当前位置:网站首页>SQL injection less24 (secondary injection)
SQL injection less24 (secondary injection)
2022-07-26 22:17:00 【Happy star】
The principle of secondary injection
The secondary injection ( Memory injection ), The principle of this technique is : When the website processes the data submitted by users , Just escaped some sensitive characters . Therefore, the user will not be executed as code when submitting for the first time . however These data are stored in the database without escape ( For example, the data entered by the user is admin'#, When executing code, it will escape to admin\'#, The data stored in the database is still admin'#), By default, the data in the database of the website program is safe , When the website program calls the dirty data just stored for the second time , Instead of escaping, it is used directly , Therefore, the effect of injection will be achieved .
Pay attention to two points :
1、 The website will store the data intact in the database .
2、 The website will directly call the data in the database without detecting it .( Trust the data in the database )
When inserting data into the database for the first time , Used addslashes 、get_magic_quotes_gpc、mysql_escape_string、mysql_real_escape_string And other functions escape the special characters , however addslashes One feature is that although parameters will be added after filtering “\” Transference , however “\” It's not inserted into the database , The original data is still written to the database . After storing the data into the database , Developers think the data is credible . The next time you need to query , The dirty data is directly extracted from the database , No further inspection and treatment , This will cause SQL The second injection of .
- First step : Insert malicious data
When inserting data into the database , The special characters are escaped , When writing to the database, the original data is retained . - The second step : Quoting malicious data
By default, the data stored in the database is safe , When making a query , Extract malicious data directly from the database , Treatment without further inspection . There is no escape operation , But directly spliced to SQL Execute in statement .
Less24 Black box
A user login interface , You can register new users and log in .
Let's log in Dumb:Dumb to glance at 
You can change the password
Let's take a look at our current users surface 
We register a new user admin'#, The password for 123456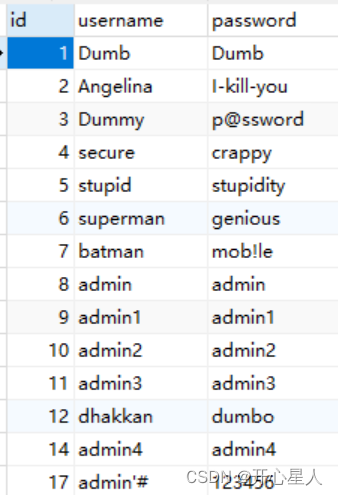
admin'# The original data is directly stored in the database
We log in admin'# user , Change the password 
Change the password to nihao
But found admin The user's password changes to nihao
Then we got admin:nihao, You can log in to this account . That's what we want to do
Less24 White box
Registered users
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
if (isset($_POST['submit']))
{
# Validating the user input........
//$username= $_POST['username'] ;
$username= mysql_escape_string($_POST['username']) ;
$pass= mysql_escape_string($_POST['password']);
$re_pass= mysql_escape_string($_POST['re_password']);
echo "<font size='3' color='#FFFF00'>";
$sql = "select count(*) from users where username='$username'";
$res = mysql_query($sql) or die('You tried to be smart, Try harder!!!! :( ');
$row = mysql_fetch_row($res);
//print_r($row);
if (!$row[0]== 0)
{
?>
<script>alert("The username Already exists, Please choose a different username ")</script>;
<?php
header('refresh:1, url=new_user.php');
}
else
{
if ($pass==$re_pass)
{
# Building up the query........
$sql = "insert into users ( username, password) values(\"$username\", \"$pass\")";
mysql_query($sql) or die('Error Creating your user account, : '.mysql_error());
echo "</br>";
echo "<center><img src=../images/Less-24-user-created.jpg><font size='3' color='#FFFF00'>";
//echo "<h1>User Created Successfully</h1>";
echo "</br>";
echo "</br>";
echo "</br>";
echo "</br>Redirecting you to login page in 5 sec................";
echo "<font size='2'>";
echo "</br>If it does not redirect, click the home button on top right</center>";
header('refresh:5, url=index.php');
}
else
{
?>
<script>alert('Please make sure that password field and retype password match correctly')</script>
<?php
header('refresh:1, url=new_user.php');
}
}
}
?>
Escape the data entered by the user
$username= mysql_escape_string($_POST['username']) ;
$pass= mysql_escape_string($_POST['password']);
$re_pass= mysql_escape_string($_POST['re_password']);
Insert database
insert into users ( username, password) values(\"$username\", \"$pass\")
Why is the original data inserted instead of the escaped data , I think it should be the internal operation of the database , The escape character is automatically removed \.
Why escape , To prevent users from SQL Inject
Change Password
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
if (isset($_POST['submit']))
{
# Validating the user input........
$username= $_SESSION["username"];
$curr_pass= mysql_real_escape_string($_POST['current_password']);
$pass= mysql_real_escape_string($_POST['password']);
$re_pass= mysql_real_escape_string($_POST['re_password']);
if($pass==$re_pass)
{
$sql = "UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass' ";
$res = mysql_query($sql) or die('You tried to be smart, Try harder!!!! :( ');
$row = mysql_affected_rows();
echo '<font size="3" color="#FFFF00">';
echo '<center>';
if($row==1)
{
echo "Password successfully updated";
}
else
{
header('Location: failed.php');
//echo 'You tried to be smart, Try harder!!!! :( ';
}
}
else
{
echo '<font size="5" color="#FFFF00"><center>';
echo "Make sure New Password and Retype Password fields have same value";
header('refresh:2, url=index.php');
}
}
?>
The data entered by the user is also escaped
$curr_pass= mysql_real_escape_string($_POST['current_password']);
$pass= mysql_real_escape_string($_POST['password']);
$re_pass= mysql_real_escape_string($_POST['re_password']);
But notice , there username It's taken directly , There is no escape operation !!!
If the username Escaped , There will be no secondary injection vulnerability
UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass'
https://blog.csdn.net/hhhhhhhhh85/article/details/121328475
https://blog.csdn.net/weixin_43901998/article/details/107288123
边栏推荐
猜你喜欢

TASK04|分类分析

新兴市场潜力无限,ADVANCE.AI风控产品助中国出海企业筑牢安全发展基础

Flink's real-time data analysis practice in iFLYTEK AI marketing business

Let me show you the MySQL isolation level. What happens when two transactions operate on the same row of data at the same time?
Summary of debugging stc8a8k64d4 MCU 485 communication

SQL注入 Less24(二次注入)

Implementation of MATLAB short-time autocorrelation

Unity对资源管理器操作 打开资源管理器选择文件并筛选文件

08 du 命令

matlab 画短时能量图
随机推荐
Software Testing Technology: cross platform mobile UI automated testing (Part 2)
Get network time by unity
C# 数据类型_摘自菜鸟教程
正则表达式及绕过案例
iptables防止nmap扫描以及binlog实现增量备份
My SQL is OK. Why is it still so slow? MySQL locking rules
Summary of debugging stc8a8k64d4 MCU 485 communication
Method overloading and method rewriting
09 expr 命令
When deploying Flink on a single machine and creating the connection table of oracle19c RAC, the error ora-12505 is reported. Who can help
Concept and classification of processes
JS 延迟执行window.onload
新兴市场潜力无限,ADVANCE.AI风控产品助中国出海企业筑牢安全发展基础
Redis 分布式锁 + Lua原子操作
Pytoch -- used by visdom
[horizon sunrise X3 sect trial experience] + unpacking post
Actual authority comes from information superiority
Protobuf之proto基础语法
Excel VBA quick start (XII. Common usage of like comparison)
unity 获取网络时间