当前位置:网站首页>Annex 2-2 confidentiality commitment docx
Annex 2-2 confidentiality commitment docx
2022-07-04 04:52:00 【Planet Guardian】
Commitment letter of participating units in network attack and defense drill
The unit is aware of the importance of this exercise and the obligation of safety and confidentiality , And solemnly promise :
One 、 Ensure the political reliability of the actors 、 Excellent quality , Be competent for this exercise task and ensure the safety and reliability of the attack process .
Two 、 Ensure that the personnel of our unit participating in the drill obey the order of the drill headquarters , Follow the command .
3、 ... and 、 Don't leak 、 Do not make use of the relevant data of the target system and the system vulnerabilities found in the exercise .
Four 、 Do not use the exercise behavior and process for commercial publicity .
5、 ... and 、 Achieve “ XVI prohibition ”:
1、 It is forbidden to talk about or disclose the relevant contents of the drill to irrelevant personnel . This drill will not be publicized , During the drill, visitors and participants are not allowed to take photos , Hair circle of friends .
2、 It is forbidden to connect the relevant data in the drill to the Internet .
3、 Drill implementation stage , Private communication between the offensive and defensive sides is prohibited .
4、 It is forbidden to perform destructive operations on any system .
5、 It is forbidden to bribe the personnel of the attacked party 、 Physical intrusion 、 Cut off and monitor the external optical fiber 、 Attack by means of radio interference and other attacks that directly affect the operation of the target system , The way of attack cannot damage personal safety .
6、 Non registered IP Attack with the springboard .
7、 Without the approval of the drill headquarters , The attack team cannot change the actors without authorization
8、 Without the approval of the drill headquarters , The attacker is forbidden to attack key parts .
9、 It is forbidden to use with automatic deletion 、 Copy the target operating system files 、 Damage boot sector 、 Active diffusion 、 Infection file 、 Attack tools that cause server downtime and other destructive functions
10、 It is forbidden to disclose and unauthorized use the system hidden dangers and vulnerabilities found in the drill .
11、 Prohibit warehouse operation , Do not download personal information 、 Business data and source code
12、 It cannot affect the normal operation of the network
13、 Data cannot be added, deleted or modified 、 data 、 Catalog 、 structure
14、 Cannot implement traffic attack . Denial of service attacks ( Including slow denial of service attacks ).
15、 You cannot upload files other than the specified verification code 、 Program
16、 Do not publish without authorization 、 Retain 、 Use the information and data you have . After the drill , Please send the objective and other relevant documents provided by the organizer immediately 、 The results and reports generated by the drill are deleted by themselves
Legal representative ( Or authorized person ) The signature office :
Seal of commitment unit :
Japan period :
download
https://download.csdn.net/download/qq_41901122/85865296
边栏推荐
- Yolov6 practice: teach you to use yolov6 for object detection (with data set)
- 附件五:攻击过程简报.docx
- 郑州正清园文化传播有限公司:针对小企业的7种营销技巧
- MAUI 入门教程系列(5.XAML及页面介绍)
- Rhcsa 04 - process management
- appliedzkp zkevm(13)中的Public Inputs
- Zhengzhou zhengqingyuan Culture Communication Co., Ltd.: seven marketing skills for small enterprises
- Utiliser des unités de mesure dans votre code pour une vie meilleure
- Statistical genetics: Chapter 3, population genetics
- 1. Mx6u-alpha development board (LED drive experiment in C language version)
猜你喜欢

Instructions for LPC interrupt binding under ft2000+
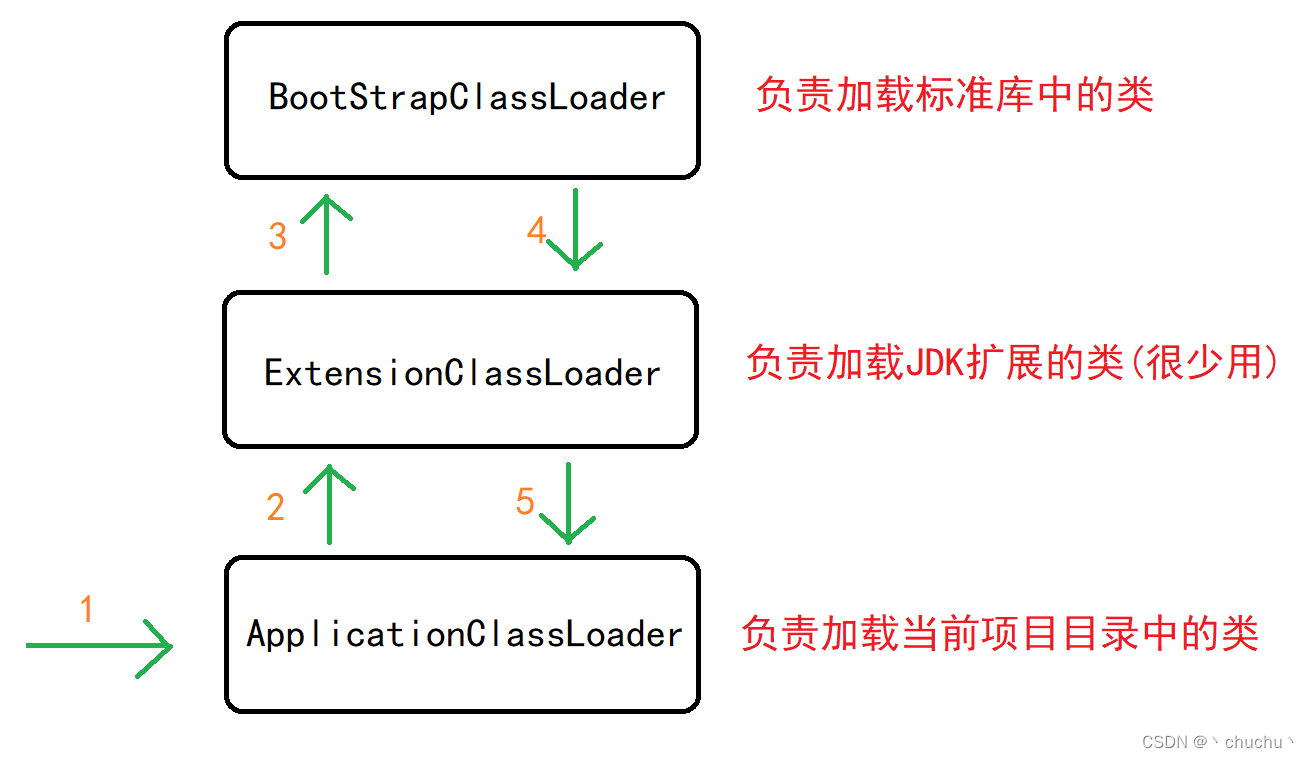
Talking about JVM
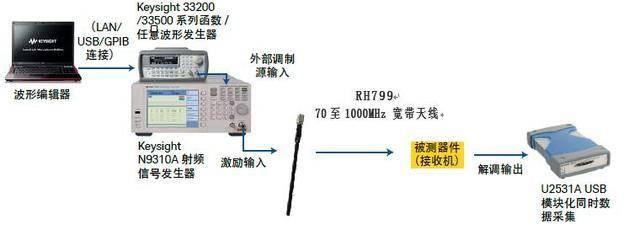
Keysight n9320b RF spectrum analyzer solves tire pressure monitoring scheme
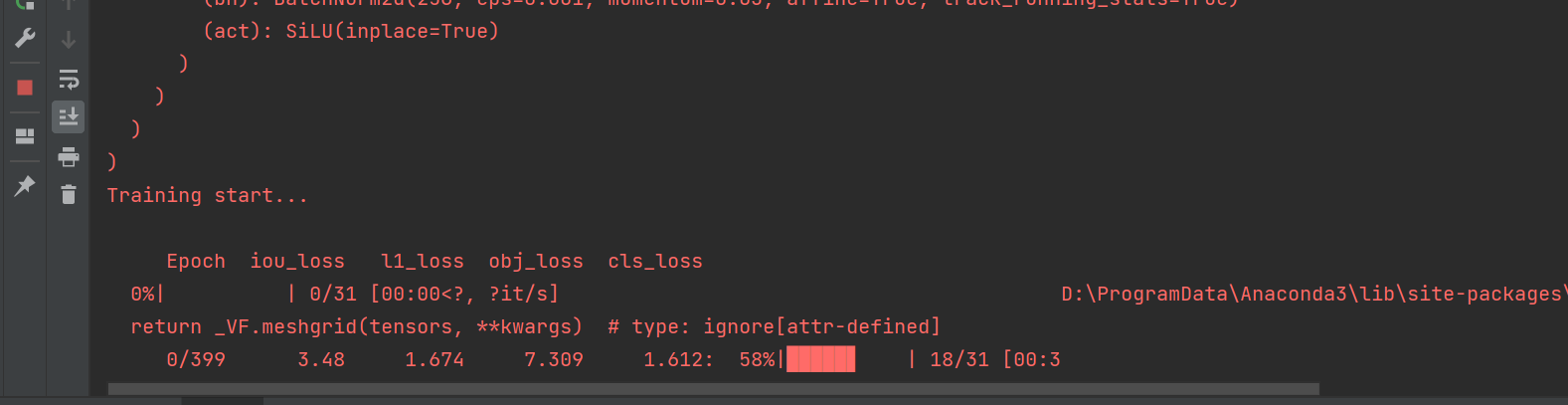
Yolov6 practice: teach you to use yolov6 for object detection (with data set)
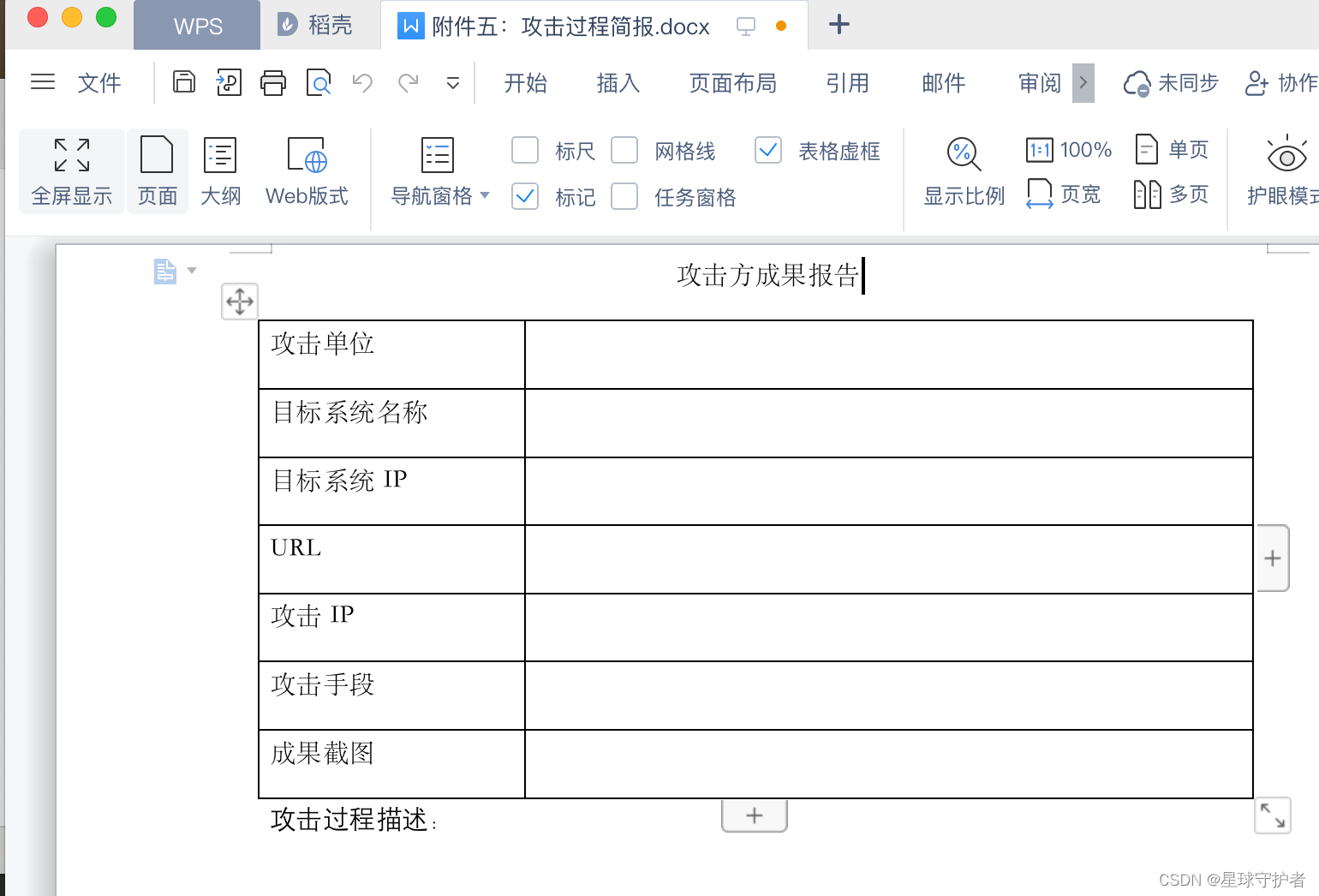
附件五:攻击过程简报.docx
Definition of DCDC power supply current
Rhcsa 04 - process management

Test cs4344 stereo DA converter
MySQL 索引和事务

郑州正清园文化传播有限公司:针对小企业的7种营销技巧
随机推荐
红队视角下的防御体系突破之第一篇介绍、阶段、方法
@Feignclient comments and parameters
Redis: operation command for collecting set type data
CRS-4013: This command is not supported in a single-node configuration.
Error response from daemon: You cannot remove a running container 8d6f0d2850250627cd6c2acb2497002fc3
[cloud native] those lines of code that look awesome but have a very simple principle
Correct the classpath of your application so that it contains a single, compatible version of com. go
更优雅地远程操作服务器:Paramiko库的实践
What should a novice pay attention to when looking for an escort
技术管理 - 学习/实践
Dp83848+ network cable hot plug
MAUI 入门教程系列(5.XAML及页面介绍)
MySQL JDBC编程
What is the difference between Western Digital Green disk, blue disk, black disk, red disk and purple disk
Sample template of software design document - learning / practice
网络设备应急响应指南
MySQL indexes and transactions
6-5漏洞利用-SSH弱口令破解利用
Network equipment emergency response Guide
附件一:202x年xxx攻防演习授权委托书