当前位置:网站首页>Web security summary
Web security summary
2022-07-03 11:36:00 【Jiangnan has no old friends】
Web Safety final summary
SQL Inject
principle :
utilize Web Security loopholes in the processing of background database query statements , The attacker submits a carefully constructed database query code , Based on the returned results , Get the data he wants to know
Affected systems : A system that does not check and filter input parameters
common SQL Injection process :
1. Modify parameter values and other data , The modified data is injected into SQL In the sentence
2. The database engine executes the modified SQL command , Return the result
3. Construct statements based on the returned sensitive information for further injection

example :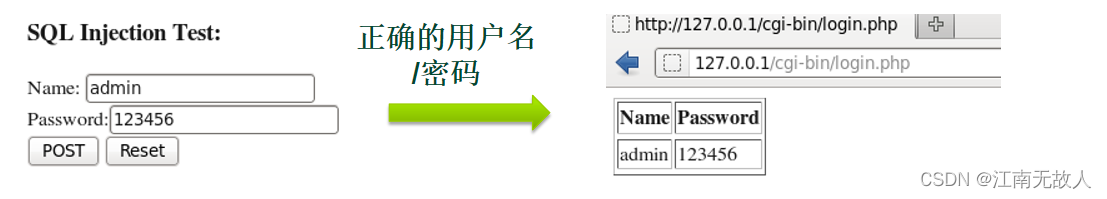

Cross-site scripting attacks (XSS)
principle :
Web The server did not validate the user input , And easily return to the client
The attacker went to Web Malicious insert in the page html Code , When a user views the web page , The malicious code embedded in it is executed
harm :
You can steal user accounts , Modify user settings , Stealing / Pollution cookie, Make false advertisement , Check the host information
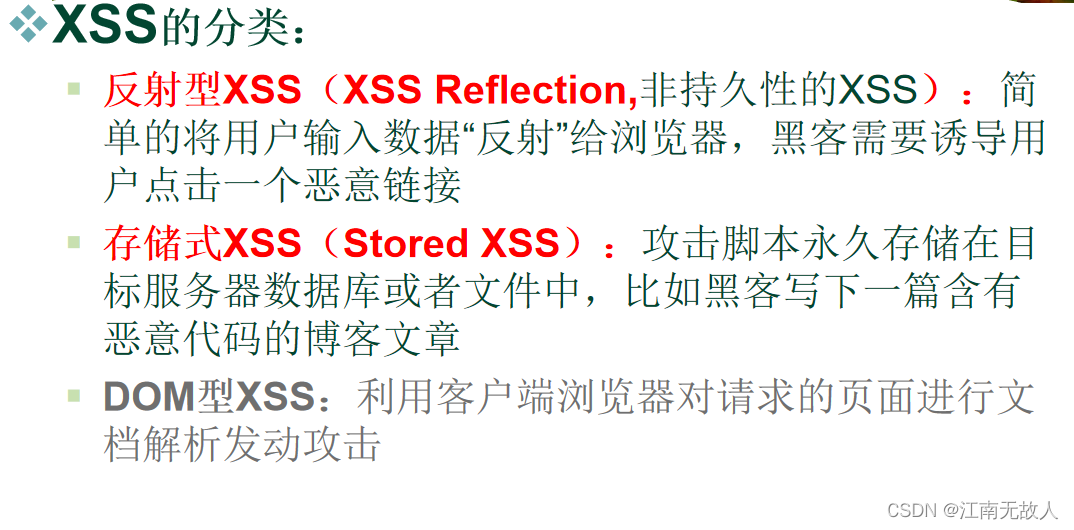
Attack steps :
1. Looking for loopholes
2. Inject malicious code
3. Trick users into accessing


Cross-site request forgery (CSRF)
principle :
The target site A, Malicious websites B

The file contains a vulnerability

When using this 4 When a function contains a new file , This document will serve as php Code execution ,php The kernel doesn't care about the type of file that should be included
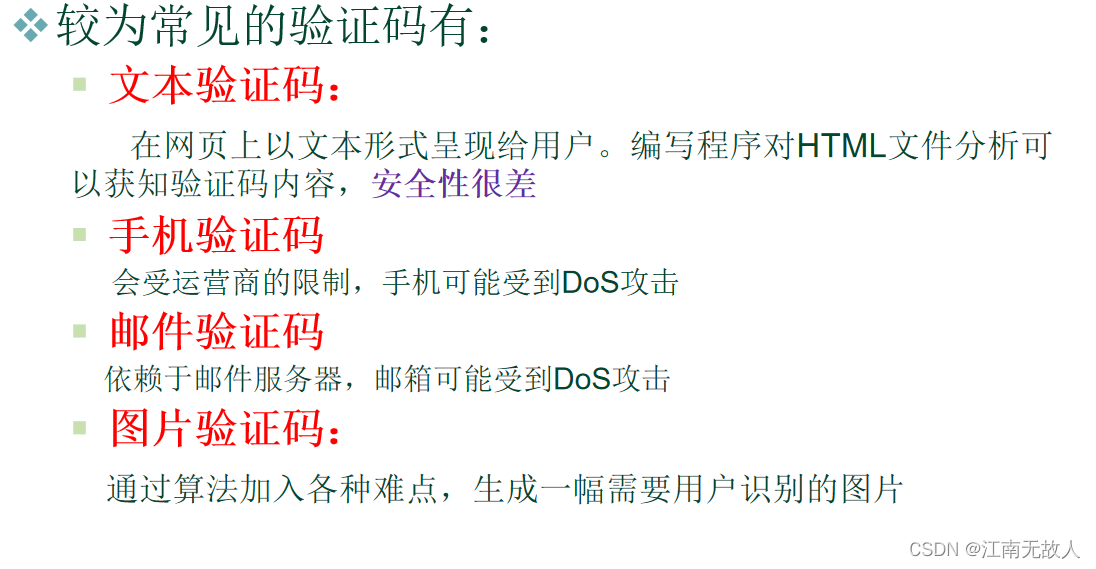
Verification code technology
It is used to distinguish between man and machine , It's defense http A means of attack
summary
Threats to clients and servers :
defense Web attack :
The server :
1. simplicity , It's best to remove unnecessary services
2. Use super users with caution
3. Local and remote access control
4. Audit , Look for suspicious data in the audit records
5. Backup policy , It is convenient to quickly restore services to reduce losses
client :
1. Set the security of the browser , Use browsers with fewer vulnerabilities , Upgrade the browser frequently
2. Often patch the operating system 、 upgrade
3. Try not to open some untrusted websites
The same-origin policy :

边栏推荐
- Spl06-007 air pressure sensor (example of barometer)
- PHP server interacts with redis with a large number of close_ Wait analysis
- Reading notes: heart like Bodhi, Cao Dewang
- C language utf8toutf16 (UTF-8 characters are converted to hexadecimal encoding)
- Gut | 香港中文大学于君组揭示吸烟改变肠道菌群并促进结直肠癌(不要吸烟)
- After setting up ADG, instance 2 cannot start ora-29760: instance_ number parameter not specified
- LeetCode 46:全排列
- After a month, I finally got Kingdee offer! Share tetrahedral Sutra + review materials
- Stm32hal library upgrades firmware based on flash analog U disk (detailed explanation)
- Arctangent entropy: the latest SCI paper in July 2022
猜你喜欢

聊聊Flink框架中的状态管理机制
Kubernetes 三打探针及探针方式
GCC compilation process and dynamic link library and static link library
Google Earth engine (GEE) - ghsl global population grid dataset 250 meter resolution

How to get started embedded future development direction of embedded
Based on MCU, how to realize OTA differential upgrade with zero code and no development?

机器学习 3.2 决策树模型 学习笔记(待补)
![抓包整理外篇fiddler———— 会话栏与过滤器[二]](/img/04/e9cc027d753e7049f273d866eefdce.png)
抓包整理外篇fiddler———— 会话栏与过滤器[二]

Summary of interview questions (2) IO model, set, NiO principle, cache penetration, breakdown avalanche
一文搞懂Go语言Context
随机推荐
R language uses grid of gridextra package The array function combines multiple visual images of the lattice package horizontally, and the ncol parameter defines the number of columns of the combined g
MATLAB提取不规则txt文件中的数值数据(简单且实用)
Internet socket (non) blocking write/read n bytes
This article explains the complex relationship between MCU, arm, MCU, DSP, FPGA and embedded system
Oracle withdraw permission & create role
Phpcms prompt message page Jump showmessage
CSRF
asyncio 警告 DeprecationWarning: There is no current event loop
一文搞懂Go语言Context
Numpy np.max和np.maximum实现relu函数
Understand go language context in one article
Arctangent entropy: the latest SCI paper in July 2022
Asyncio warning deprecationwarning: there is no current event loop
LeetCode 46:全排列
(2) Base
AMS series - application startup process
AI模型看看视频,就学会了玩《我的世界》:砍树、造箱子、制作石镐样样不差...
How to get started embedded future development direction of embedded
Redis things
R语言使用aggregate函数计算dataframe数据分组聚合的均值(sum)、不设置na.rm计算的结果、如果分组中包含缺失值NA则计算结果也为NA