当前位置:网站首页>Nbear introduction and use diagram
Nbear introduction and use diagram
2022-07-04 03:23:00 【Brother Lei talks about programming】
NBear Introduction and use diagram
Frame type :ORM Mapping framework
brief introduction :NBear It's based on .Net 2.0、C#2.0 Open all source code software development framework class library .NBear The design goal of is to try our best to reduce the workload of developers , Maximize development efficiency , At the same time, both performance and scalability .
Demo edition : NBear 1.0.1.5 + MsSql 2005 + Vs 2010[net framework 3.5]
Download address :【①. Nbear download ②. Ben Demo download 】
Using diagrams
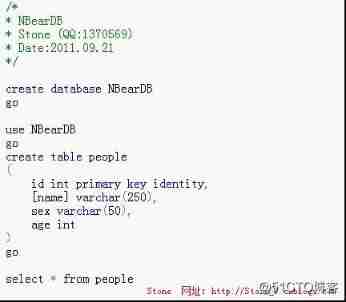
1. establish Demo database 、 surface
2. Create a new website and add NBear quote

New website ==> add to NBear quote NBear.Core.dll、NBear.Mapping.dll、NBearLite.dll(dll Position in download NBear Of dist\... Folder ) Right click the solution to add a new item ==> Name the new class library Com.uuu9.NBear Delete Class1, Add Com.uuu9.NBear Class library reference .
3. Generate entity class code , To configure web.config
The next step is to generate entity classes , The generator is in download NBear Of dist\... Folder , The name is :NBearLite.QueryColumnsGenerator.exe, Double-click on the run , Pictured :
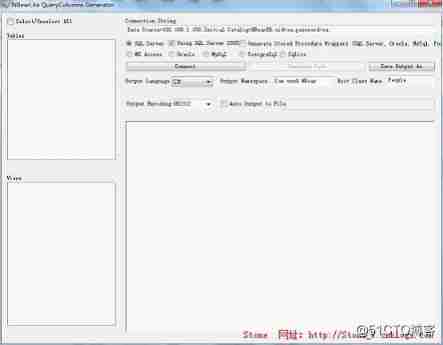
The built-in code generator is very simple and convenient , If you can understand it, you don't need to read the following introduction , Are very basic introductions . stay Connection String Next, enter the connection string , choice SQL Server ==> Hook in Using SQL Server 2005( Database users can choose according to their own needs ), Click on Connect Button connection , If connected as , On the left Tables The table name will be displayed in the box , Select the... To generate People surface , Configure the language to be output Output Language by C#, Fill in the output namespace Output Namespace, Entity class name Root Class Name by People, Click on
Generate Code The generated code , And then click Save Output As Button select the storage path as this Demo Next , Then refresh the project , You can see and use the generated People Entity class .
web.config The configuration of is the same as that of a common project configuration connection string , stay ConnectionStrings Nodes are added underground <add name="NBearDB" connectionString="Data Source=192.168.1.150;Initial Catalog=NBearDB;uid=sa;password=sa;"/> Just connect the string , Other configurations will be fine by default . The connection string configured here name="NBearDB", wait NBear You need to use , There are no special requirements for naming here .
4.NBear Grammar use .
The grammar is as follows :
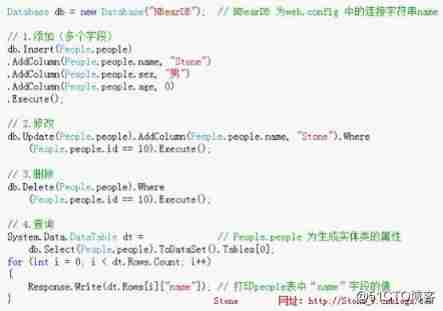

 View Code
View Code
I don't like grammar very much , Let's make our own choices , thus NBear The simple use of has been completed .
Download address :【①. Nbear download ②. Ben Demo download 】
Follow the QR code below , Subscribe to more .

边栏推荐
- Solve the problems encountered by the laravel framework using mongodb
- Jenkins continuous integration environment construction V (Jenkins common construction triggers)
- 2022 examination summary of quality controller - Equipment direction - general basis (quality controller) and examination questions and analysis of quality controller - Equipment direction - general b
- Contest3145 - the 37th game of 2021 freshman individual training match_ F: Smallest ball
- Remote work guide
- In my spare time, I like to write some technical blogs and read some useless books. If you want to read more of my original articles, you can follow my personal wechat official account up technology c
- Consul of distributed service registration discovery and unified configuration management
- 96% of the collected traffic is prevented by bubble mart of cloud hosting
- Www 2022 | taxoenrich: self supervised taxonomy complemented by Structural Semantics
- Add token validation in swagger
猜你喜欢

Www 2022 | taxoenrich: self supervised taxonomy complemented by Structural Semantics
Jenkins continuous integration environment construction V (Jenkins common construction triggers)
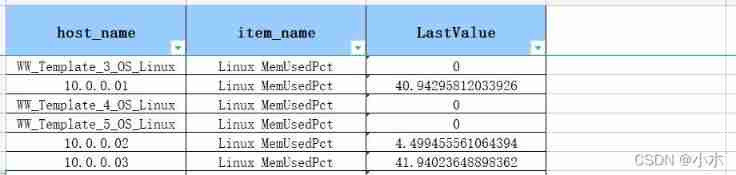
ZABBIX API pulls the values of all hosts of a monitoring item and saves them in Excel
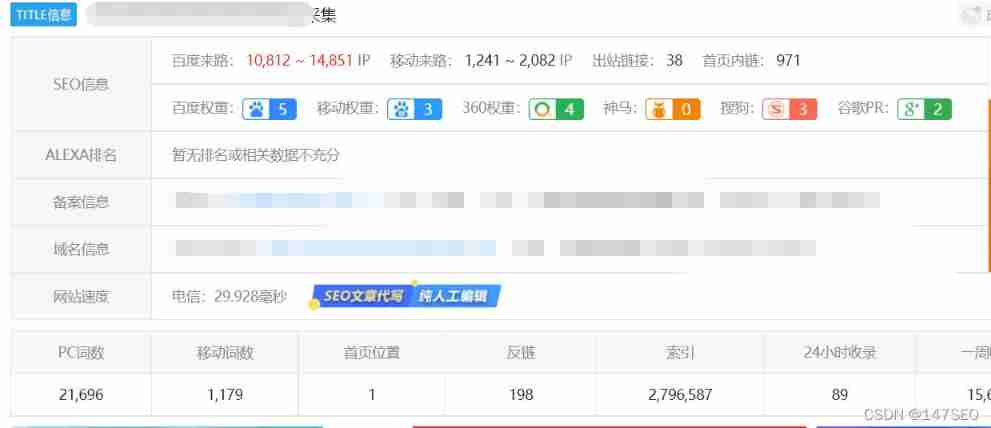
Zblog collection plug-in does not need authorization to stay away from the cracked version of zblog

Add token validation in swagger

96% of the collected traffic is prevented by bubble mart of cloud hosting
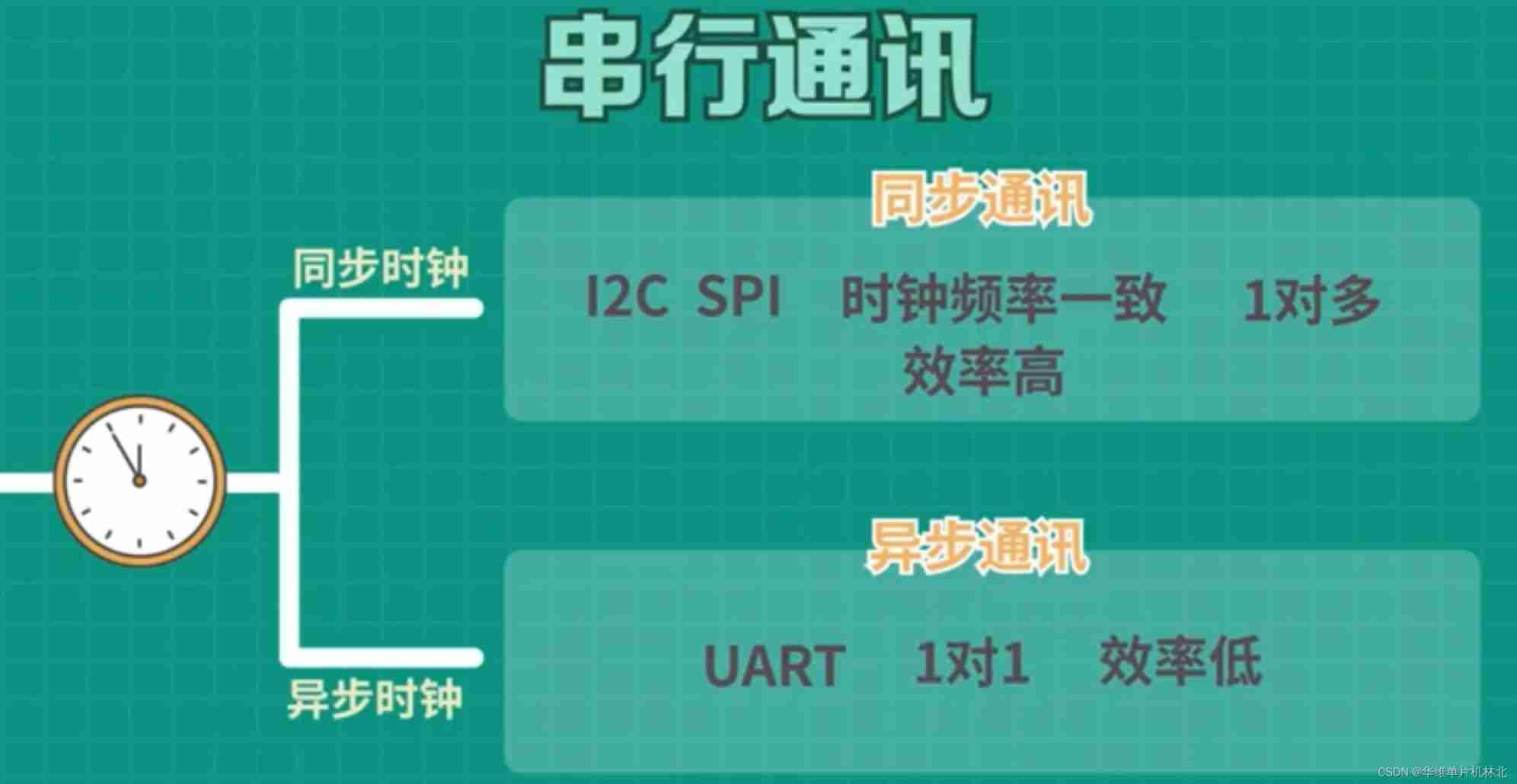
The difference between MCU serial communication and parallel communication and the understanding of UART

Setting methods, usage methods and common usage scenarios of environment variables in postman
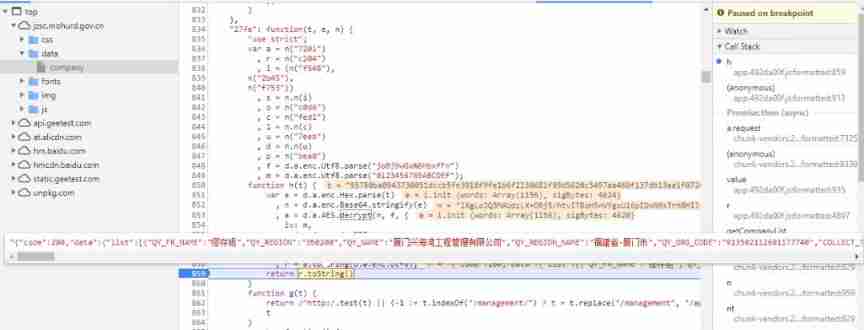
Dare to climb here, you're not far from prison, reptile reverse actual combat case
Session learning diary 1
随机推荐
I stepped on a foundation pit today
VRRP+BFD
Record a problem that soft deletion fails due to warehouse level error
SQL injection (1) -- determine whether there are SQL injection vulnerabilities
Zigzag scan
150 ppt! The most complete "fair perception machine learning and data mining" tutorial, Dr. AIST Toshihiro kamishima, Japan
What are the conditions for the opening of Tiktok live broadcast preview?
Ai aide à la recherche de plagiat dans le design artistique! L'équipe du professeur Liu Fang a été embauchée par ACM mm, une conférence multimédia de haut niveau.
機器學習基礎:用 Lasso 做特征選擇
2022 registration examination for safety production management personnel of fireworks and firecracker production units and examination skills for safety production management personnel of fireworks an
What is cloud primordial?
Explain AI accelerator in detail: why is this the golden age of AI accelerator?
Slurm view node configuration information
Summary of Chinese remainder theorem
Solve the problem that the tabbar navigation at the bottom of vantui does not correspond to the page (window.loading.hash)
Have you entered the workplace since the first 00???
The "message withdrawal" of a push message push, one click traceless message withdrawal makes the operation no longer difficult
Imperial cms7.5 imitation "D9 download station" software application download website source code
[untitled] the relationship between the metauniverse and digital collections
Command Execution Vulnerability - command execution - vulnerability sites - code injection - vulnerability exploitation - joint execution - bypass (spaces, keyword filtering, variable bypass) - two ex