当前位置:网站首页>About dos/ddos attack and defense
About dos/ddos attack and defense
2022-06-23 05:25:00 【Johnny, me】
About DOS attack
- DOS An attack is also called a denial of service attack
- The principle is
- Simulate normal user access , But the traffic is huge
- Consume a lot of server resources , Resources such as server load and network bandwidth are always limited
- When an attack occurs , The server will affect the access of normal users , You can't serve them
- It seems to the user that the server service is down , In fact, the server is dealing with a large number of requests sent by attackers
- Its types are
- 1 ) according to TCP Semi connection of the protocol :TCP Half a connection
- The normal handshake is three times , The attacker only launches once , The server is forced to wait for the attacker's next connection
- When an attack occurs , The server generates many half connections to occupy resources
- 2 ) HTTP Connect , It looks like a normal request , It's really asking for your service
- But your service capacity is limited , Unable to cope with too many requests
- 3 ) DNS attack , If the server is very defensive , Can shut out many illegal requests
- Then the attacker may turn to attack you DNS Domain name resolution server , commonly DNS Low access load
- Generally speaking, the access load is not so large , attack DNS Is a very effective means of attack
- stay DOS There is also an attack called DDOS
- Large scale distributed denial of service attacks
- DOS Generally, only a few machines launch attacks
- DDOS There may be a large number of machines to attack , Its flow can reach tens to hundreds G
- These flows are distributed , Through broilers and agents
- Extremely difficult to defend , Unable to distinguish between normal traffic and attack traffic
- If we can distinguish by some special high-level knowledge , But there is no effective defense
Related attack cases
- The game was attacked on a large scale before it was put on the shelves , Game servers interact with each other DDOS attack
- The attack will not come down , Change to attack DNS The server , Lead to DNS Server offline
- Hundreds of thousands of websites DNS Analytic paralysis , Because it's hard to respond , Some software backstage is madly disconnected and reconnected
- by DNS Added some traffic , worse , Leading to the disconnection of many provinces in China
- This is a very vicious event
How to defend
- In fact, it is very difficult to defend , But there are still things you can do , such as
- Hardware firewall , Try filtering some traffic
- The corresponding traffic filtering mechanism of switches and routers
- Flow cleaning : In general terms , Including firewall and router , Switches can do
- Specifically, flow analysis , Find the characteristics of attack traffic and normal traffic respectively
- High prevention IP( Business services ): Services provided by cloud service providers
- When attacked , It will give you one ip, Let your domain name point to this ip
- Both users and attackers will access this ip, This ip The latter corresponds to a large-scale flow cleaning service
- It will intercept attack traffic and leave normal traffic , At the same time, cloud service providers provide very large bandwidth
- It's better to deal with DDOS attack
- In fact, these defense methods are limited defense programs , We should also take precautions during development
- 1 ) Pay attention to light logic and split heavy logic
- The higher the bearing capacity of the server , The more attacks you can withstand
- such , We can avoid the logic business when developing
- That is to say , This logic should be able to be completed quickly when the user accesses
- When logic is light enough , The greater the access capacity that can be carried , The possibility of being captured will be much smaller
- If there is some time-consuming logic , You can split the business , Process by queuing , It is common to use asynchronous frameworks
- 2 ) In case of failure , Should fail quickly , Come back quickly , Reduce the number of retries
- Because the higher the load , Increase the number of attempts , The more likely it is to fail
- 3 ) Anti avalanche mechanism
- For example, the more retries , The more you fail , This can only be a vicious circle
- In terms of mechanism, it means , Fast failure , Come back quickly
- Clearly understand the load of the system , When the number of requests reaches the limit , You have to intercept some requests , Will not collapse
- 4 ) Damaging service
- Allow abnormal business , Allow imperfections , When a service collapses, it does not affect other services
- 5 ) adopt CDN service
- Distribute some static files to CDN Up , Reduce server load
- For dynamic requests ,CDN The performance is not very ideal , If any , Use as much as possible CDN service
边栏推荐
猜你喜欢

MCS: continuous random variable - student's t distribution
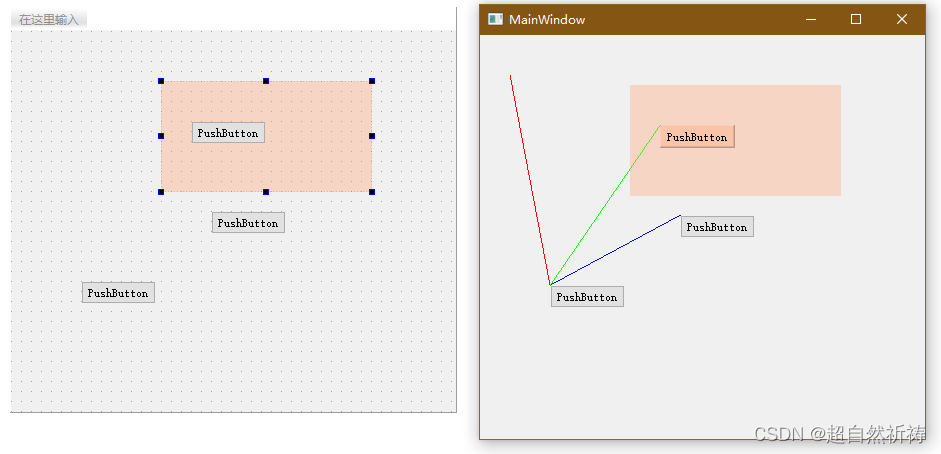
Qt QWidget嵌套相对位置获取 (qt 画线 嵌套)
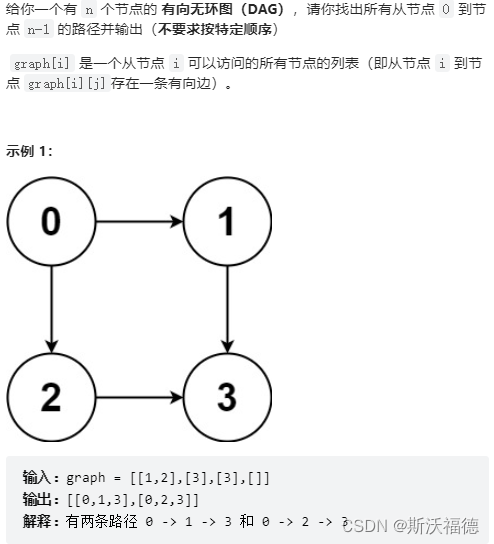
LeetCode 797:所有可能的路径

Jenkins安装部署以及自动构建和发布jar应用

云原生数据库是未来数据库的天下
Difficult to find a job in a bad environment? Ali on three sides. Fortunately, he has made full preparations and has offered

Zygote process

ES6的Array.from方法创建长度为N的undefined数组

A bug in rtklib2.4.3 B34 single point positioning

MCS:连续随机变量——LogNormal分布
随机推荐
MCS:连续随机变量——Student’s t分布
人脸识别 确定阈值
左侧固定,右侧自适应 三种实现办法(Flex,float + BFC ,float-margin-left)
PHP move_ uploaded_ File failed to upload mobile pictures
Jetpack Compose 从开门到入门之 MenuBar桌面菜单(Desktop Menu)
Introduction to JDBC (IV) - use of Druid connection pool
JDBC入门学习(三)之事务回滚功能的实现
第十六届东北地区大学生程序设计竞赛(热身赛)B-String Value(字符串dp)
Get bat command results in bat
AMS:startActivity桌面启动应用
CF【1700D】D. River Locks(dp、二分、数学)
Mysql入门学习(一)之语法
MCS:连续随机变量——LogNormal分布
Qt QWidget嵌套相对位置获取 (qt 画线 嵌套)
Jenkins安装部署以及自动构建和发布jar应用
Drama asking Huamen restaurant Weng
面对新的挑战,成为更好的自己--进击的技术er
Fund performance evaluation
关于信息泄露和防御
pkav简单爆破