当前位置:网站首页>466. Count The Repetitions
466. Count The Repetitions
2022-08-03 21:46:00 【51CTO】
Define S = [s,n] as the string S which consists of n connected strings s. For example, [“abc”, 3] =”abcabcabc”.
On the other hand, we define that string s1 can be obtained from string s2 if we can remove some characters from s2 such that it becomes s1. For example, “abc” can be obtained from “abdbec” based on our definition, but it can not be obtained from “acbbe”.
You are given two non-empty strings s1 and s2 (each at most 100 characters long) and two integers 0 ≤ n1 ≤ 106 and 1 ≤ n2 ≤ 106. Now consider the strings S1 and S2, where S1=[s1,n1] and S2=[s2,n2]. Find the maximum integer M such that [S2,M] can be obtained from S1.
Example:
边栏推荐
- 聚焦开源与联合共创|麒麟软件出席开源峰会欧拉分论坛
- 《强化学习周刊》第56期:GraphIRL、REDEEMER & 眼科强化学习的潜在研究
- Engineering Effectiveness Governance for Agile Delivery
- 距LiveVideoStackCon 2022 上海站开幕还有2天!
- win10安装及配置Gradle
- Unification of east-west and north-south communications
- 基于DMS的数仓智能运维服务,知多少?
- FVCOM 3D Numerical Simulation of Hydrodynamics, Water Exchange, Dispersion and Transport of Oil Spills丨FVCOM Model Watershed, Numerical Simulation Method of Marine Water Environment
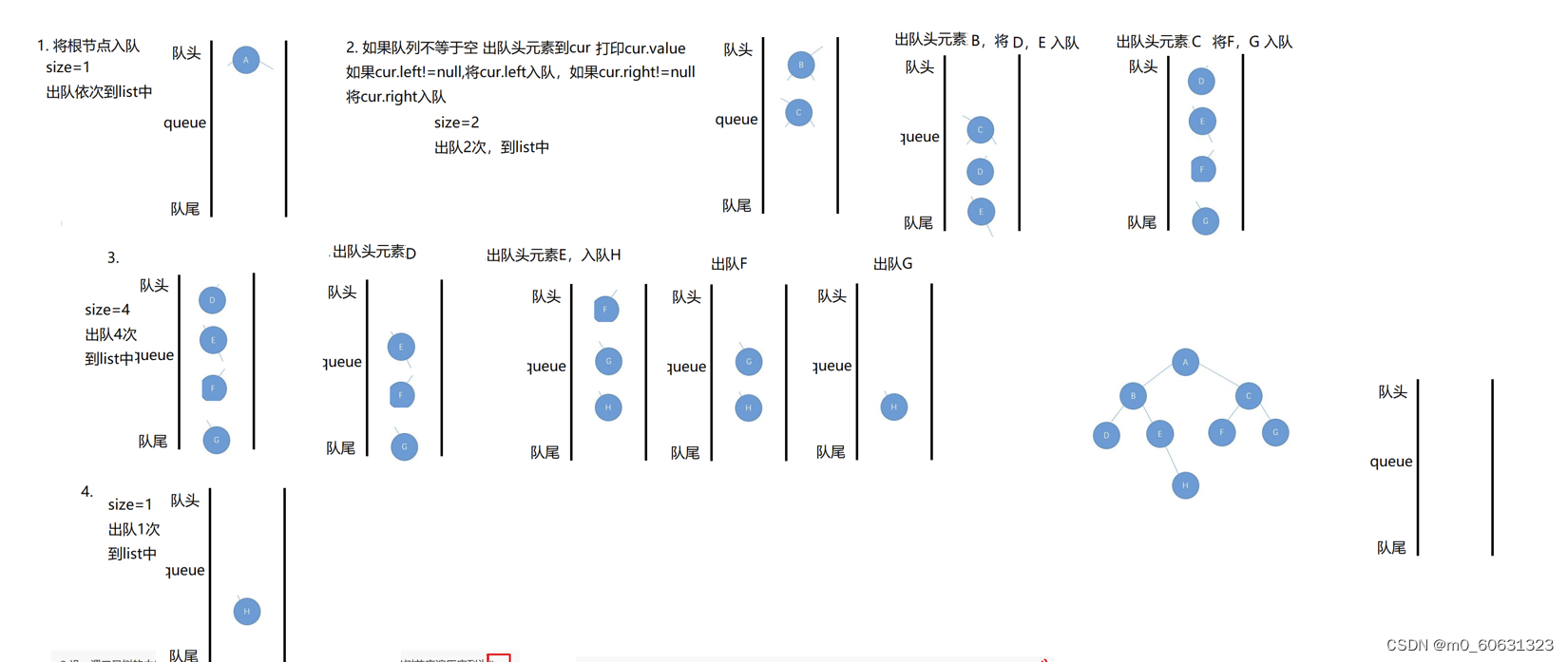
- 【刷题篇】二叉树的右视图
- HCIP第十四天
猜你喜欢
随机推荐
idea2021.1.3版本如何启动多个客户端程序
MMA安装及使用优化
解决npm -v查看npm版本出现npm WARN config global `--global`, `--local` are deprecated. Use `--location报错
PyCharm function automatically add comments without parameters
Soft exam system analysts note experience sharing: theory of protracted war
E-commerce data warehouse ODS layer-----log data loading
AI首席架构师13-AICA-智能文档分析技术在行业场景中的应用
数据一致性:双删为什么要延时?
深度学习和机器学习有什么区别?
C. awoo‘s Favorite Problem--Educational Codeforces Round 130 (Rated for Div. 2)
DO280管理和监控OpenShift平台--资源限制
From September 1st, my country has granted zero-tariff treatment to 98% of tax items from 16 countries including Togo
一些思考:腾讯股价为何持续都低
线程池的高级应用技巧核心解读
云图说丨初识华为云微服务引擎CSE
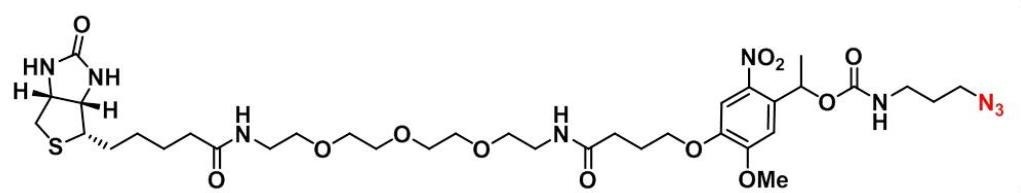
CAS: 1192802-98-4 _uv cracking of biotin - PEG2 - azide
False label aggregation
[kali-vulnerability scanning] (2.1) Nessus lifts IP restrictions, scans quickly without results, and plugins are deleted (middle)
376. Wiggle Subsequence
CAS: 773888-45-2_BIOTIN ALKYNE_生物素-炔基