当前位置:网站首页>[Yugong series] March 2022 asp Net core Middleware - conditional routing
[Yugong series] March 2022 asp Net core Middleware - conditional routing
2022-06-12 03:26:00 【Hua Weiyun】
Preface
1. Introduction to conditional routing
First of all, we have to understand what is routing rules ? Suppose there is such a scenario, as shown in the figure below :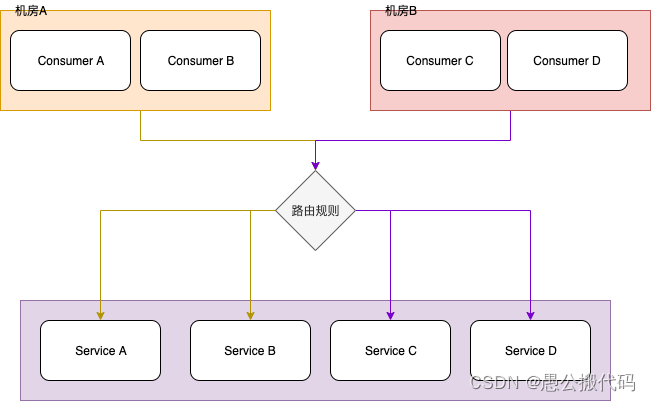
In the figure above, we can see that there are two machine rooms, namely the machine room A、 Computer room B, Including machine room A Only access to Service A and Service B , And the computer room B Only access to Service C and Service D. To realize the above scenario, we need to use the so-called routing rules . Routing rules are initiated once RPC Filter the target server address before calling , And the filtered address list , Will be the final launch of the consumer side RPC Alternative address for the call . stay Dubbo Two routing rules are supported in. Today, we mainly discuss conditional routing .
Conditional routing : Support the configuration of routing rules at the granularity of interface services or consumer applications .
2. Use scenarios
1. The blacklist : For example, we need to prohibit certain service consumers from consuming Services
host = 192.168.53.10,192.168.53.11 The above configuration indicates that 192.168.53.10、192.168.53.11 Consumers access service providers .
2. Service boarding in application , Only a part of the machine is exposed , Prevent the whole cluster from hanging up
host = 192.168.53.1*,192.168.53.2* The above configuration indicates that only 192.168.53.1*、192.168.53.2 ip The service provider at the beginning of the address .
3. Read / write separation : Read data and write data operations are separated
method = find*,list*,get*,is* => host = 192.168.53.10,192.168.53.11,192.168.53.12method != find*,list*,get*,is* => host = 192.168.20.97,192.168.53.21 The above configuration indicates that find*,list*,get*,is* Method names start with methods that can only access 192.168.53.10,192.168.53.11,192.168.53.12 Service providers , instead of find*,list*,get*,is* Method names start with methods that can only access 192.168.20.97,192.168.53.21 Service providers .
4. Providers and consumers are deployed in the same cluster , This machine only accesses the service of this machine
host = $hostThe above configuration indicates that all consumers can only access the services in the cluster .
Two 、ASP.NET Core Middleware conditional routing
Common implementation
endpoints.MapGet("/test2/{key:alpha}", async context =>{ var key = context.Request.RouteValues["key"].ToString(); foreach (var provider in Configuration.Providers.Reverse()) { if (provider.TryGet(key, out string value)) { await context.Response.WriteAsync(provider.ToString()); await context.Response.WriteAsync("\r\n"); await context.Response.WriteAsync(value); break; } }});But it is certain that they will be exposed in the production environment , To prevent exposure, you can use middleware .
1. Middleware code
public class DebugMiddleware : IMiddleware{ public async Task InvokeAsync(HttpContext context, RequestDelegate next) { var isDebugEndpoint = context.Request.Path.Value.Contains("/test"); var debugKey = context.Request.Query["debugKey"].ToString(); var debugKeyInConfig = "123456";// From configuration if (isDebugEndpoint && debugKey!=debugKeyInConfig) { context.SetEndpoint(new Endpoint((context) => { context.Response.StatusCode = StatusCodes.Status403Forbidden; return Task.CompletedTask; }, EndpointMetadataCollection.Empty, " No access ")); } await next(context); }}2. Use in pipes
app.UseMiddleware<DebugMiddleware >()边栏推荐
- Restful interface design specification [for reference only]
- Sequence list and linked list ----- advanced
- An example of how to migrate the stock equipment of the Internet of things platform to the enterprise version with one click
- CA证书及密钥对应用笔记
- Yu Xia looks at win system kernel -- debugging
- [data recovery in North Asia] data recovery in which the logical volume of the server is changed and the file system is damaged due to system reinstallation
- The rise of another domestic mobile phone chip is close to the height reached by Huawei
- KV storage separation principle and performance evaluation of nebula graph
- mysql/oracle 以唯一时间为分界,小于等于该时间求和,大于该时间求和
- Sed command
猜你喜欢
无限循环判断方法;

MySQL partition table create delete modify view
![What is a request response pair called? [repeat] - what is a request response pair called? [duplicate]](/img/65/a214d137e230b1a1190feb03660f2c.jpg)
What is a request response pair called? [repeat] - what is a request response pair called? [duplicate]

Exemple de projet d'applet Wechat - calculatrice de constitution

Data flow diagram of Flink
Youcans' opencv lesson - 10 Image restoration and reconstruction

Paper recommendation: relicv2, can the new self supervised learning surpass supervised learning on RESNET?

Wechat applet project example - I have a paintbrush (painting)

2020-12-10

The road of global evolution of vivo global mall -- multilingual solution
随机推荐
MySQL创建用户并授权
vim命令大全
Computer configuration suggestions for learning modeling
消息队列概述
[Business Research Report] 2021 global mobile game player white paper - download link attached
[untitled]
Sed command
Lighting Basics: optical model
Review of technical economy and Enterprise Management Chapter 4
无限循环判断方法;
微信小程序项目实例——我有一支画笔(画画)
Cryptology Summary
Cloud native overview
Fastjson enables safemode, closes autotype, and removes security vulnerabilities
Demand and business model innovation - demand 11 - overview of demand analysis
2020-12-07
mysql/oracle 以唯一时间为分界,小于等于该时间求和,大于该时间求和
Message queuing overview
Paper recommendation: relicv2, can the new self supervised learning surpass supervised learning on RESNET?
Leetcode 6[finding rules] Z-transform the leetcode path of heroding