Code audit essential skills ,github Code comparison , Write a stroke :
Search for an open source build vulnerability , Search out a certain version rce:

From the message : There is a vulnerable version :1.10.10 , Fix vulnerable version 1.10.11
Go to github seek apache-airflow:
Open is the main branch :
Switch to the vulnerability version Branch :
There are two ways :
(1)https://github.com/apache/airflow/tags
One by one , Turn to the corresponding version , Pull down
(2) Search for Tags Branch , Switch branches :

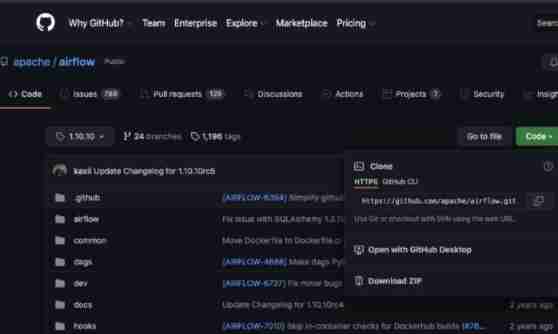
Switch over and :
Switch branches to download corresponding version items :
git clone -b 1.10.10 https://github.com/apache/airflow.git
In this way, the vulnerable version is downloaded , The repair version is 1.10.11
Download the repair version :
git clone -b 1.10.11 https://github.com/apache/airflow.git
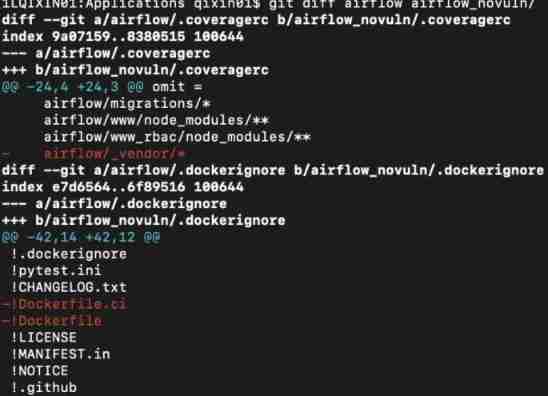
After downloading, you can use
git diff Folder 1 Folder 2:In this way, you can see which files have been modified :
In addition to downloading and checking , You can also view the comparison directly on the web :
https://github.com/apache/airflow/compare/1.10.10...1.10.11?diff=split
You can see 1.10.10~1.10.11 Between submissions Commits And modified documents :

View code modification , On the left is before repair , On the right is the repaired code fragment :

Problems encountered :Commit That's too much , There are too many files for version update iteration , Now , How can we locate which is the problem file ?
(1) Ideal state : The third-party vulnerability warning platform provides corresponding vulnerabilities Commit Submit the record
(2) Only certain vulnerability types are known , Such as sql Injection type /rce type
Most of them are 2, If it is 1 The situation of , Look directly at the corresponding Commit Just submit the record , Don't try so hard
If it is 2, Only know what to do with the vulnerability type ?
Illustration :git diff coordination grep:
git diff airflow airflow_novuln/ | grep "command" > aa.txt
Search for some code snippets in the vulnerability version project :
grep -rn "echo \"Here is the message: '" ./

Find the vulnerability file , If there's a better way , Please leave a message !