当前位置:网站首页>Exercise bubble sort
Exercise bubble sort
2022-07-04 04:59:00 【Ssaty.】
边栏推荐
猜你喜欢
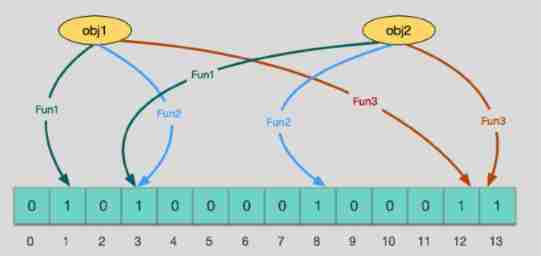
Deep understanding of redis -- bloomfilter

2022年6月总结

Fault analysis | mongodb 5.0 reports an error, and the legal instruction solves it
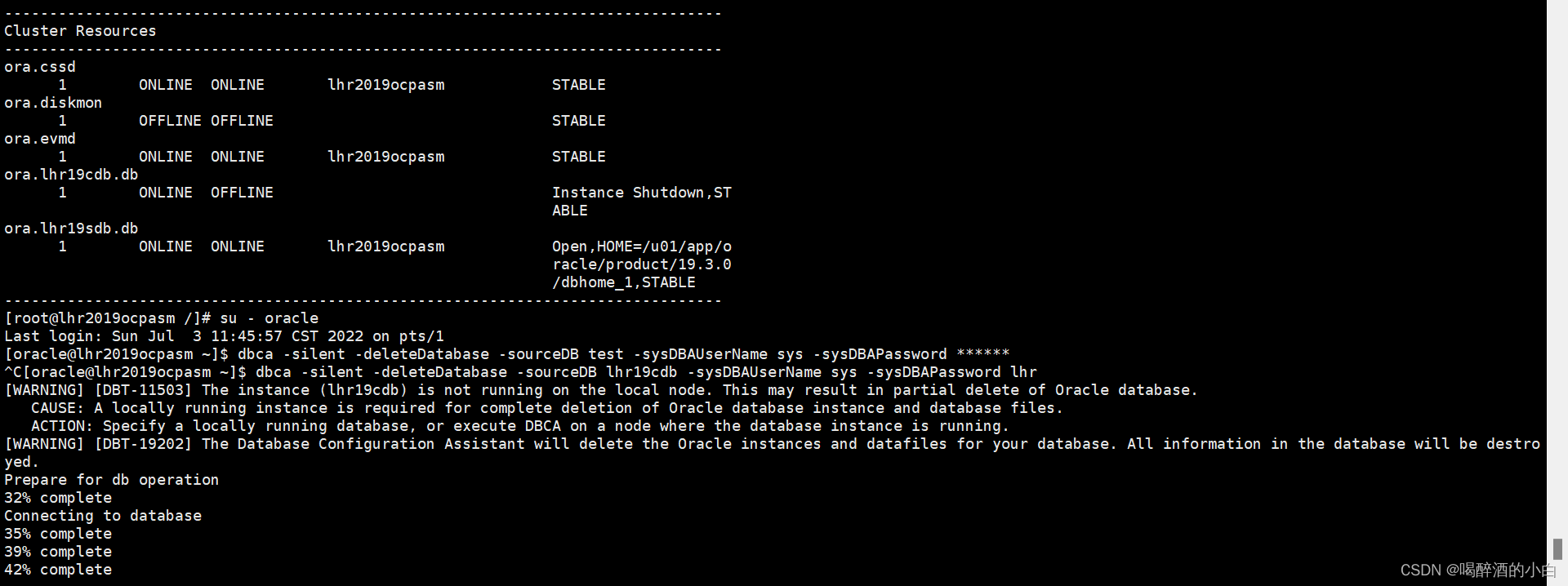
关闭的数据能用dbca删除吗? 能

软件设计文档示例模板 - 学习/实践

分享一些我的远程办公经验
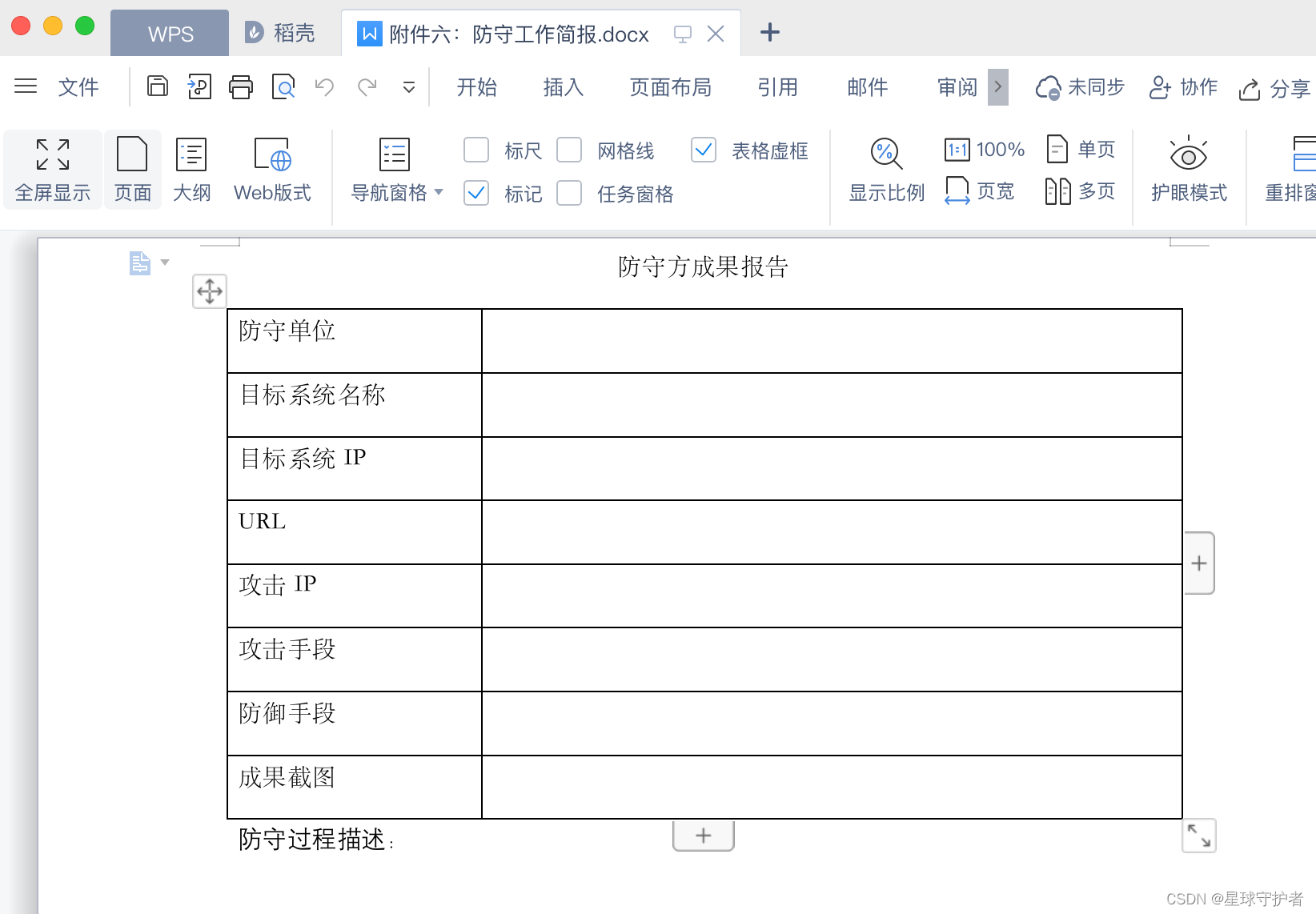
附件六:防守工作簡報.docx

Utiliser des unités de mesure dans votre code pour une vie meilleure

What is context?

Flutter ‘/usr/lib/libswiftCore.dylib‘ (no such file)
随机推荐
【MATLAB】MATLAB 仿真数字基带传输系统 — 数字基带传输系统
【MATLAB】MATLAB 仿真数字基带传输系统 — 双极性基带信号(第 I 类部分响应波形)的眼图
【MATLAB】通信信号调制通用函数 — 傅里叶逆变换
@Feignclient comments and parameters
Flutter 调用高德地图APP实现位置搜索、路线规划、逆地理编码
MySQL JDBC programming
抓包整理外篇fiddler———— 会话栏与过滤器
RAC delete damaged disk group
qt下开发mqtt的访问程序
Annex 2-2 confidentiality commitment docx
令人头痛的延时双删
通过dd创建asm disk
[go] database framework Gorm
【MATLAB】MATLAB 仿真数字基带传输系统 — 双极性基带信号(余弦滚降成形脉冲)的眼图
《Cross-view Transformers for real-time Map-view Semantic Segmentation》论文笔记
Solve the problem of failed to load property source from location 'classpathapplication YML 'problem
关于solidworks standard无法获得许可 8544问题的总结
Niuke Xiaobai monthly race 49
Definition of DCDC power supply current
在代码中使用度量单位,从而生活更美好