当前位置:网站首页>Calculate the odd sum of 1~n (1~100 as an example)
Calculate the odd sum of 1~n (1~100 as an example)
2022-07-04 03:33:00 【Yueyechong】
n=int(input())
sum=0
for i in range(1,n+1,2):
sum+=i
print(sum)Input 100 have to 2500
utilize range function :range(1,5,2) # For from 1 To 5, interval 2( It doesn't contain 5)
Method 2: use while,matlab Thought
b=int(input())
n=1
sum=0
while n<b:
sum+=n
n+=2
print(sum)Method 3
n=int(input())
sum=0
ls=[]
for i in range(1,n+1):
if i %2!=0:
sum+=i
print(sum)Method 5: If you want to check the inside
n=int(input())
sum=0
ls=[]
for i in range(1,n+1):
if i %2!=0:
sum+=i
ls.append(i)# Show list , Beginners can't debug Internal numbers can be displayed in a list
print(ls)# Show the numbers
print(sum)Is the number correct , It can be displayed in a list
边栏推荐
- CSP drawing
- Unity knapsack system (code to center and exchange items)
- Ningde times and BYD have refuted rumors one after another. Why does someone always want to harm domestic brands?
- PMP 考試常見工具與技術點總結
- Setting methods, usage methods and common usage scenarios of environment variables in postman
- Unity controls the selection of the previous and next characters
- [untitled]
- (practice C language every day) pointer sorting problem
- Setting methods, usage methods and common usage scenarios of environment variables in postman
- XSS prevention
猜你喜欢
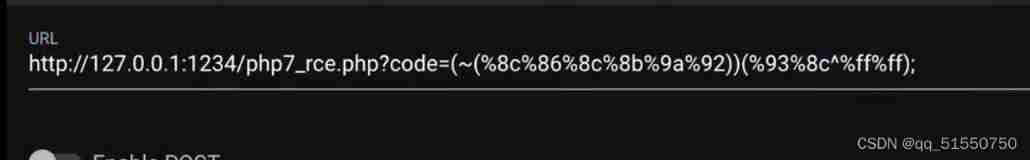
Code Execution Vulnerability - no alphanumeric rce create_ function()

Setting methods, usage methods and common usage scenarios of environment variables in postman
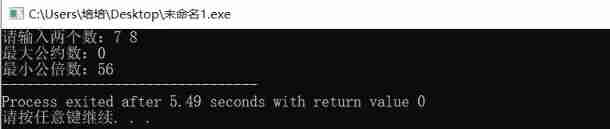
(column 23) typical C language problem: find the minimum common multiple and maximum common divisor of two numbers. (two solutions)

Recursive structure

96% of the collected traffic is prevented by bubble mart of cloud hosting
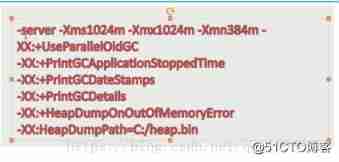
JVM family -- heap analysis

Defensive programming skills
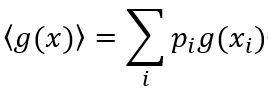
長文綜述:大腦中的熵、自由能、對稱性和動力學
No clue about the data analysis report? After reading this introduction of smartbi, you will understand!
How about the ratings of 2022 Spring Festival Gala in all provinces? Map analysis helps you show clearly!
随机推荐
System integration meets the three business needs of enterprises
Contest3145 - the 37th game of 2021 freshman individual training match_ D: Ranking
2022 examination summary of quality controller - Equipment direction - general basis (quality controller) and examination questions and analysis of quality controller - Equipment direction - general b
Contest3145 - the 37th game of 2021 freshman individual training match_ 1: Origami
1day vulnerability pushback skills practice (3)
Backpropagation formula derivation [Li Hongyi deep learning version]
CUDA basic knowledge
Package details_ Four access control characters_ Two details of protected
Future源碼一觀-JUC系列
Webhook triggers Jenkins for sonar detection
[database I] database overview, common commands, view the table structure of 'demo data', simple query, condition query, sorting data, data processing function (single row processing function), groupi
Www 2022 | taxoenrich: self supervised taxonomy complemented by Structural Semantics
2022 Guangxi provincial safety officer a certificate examination materials and Guangxi provincial safety officer a certificate simulation test questions
Dare to climb here, you're not far from prison, reptile reverse actual combat case
基於.NetCore開發博客項目 StarBlog - (14) 實現主題切換功能
[latex] production of complex tables: excel2latex and detail adjustment
Development of digital collection trading platform development of digital collection platform
SQL injection (1) -- determine whether there are SQL injection vulnerabilities
Management and thesis of job management system based on SSM
Love and self-discipline and strive to live a core life