当前位置:网站首页>Three person management of system design
Three person management of system design
2022-07-26 23:18:00 【qq_ forty-one million five hundred and twelve thousand nine hun】
One 、“ Three members ” duty
System administrator : Mainly responsible for the daily operation and maintenance of the system . Including network devices 、 Security products 、 Server and user terminal 、 Operating system database 、 Installation of confidential business system 、 To configure 、 upgrade 、 maintain 、 Operation management ; Network and system users add or delete ; Data backup of network and system 、 Operation log review and operation monitoring ; Safety recovery under emergency conditions .
Security Administrator : Mainly responsible for the daily security and confidentiality management of the system . Including the granting and revocation of network and system user permissions ; Safety design of user operation behavior ; Security equipment management ; Audit of system security events 、 Analysis and processing ; Safety recovery under emergency conditions .
Security auditors : It is mainly responsible for auditing and tracking the operation behavior of system administrators and security personnel 、 Analysis, supervision and inspection , Find violations in time , And regularly report to the system security management organization .
Two 、“ Three members ” Configuration requirements
1、 System administrator 、 Security administrators and security auditors cannot log in to the system as other users ; You cannot view and modify information in any business database ; You cannot add, delete or change the contents of the log .
2、 The three members of the confidential information system shall be held by the internal personnel of the unit , Require political reliability , Familiar with confidential information system management operation process , Have a strong sense of responsibility and risk prevention and control ; And sign the confidentiality commitment .
3、 System management personnel and security management personnel can be professional technicians of the information department , For the confidential information system with strong business, the relevant business department can serve ; The Security Auditor shall be held by the security department or other personnel who are competent for the work of Security Auditor according to the work needs .
4、 The system administrator and Security Auditor of the same equipment or system cannot be held by the same person , The security administrator and the Security Auditor shall not be held by the same person .
3、 ... and 、“ Three members ” Authority management process 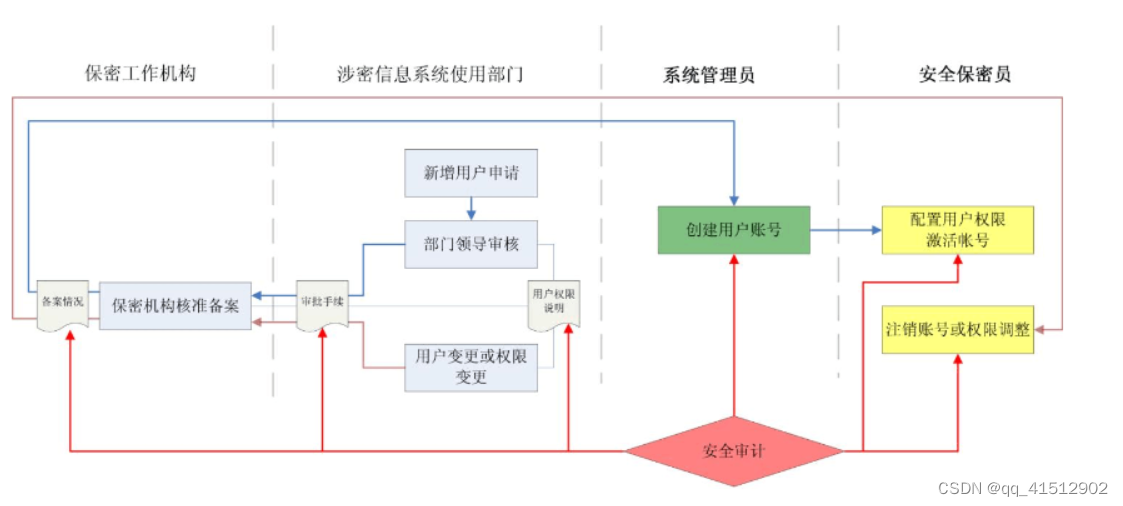
When users need to use classified information systems , You should first submit a written application in this department , After the approval of the leader in charge of the Department , Explain the permissions of this user in the system according to the actual situation , And report the whole situation to the confidentiality organization of the unit for filing .
After the system administrator receives the user's written application , According to the examination and approval results of the competent leader of the Department and the approval and approval of the confidentiality work organization of the unit , Generate an identifier for the user in the system , Create user account .
After the security administrator receives the user's written application , According to the audit results of the confidentiality organization , Configure corresponding permissions , And activate the account . thus , Only this account can be used . When users' work changes or permissions change , The leader in charge of the user's department shall notify the security administrator in writing , And report to the confidentiality organization of the unit for filing . After receiving the notice, the security administrator , Cancel the user account or adjust the permission according to the change result .
The security auditor should check with the system administrator regularly 、 Audit log related to security administrator , When a user account is found to have increased 、 When deleting and changing user permissions , Check relevant procedure documents in time , To determine the system administrator 、 Whether the operation of the security administrator has been authorized and approved .
In practice , Through a management process similar to the above , send 3 Security and confidentiality management personnel of this category perform their respective duties , Give full play to , Coupled with the perfect security and confidentiality approval and supervision mechanism , We can thoroughly implement security and confidentiality management measures , Fully realize the security and confidentiality objectives of the system .
Four 、 Confidential information system provides “ Three members ” Security and confidentiality protection measures such as authority division
( One )“ Three members ” Equal permission setting
System administrator 、 Whether the security administrator and security auditor can play an effective role , In addition to personnel setting and management in place , It also depends on whether the business application system and security products used by the system provide corresponding administrator accounts , And the functions of authority division and audit log . therefore , When designing and developing business application systems and security products , Full consideration should be given to the needs in this regard , Provide corresponding functions for users .
Administrator role division
Serial number role duty
1
System administrator
1. Responsible for system parameters , Such as process 、 Configuration of forms 、 Maintenance and management . 2. Responsible for user registration 、 Delete , Ensure the uniqueness of user identifier in the system life cycle ;
3. Be responsible for the change and adjustment of the organization , Be responsible for all... Related to user rights Class role settings .
2 Security Administrator
1. Be responsible for the adjustment of personnel's confidential level and position and the allocation of user authority ; 2. Be responsible for keeping all users except the system administrator ID Flag file . The security administrator cannot log in to the system as other users ; 3. You cannot view and modify information in any business database ; 4. Be responsible for viewing user audit logs and Security Auditor logs , But you can't add, delete or change the contents of the log .
3 Security auditors
1. Be responsible for supervising and checking the system administrator 、 Operation logs of security administrator and security audit administrator , But you can't add, delete or change the contents of the log ; 2. Be responsible for regular backup 、 Maintain and export logs .
Super users should be avoided in the process of application system design , That is, the user has full access to resources .
Permissions for ordinary users , It should be divided according to the principle of minimum authorization , Set its authority within the minimum authorization required to complete the work .
( Two ) Security audit function
The audit function mainly records the business operation process of system users , It provides a basis for security administrators and security auditors to judge the legitimacy of user operations .
1. Audit scope . Include : Start and close the audit function , The increase of users 、 Modification, deletion and permission change , System administrator 、 Security Administrator 、 Various operations performed by safety auditors and users , Including looking up 、 Backup 、 Maintain and export audit logs .
2. Contents of audit records . It should include the time when the event occurred 、 place 、 type 、 The main body 、 Object and result ( Start 、 end 、 Failure 、 Success and so on ).
3. Management of audit matters . The management of audit matters refers to the operation of core business 、 Definition and management of events requiring audit , Configure and define all matters or operations that may need to be audited .
4. Audit policy configuration . Audit strategy configuration refers to the relationship between audit matters and auditors 、 set relationship , That is, set which key personnel and which key operations need to be audited ; And according to the requirements of national standards , Addition and deletion of users 、 Change of authority 、 System administrator 、 Audit Manager 、 Operations performed by security administrators and users must be audited , Therefore, according to the audit content, the audit is divided into two types: mandatory audit and configurable audit .
5. Storage of audit information . The system shall be designed with sufficient storage space for audit records , And when the storage space is full, it can give an alarm in time , Stored audit records must be protected , It can detect or prevent the modification and forgery of audit records , Records should be kept for at least three months .
边栏推荐
- 为什么我还在CSDN写文章?一段陪伴学习的历程。
- 逆袭黑马:数据库全栈工程师(DevDBOps)培训,把最好的课程送给您!
- One fingerprint patent has been declared invalid! Huiding and siliwei both officially responded!
- 云原生微服务第一章之服务器环境说明
- Product principles of non-financial decentralized application
- Reinforcement learning weekly 55: lb-sgd, msp-drl & robust reinforcement learning against
- Boss; Can flick CDC Oracle finish reading the full amount of data, just like directly fetching data from the database
- 测试开发是开发吗?
- After closing the Suzhou plant, Omron Dongguan plant announced its dissolution, and more than 2000 people are facing unemployment!
- With a total investment of 10billion US dollars, Huahong Wuxi 12 inch wafer factory was officially put into operation
猜你喜欢
![[untitled]](/img/88/68952146da17a4a504ee7d1bc8858d.png)
[untitled]
What if redis memory is full? This is the right way to deal with it

黑马瑞吉外卖之新增员工

The most classic Nature paper on Alzheimer's disease is suspected of fraud

Ribbon负载均衡
![[MySQL] - index principle and use](/img/e1/af74ee20ebe0c6e6f5e453330cc13b.png)
[MySQL] - index principle and use

Recruit | PostgreSQL database R & D engineers every week, with an annual salary of 60+, high salary for famous enterprises, and challenge yourself!

逆袭黑马:数据库全栈工程师(DevDBOps)培训,把最好的课程送给您!

面试官问:JS的this指向
电脑开机后内存占用过高(50%以上)
随机推荐
正则表达式与绕过案例复现
科研太忙无法顾家?陈婷:人生不能只有一个支点
[untitled]
How to use data pipeline to realize test modernization
HCIA-R&S自用笔记(21)STP技术背景、STP基础和数据包结构、STP选举规则及案例
Basic use of gateway
8 other programming languages -- Recording
Openstack virtual machine network card is renamed cirename0
面试:你印象最深的BUG,举个例子
Introduction to the use of Jerry downloader forced download tool_ Ac695n696nad14ad15 full range support
[hcip] OSPF relationship establishment
Introduction to Nacos as a registry and configuration center - realize remote call, dynamically obtain configuration files and database configuration information
After working for one year, I have some insights (written in 2017)
PostgreSQL and Navicat: the backbone of the database industry
Download win10 system image and create virtual machine on VMware virtual machine
HCIA-R&S自用笔记(19)VLAN配置及实验、VLAN间路由
【flask高级】结合源码分析flask中的线程隔离机制
Huawei atlas900 reveals the secret: it integrates thousands of shengteng 910 chips, and its computing power is comparable to 500000 PCs!
SQL 基础知识
Weilai cup 2022 Niuke summer multi school training camp 2

