当前位置:网站首页>A. ABC
A. ABC
2022-07-04 01:48:00 【Felven】
time limit per test
1 second
memory limit per test
256 megabytes
input
standard input
output
standard output
Recently, the students of School 179 have developed a unique algorithm, which takes in a binary string ss as input. However, they soon found out that if some substring tt of ss is a palindrome of length greater than 1, the algorithm will work incorrectly. Can the students somehow reorder the characters of ss so that the algorithm will work correctly on the string?
A binary string is a string where each character is either 0 or 1.
A string aa is a substring of a string bb if aa can be obtained from bb by deletion of several (possibly, zero or all) characters from the beginning and several (possibly, zero or all) characters from the end.
A palindrome is a string that reads the same backwards as forwards.
Input
Each test contains multiple test cases. The first line contains the number of test cases tt (1≤t≤1001≤t≤100). Description of the test cases follows.
The first line of each test case contains a single integer nn (1≤n≤1001≤n≤100) — the length of the string ss.
The second line of each test case contains the string ss of length nn consisting only of the characters 0 and 1.
Output
For each test case, print YES (case-insensitive) if it is possible to reorder the characters of ss so that there are no substrings that are a palindrome of length greater than 1, or NO (case-insensitive) otherwise.
Example
input
Copy
4 1 1 2 10 2 01 4 1010
output
Copy
YES YES YES NO
Note
In the first three test cases, the given strings do not contain palindromes of length greater than 1, so the answers are YES.
In the last test case, it is impossible to reorder the characters so that the string does not contain palindromes of length greater than 1, so the answer is NO.
Problem solving instructions : This problem is a simulation problem , Analyzing the meaning of the question, we can find that as long as the length exceeds 3 It is impossible to meet the requirements , When the length is 2 You must also ensure that the two numbers are not consistent .
#include <stdio.h>
char s[107];
int main()
{
int t;
scanf("%d", &t);
for (int i = 1; i <= t; i++)
{
int n;
scanf("%d", &n);
scanf("%s", &s[1]);
if (n == 1 || (n == 2 && s[1] != s[2]))
{
printf("YES\n");
}
else
{
printf("NO\n");
}
}
return 0;
}边栏推荐
- What are the advantages and disadvantages of data center agents?
- C import Xls data method summary IV (upload file de duplication and database data De duplication)
- 1189. Maximum number of "balloons"
- How to use AHAS to ensure the stability of Web services?
- ES6 deletes an attribute in all array objects through map, deconstruction and extension operators
- Stringutils and collectionutils
- be based on. NETCORE development blog project starblog - (14) realize theme switching function
- Is Shengang securities company as safe as other securities companies
- Huawei cloud micro certification Huawei cloud computing service practice has been stable
- Jerry's watch listens to the message notification of the target third-party software and pushes the message to the device [article]
猜你喜欢

SQL statement
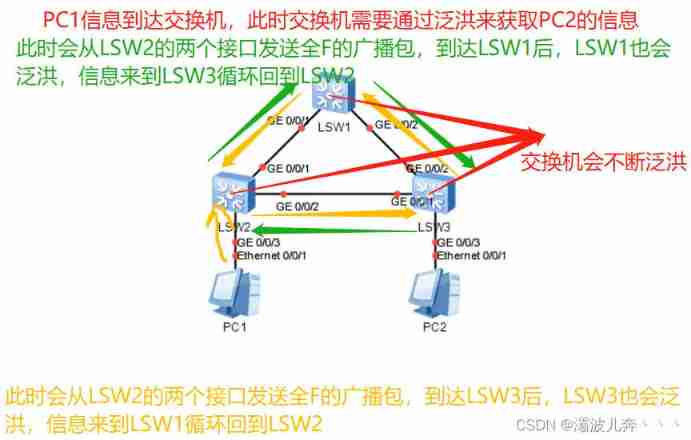
Three layer switching ②

String hash, find the string hash value after deleting any character, double hash

Yyds dry goods inventory it's not easy to say I love you | use the minimum web API to upload files
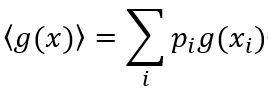
Long article review: entropy, free energy, symmetry and dynamics in the brain
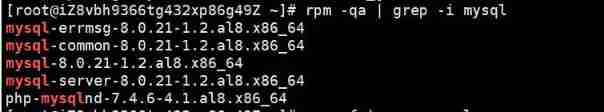
How to delete MySQL components using xshell7?
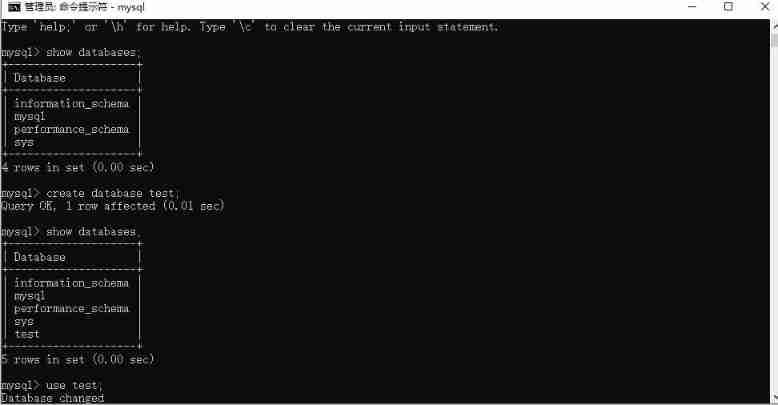
MySQL statement learning record

Lightweight Pyramid Networks for Image Deraining
Gee: create a new feature and set corresponding attributes

AI helps make new breakthroughs in art design plagiarism retrieval! Professor Liu Fang's team paper was employed by ACM mm, a multimedia top-level conference
随机推荐
Why is the operation unsuccessful (unresolved) uncaught syntaxerror: invalid or unexpected token (resolved)
Small program graduation project based on wechat examination small program graduation project opening report function reference
HackTheBox-baby breaking grad
Solution of cursor thickening
Bacteriostatic circle scanning correction template
What is the student party's Bluetooth headset recommendation? Student party easy to use Bluetooth headset recommended
Pytoch residual network RESNET
Software product download collection
Audio resource settings for U3D resource management
Lightweight Pyramid Networks for Image Deraining
The reasons why QT fails to connect to the database and common solutions
Notice on Soliciting Opinions on the draft of information security technology mobile Internet application (APP) life cycle security management guide
Future source code view -juc series
Example 073 square sum value judgment programming requires the input of a and B, if a ²+ b ² If the result of is greater than 100, a is output ²+ b ² Value, otherwise output the result of a + B.
[leetcode daily question] a single element in an ordered array
Which insurance products can the elderly buy?
Douban scoring applet Part-3
Example 072 calculation of salary it is known that the base salary of an employee of a company is 500 yuan. The amount of software sold by the employee and the Commission method are as follows: Sales
Development of user-defined navigation bar in uniapp
Feign implements dynamic URL