当前位置:网站首页>Northwestern Polytechnic University attacked by hackers? Two factor authentication changes the situation!
Northwestern Polytechnic University attacked by hackers? Two factor authentication changes the situation!
2022-06-24 19:00:00 【51CTO】

In the near future , Northwest Polytechnic University The e-mail system is under network attack , Have a negative impact on the normal teaching life of the school . after According to the preliminary judgment of the public security organ , It is a network attack launched by overseas hacker organizations and criminals . In this network attack , There are hacker organizations and lawless elements from abroad to The School teachers and students send phishing emails containing Trojan horse programs , Attempt to steal relevant teacher-student email data and personal information of citizens , Cause major risks and hidden dangers to the normal work and life order of the school .
In today's Internet age , Not only will there be phishing mailboxes , SMS will also have fishing QR code . Two factor certification It can protect computers and mobile phones from accidental viruses .

How hacker organizations steal information ?
- Smoke screen : Hacker groups write fake programs , For example, the account login page , If you enter the account number and password , The information you enter will be sent to the hacker through the background .
- Phishing site : Phishing websites usually refer to websites disguised as banks and e-commerce , It's really a website to use counterfeiting URL Address and interface content or exploit the vulnerability of the website to insert dangerous HTML Code , So as to defraud the user's bank or credit card account 、 Passwords and personal information .
- Trojans : Hackers will implant Trojan viruses into the malicious websites they build , When users browse these websites, their computers will be infected by viruses . And Trojan virus will also be implanted into the game 、 Software, etc . When the Trojan runs, it will hide itself , Monitor and record the information entered by users in the background and send it to hackers .
How to prevent hackers from stealing your information ?
The strongest barrier : Two factor certification !
Even if the hacker has your account password , Can not steal your information !
The first factor ( Static password ) It can be set up simply , The second factor can use dynamic passwords 、 SMS verification code 、 Biometrics , Dynamic password and SMS verification code are random numbers , Very high security level and practicability , Biometrics is more secure , Lack of practicality , So now enterprises widely use dynamic password or SMS verification code for two factor authentication !
Which is better, dynamic password or SMS verification code ?
Let's start with the SMS verification code
SMS verification code is an effective verification code system that sends verification code to mobile phone , Each website sends a request to the server of the access provider through the interface , The server sends random numbers or letters to the phone , By the access provider's server unified verification code verification .
Infrastructure

First, add one CKEY Two factor authentication server , As a two factor management platform ;
Then add a SMS gateway , Send verification code ;
Finally, the user's mobile phone number is required , Receive verification code ;
When the user logs in , Need user name 、 Static password 、 SMS verification code Log in , This completes the closed loop of secure login !
Advantages of SMS verification code
1、 In the original user name 、 Add two factor authentication on the basis of static password , Safety and security ;
2、 You can receive the verification code through your mobile phone number , Easy to use ;
So the advantage summary is : Safe and convenient !
Similarly, SMS verification code also has some disadvantages
1、 The SMS verification code is seriously disturbed by the signal , The verification code may not be received ;
2、 SMS verification code is transmitted through the network , There is a risk of being intercepted ;
The shortcoming is summarized as : Poor stability and reliability
Let's look at dynamic password
One-time password (Dynamic Password) It is to generate an unpredictable combination of random numbers according to a special algorithm , It is widely used in online banking 、 Online games 、 Telecom operators 、 Electronic Commerce 、 Enterprise and other application fields .
Infrastructure

1、 Add one CKEY Two factor authentication server , As a two factor authentication management platform ;
2、 Bind a mobile phone for each user APP token , Generate dynamic password in real time ;
To achieve user name 、 Static password 、 One-time password Sign in . It is worth mentioning that dynamic passwords do not require network transmission , Therefore, it will not receive network interference .
Dynamic password advantage
1、 The dynamic password is generated and received independently , No need for network transmission , Will not be disturbed by the network ;
2、 Carry it with your mobile phone , Use as you go ;
safer !
The disadvantage is that it is not so convenient to use SMS verification code !
Comprehensive speaking
SMS verification code and dynamic password It's all worth mentioning , SMS verification code can make your system more secure , Dynamic password can greatly improve the security level of your system .
SMS verification code is more convenient , But the security is not as good as dynamic password ; Although dynamic password is a little troublesome , But it is more suitable for users who have higher requirements for system security .
边栏推荐
- DOM (document object model)
- 应用程序DDoS攻击原理及防御方法
- Real time rendering: the difference between real-time, offline, cloud rendering and hybrid rendering
- 为什么 Nodejs 这么快?
- Sr-gnn shift robot gnns: overlapping the limitations of localized graph training data
- BSS应用程序云原生部署的8大挑战
- finkcdc支持sqlserver2008么?
- ###脚本实现raid0自动化部署
- Sudoku (easy to understand)
- Mqtt protocol usage of LabVIEW
猜你喜欢

Volcano becomes spark default batch scheduler

网络安全审查办公室对知网启动网络安全审查

Vite+web3: referenceerror: process is not defined

电源噪声分析

Spatial simulation model acquisition future land cover tutorial

starring开发HttpJson接入点+数据库
Game between apifox and other interface development tools
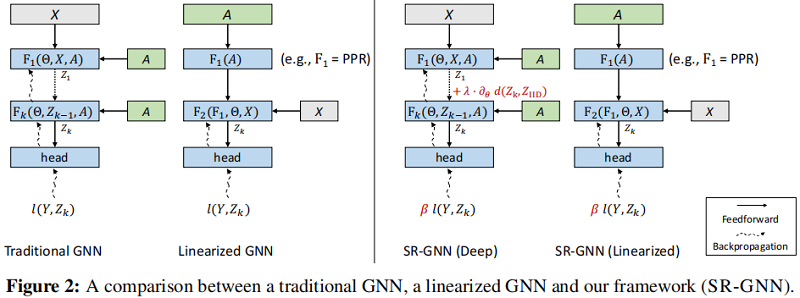
Interprétation de la thèse (SR - gnn) Shift Robust GNNS: Overcoming the Limits of Localized Graph Training Data

LabView之MQTT协议使用
![subject may not be empty [subject-empty]](/img/6b/9b57a7ed3ab086036cb6dfe0b31de4.png)
subject may not be empty [subject-empty]
随机推荐
LabView之MQTT协议使用
Buddha bless you that there will never be a bug
小滴课堂海量数据处理商用短链平台大课
Tkde2022: Dialogue recommendation system based on knowledge enhanced sampling
Monotone stack template
Microservice system design -- data model and system architecture design
上位机与MES对接的几种方式
Remote sensing Forum
微服务系统设计——数据模型与系统架构设计
想问下 pgsql cdc 账号同一个 多个 task 会有影响吗,我现在3个task 只有一个 有
JS deep understanding of scope
論文解讀(SR-GNN)《Shift-Robust GNNs: Overcoming the Limitations of Localized Graph Training Data》
Learn routing and data delivery
finkcdc支持sqlserver2008么?
Location object
okcc呼叫中心数据操作的效率问题
微服务系统设计——接口文档管理设计
How to perform power regression in R
Differences between get and post request modes
请问一下2.2.0版本支持动态新增mysql同步表吗