当前位置:网站首页>Supplement the JS of a video website to decrypt the video
Supplement the JS of a video website to decrypt the video
2022-07-04 05:19:00 【Black swordsman and sword】
Preface :
Not long ago , A group friend posted a video in the Group m3u8 file , Among them key yes 16 byte , But it just can't be downloaded . But with m3u8 When the Downloader Downloads , Can't download it , I began to suspect that there was a request for head test , I requested it with code , It is found that normal requests can be made . That should be encryption .
1. Lay down ts,m3u8 or key The breakpoint
Find out where there is encryption , Follow in . I found this js
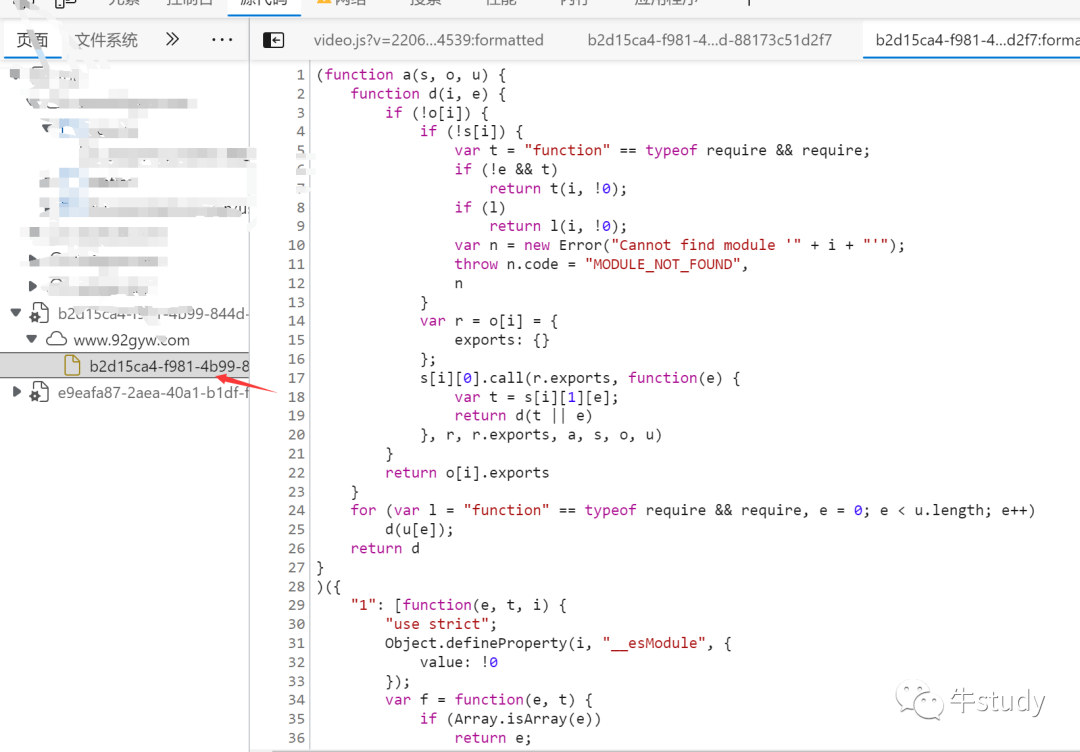
This js It's loaded later , You can see , Generally, it is automatically loaded later js, There is something fishy inside .
2. Find decryption js
Find this function here , Decryption is here
![]()
find js after , Here we will not analyze the algorithm , Directly intend to supplement the environment . This will make us js download , To vscode Run it inside and have a look . He will report a mistake self and window Undefined . Let's make up this ,self Directly assign an empty object ,window=this;
![]()
And run it , Found no error reported . We want to call this e.onmessage function . What to do then ?
3. Call the function to decrypt
I think so webpack pack , There is a loader . All functions are in o Inside the object , Here we put o Object export , To call .

Let's run it here , Look at the effect .

You can see , All functions have been exported . So we can call normally .
4. Look at the incoming parameters
We can see , These parameters are passed in

This key and iv It's a little strange. . Here we use this directly key and iv To decrypt , It is found that it can be decrypted normally .
5 see iv and key How to generate
Here is the old step , Make breakpoints , then , Step by step . Let's put the encryption method directly here
key = new Uint32Array([(r.getUint32(0) ^ a[0]) >>> 0, (r.getUint32(4) ^ a[1]) >>> 0, (r.getUint32(8) ^ a[2]) >>> 0, (r.getUint32(12) ^ a[3]) >>> 0])
IV[0] = parseInt(r.attributes.IV[0], 16), IV[1] = parseInt(r.attributes.IV[1], 16), IV[2] = parseInt(r.attributes.IV[2], 16), IV[3] = parseInt(r.attributes.IV[3], 16),
key Generated a Of , Is in window One of the attributes in it .

I didn't study this , It's dead .
The environment here has been improved , Just call it directly , After decryption, there is no flower screen .
OK, That's it today , Communication group 902854353
边栏推荐
- LM小型可编程控制器软件(基于CoDeSys)笔记二十二:错误4268/4052
- Trie number dictionary tree
- Notepad++--显示相关的配置
- 令人头痛的延时双删
- JS string splicing enhancement
- 2022 question bank and answers for safety management personnel of hazardous chemical business units
- A summary of the 8544 problem that SolidWorks Standard cannot obtain a license
- 空洞卷积、可变形卷积、可变形ROI Pooling
- [untitled]
- 模拟小根堆
猜你喜欢
![[interested reading] advantageous filtering modeling on long term user behavior sequences for click through rate pre](/img/3e/b5df691ca1790469eb1b4e8ea5b4c0.png)
[interested reading] advantageous filtering modeling on long term user behavior sequences for click through rate pre
Sécurité du réseau dans les écoles professionnelles secondaires - preuve de mémoire
![[QT] timer](/img/df/5db6af851ef19f33fd7e7a7ed46586.png)
[QT] timer
VSCode的有用插件
![[wechat applet] template and configuration (wxml, wxss, global and page configuration, network data request)](/img/78/63ab1a8bb1b6e256cc740f3febe711.jpg)
[wechat applet] template and configuration (wxml, wxss, global and page configuration, network data request)
![[technology development -25]: integration technology of radio and television network, Internet, telecommunication network and power grid](/img/87/e0469e280365ed0261e2b551ebd888.png)
[technology development -25]: integration technology of radio and television network, Internet, telecommunication network and power grid
NTFS security permissions

Trie数-字典树

Fault analysis | mongodb 5.0 reports an error, and the legal instruction solves it

TCP状态转换图
随机推荐
2022 t elevator repair operation certificate examination question bank and simulation examination
[paper summary] zero shot semantic segmentation
COMP1721 Creating Classes
[matlab] matlab simulates digital bandpass transmission systems - QPSK and OQPSK systems
How to use postman to realize simple interface Association [add, delete, modify and query]
2022年A特种设备相关管理(电梯)考试题模拟考试平台操作
Graduation design of small programs -- small programs of food and recipes
Annex 2-2 confidentiality commitment docx
TCP state transition diagram
[matlab] matlab simulation - narrow band Gaussian white noise
RSA加密应用常见缺陷的原理与实践
c语言经典指针和数组笔试题解析
全国职业院校技能大赛(中职组)网络安全竞赛试题—解析
Several smart watch related chips Bluetooth chip low power consumption
PostgreSQL has officially surpassed mysql. Is this guy too strong!
小程序毕业设计---美食、菜谱小程序
Analysis of classical pointer and array written test questions in C language
中科磐云—2022广西逆向解析思路
中科磐云—D模块解析以及评分标准
Fault analysis | mongodb 5.0 reports an error, and the legal instruction solves it