当前位置:网站首页>[server data recovery] data recovery case of RAID5 crash of buddy storage
[server data recovery] data recovery case of RAID5 crash of buddy storage
2022-06-11 04:12:00 【North Asia data recovery】
Server storage failure :
Built in the same friend store raid5 The disk array crashed for an unknown reason and could not be started ,raid5 All virtual machines in are lost , among 3 The data in the virtual machine is particularly important , The administrator contacted our data recovery center to ask for this 3 Virtual machines for data recovery .
Server storage data recovery process :
1、 Analyze the storage infrastructure .
Through communication with the administrator and raid Analysis of , Understand the underlying structure of fault storage : Multiple physical disks form a storage pool and are divided into multiple disks lun, Data recovery is required lun1,lun1 Including that 3 Virtual machines . As shown in the figure below :

Storage structure
2、 restructuring raid.
When analyzing and reorganizing the array , The data recovery engineer finds that there are raid5 defect 2 Block hard disk , The hot spare has been enabled .( Restore the process in which the failure occurred : After the first hard disk is disconnected, the system starts the hot spare disk for replacement , When the second hard disk is disconnected raid5 In a degraded state , The third hard disk is disconnected, resulting in raid Array crash .) In this case, the data of the lost disk cannot be directly obtained through verification , Only full disks of the same size can be used 0 Reorganize the image ( Due to the dependence on empty images raid The structure of the file system will be seriously damaged , It is equivalent to that each strip will be missing two blocks of data , Therefore, unless special circumstances do not recommend such operation ).
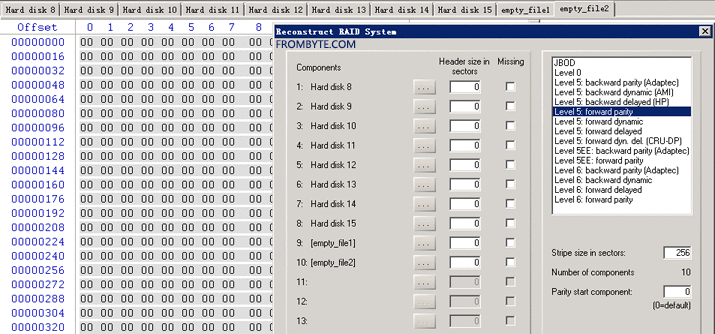
The reconstruction raid
3、 Through reorganization raid Array extraction LUN. Through the further analysis of the storage structure, we get the result of the storage partition MAP block , To each LUN The data block pointer of . North Asia data recovery engineer writes data extraction program LUN debris . After extraction, the fragments are spliced , Complete composition LUN.
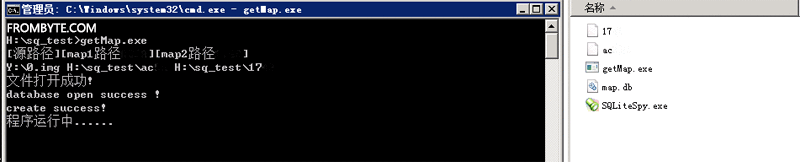
extract LUN
4、 export LUN And try to start , Because the operating system is damaged , Virtual machine failed to start .
5、 Extract the files in the virtual machine . Because the virtual machine could not start , Only files in the virtual machine can be extracted , But most of the files are seriously damaged , Only a few files are available , We have to continue to work out other data recovery schemes .
6、 Extract data by analyzing database pages . The virtual machine in this case has mysql database , You can use the particularity of the underlying storage of the database to scan data pages , Extract the data .( Both the parent disk and the snapshot file are damaged , The regular merge operation cannot complete the snapshot merge , Use the... Independently developed by North Asia VMFS The snapshot merging program performs snapshot merging .) The screenshot of the data recovery process is as follows :

7、 obtain mysql Data page and analyze . according to mysql Data page features scan and export data pages (innodb The engine can use this scheme ;myisam Because no “ Data pages ” The concept , So this solution is not available ), Analyze the system table to obtain the information of each user table , According to the... Of each table id Split the data page .
8、 Extract table structure 、 Extract record . Because the database has been used for a long time , The table structure has also changed many times , In addition, some data of the system table is lost after the storage is damaged , There is a lot of resistance in the record extraction process . First, get the table structure of each table in the original version of the database : The parent disk before the snapshot was merged because it was written earlier , Use the first drop disk for verification to obtain the complete data of this file , Then extract the table structure of each table in the database , After that, the administrator provides the latest version of database table creation script . Two groups of different table structures are used to extract data records and import them into the recovery environment mysql In the database , Then eliminate the garbled data caused by the change of table structure in each table , Finally, the two sets of data are exported as .sql file .
9、 data validation . Because the database table structures of the two versions are different , So the administrator contacts the application engineer for debugging . Import the platform after debugging , Platform debugging succeeded , The data recovery is completed .
边栏推荐
- This artifact is highly recommended. One line command will convert the web page to PDF!
- B - wall painting (C language)
- Source Insight 4.0设置注释与反注释的快捷键
- Composition and configuration of GPS Beidou clock synchronization (satellite time synchronization system) in power plant
- SQL injection correlation analysis
- FreeRTOS startup - based on stm32
- Vulkan-官方示例解读-RayTracingShadows&在这里边使用模型(1)
- Eth Of Erc20 And Erc721
- Unity prefab scene conflict merge tool unityyamlmerge
- Management system of College Students' associations based on SSM
猜你喜欢

Evil CSRF

AI助力,释放法务势能!iTerms合同智审系统重磅发布

Source Insight 4.0设置注释与反注释的快捷键

L'avenir est venu, l'ère 5G - Advanced s'ouvre

雷达辐射源调制信号仿真

2022 love analysis · privacy computing vendor panoramic report | love Analysis Report

Safe and borderless, Guanghe tongdai 5g module +ai intelligent security solution shines at CPSE Expo

超简单 CameraX 人脸识别效果封装

直播助力杭州电商独角兽冲击上市,分账系统重构电商交易新格局

Eth Transfer
随机推荐
关于重复发包的防护与绕过
Docker uses PXC to build a MySQL Cluster (mysql:5.7.24)
Methods to detect whether PHP websites have been broken
How to invest in programming knowledge and reduce the impact of knowledge failure
Esp32 porting lvgl
华生·K的秘密日记
Market prospect analysis and Research Report of single photon counting detector in 2022
Programming battle -- challenging college entrance examination questions
CES 2022 𞓜 guanghetong LTE module fm101 has obtained two important ce/fcc certifications with excellent performance
Embedded basic interface SDIO
Esp32 development -lvgl display picture
Embedded basic interface UART
MAUI 遷移指南
店铺门面转让出租小程序开发制作功能介绍
Fundamentals of embedded audio processing
Unity prefab scene 冲突合并工具 UnityYAMLMerge
From function test to advanced automation test, I stayed up 7 days to sort out this 3000 word super complete learning guide [with network disk resources]
Docker builds a redis Cluster - three machines, three masters and three slaves
Esp32 development -lvgl uses internal and external fonts
Source insight 4.0 setting shortcut keys for comments and uncomments