of foundation safety , Security coding specification , Procurement safety requirements , Open source and third-party software security management strategy .
Huawei cloud is referring to the general responsibility of information technology security evaluation CC Security function item of 、NIST Control set , Summarized into product safety architecture design 8 dimension 24 children ,.8 The design of dimensional security architecture includes the following aspects :
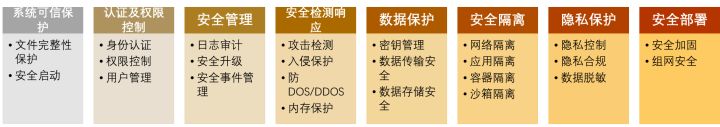
To guide the architecture designer system 、 Comprehensively design the security architecture , Avoid omission of architecture level security design .
Threat modeling
Huawei has its own threat modeling tool SecDesign, Conduct threat modeling during product design , Identify and mitigate risks
Start with the problem of pain points to think : In the system requirements analysis and design phase , How to make the product safer ? In what kind of subsystem 、 modular 、 Consider security risks between data streams ? After identifying the risks , How to reduce several aspects of thinking ? Huawei cloud open security design domain , Yes STRIDE Methodology upgrade , For system threat analysis , Provide analytical dimensions 、 Reference cases , Assist in safety design ; Based on the identified safety risks , Intelligent recommended mitigation measures and test cases , Output analysis report ; Long term accumulated safety risk identification scheme 、 Abatement programs 、 design scheme 、 The test case 、 Scene examples and knowledge , Provide rich Huawei and industry experience for security design , Greatly reduce the threshold of enterprise security design .
Security, privacy and data protection
Huawei cloud has built a life-cycle data security and privacy protection design , Achieve data isolation 、 Data encryption and data redundancy .
• Data isolation : Isolation mechanism can avoid intentional or unintentional unauthorized access between customers 、 Tampering, etc , Reduce the risk of data leakage . The cloud disk drive of Huawei cloud EVS、 Object storage service OBS、 Elastic file service SFS And other services regard customer data isolation as an important feature . When designing the cloud business architecture, users can use these cloud services to achieve the goal of data security isolation .
• Data encryption : Encryption protects both static and in transit data . The cloud disk drive of Huawei cloud EVS And other services support data encryption services DEW Integrate , Realize key management and data encryption . Huawei cloud also uses encrypted transmission channels , Ensure the confidentiality and integrity of data during transmission . When designing the data encryption function , We can fully learn from the existing practices and capabilities of Huawei cloud .
• data redundancy : Redundancy design can effectively prevent data loss . Huawei cloud adopts multi copy backup and erasure code design , Through redundancy and verification mechanism to judge the damage of data and repair it quickly , To ensure the reliability of the service . When users design services on the cloud , It can make full use of the reliable services provided by Huawei cloud services .
• Privacy protection design : Consider privacy in product design , It can greatly improve the privacy protection ability of the product . When Huawei cloud builds cloud services , Put privacy protection as a requirement into the product development and design process . Huawei cloud implements the policy throughout the life cycle of personal data PbD(Privacy by design) Idea , Build a secure cloud service with privacy protection . Huawei cloud is based on PbD The principle is to consider privacy in the design , That is to protect personal data and privacy through design , Apply the concept of protecting personal data and privacy to all links of products and services by technical means .
The seven basic principles of privacy protection implemented by Huawei cloud are legal 、 proper 、 transparent , Purpose limit , Data minimization , accuracy , Minimize storage life , Integrity and confidentiality , Imputable .
Huawei cloud interpretation GDPR And other laws and regulations , Help companies meet compliance requirements . Huawei cloud's open privacy compliance domain , According to GDPR Etc , Provide tools , Generate privacy compliance reports 、 Privacy statement , Help enterprises design compliance ; According to privacy compliance design , Automatically generate and execute test cases , Finally, the privacy compliance verification report is given .
Postscript
DevOps One of the basic demands of the government is to “ fast ”, And security has “ I can't get up quickly ” Characteristics . Because security itself needs more professional knowledge background , Analysis of more complex attacks and potential security issues . also , Even with tools , Its technology stack is also deeper than ordinary inspection tools , That means it takes longer . such as , Static checking of source code , If it's just checking the style of the code , They can do a quick scan ; If you need to do automatic checking of security coding , So we need to do flow analysis , Even a special compilation process is needed to gather the necessary information . There is a long way to go , Realization DevSecOps There is still a long way to go .
Refer to appendix
1.《DevSecOps Leader's Guide 》 Glen · Wilson (GLENN WILSON) translate : Zhuang Fei
2.《 R & D white paper on operational security 》. Cloud computing Open Source Industry Alliance .
3.《 Huawei cloud security white paper 》. Huawei Technology Co., Ltd
4. Huawei is a trusted professional —— Trusted design
5. Scan more than... Every day 300 One hundred million lines of code ,DevSecOps Landing and practice in Huawei _DevOps
Click to follow , The first time to learn about Huawei's new cloud technology ~
边栏推荐
- Embedded development: skills of debugging embedded software
- Usage of nn.conv2d and nn.convtranspose2d functions in pytorch
- 智能家居行业发展,密切关注边缘计算和小程序容器技术
- The difference between torch.nn and torch.nn.functional in pytorch
- 10 schemes to ensure interface data security
- Win11 running virtual machine crashed? Solution to crash of VMware virtual machine running in win11
- CAS based SSO single point server configuration
- Arithmetic operation and logic operation of image in opencv
- GOM login configuration free version generate graphic tutorial
- Pdf translation, which translation company in Beijing is good
猜你喜欢

PyTorch中 torch.nn与torch.nn.functional的区别
When AI encounters life and health, Huawei cloud builds three bridges for them

Minecraft 1.16.5模组开发(五十二) 修改原版生物战利品 (Loot Table)

Tdengine helps Siemens' lightweight digital solution simicas simplify data processing process

Create Yum warehouse inside the enterprise

SiamRPN++:深层网络连体视觉跟踪的演变
![[integer programming]](/img/e5/aebc5673903f932030120822e4331b.png)
[integer programming]

Stacked noise reducing auto encoder (sdae)

AMB | towards sustainable agriculture: rhizosphere microbial engineering

The development of smart home industry pays close attention to edge computing and applet container technology
随机推荐
SiamRPN++:深层网络连体视觉跟踪的演变
《MySQL高级篇》五、InnoDB数据存储结构
PyTorch中 nn.Conv2d与nn.ConvTranspose2d函数的用法
9、学习MySQL DELETE 语句
保证接口数据安全的10种方案
As the "first city" in Central China, Changsha's "talent attraction" has changed from competition to leadership
Use of LINGO software
How to get 5L water in a full 10L container, 7L or 4L empty container
go开发调试之Delve的使用
Whaledi message queue stability improvement practice
SP export map to Maya
次轮Okaleido Tiger即将登录Binance NFT,引发社区热议
Figure introduction to neural network core dataset
Summary and analysis of image level weakly supervised image semantic segmentation
Parsing XML files using Dom4j
SSH that must be read on cloud native
[nuxt 3] (XII) project directory structure 1
SiamRPN:建议区域网络与孪生网络
CVE-2022-33891 Apache spark shell 命令注入漏洞复现
[1.2. return and risk of investment]