当前位置:网站首页>System call capture and analysis conclusion making system call log collection system
System call capture and analysis conclusion making system call log collection system
2022-07-26 11:43:00 【H4ppyD0g】
This article is about learning relevant knowledge in the process of graduation design 、 Complete notes from hands-on practice , By reading this series , You can understand the underlying principles of system calls from a zero basis and intercept system calls . Due to my limited ability , Some error messages may appear in the article , Please correct me if there is any mistake . in addition , All contents of this series are only used as notes for personal study and research , Reprint please indicate the source . Thank you for your attention ! This is also a series of articles highly recommended by the author !
A complete list of articles in the series
System call capture and analysis — adopt ptrace Get system call information
System call capture and analysis — adopt strace Get system call information
System call capture and analysis — Necessary system security knowledge points
System call capture and analysis — Use LKM Method to add a system call
System call capture and analysis — Modify kernel methods and add system calls
System call capture and distribution —Ring3 layer LD_PRELOAD Mechanism for library function hijacking
System call capture and analysis —Ring0 layer kprobe Hijack system calls
List of articles
Preface
Be careful : The project environment is ubuntu16.04, Source kernel version 4.15.x, Compile the kernel version 4.13.10.
in addition , Before the experiment starts, you need to download 4.13.10 Source code !!
Project architecture

Project implementation
First step , Add system calls 、 Intercept
modify /usr/src/linux-4.13.10/arch/x86/entry/syscalls/syscall_64.tbl, Add the system call number .
In the catalog /usr/src/linux-4.13.10/arch/x86/kernel/ Next add a file myaudit_sys.c, Where is the added system call , And we should export several variable symbols .
#include <linux/uaccess.h>
#include <linux/proc_fs.h>
#include <linux/init.h>
#include <linux/types.h>
#include <asm/current.h>
#include <linux/sched.h>
/* Add a system call , Used for logging program calls , from buf Get log information from ; Export two function pointers at the same time , be used for LKM Method defines the function body and calls outside the file . */
/* u8 -> unsigned byte (8 bits) u16 -> unsigned byte (16 bits) */
void (*audit_to_buf) (int, int) = NULL;
int (*audit_from_buf)(u8, u8*, u16) = NULL;
asmlinkage long sys_myaudit(u8 type, u8* us_buf, u16 us_buf_size)
{
if (audit_from_buf) {
printk("oh~ audit_from_buf() found !!\n");
return (*audit_from_buf)(type, us_buf, us_buf_size); // perform audit_from_buf() function
} else
printk("oh~ audit_from_buf() not found !!\n");
return 1;
}
EXPORT_SYMBOL(audit_to_buf);
EXPORT_SYMBOL(audit_from_buf);
modify /usr/src/linux-4.13.10/arch/x86/kernel/Makefile file , add to myaudit_sys.c Compilation of .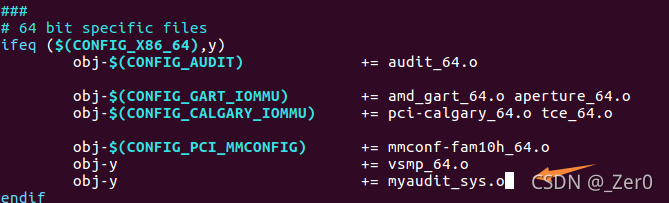
Add function declaration , edit /usr/src/linux-4.13.10/include/linux/syscalls.h file , Add... At the bottom 
Intercept system calls
modify /usr/src/linux-4.13.10/arch/x86/entry/common.c Medium do_syscall_64(struct pt_regs *regs) function .
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-9XBw7R9B-1658646740076)(images/a5625a1009a947eda0bdb8f3eaaba006.png)]
Reference external variables 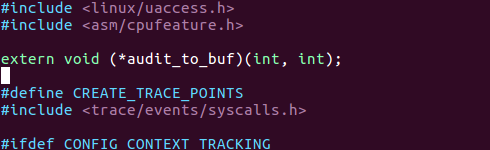
Configure compile options
First delete the files and configuration files generated by the previous compilation
sudo make mrproper
sudo make clean
To configure --> Generate .config file
sudo make menuconfig
sudo cp /boot/config-xxx -r .config These two lines of commands use the existing configuration compilation settings ,
sudo make oldconfig It's OK not to add , If an error is reported, execute again
Compilation and installation
sudo make -j5 5 Threads are faster
sudo make modules_install
sudo make install
Press on restart esc key , choice ubuntu senior , Then select the kernel just compiled to enter .
Through the command dmesg perhaps syscall( System call number ) To check for success .
#include <stdio.h>
#include <sys/syscall.h>
#include <unistd.h>
int main(){
long int res = syscall(334); 333 It is the system call number just added
printf("res = %d\n", res);
}
The second step , Add a kernel module
Writing module myaudit_module.c
#include <linux/module.h>
#include <linux/init.h>
#include <linux/kernel.h>
#include <linux/types.h>
#include <linux/time.h>
#include <linux/cred.h>
#include <asm/current.h>
#include <linux/sched.h>
#include <linux/uaccess.h>
/* pid_t -> int uid_t -> int u8 -> unsigned byte (8 bits) u32 -> unsigned byte (32 bits) */
#define COMM_LENGTH 16 // Each command has a maximum of 16 Bytes
struct Audit_buf {
u32 serial; // Record the number of logs
u32 syscall; // System call number
u32 status; // The return value of the system call
pid_t pid; // process id
uid_t uid; // user id
u8 comm[COMM_LENGTH]; // command
};
// Create a waiting queue header
DECLARE_WAIT_QUEUE_HEAD(buffer_wait);
//audit Information buffer definition
#define AUDIT_BUF_SIZE 20
static struct Audit_buf audit_buf[AUDIT_BUF_SIZE]; //audit Information buffer
static int current_pos = 0;
static u32 serial = 0; // The number of data recorded
// Introduce system call function pointer
extern void (*audit_to_buf)(int, int);
extern int (*audit_from_buf)(unsigned char, unsigned char *, unsigned short);
void audit_to_buf_body(int syscall, int return_status)
{
struct Audit_buf * ppb_temp; // Traverse audit_buf Pointer to array
if(current_pos < AUDIT_BUF_SIZE) {
ppb_temp = &audit_buf[current_pos];
ppb_temp->serial = serial++;
ppb_temp->syscall = syscall;
ppb_temp->status = return_status;
ppb_temp->pid = current->pid;
ppb_temp->uid = current_uid().val;
memcpy(ppb_temp->comm, current->comm, COMM_LENGTH);
if(current_pos++ == AUDIT_BUF_SIZE*8/10) {
// The queue is almost full , Activate the waiting that is blocking
printk("oh~ audit_buf is nearly full !!\n");
wake_up_interruptible(&buffer_wait);
}
}
}
int audit_from_buf_body(u8 type, u8 * usr_buf, u16 usr_buf_size)
{
int ret = 0;
if(!type) {
if(__clear_user(usr_buf, usr_buf_size)) {
// Empty user space memory , Return cannot be cleared 0 Bytes of
printk("oh~ Error: can not zero all buf !!\n");
return 0;
}
printk("oh~ in kernel module audit_from_buf_body starting !!\n");
ret = wait_event_interruptible(buffer_wait, current_pos >= AUDIT_BUF_SIZE*8/10); // Blocking
//printk("oh~ in kernel module current_pos is %d !!\n", current_pos);
if(__copy_to_user(usr_buf, audit_buf, (current_pos)*sizeof(struct Audit_buf))) {
// from audit_buf Take out all at once
printk("oh~ Error: copy error !!\n");
return 0;
}
ret = current_pos - 1;
current_pos = 0;
}
return ret;
}
static int __init audit_init(void)
{
audit_from_buf = audit_from_buf_body;
audit_to_buf = audit_to_buf_body;
printk("oh~ Starting System Call Auditing !!\n");
return 0;
}
static void __exit audit_exit(void)
{
audit_to_buf = NULL;
audit_from_buf = NULL;
printk("oh~ Exiting System Call Auditing !!\n");
return;
}
MODULE_LICENSE("Dual BSD/GPL");
module_init(audit_init);
module_exit(audit_exit);
Makefile file
obj-m += myaudit_module.o
CONFIG_MODULE_SIG=n
LINUX_KERNEL_PATH := /lib/modules/$(shell uname -r)/build
all:
make -C $(LINUX_KERNEL_PATH) M=$(CURDIR) modules
clean:
make -C $(LINUX_KERNEL_PATH) M=$(CURDIR) clean
Compile and load modules
sudo make
sudo insmod hello.ko
lsmod | grep hello View information about adding modules
dmesg Get kernel information
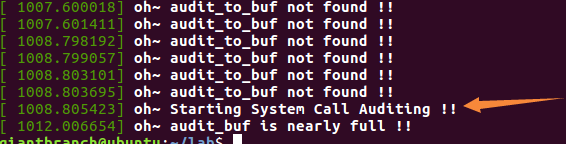
The third step , Write a log collector
#include <stdlib.h>
#include <stdio.h>
#include <errno.h>
#include <signal.h>
#include <sys/resource.h>
#include <sys/syscall.h>
#include <sys/types.h>
#include <unistd.h>
#include <stdbool.h>
typedef unsigned char u8;
typedef unsigned int u32;
#define COMM_LENGTH 16
struct Audit_buf {
u32 serial;
u32 syscall;
u32 status;
pid_t pid;
uid_t uid;
u8 comm[COMM_LENGTH];
};
#define AUDIT_BUF_SIZE 20
#define USR_AUDIT_BUF_SIZE AUDIT_BUF_SIZE*sizeof(struct Audit_buf)
int main(int argc, char *argv[])
{
u8 my_audit_buf[USR_AUDIT_BUF_SIZE];
struct Audit_buf *p;
while(true) {
//334 Is the call number of the customized system call
int log_cnt = syscall(334, 0, my_audit_buf, USR_AUDIT_BUF_SIZE);
p = (struct Audit_buf *)my_audit_buf;
int i;
for(i=0; i<log_cnt; i++) {
printf("serial:%d, ", p[i].serial);
printf("syscall_number:%d, ", p[i].syscall);
printf("ret_status:%d, ", p[i].status);
printf("pid:%d, ", p[i].pid);
printf("uid:%d, ", p[i].uid);
printf("commond:%s.\n", p[i].comm);
}
}
return 0;
}
gcc -o myaudit_program myaudit_program.c
./myaudit_program

linux kernel api
https://www.kernel.org/doc/htmldocs/kernel-api/index.html
Reference link
> https://blog.csdn.net/weixin_41708020/article/details/106124753
> https://blog.csdn.net/qq_32828145/article/details/78667414?spm=1001.2101.3001.6650.10&utm_medium=distribute.pc_relevant.none-task-blog-2~default~OPENSEARCH~default-10.no_search_link&depth_1-utm_source=distribute.pc_relevant.none-task-blog-2~default~OPENSEARCH~default-10.no_search_link
边栏推荐
- On vio's IMU pre integration (the idea when I first started)
- 滴滴被罚80亿!拿用户数据赚钱的时代结束了
- 【云驻共创】为了写好代码,你坚持了哪些好习惯?
- Build neural network from simple to deep
- ESP8266-Arduino编程实例-开发环境搭建(基于Arduino IDE)
- 了解 useRef 一篇就够了
- 想让照片中的云飘起来?视频编辑服务一键动效3步就能实现
- Meiker Studio - Huawei 14 day Hongmeng equipment development practical notes 8
- Orbslam2 cmakelists File Structure Parsing
- 7月27日19:30直播预告:HarmonyOS3及华为全场景新品发布会
猜你喜欢
随机推荐
梅科尔工作室-华为14天鸿蒙设备开发实战笔记八
Static routing and dynamic routing
常用库安装
系统调用捕获和分析—修改内核方法添加系统调用
Mongodb - use $type to query whether the type of a field is XXX
MySQL locking mechanism
武林头条-建站小能手争霸赛
想让照片中的云飘起来?视频编辑服务一键动效3步就能实现
ESP8266-Arduino编程实例-认识ESP8266
swagger2.9.2教程 与swagger3.0.0教程
Data visualization - White Snake 2: black snake robbery (2)
Creation and modification of basic tables and data in them by SQL statements of SQL Server
李宏毅《机器学习》丨2. Regression(回归)
系统调用捕获和分析—Ring0层kprobe劫持系统调用
贝尔曼期望方程状严谨证明
打造绿色数据中心,Colt DCS 是认真的!
Hal library IIC simulation in punctual atom STM32 `define SDA_ IN() {GPIOB->MODER&=~(3<<(9*2));GPIOB->MODER|=0<<9*2;}` // PB9 input mode
Orbslam2 cmakelists File Structure Parsing
【云驻共创】解密SparkRTC如何在全球实现超低时延交互
10 reduce common "tricks"




![[idea] how to create a new project](/img/33/f210d59ccd3664487f401929dac24c.png)




