当前位置:网站首页>PCIe Capabilities List
PCIe Capabilities List
2022-06-26 15:42:00 【Little fatty fruit】
PCIe Configuration space
PCIe take PCI Of 256Bytes The configuration space is extended to 4096bytes.PCIe The configuration space can be divided into two parts :256bytes Of PCI Compatible with some configuration spaces and PCIe Expand the configuration space .
and PCIe Of Capabilities List It's also divided into two parts :PCI Compatible parts and PCIe Extension part Capabilities List.

PCI Capabilities List
stay PCI2.1 Add some abilities after , The protocol is added according to the linked list , This management Capabilities The linked list is called Capabilities;
Whether or not this linked list exists can be saved through PCI Status Register Of bit4(Capabilities List) instructions , When it is 1 Indicates presence ; Otherwise, it does not exist ;0x34h Indicates the first Capabilities The pointer to ;
In each table Capability Include 8bit ID Domain ,ID from PCI SIG Distribute ;8bit The pointer to , Points to the next... In the table Capabilities The location of ( When its value is 0x00h It means the end of the linked list ); And some other registers to perform correlation Capabilities, These registers are followed by the previous registers ;

The above example constructs a simple Capabilities List.0x34h Point to the first one Capabilities The location of , Yes 0xA4h, There is a ID, next Capabilities The pointer points to 0x5Ch, And contains other related registers ;
0xA4h Yes 0x5Ch;0x5Ch Point to 0xE0h;0xE0h Point to 0x0 Indicates that the linked list is over .
PCIe Extended Capabilities List
PCIe Extended Capabilities List and PCI Different ; The relevant registers are placed in 0x100 And higher address locations ; first PCIe Extended Capabilities Register fixed in 0x100 Location , Include 16bit Of Capabilities ID、4bit Capabilities Version Number and 12bit Next Capabilities Offset; Other forms are similar to the above ;
边栏推荐
- el-dialog拖拽,边界问题完全修正,网上版本的bug修复
- HW safety response
- [applet practice series] Introduction to the registration life cycle of the applet framework page
- [tcapulusdb knowledge base] Introduction to tcapulusdb general documents
- [tcapulusdb knowledge base] tcapulusdb doc acceptance - transaction execution introduction
- Comparative analysis of restcloud ETL and kettle
- 学习内存屏障
- 【TcaplusDB知识库】TcaplusDB单据受理-建表审批介绍
- JS之手写 bind、apply、call
- AbortController的使用
猜你喜欢

【TcaplusDB知识库】TcaplusDB数据构造介绍
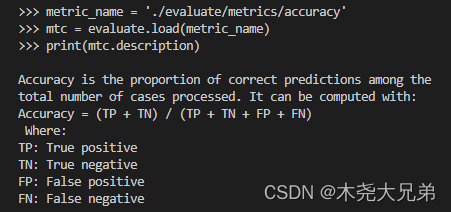
Evaluate:huggingface评价指标模块入门详细介绍
Mr. Du said that the website was updated with illustrations

Binding method of multiple sub control signal slots under QT

评价——模糊综合评价
![[tcapulusdb knowledge base] tcapulusdb doc acceptance - transaction execution introduction](/img/7c/25a88f46e02cebd2e003b9590b9c13.png)
[tcapulusdb knowledge base] tcapulusdb doc acceptance - transaction execution introduction

AbortController的使用

svg环绕地球动画js特效

Don't remove custom line breaks on reformat

查词翻译类应用使用数据接口api总结
随机推荐
Using restcloud ETL shell component to schedule dataX offline tasks
学习内存屏障
【TcaplusDB知识库】TcaplusDB系统管理介绍
通过券商经理的开户链接开股票账户安全吗?还是去证券公司开户安全?
Seurat转h5ad总结
There are so many vulnerabilities in tcp/ip protocol?
Database - integrity constraints
Secure JSON protocol
How to handle 2gcsv files that cannot be opened? Use byzer
【leetcode】112. Path sum - 113 Path sum II
[tcapulusdb knowledge base] Introduction to tcapulusdb system management
Is it safe to buy stocks and open accounts through the QR code of the securities manager? Want to open an account for stock trading
AUTO sharding policy will apply DATA sharding policy as it failed to apply FILE sharding policy
【问题解决】新版webots纹理等资源文件加载/下载时间过长
Cache page keepalive use in Vue
JS之手写 bind、apply、call
在重新格式化时不要删除自定义换行符(Don‘t remove custom line breaks on reformat)
Auto Sharding Policy will apply Data Sharding policy as it failed to apply file Sharding Policy
Audio and video learning (III) -- SIP protocol
golang 1.18 go work 使用
