当前位置:网站首页>NTFS security permissions
NTFS security permissions
2022-07-04 04:58:00 【Liang Chenxing】
List of articles
NTFS Summary of permissions
1. By setting NTFS Authority , Realization ( Limit ) Different users have different permissions to access different objects .
2. After assigning the correct access rights , Users can access their resources .
3. Set permissions to prevent resources from being tampered with , Delete .
File System Overview
A file system is a method of organizing files on an external storage device .
Common file systems :
- FAT windows
- NTFS windows
- EXT Linux common
NTFS characteristic
1. Improve disk read and write performance .
2. reliability .
Encrypted file system
Access control list ( Set the permissions )
3. Disk utilization .
Compress
Disk quota
4. Support single file larger than 4 individual G.
modify NTFS jurisdiction
Cancel permission inheritance
effect : After the cancellation , You can modify the permission list at will .
Method : Folder right click Properties —— Security —— senior —— Remove the first check mark — Select copy .
File and folder permissions
File permissions :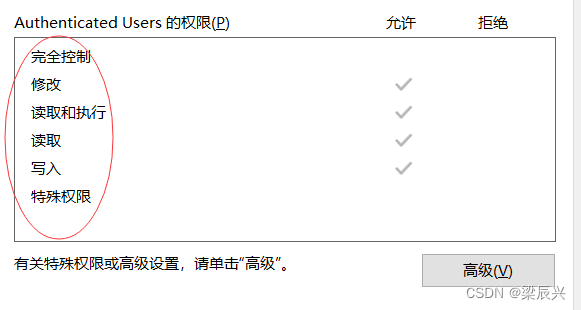
Folder permissions :
Case study :
establish jimi Folder , And set up NTFS jurisdiction , requirement a Users can only read files in folders , Can't be in jimi Create a new file in the folder ,b Users can only use jimi Create a new file in the folder , Can't read file .
Authority accumulation
When users belong to multiple groups at the same time , Permissions are cumulative !
Case study :
user a Belong to at the same time IT and HR Group ,IT Groups can pair folders jimi Read ,HR Groups can write to folders , be a The final permissions of the user are read and write .
Refuse maximum
When user permissions accumulate , If permission is denied , Refuse maximum !
Case study :
user a It belongs to the finance department , The members of the finance department are 10 Users , The finance department organizes the documents xxx Have access to , Current requirements a Users cannot leave the financial department group , Simultaneous requirements a No access to folder xxx Authority .
Take ownership
Only by default administrator You have the right to !
effect : You can change the owner of any folder to administrator.
Case study :
user a Resigned , but xxx The folder belongs to a, because a The user to xxx Permission modification has been made to the folder , Cause other users to xxx The folder does not have any permissions , Now you need an administrator administrator Users will xxx Modify folder permissions again .
Forced inheritance
effect : Forced inheritance of parent-child relationship !
Method : Right click folder properties – Security – senior – Tick the second check mark , that will do !
Case study :
xxx How high are subfolders and files in a folder , Due to long-time permission management , The permissions of multiple subfolders have been modified differently , Now we need xxx The permissions of all sub files and folders under are unified .
Impact of file replication on permissions
After the file is copied , The permissions of the file will be overwritten by the permissions of the target folder .
This chapter exercises :
1. Create a folder , Realization tom Users can only create new files ,jack Users can only read and download files .
2. Will the user a Add to ceo Group , And cannot be deleted from this group , For folder jimi Grant authority , requirement ceo The group can completely control jimi Folder , but a Cannot access this folder .
3. Ordinary users create files , And set permissions , And the administrator is not given any permission , After the administrator logs in to the system , The file can be deleted successfully ,
4. Practice forced inheritance , And verify the success .
边栏推荐
- How do good test / development programmers practice? Where to go
- DCDC电源电流定义
- Niuke Xiaobai monthly race 49
- 加密和解密
- Y55. Chapter III kubernetes from entry to proficiency -- HPA controller and metrics server (28)
- Correct the classpath of your application so that it contains a single, compatible version of com.go
- Flutter 调用高德地图APP实现位置搜索、路线规划、逆地理编码
- 中科磐云—数据分析与取证数据包flag
- Acwing game 58
- RAC delete damaged disk group
猜你喜欢

Change the background color of Kivy tutorial (tutorial includes source code)
Yolov6 practice: teach you to use yolov6 for object detection (with data set)

测试 CS4344 立体声DA转换器
Annexe VI: exposé sur les travaux de défense. Docx

在代碼中使用度量單比特,從而生活更美好

附件六:防守工作简报.docx

Sample template of software design document - learning / practice

Create ASM disk through DD

Fault analysis | mongodb 5.0 reports an error, and the legal instruction solves it

Introduction and application of rampax in unity: optimization of dissolution effect
随机推荐
Create ASM disk through DD
拼夕夕二面:说说布隆过滤器与布谷鸟过滤器?应用场景?我懵了。。
我们认为消费互联网发展到最后,依然会局限于互联网行业本身
定制一个自己项目里需要的分页器
【MATLAB】MATLAB 仿真模拟调制系统 — DSB 系统
Cmake compilation option setting in ros2
在代码中使用度量单位,从而生活更美好
Share some of my telecommuting experience
Operate the server remotely more gracefully: the practice of paramiko Library
RPC Technology
【MATLAB】MATLAB 仿真数字带通传输系统 — ASK、 PSK、 FSK 系统
6-5 vulnerability exploitation SSH weak password cracking and utilization
【MATLAB】通信信号调制通用函数 — 低通滤波器
qt下开发mqtt的访问程序
C language one-way linked list exercise
Correct the classpath of your application so that it contains a single, compatible version of com. go
Deep parsing structured exception handling (SEH) - by Matt Pietrek
中科磐云—2022广东木马信息获取解析
简单g++和gdb调试
红队视角下的防御体系突破之第二篇案例分析