当前位置:网站首页>The first in China! Tencent cloud key management system passes password application verification test
The first in China! Tencent cloud key management system passes password application verification test
2022-06-24 15:36:00 【Tencent security】
In the era of digital economy , Data has become a key means of production . Using cryptography to transmit data 、 The circulation 、 Storage and use are encrypted , It is an important means to ensure the information security of users and enterprises .
In recent days, , Tencent cloud key management system (KMS) The cloud key management system password application verification test conducted by Dingxuan, a third-party authoritative password evaluation organization , Its compliance 、 The correctness and effectiveness have been verified again . This is also The first cloud key management system in China that has passed the password application verification test , It has important reference significance for the exploration and formulation of industry standards .
Tencent cloud key management system has passed the verification test , Explore the way for establishing industry standards
recently , Dingxuan, a national third-party commercial password testing institution authorized by the State Password Administration, conducted a password application verification evaluation on Tencent cloud key management system . Dingxuan company has the qualification of commercial password product testing agency , Qualification of pilot organization for security evaluation of commercial password application , National Laboratory Accreditation CNAS And national metrology accreditation CMA Qualifications , International financial data security assessment PCI DSS Of QSA and ASV Institutional qualifications , And have information system security 、 software security 、 Intelligent terminal security assessment and risk assessment capability .
The evaluation report shows , Basic password functions of Tencent cloud key management system 、 Interface security 、 The application function is correct and effective , The test item verifies that it meets the expectations . meanwhile , Also from the physical and environmental security 、 Network and communication security 、 Device and computing security 、 Application and data security 、 Management system 、 Personnel management 、 Construction and operation 、 Quantitative assessment was made in eight aspects including emergency response , The system has achieved GB/T39786-2021《 Information security technology information system password application basic requirements 》 The third level of requirements .
Seamless integration with multiple cloud services , End to end guard the whole life cycle of cloud data
In recent years , Large scale data leakage incidents occur frequently at home and abroad , Countries and enterprises pay more attention to network and information security , It puts forward higher requirements for using password technology to protect network security . To guide and standardize the application of passwords in enterprises' reasonable compliance , The state has successively promulgated and implemented 《 Network security law 》、《 Cryptology 》 And a series of policies and regulations , Put forward requirements for password application security evaluation .
Cloud key management system is an important part of password application , At present, it has been widely used in the cloud computing industry . Due to the technological frontier 、 New application fields , There is still no unified certification standard in the industry . This time, Tencent cloud actively cooperated with the third-party certification authority to conduct security assessment , While verifying the security of Tencent cloud key management system , It also provides reference value and significance for the establishment of industry standards .
Tencent cloud key management system (KMS) Tencent security Yunding laboratory relies on Tencent itself 20 A security management service created through years of security attack and defense practice , It can help enterprises create and manage keys easily , Protect the confidentiality of the key 、 Integrity and availability , Meet the needs of multiple applications in enterprises 、 Key management requirements of multi service , And meet regulatory and compliance requirements . besides ,“ Cloud native ” It is also a major feature of Tencent security in password services , Tencent cloud key management system can be stored with Tencent cloud objects 、 Distributed database 、 Seamless integration of cloud services such as cloud disk , So that enterprises can manage their keys through the key management system .
Tencent cloud key management system (KMS) yes “ Tencent cloud data security center ” One of the core components of , Based on key management system (KMS)、 Data encryption software and hardware services for commercial passwords (HSM/SEM) And identity credentials and authorization (Secrets Manager) Three abilities , Tencent security has also created End to end cloud data full lifecycle data security protection solution ——“ Tencent cloud data security center ”, With componentization 、 The service-oriented capability ensures that the data is identifying 、 Use 、 Safety in the process of consumption .
After the enterprise goes to the cloud , The data usage scenarios in the cloud environment will continue to expand , The data needs to be provided during generation 、 flow 、 Storage 、 Whole process safety protection during use and destruction . Tencent cloud data security center provides data security protection strategies based on cloud nativity , From the whole process of data encryption 、 Access control, etc , Form a closed loop of cloud native data key links , Effectively help enterprises deal with cloud data security issues .
In the era of digital economy , The importance of data security has become increasingly prominent . future , Tencent security will continue to carry out product innovation , Enrich “ Cloud data security middle platform ” Component capability , Help enterprises consolidate the safety base , Welcome digitalization more calmly 、 Intelligent upgrade .
边栏推荐
- 国产芯片的赶超,让美国手机芯片龙头高通害怕了,出招应对竞争
- 国产最长寿的热销手机,苹果也不是对手,总算让国产手机找回面子
- Binary computing
- How to modify the login user name of easynvr video monitoring system?
- 运营商5G用户渗透远远比4G慢,5G的普及还得看中国广电
- Is it safe to open an account in flush? What preparation is needed
- Bosun query
- Arrays API
- The security market has entered a trillion era, and the security B2B online mall system has been accurately connected to deepen the enterprise development path
- MySQL toolset: the official performance testing tool mysqlslap
猜你喜欢
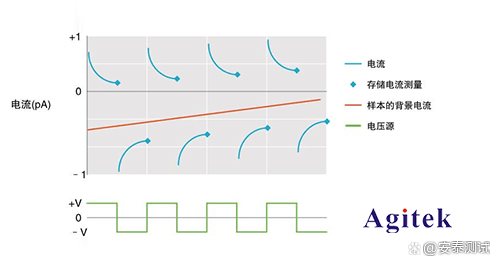
Wide measuring range of jishili electrometer

Multimeter resistance measurement diagram and precautions
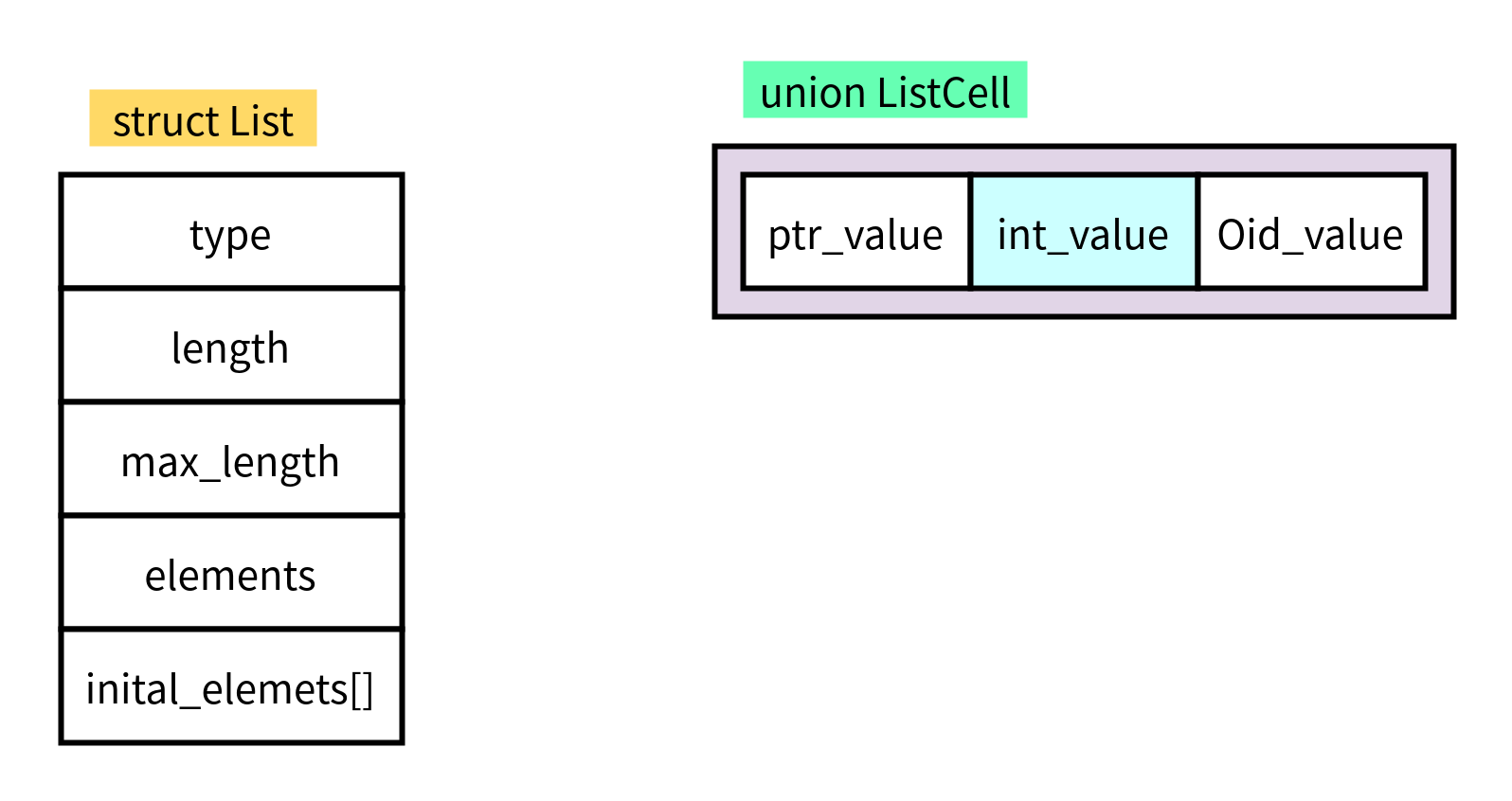
List of PostgreSQL
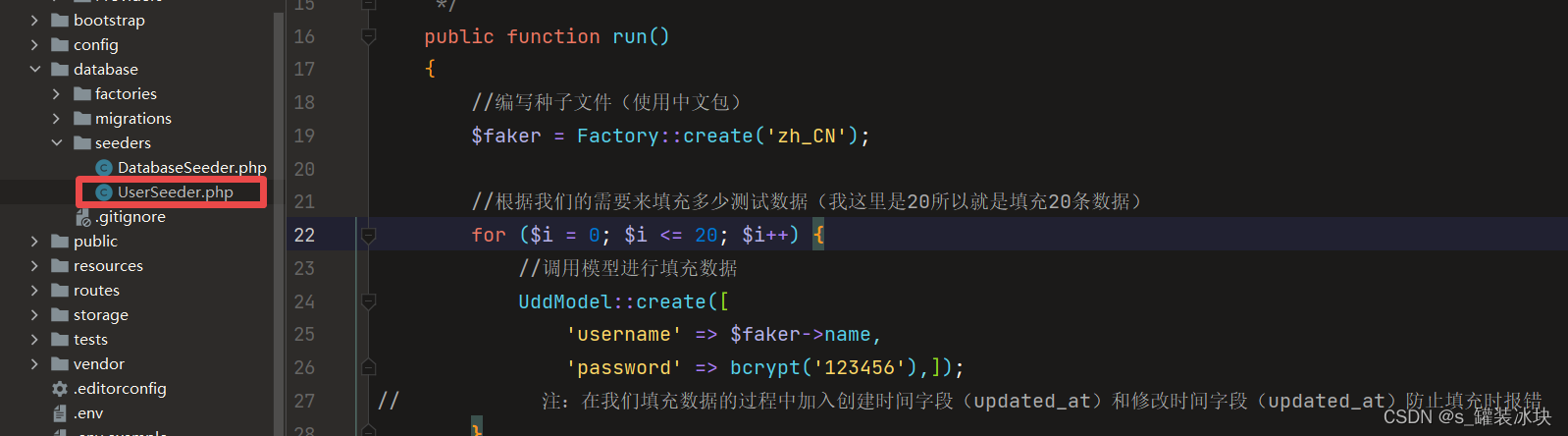
Laravel8 uses faker to call factory to fill data
Bitmap of redis data structure

【C语言刷题——Leetcode12道题】带你起飞,飞进垃圾堆

CVPR 2022 - Interpretation of selected papers of meituan technical team
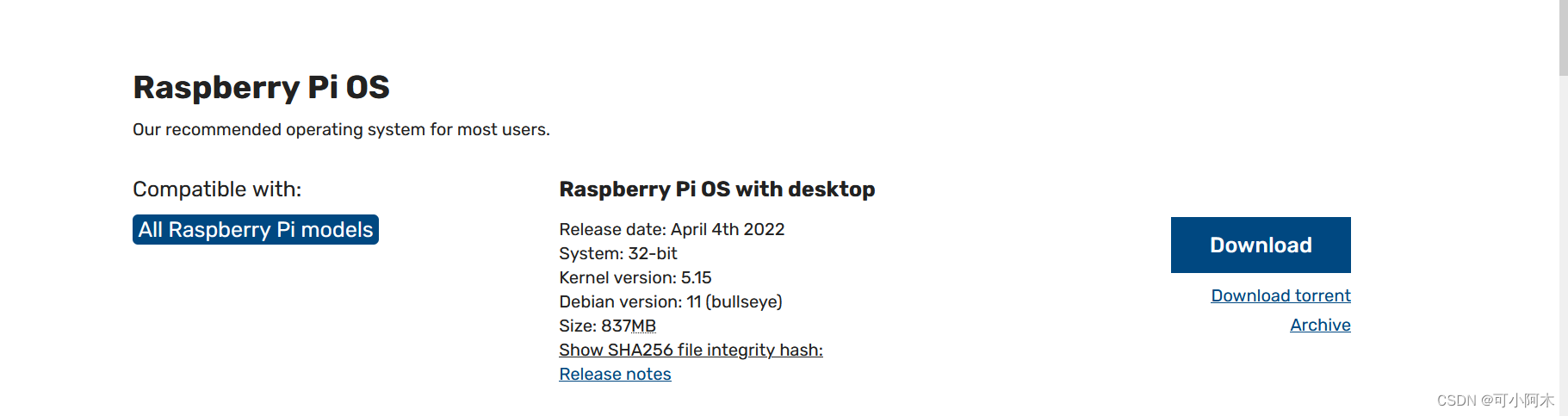
VNC Viewer方式的远程连接树莓派

leetcode. 12 --- integer to Roman numeral
Record the range of data that MySQL update will lock
随机推荐
Chaos mesh in Tencent -- Tencent mutual entertainment chaotic engineering practice
Phpcms upgrade editor method -- simple and effective
Multimeter resistance measurement diagram and precautions
How to optimize performance
How to efficiently transfer enterprise business data?
Use list
Concurrent writing of maps in golang
中国十大证券app排名 炒股开户安全吗
Do you really know the difference between H5 and applet?
The future of robots -- deep space exploration
CVPR 2022 - Interpretation of selected papers of meituan technical team
Istio practical skill: enable accesslog locally
刚刚阿里面软件测试回来,3+1面任职阿里P7,年薪28*15薪
Data stack technology sharing: how to use data stack for data collection?
List of PostgreSQL
股票网上开户及开户流程怎样?网上开户安全么?
At? Let's blow the air conditioner together!
Design of CAN bus controller based on FPGA (Part 2)
期货公司开户安全吗
An accident caused by a MySQL misoperation, and the "high availability" cannot withstand it!

