当前位置:网站首页>Be on the list again! Know that Chuangyu was selected as one of the top 50 competitive enterprises in China's network security industry in 2022
Be on the list again! Know that Chuangyu was selected as one of the top 50 competitive enterprises in China's network security industry in 2022
2022-06-28 23:22:00 【Know Chuangyu kcsc】

In recent days, , China Network Security Industry Alliance (CCIA) Officially released “2022 The competitiveness of China's network security industry in 50 strong ( hereinafter referred to as “CCIA Competitive power 50 strong ”)、 Growth star 、 Potential star ” list .
As the backbone of China's network security industry , Know that Chuangyu relies on its excellent network security practical technical ability and market competitiveness , Included in the 2022 year “CCIA Competitive power 50 strong ” The list . This is also the next step 2021 Years later, I know Chuangyu Again .
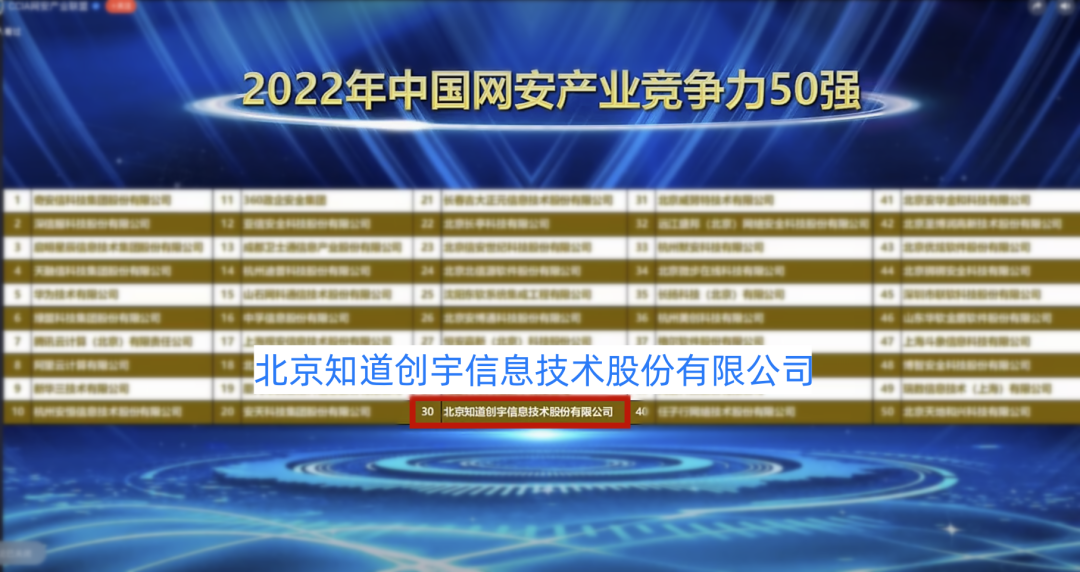
The backbone of the industry , On the list 50 strong
“CCIA Competitive power 50 strong ” Combined with the characteristics of China's network security industry , On the basis of data, based on the enterprise competitiveness and resource strength 2 Three dimensions are used to describe the comprehensive capabilities of enterprises .
Know that Chuangyu has been 2 In the list “CCIA Competitive power 50 strong ”, This shows that the industry knows that Chuangyu is in technological innovation 、 Business capability 、 Brand influence 、 Continuous recognition of the company's scale and other aspects of performance .
Know that Chuangyu will continue to give full play to its technical advantages , Use relevant resources efficiently , Speed up the development and expansion .
Excellent comprehensive strength
Always take the responsibility of ensuring network security
More than ten years of development , Covering the whole country
Know that Chuangyu was founded in 2007 year , Founded by several senior security experts , Headquartered in Beijing . After more than ten years of continuous development , I know that the staff size of Chuangyu has reached 1800 people .
The company pays attention to technological innovation , In Beijing, 、 Chengdu 、 Wuhan has three major technology centers , The domestic sales and service system covers North China 、 East China 、 south China 、 Central China 、 The West and Hong Kong , It can respond to various security needs of customers at any time .
2021 year , Know that Chuangyu has obtained the state-owned capital China Mobile equity fund 、 China Internet investment fund 、 Joint investment of CLP scientific research investment fund .
Continue to focus on the actual combat capability of network security
Know that since its establishment, Chuangyu has been continuously focusing on the construction of network security actual combat capability . As a network security company that put forward the concept of cloud defense earlier in China , Know that Chuangyu is based on cyberspace mapping and cloud defense SaaS service , It is committed to building a network security practical defense system based on big data joint defense and control .

And cyber attacks continue “ A war ”, Actively carry out dynamic defense
SaaS Cloud defense platform , Handle hundreds of billions of network requests per day , Daily interception attack exceeds 10 100 million times ;
Hundreds of thousands of online business systems “ Zero accident ” Security , A little bit attacked , Network wide defense .
Professional technology and products , Follow up on cyber threats in real time
404 Team of laboratory experts , Real time vulnerability mining 、APT Threat analysis ;
sense 、 prevent 、 tube 、 Integrated control solution , Quickly build a network security guarantee governance system .
Unique and rich Threat Intelligence , Accurately perceive the security dynamics
ZoomEye Cyberspace mapping system , super 200 Billion historical assets ;
Seebug Vulnerability community , Massive vulnerability resources ;
hackers & Black product fingerprint database , Featured attacker big data .
Systematic product polishing , Training in actual combat
these years , Know that Chuangyu adheres to “ For the state and the people ” Idea , Constantly explore solutions to threats in cyberspace , With “ cloud 、 tube 、 edge 、 End ” and “ intelligence 、 Probe 、 perception 、 protective 、 situational ” Build a product system in two dimensions , Strive to protect against network threats “ See clearly 、 It can be prevented 、 Attack Deke ”.

Know the family Atlas of Chuangyu products
at present , I know that Chuangyu has been the leader of domestic party and government organs and enterprises in various industries Hundreds of thousands The information system and internal network provide practical security protection , No accident in more than ten years , Widely trusted by customers .
Again on the list “CCIA Competitive power 50 strong ”, It is not only the industry's full recognition of the comprehensive ability of Chuangyu enterprises , It is also a breakthrough for Chuangyu 、 A growing incentive .
Know that Chuangyu will continue to take ensuring network security as its own responsibility , Continuous technological breakthroughs 、 Polish products and services , Provide more customers with practical security protection , Contribute to the development of network security industry !

边栏推荐
- [matlab]函数定义与使用
- 笔记
- One card can sell tens of millions, and the business expansion is faster than that of players: you don't understand the Jianghu of star cards
- 云计算的迷路者
- 解决ConfigParser解析中文问题
- ROS2中的行为树 BehaviorTree
- Machine learning 6-decision tree
- [chapter 71 of the flutter problem series] mutual conversion between uint8list and image in flutter
- C interview questions_ 20220627 record
- CS5463代码模块解析(包含下载链接)
猜你喜欢

Lock4j -- distributed locking Middleware -- use / instance

YuMinHong set up two funds funded by his hometown

Finally, someone explained the cloud native architecture
![[数学建模]Matlab非线性规划之fmincon()函数](/img/fc/46949679859b1369fcc83d0d8b637c.png)
[数学建模]Matlab非线性规划之fmincon()函数

mysql-5.7.30-winx64免安装版下载安装教程

Interviewer: what is the internal implementation of strings in redis?

Chapter IV memory management exercise

月薪6万,互联网“降本增效”后,这类人开始被疯抢

Chapter V virtual memory exercise

机器学习4-降维技术
随机推荐
第四章 存储器管理练习
Master the usage of const
The picture display on the left of the two column layout is determined by the content height on the right
月薪6万,互联网“降本增效”后,这类人开始被疯抢
国盛证券开户是真的安全可靠吗
图片64base转码与解码
What will be done after digital IC Verification?
2022 PMP project management examination agile knowledge points (4)
Advice to friends
Machine learning 4-dimension reduction technology
See fengzhixia | FENGZikai, the originator of Guoman, for exclusive sale of Digital Collections
Online sql to htmltable tool
融云通信解决方案 破解企业沟通痛点
Oil monkey script learning
PHP 使用endroid/qrcode 二维码生成, GD库生成分享海报
pymysql.Error 获取错误码与具体错误信息
Chapter V virtual memory exercise
全面掌握const的用法《一》
论文解读(DCN)《Towards K-means-friendly Spaces: Simultaneous Deep Learning and Clustering》
[matlab]函数定义与使用