当前位置:网站首页>Logic Vulnerability----Permission Vulnerability
Logic Vulnerability----Permission Vulnerability
2022-07-30 13:23:00 【jjj34】
Ultra-authority loopholes are further divided into parallel ultra-authority, vertical ultra-authority and cross-authority.
Parallel override: the permission type remains unchanged, and the permission id changes
Vertical override: permission type changes, permission id remains unchanged
Cross-override: permission type changed, permission id changed

User 1 becomes user 2, and user 2 is also an ordinary user, and the level is overridden
User 1 changes from a common user to a system administrator, and vertically overrides the authority
User 1 becomes user 4, and user 4 has system administrator rights, cross-override
In Windows, the difference between admin and system:
The system user is used to manage the software, admin is the authority for the user
system manages software, admin manages users
1. Parallel overstepping
Horizontal override refers to an attacker attempting to access the resources of a user who has the same permissions as him.
For example, in a certain system, there is a function of personal data. Both account A and account B can access this function, but account A and account B have different permissions
When a accesses this function, it is intercepted by bp packet capture, and the user name is changed from a to b. At this time, user a may obtain the information of b, which is a horizontal unauthorized vulnerability.
All functions with horizontal authority division in the system have the risk of horizontal over-authorization. The following are the common scenarios of horizontal over-authorization:
1. Based on user ID
Such as an airline's order, he will access or operate the corresponding data through the identity id submitted by the user (user id, account number, mobile phone number, ID number and other unique user identifiers)

Among them, passengerID is the passenger, and contactID is the contact
After testing, it can be found that after these two parameters are modified, the ID cards and contact information of other passengers can be viewed
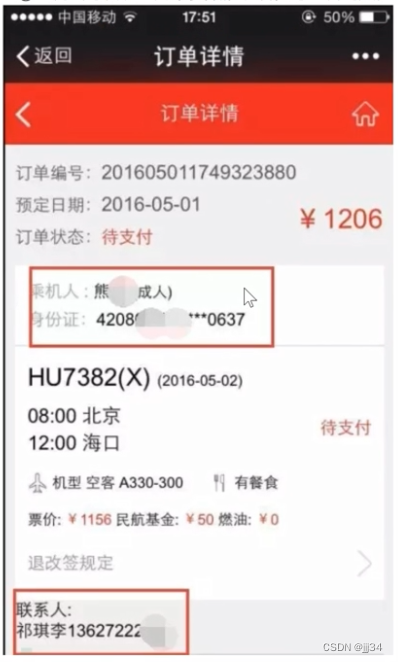
2. Based on object id
When using a function, access or operate the corresponding data through the object id submitted by the user (such as Dingding, record number)
For example: a system has a horizontal override vulnerability, grab the data package submitted by the order, and find that there is an oid that is very suspicious

Blast this oid to view the order information paid by others
3. Based on filename
When using a function, you can directly access the file through the file name, which is most common in the scenario where the user uploads the file
Hundreds of thousands of resources can be downloaded by traversing fileid

Vertical override
Vertical override refers to an attempt by a low-level attacker to access the resources of a high-level user.For example, a system is divided into ordinary users and administrators. The administrator has system management functions but ordinary users do not. Then we can understand that the management function has vertical authority division. If ordinary users can use some attack method to access themanagement function, then we call it vertical override.
Case 1: Vertical override by modifying js
A site's management background only uses js jump to restrict unauthorized user access

After removing js, you can successfully access the background and can operate

Case 2: First enter the background through ordinary users, and then achieve vertical override by modifying parameter values
A certain brand of light cats
Use the default username and password: useradmin/[email protected]#$%^ to log in to the system

Successful login background

Click "object management-user management-edit useradmin->get url */cgi/webif/Objset-users.sh?edituser=edituser&id=5"

Modify the parameter id=4 to vertically override the authority to telecomadmin's modification page

You can directly view the password by changing the password type of the password to the text type through the source code

Case 3: Permission control framework defect
The authority control framework is the basis for realizing the authority control function. If the authority control framework itself has defects and is easily compromised, the authority control function will be completely invalid.
Using a simple permission identifier in a cookie to mark the user's permission level or using a simple user ID in the user request parameter to control user permissions is typicalPermissions framework flaw.
For example, after a normal user logs in, uid=1 in the cookie; after an administrator user logs in, uid=2
Then we can log in as a normal user first, and then change the uid to 2
Summary
Be careful,
1. Modify js
2. Find the difference between ordinary users and administrator users, and then change the cookie of ordinary users to administrator users
边栏推荐
- R语言筛选时间序列数据的子集(subset time series data)、使用window函数筛选连续日期时间范围内的数据(start参数和end参数分别指定起始和结束时间)
- jsArray数组复制方法性能测试2207300040
- 一文读懂Elephant Swap,为何为ePLATO带来如此高的溢价?
- CMake库搜索函数居然不搜索LD_LIBRARY_PATH
- 创意loadingjs特效小点跳跃动画
- dolphinscheduler simple task definition and complex cross-node parameter transfer
- Parallelized Quick Sort Ideas
- 【高等数学】【7】二重积分
- R语言时间序列数据算术运算:使用log函数将时间序列数据的数值对数化(平方、开平方、指数化等函数类似使用)
- 基于反步积分滑模摩擦补偿的光电伺服转台控制
猜你喜欢
随机推荐
Markdown 3 - 流程图表
jsArray array copy method performance test 2207292307
双击Idea图标打不开——解决办法
Lake storehouse which electricity (2) of the project: project using technology and version and the environment
基于反步积分滑模摩擦补偿的光电伺服转台控制
cpu/CS and IP
dolphinscheduler simple task definition and complex cross-node parameter transfer
第十三天笔记
strlen跟sizeof区别
datax enables hana support and dolphinscheduler enables datax tasks
深度操作系统DeepinOS安装步骤和MySQL安装测试
树形dp小总结(换根,基环树,杂七杂八的dp)
一本通循环结构的程序设计第一章题解(1)
There is no one of the strongest kings in the surveillance world!
[PostgreSQL] - Storage structure and cache shared_buffers
在 Scala 中读取整个文件
These critical programs are missing or too old: ma
Dry Goods Sharing: Various Implementation Methods of Bean Management Factory with Great Use of Small Skills
Composer安装方式
【23考研】408代码题参考模板——顺序表









